Author: Yohan Yun, Aaron Wood; Translator: Deng Tong, Golden Finance
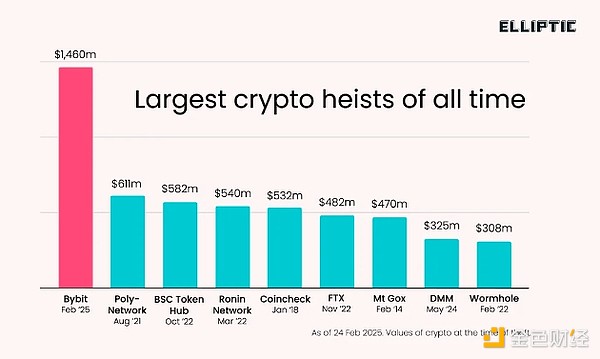
The $1.4 billion hack on Bybit was not only the largest attack in cryptocurrency history, but also a major test of the industry's crisis management capabilities, highlighting the maturity of the industry since the FTX collapse.
On February 21, North Korea's Lazarus Group stole $1.4 billion worth of Ethereum and related tokens, an incident that initially sent shudders through the entire cryptocurrency world, but was quickly quelled as the industry rallied to support Bybit to manage the consequences.
Let's take a look at how the attack unfolded, how Bybit responded, and where the stolen funds went.
February 21: Bybit Hacked
The Bybit hack was first discovered by on-chain sleuth ZachXBT, who warned platforms and exchanges to blacklist addresses associated with the hack.
Soon thereafter, Bybit co-founder and CEO Ben Zhou confirmed the breach and began providing updates and information about the intrusion.
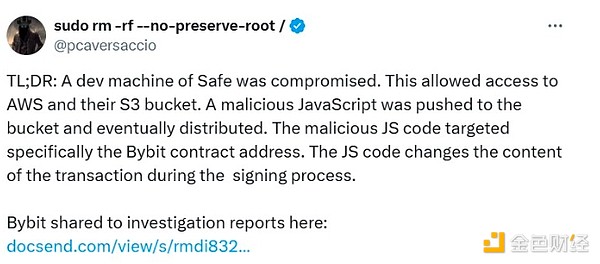
A post-mortem analysis report from Chainalysis initially stated that Lazarus carried out a phishing attack to access the exchange’s funds, but the analysis was later updated to report that the hackers took control of the computers of Safe developers rather than hacking into Bybit’s systems.
The attacker managed to "reroute" approximately 401,000 ETH, worth $1.14 billion at the time of the attack, and transferred it through an intermediary wallet network.
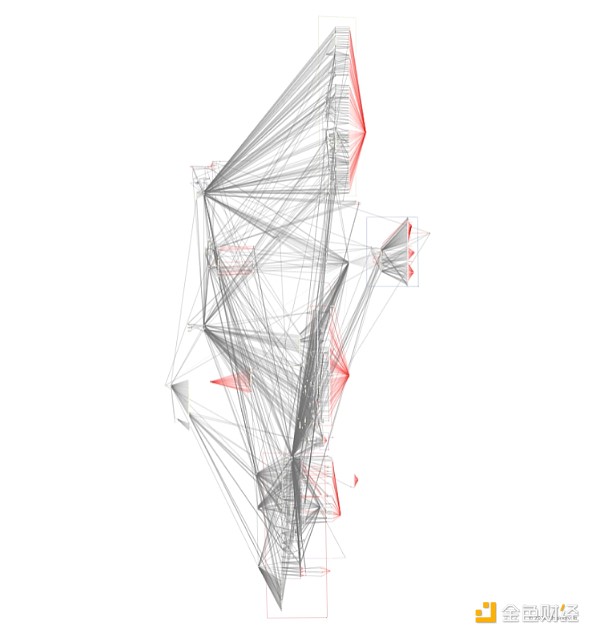
The hacker used a complex network of wallets, exchanges, and cross-chain transfers to hide the funds. Source: Chainalysis
February 21: Bybit Assures Wallets Safe, Ethena Solvent
The exchange quickly assured users that its remaining wallets were safe, and minutes after confirming the breach, the exchange announced that "all other Bybit cold wallets remain completely secure. All customer funds are safe and our operations are continuing as usual without any interruption."
Hours after the hack, customer withdrawals remained open. Zhou stated during a Q&A session that the exchange had approved and processed 70% of withdrawal requests at the time.
Decentralized finance platform Ethena told users that its yield stablecoin USDe remained solvent following the hack. The platform reportedly had $30 million in financial derivatives exposure on Bybit but was able to cover the losses through its reserve fund.
February 22: Crypto Industry Reaches a Hand to Bybit, Hacker Blacklisted
Many crypto exchanges reached out to help Bybit. Bitget CEO Gracy Chen announced that her exchange had loaned Bybit about 40,000 ETH (about $95 million at the time).
