Hackers happen every year, and this year is no exception.
As we all know, in the dark jungle of the crypto world, theft and theft are in a delicate balance. Hackers are rampant and pervasive. Security standards are continuously raised in these stress tests. Public responsibility, a rare term in the self-financing crypto field, is also placed in front of the project or platform again and again, testing the "pattern" of each platform and the "combined force" of the market.
Just after the beginning of the year, a vicious incident occurred again. On the evening of February 21, the exchange Bybit suffered a hacker attack worth $1.46 billion. In terms of the amount alone, this incident is already the largest hacker attack in the history of cryptocurrency.
Tracing the source of the hacker, the mysterious North Korean organization Lazarus Group has surfaced again.
Back to February 21, an ordinary Friday night, an extraordinary thing happened in the crypto market. First, at 23:27, the on-chain detective Zachxbt monitoring channel said that it had monitored suspicious funds flowing out of Bybit, with a total amount of more than 1.46 billion US dollars.
Later, the crypto KOLFinish also issued a statement to confirm that the on-chain data detected that a multi-signature address on Bybit transferred out ETH worth 1.5 billion US dollars and used DEX to exchange LSD assets for native ETH. It emphasized that the address was exchanged through 4 different DEXs, which would cause large slippage and transaction losses, and the transaction volume was so large that it was obviously unusual.
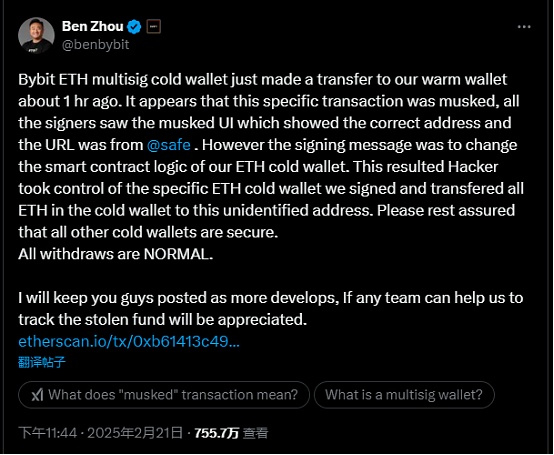
At 23:44, Bybit co-founder and CEO Ben Zhou issued a statement confirming this statement, saying that hackers controlled a specific ETH cold wallet, but the rest of the cold wallets were safe and withdrawals were normal. This news undoubtedly confirmed that the hacker committed the crime, and the stolen amount of up to $1.5 billion caused the market to panic for a while.
According to CoinMarketCap statistics, Bybit had $16.2 billion in reserve assets before the hacker attack, and the stolen assets of $11.5 billion accounted for about 8.64%. Judging from the amount alone, this has become the largest hacker theft in the history of encryption, exceeding the $611 million theft suffered by Poly Network in 2021. Even if it is not in the encryption field, the fraud amount of $1.5 billion is already astonishing in the traditional field. After this incident, Bybit hacker ETH holdings exceeded Fidelity and Vitalik, holding about 0.42% of the total supply of Ethereum tokens, becoming the 14th largest holder in the world.
The hacker's operation seemed to be very familiar. Shortly after the funds were stolen, the hacker evenly transferred 490,000 ETH to 49 addresses, and then used the mixer to launder money.
In this context, although Bybit spoke out in time, saying that it had sufficient solvency, and quickly launched a live Q&A session to propose a bridge loan to solve the problem, after the incident, the directly related ETH price fell by 6.7% on the same day, and Bitcoin also fell by nearly 3% from its high point on the same day.
From this moment on, Bybit and the hacker entered a tug-of-war of life and death. On the one hand, Bybit needs to solve the possible asset deficit as soon as possible, and face the panic withdrawal of users and even the possible run demand. On the other hand, the exchange is also obliged to use all means to prevent the hacker's funds from being realized.
