Deng Tong, Golden Finance
On October 28, 2025, the GoPlus Chinese community issued a security alert: the x402 cross-chain protocol @402bridge was suspected of being hacked, resulting in the loss of USDC assets for over 200 users.
This article reviews the 402Bridge cross-chain protocol theft incident, official and multi-party responses, and analyzes the cause of the theft, as well as other cases of hacker attacks resulting from private key leaks.
I. Theft Incident Restoration and Official and Multi-Party Responses from 402Bridge
In the early morning hours, the official 402Bridge account posted: "According to community feedback, a token theft has occurred. Our technical team is currently investigating the entire process. All users are advised to immediately revoke all existing authorizations and transfer assets out of their wallets as soon as possible."
Subsequently, the official statement continued: The x402 mechanism requires users to sign or approve transactions through the web interface before sending them to the backend server." The backend server extracts funds and performs the minting, ultimately returning the results to the user. When we join https://x402scan.com, we need to store our private key on the server in order to call contract methods. This step may expose administrator privileges, as the administrator's private key is connected to the internet at this stage, potentially leading to privilege leaks. If hackers obtain the private key, they can take over these privileges and reallocate user funds to carry out attacks. We are still investigating the specific details of the attack.
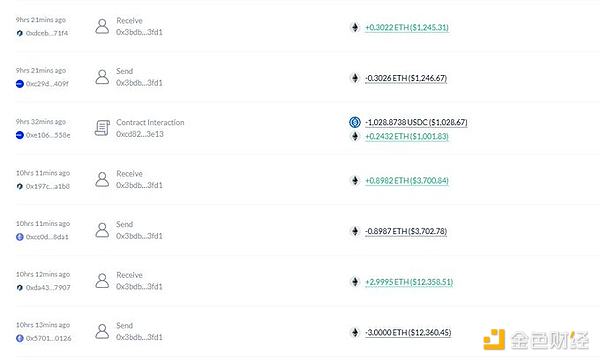
Two hours ago, officials stated: Due to this private key leak, more than a dozen of the team's test wallets and main wallets were also compromised (as shown in the figure below). We have immediately reported the matter to law enforcement and will keep the community informed of the latest developments. The GoPlus Chinese community restored the theft: The Creator of the contract 0xed1AFc4DCfb39b9ab9d67f3f7f7d02803cEA9FC5 transferred the Owner to 0x2b8F95560b5f1d1a439dd4d150b28FAE2B6B361F, and then the new Owner called the transferUserToken method in the contract to transfer the remaining USDC in all authorized user wallets. Before minting, USDC must be authorized to the @402bridge contract. As a result, more than 200 users had their remaining USDC transferred away due to excessive authorization. 0x2b8F95560b5f1d1a439dd4d150b28FAE2B6B361F transferred a total of 17,693 USDC to users. The USDC was then exchanged for ETH and transferred to Arbitrum through multiple cross-chain transactions.
GoPlus Security Recommendations:
1. Users who have participated in this project, please cancel the relevant authorization (0xed1AFc4DCfb39b9ab9d67f3f7f7d02803cEA9FC5) as soon as possible;
2. Before authorization, check whether the authorization address is the official address of the interactive project;
3. Only authorize the required number, and do not authorize unlimitedly;
4. Check authorization regularly and cancel useless authorizations. X user @EamonSol posted: Many current x402s actually deploy a service at http://x402scan.com, which forwards on-chain interactions to the project's server. The project then interacts with the chain to distribute tokens. This process requires the private key of the on-chain contract to be stored on the server. Once the project's server is compromised, all addresses related to the contract will be exposed. X user @fenzlabs pointed out: This case highlights the dangers of unlimited token approval. Wallets and AI agents need stricter restrictions and better monitoring to prevent these rapid thefts. Never blindly trust new contracts - always check carefully before signing!
II. Cause of the Theft
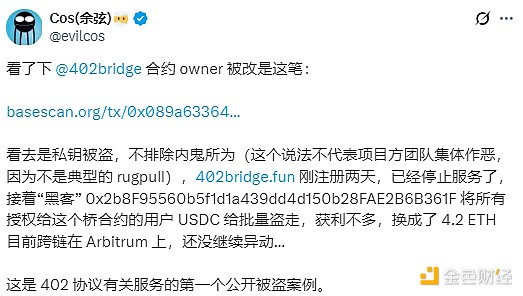
According to SlowMist Yusin's analysis, the attack on the cross-chain bridge project 402Bridge stemmed from a private key leak, and the possibility of insider involvement cannot be ruled out. The 402bridge.fun domain name ceased service after only two days of registration, and no further movement of the stolen funds has been observed. This is the first public security incident involving 402 Protocol services. SlowMist Yusin stated that this incident was not a typical case of collective malicious activity by the project's members.
"Not a collective malicious act by the project's members" means the attack was more likely the result of a failure in internal security controls or a targeted infiltration by external hackers, rather than deliberate fraud by the project's members.
III. Are there other cases of private key leaks leading to hacker attacks?
1. Nomad
In August 2022, Nomad Bridge was hacked, and almost all of the $200 million in funds on the cross-chain bridge were stolen. After the hack, Moonbeam blocked anyone from trading or interacting with the smart contract. The core cause of the attack was an error in the contract verification mechanism, which allowed private keys or permission signature logic to be easily forged.
2. Ankr
In December 2022, the Ankr node private key was leaked, allowing attackers to forge contracts and mint unlimited aBNBc tokens, resulting in approximately $5 million in losses. Ankr's response: restoring security and cooperating with DEXs to halt trading; developing and implementing a comprehensive compensation plan for the community; and locating the attack as a former employee. Ankr officially confirmed the hack was caused by the theft of deployment keys.
3. Platypus Finance
In February 2023, attackers exploited a vulnerability in the administrator's private key to attack a stablecoin pool, stealing approximately $9 million in USDC. The team subsequently recovered some of the assets and stated that "the development private key may have been compromised." 4. Multichain In July 2023, members of the Multichain core team disappeared, and the project's primary private key was suspected to be in the hands of a single individual. Approximately $126 million in assets were subsequently transferred, making this one of the largest permission-based attacks in the history of cross-chain bridges. 5. Exactly Protocol In April 2024, attackers exploited a leaked deployment private key from a front-end server to replace a contract and steal approximately $7.3 million. This incident exposed widespread industry issues regarding weak private key custody and DevOps process security. 6. UXLINK In September 2025, security company Cyvers' systems detected suspicious transactions involving $11.3 million in UXLINK, ultimately confirming the theft. SlowMist Yuxian noted that several private keys related to UXLINK's Safe multi-signature were likely compromised. The theft of UXLINK directly caused the price of UXLINK tokens to plummet by more than 70%.
 Xu Lin
Xu Lin