Crypto.com CEO Kris Marszalek said he would instruct the company's security team to help.
Other exchanges and institutions began freezing funds related to the hack. Tether CEO Paolo Ardoino posted on X that the company had frozen 181,000 USDt related to the hack. Polygon CISO Mudit Gupta said the Mantle team had recovered about $43 million in funds from the hackers.
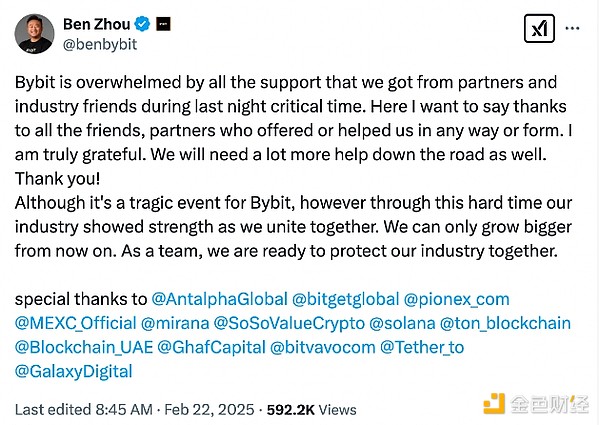
Zhou published a thank you note on X, mentioning some well-known crypto companies that helped Bybit, including Bitget, Galaxy Digital, TON Foundation, and Tether.
Bybit also announced a bounty program with rewards of up to 10% of recovered funds, with a total bonus of up to $140 million.
February 22: Withdrawal run, Lazarus transfers funds
After the incident, user withdrawals caused the exchange's total asset value to drop by more than $5.3 billion.
Despite the run on withdrawals, the exchange is keeping withdrawal requests open, albeit with delays, and Bybit’s independent Proof of Reserves auditor Hacken confirmed that reserves still exceed liabilities.
Meanwhile, blockchain traces show that Lazarus continues to split funds into intermediary wallets, further obfuscating the movement of funds.
For example, blockchain analytics firm Lookonchain said Lazarus has moved 10,000 ETH, worth nearly $30 million, to a wallet called “Bybit Exploiter 54” to begin laundering funds.
Blockchain security firm Elliptic wrote that the funds were likely moved to a mixer (a service that hides links between blockchain transactions), though “this may be challenging due to the sheer volume of stolen assets.”
February 23: eXch, Bybit continue to recover funds, blacklist grows
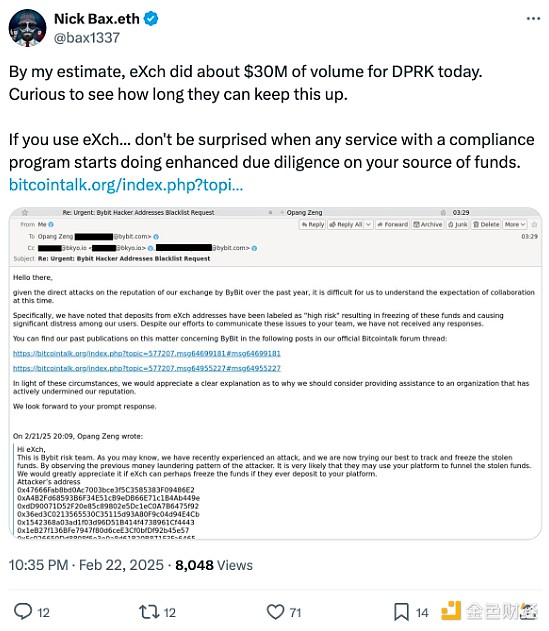
Blockchain analysts ZachXBT and Nick Bax both claim that hackers were able to launder funds on non-know-your-customer cryptocurrency exchange eXch. ZachXBT claims that eXch laundered $35 million and then accidentally sent 34 ETH to another exchange’s hot wallet.
EXch denied laundering money for North Korea, but admitted to processing "a small portion of the funds from the ByBit hack."
eXch said the funds "ended up in our address 0xf1da173228fcf015f43f3ea15abbb51f0d8f1123, which is an isolated case and the only part processed by our exchange, from which we will collect fees for the public benefit."
To help identify wallets involved in the incident, Bybit released a blacklist wallet application programming interface (API). The exchange said the tool will help white hat hackers implement the above-mentioned bounty program.
Bybit also managed to restore its Ethereum reserves to nearly half of what they were before the hack, mostly through spot purchases on OTC exchanges after the incident, but also including Ethereum borrowed from other exchanges.
February 24: Lazarus appears on DEX, Bybit fills ETH gap
Blockchain sleuths continue to monitor Lazarus-related fund flows. Arkham Intelligence observed addresses associated with the hacker on decentralized exchanges (DEXs) attempting to trade the stolen cryptocurrency for Dai.