It is worth mentioning that after the incident, the major exchanges that share the same aspirations also quickly staged a rescue operation. First-tier exchanges Binance and OKX, HTX, and HashKey quickly launched support, and CZ also gave a solution in a timely manner. But what is surprising is that the second-tier exchanges huddled together for warmth and directly came to help. Bitget showed an amazing big picture, supporting Bybit with 40,000 ETH in the shortest time. Of course, such a huge amount inevitably means the possibility of a community of interests behind it, but the support of real money still reflects the rare warmth in the industry.
MEXC hot wallet also transferred 12,652 stETH to Bybit cold wallet. Although Binance did not move, whales took the lead. Whale users also provided about 67,000 ETH. ABCDE co-founder Du Jun also posted on social media that he would transfer 10,000 ETH to Bybit and would not withdraw the currency within 1 month. According to monitoring by Ember, 5 institutions and individuals have provided loan support to Bybit, totaling about 120,000 ETH, worth about 321 million US dollars.
Thanks to the effective actions of the CEO and the joint efforts of the industry, at 9 am on February 22, Bybit CEO Ben Zhou said that 99.994% of the withdrawals had been completed, and all services of the Bybit exchange, including the withdrawal function, had returned to normal. On the same day, monitoring agencies such as SOSOVALUE also stated that Bybit funds had completed the gap coverage, saying that the Bybit trading platform had received a total inflow of more than 4 billion US dollars in the past 12 hours. According to the latest news today, Bybit CEO Ben Zhou tweeted that Bybit has completely filled the ETH gap, and a new audit POR (proof of reserves) report will be released soon. Lookonchain also monitored that Bybit obtained 447,000 ETH through various channels.
The industry is also working hard to block hackers in order to solve the fund run. Bybit said it has filed a case to track it down, and through the coordinated efforts of multiple parties, it successfully froze $42.89 million in stolen funds in one day. Institutions that provided assistance include Tether, THORChain, ChangeNOW, FixedFloat, Avalanche Ecosystem, CoinEx, Bitget, Circle, etc. But it has to be admitted that despite this, in the decentralized market of encryption, it is still very difficult to hope to completely block the hacker's token sale. As of 9 am today, the Bybit hacker has exchanged 50,700 ETH (US$142 million) for DAI and other on-chain assets, and currently holds 448,600 ETH (US$1.26 billion). If the timeline is extended, this fund will be sold out sooner or later.
What kind of hacker can bypass the industry's highest security standard of multi-signature + cold wallet and successfully take away $1.5 billion in full view of the public?
Soon, the details of the attack were further disclosed. Bybit's official Twitter account stated that Bybit detected unauthorized activity involving one of the ETH cold wallets. At the time of the incident, the ETH multi-signature cold wallet executed a transfer from the hot wallet. Unfortunately, the transaction was manipulated through a complex attack that obscured the signature interface, displayed the correct address, and changed the underlying smart contract logic. As a result, the attacker was able to control the affected ETH cold wallet and transfer its assets to an unidentified address.
The attack method is actually not complicated. In short, all exchanges have cold wallets and hot wallets. Cold wallets are used to store assets safely, while hot wallets are used for daily trading needs. There will also be a flow of money between the two. The hacker focused on this process. When Bybit transferred funds from cold wallets to hot wallets as usual, the hacker disguised a fake transaction interface and link to fish in troubled waters. Since cold wallets are usually multi-signature mechanisms, hackers also used social engineering techniques in this process. By hacking into the person/device who initiated the transaction, the subsequent auditors lowered their vigilance. After seeing the initiator's transfer application, the auditors would directly click to agree, and after agreeing, the wallet permissions were handed over to the hacker. In other words, the hacker did not attack the Safe multi-signature protocol itself, but designed a plan targeting the weaknesses of human nature.
Safe's front-end intrusion + social engineering techniques quickly reminded the market of the notorious initiator, the North Korean hacker Lazarus Group. In previous historical cases, Radiant Capital and WazirX were both stolen using similar methods, starting with employees' multiple signatures to replace signature content, upgrading the Safe contract to replace the deployed malicious contract, and quickly transferring the funds to the mixer after the operation was successful, and then disappearing to find traces.
