At 4:22:49 am on May 16, 2022, Beijing time, the CertiK security technology team monitored that FEG suffered a large-scale flash loan attack on the Ethereum and BNB chains, resulting in asset losses worth approximately US$1.3 million.
This attack is caused by a vulnerability in the "swapToSwap()" function, which directly uses the "path" entered by the useras a trusted party without screening and verifying the incoming parameters, allowing unauthenticated The "path" parameter (address) to use the assets of the current contract.
Therefore, by repeatedly calling "depositInternal()" and "swapToSwap()", the attacker can obtain permission to use the assets of the current contract without restriction , thereby stealing all assets in the contract.
One of the affected contract addresses: https://bscscan.com/address/0x818e2013dd7d9bf4547aaabf6b617c1262578bc7
Vulnerability transaction
Vulnerability address: https://bscscan.com/address/0x73b359d5da488eb2e97990619976f2f004e9ff7c
Vulnerability transaction sample: https://bscscan.com/tx/0x77cf448ceaf8f66e06d1537ef83218725670d3a509583ea0d161533fda56c063
Stolen Funds Tracking: https://debank.com/profile/0x73b359d5da488eb2e97990619976f2f004e9ff7c/history
relevant address
Attacker address: https://bscscan.com/address/0x73b359d5da488eb2e97990619976f2f004e9ff7c
Attacker contract: https://bscscan.com/address/0x9a843bb125a3c03f496cb44653741f2cef82f445
FEG token address: https://bscscan.com/token/0xacfc95585d80ab62f67a14c566c1b7a49fe91167
FEG Wrapped BNB(fBNB): https://bscscan.com/address/0x87b1acce6a1958e522233a737313c086551a5c76#code
attack steps
The following attack flow is based on this vulnerability transaction: https://bscscan.com/tx/0x77cf448ceaf8f66e06d1537ef83218725670d3a509583ea0d161533fda56c063
① The attacker borrows 915 WBNB and deposits 116 BNB into fBNB.
② The attacker created 10 addresses for use in subsequent attacks.

③The attacker deposits fBNB into the contract FEGexPRO by calling "depositInternal()".
"_balances2[msg.sender]" is incremented according to the balance of the current address.

④ The attacker calls "swapToSwap()", and the path parameter is the address of the previously created contract.
This function allows "path" to get 114 fBNB of the FEGexPRO contract.

⑤ The attacker repeatedly calls "depositInternal()" and "swapToSwap()" (steps ③ and ④), allowing multiple addresses (created in step ②) to acquire fBNB tokens for the following reasons:
Every time "depositInternal() " is called, _balance2[msg.sender] will increase by about 114 fBNB.
Every time "swapToSwap()" is called, the contract created by the attacker can obtain the usage permission of the 114 fBNB.
⑥ Since the attacker controls 10 addresses, each address can spend 114 fBNB from the current address, so the attacker can steal all fBNB in the attacked contract.

⑦ The attacker repeats steps ④⑤⑥ to exhaust the FEG tokens in the contract.

⑧ Finally, the attacker sells all depleted assets, repays the flash loan, and finally takes the rest of the profits.
Whereabouts of assets
As of 6:43 on May 16, 2022, the stolen funds were still stored in the attacker's wallet (0x73b359d5da488eb2e97990619976f2f004e9ff7c) on both the Ethereum and BSC chains.
Original funds from Tornado cash on Ethereum and BSC: https://etherscan.io/tx/0x0ff1b86c9e8618a088f8818db7d09830eaec42b82974986c855b207d1771fdbe
https://bscscan.com/tx/0x5bbf7793f30d568c40aa86802d63154f837e781d0b0965386ed9ac69a16eb6ab
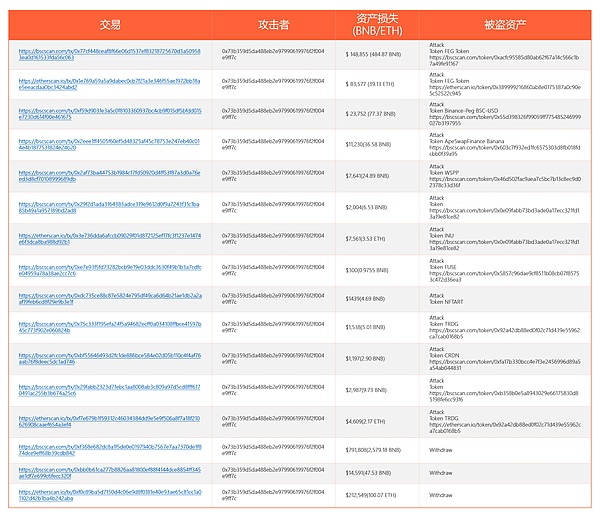
The attacker attacked 13 FEGexPRO contracts , the following is an overview:
 Edmund
Edmund