A wallet that received part of the stolen ETH from Bybit reportedly interacted with Sky Protocol, Uniswap, and OKX DEXs. According to trading platform LMK, the hacker successfully exchanged at least $3.64 million.
Unlike other stablecoins like USDT and USDC, Dai cannot be frozen.
Zhou announced that Bybit had “fully covered the ETH gap” — that is, replenished the $1.4 billion in Ethereum lost in the hack. His statement was followed by a third-party proof of reserves report.
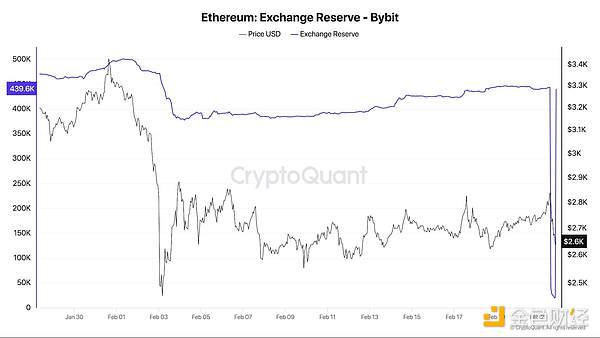
Bybit restored its Ether reserves to pre-hack levels. Source: Darkfost
February 25: The Battle Against Lazarus
Bybit launched a dedicated website to publicize its recovery efforts, which Zhou promoted while calling on the crypto community to unite against the Lazarus Group. The website distinguishes between those who offered to help and those who allegedly refused to cooperate.
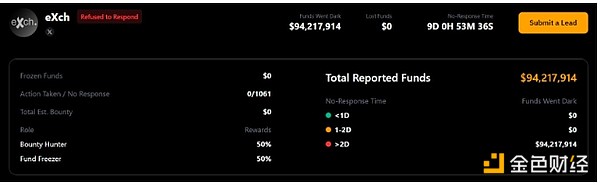
Nearly $95 million in funds were reportedly transferred to eXch. Source: LazarusBounty
The report highlights individuals and entities that assisted in freezing the stolen funds, awarding them a 10% bounty, split equally between the tipster and the entity that froze the funds.
The report also states that eXch was the only platform to refuse to help, claiming it ignored 1,061 tips.
February 26: FBI Confirms Reports of Lazarus and Safe Hacks
The U.S. Federal Bureau of Investigation (FBI) has confirmed widely reported suspicions that North Korean hackers carried out the Bybit exploit, naming the TraderTraitor organization, better known in cybersecurity circles as the Lazarus Group.
In a public service announcement, the FBI urged the private sector, including node operators, exchanges, and bridges, to block transactions from addresses associated with Lazarus.
The FBI identified 51 suspected blockchain addresses linked to the hack, while cybersecurity firm Elliptic identified more than 11,000 intermediaries.
Meanwhile, post-hacking investigations found that compromised SafeWallet credentials led to the exploit, rather than through Bybit’s infrastructure as previously reported.
February 27: THORChain transaction volume explodes
Security firm TRM Labs called the speed at which the Bybit hackers laundered funds “particularly concerning,” reporting that as of February 26, the hackers had moved more than $400 million through intermediary wallets, cryptocurrency exchanges, cross-chain bridges, and DEXs. TRM also noted that most of the stolen proceeds were converted to Bitcoin, a tactic commonly associated with Lazarus. Most of the converted Bitcoin remains stored where it was.
Meanwhile, Arkham Intelligence discovered that Lazarus had moved at least $240 million in ETH through the troubled cross-chain protocol THORChain, converting it to Bitcoin. THORChain’s total conversion volume surged to more than $1 billion in 48 hours.
After a vote to block transactions linked to North Korean hackers was overturned, THORChain developer “Pluto” announced his immediate exit from the project. Meanwhile, Lookonchain reports that the hackers have laundered 54% of the stolen funds.
What the Bybit hack means for crypto
Bybit may have been able to fully recover its lost reserves, but the incident raises larger questions about the blockchain industry and how to respond to hacks.
Ethereum developer Tim Beiko quickly dismissed calls to roll back the Ethereum network to refund Bybit. He said the hack was fundamentally different from previous incidents, adding that “the interconnected nature of Ethereum and the settlement of on-chain <>off-chain economic transactions makes this a difficult problem today.”
The fallout from the Bybit breach suggests that the Lazarus Group has become more efficient at moving blockchain-based funds. TRM Labs investigators suspect this could indicate improvements in North Korea’s crypto infrastructure or an increased ability for underground financial networks to absorb illicit funds.
As the value locked in blockchain platforms continues to grow, so too does the sophistication of attacks. The industry remains a prime target for North Korean state hackers, who reportedly use its revenue to fund their weapons programs.
 Alex
Alex
 Alex
Alex Kikyo
Kikyo Brian
Brian Alex
Alex Alex
Alex Joy
Joy Brian
Brian Alex
Alex Joy
Joy Edmund
Edmund