This suspicion was confirmed. Four hours after the incident, the chain detective ZachXBT submitted conclusive evidence to prove that the attack on Bybit was carried out by the North Korean hacker group Lazarus Group.
In a derogatory sense, Lazarus is undoubtedly a terrifying existence in the industry. Coming from North Korea, which is not very modernized, Lazarus is the world's top hacker group, which is quite split and absurd. The first battle of the Lazarus Group was Operation Troy in 2009. Hackers used the common DDOS attack to complete the breach of the South Korean government and successfully implanted the text commemorating Independence Day in the master boot record (MBR) of 36 websites.
Afterwards, Sony Pictures and the Federal Reserve Bank of New York were attacked one after another, and the WannaCry ransomware attack affected nearly 200,000 computers in 150 countries, making it famous overnight. Starting in 2017, this hacker group began to turn its attention to the more anonymous encryption field. Bithumb and Nicehash have both been attacked. In recent years, the $620 million stolen from Ronin and the $100 million from Horizon Bridge were all behind the organization. A report released by blockchain security platform Immunefi stated that the Lazarus Group caused losses of more than $300 million in cryptocurrency hacking incidents in 2023, accounting for 17.6% of the total losses that year. In 2024, WazirX was also attacked and lost $234.9 million in crypto assets.
The attacks are frequent and the amount is huge. Even the US Department of Justice has failed to trace them. This organization has created chaos in the no-man's land of the Internet world and continuously earned foreign exchange for its motherland, North Korea. Perhaps some people wonder how North Korea has cultivated such a powerful hacker?
In fact, this is also a last resort for North Korea. In the long-term sanctions, compared with the actual huge investment in national defense and security affairs such as guns and cannons, cultivating hackers in the digital world has become the most cost-effective solution for North Korea. Since the 1980s, South Korea has begun to cultivate hackers under the code name of "Secret War" and recruit students with Automation University as the core base. It is said that the application elimination rate is as high as 80%. Even if you enter the study, you have to undergo rigorous training for up to 9 years, and you have been given missions since childhood. You will be assigned to different groups according to the attack area, and you will even become an undercover agent to integrate into the local culture to complete the mission objectives.
Of course, the lucrative income is not small. Hackers can earn up to $2,000 a month and be equipped with a luxury apartment of more than 185 square meters in the center of the capital. Although it seems that it is not worth much to hackers, in North Korea, where the per capita annual income is less than $1,000, they can be considered as the top of the pyramid.
Good and evil, in the adult world, it is difficult to evaluate. For users who have suffered unprovoked disasters, Lazarus can be considered pure evil, but for North Korea, every action of hackers represents the country's income and contribution, and for ordinary people, it may be a great good.
In the interweaving of good and evil, what the encryption field can do is to continuously improve security standards, formulate more complete security mechanisms and crisis solutions, to face the fierce attacks, and preserve fragile assets in the dark forest.
It is worth mentioning that this Bybit incident is undoubtedly a great rescue in the history of encryption. Regardless of the reason, the confidence and courage of the crypto world to work together in the industry still touched the market and became a rare dawn of humanity in garbage time. Perhaps everyone knows that today's market can no longer withstand another hacker attack of such a large scale. Interestingly, in the face of such a high-value attack, the US regulators who love long-arm jurisdiction seem to remain silent, and the new era of supervision is well-deserved.
But in any case, improving security is a priority that all users need to pay close attention to. This time it is Bybit, which has strong capital, so all employees support it. Although the amount stolen is large, it is only Bybit's profit for one year. However, the currency circle is never limited to Bybit. It is the norm for retail investors who are stolen without a ripple, have no way to seek help, and are easily bankrupt. For ordinary users, how to strike a balance between security and efficiency will be an eternal issue.
 Catherine
Catherine








