Author: Spirit, Golden Finance
"Transaction History Record Pollution Attack" is an emerging attack method in the crypto industry. Although a fully standardized definition has not yet been formed, its core is to mislead users or systems by polluting or forging transaction records on the blockchain, thereby achieving illegal profits. With the popularization of blockchain technology and the surge in the value of crypto assets, this attack has gradually attracted attention.
1. Causes of "Transaction History Record Pollution Attack"
1.1 Transparency and immutability of blockchain
The openness and immutability of blockchain are its core advantages, but they also provide opportunities for pollution attacks. All transaction records are permanently stored and traceable. Attackers can pollute users' transaction history records by sending a large number of forged or misleading transactions. For example, through a "dust attack", attackers send trace amounts of cryptocurrency to a large number of addresses to confuse normal transaction records and increase the difficulty of analysis.
1.2 Vulnerabilities in user operation habits
Crypto users often rely on wallet interfaces or transaction history records to perform operations, such as copying addresses or verifying transactions. Attackers take advantage of this habit and mix fake addresses into users' history records by disguising legitimate transactions. For example, on March 18, a user transferred $103,100 to a fraudulent address by copying the wrong address in the contaminated history.
1.3 Economic motivation
The speculation and high returns of the crypto industry attract hackers and scammers. Contaminated transaction history can be used for phishing attacks, market manipulation, or to conceal the flow of funds. For example, attackers may forge transaction records to induce users to transfer to fake addresses, or conceal the true source of illegal funds to avoid on-chain tracking.
1.4 Lower technical threshold
Generative AI (such as FraudGPT) and automated tools have lowered the threshold for attacks. Attackers can easily generate fake transactions or send polluted data in batches to amplify the scale of attacks. According to the "China Enterprise Ransomware Attack Situation Analysis Report", the ransomware attack payload increased by 57.5% year-on-year, showing how technological progress has helped crypto crimes.
II. Development Trend: From Secret to Scale
2.1 From Single Attack to Combined Threat
Early pollution attacks were mainly "dust attacks", which were small and secretive. However, as the encryption ecosystem becomes more complex, attacks are evolving towards combination. For example, polluted transaction history may be combined with phishing websites, social engineering or malware to further increase the success rate.
2.2 Deep integration of AI and automation
By 2025, AI-driven attack tools (such as WormGPT) are expected to become more common. Attackers can use AI to generate realistic fake transactions, simulate user behavior, and even predict the target's operating habits. "Five Major Trends in Cybersecurity Predictions for 2025" (Security Insider) pointed out that AI abuse will make attacks more precise and covert.
2.3 Cross-chain and L2 network expansion
With the popularity of Bitcoin Layer 2 (such as Lightning Network) and cross-chain bridges (such as BitVM), pollution attacks may expand from a single chain to a multi-chain environment. Attackers may take advantage of the complexity of cross-chain transactions, pollute bridge records, and interfere with the transparency of asset transfers.
2.4 Intensified regulation and countermeasures
Strengthening global regulation (such as EU MiCA and US SEC new regulations) will force attackers to find more covert ways. Polluting transaction history may become a new means to circumvent KYC/AML tracking. At the same time, countermeasures (such as on-chain analysis tools) will also be upgraded.
III. Analysis of attack scenarios and links
3.1 Typical scenarios
Phishing transfer misleading Link: The attacker sends a small amount of tokens (such as 0.0001 BTC) to the target wallet, with a fake address disguised as a legitimate source. When the user makes a subsequent transfer, he mistakenly copies this address from the historical record.
Case: According to the monitoring of ScamSniffer (@realScamSniffer), an on-chain security analyst, about 7 hours ago, a user transferred $103,100 to a fraudulent address by copying the wrong address from the contaminated transfer history. In addition, about 14 hours ago, another user lost $43,674 in the same way.
Upgraded version of dust attack
Link: Send trace amounts of tokens to a large number of addresses to confuse transaction history, cover up the flow of illegal funds, or induce user interaction (such as clicking on malicious links to receive "airdrops").
Case: In the zkSync incident in 2023, dust attacks were used to create chaos.
Cross-chain bridge pollution
Link: The attacker inserts forged records in the cross-chain bridge transaction, interferes with the bridge status verification, and induces users or protocols to misjudge the balance.
3.2 Attack Link
Preparation phase: Analyze the target wallet address and generate similar or disguised addresses.
Pollution phase: Inject false data into the target transaction history through small transactions or malicious scripts.
Execution phase: Wait for user misoperation (such as copying the wrong address) or system misjudgment.
Profit phase: Transfer assets, or use confusion to cover up other attacks (such as money laundering).
Fourth, data trends: scale and losses are rising
4.1 Attack frequency and scale
According to Beosin's "2024 Web3 Blockchain Security Situation Report", the global crypto security incident losses in 2024 exceeded US$2.5 billion, a year-on-year increase of about 24.42%. Although pollution attacks are not counted separately, "dust attack" related incidents account for about 15% of phishing attacks.
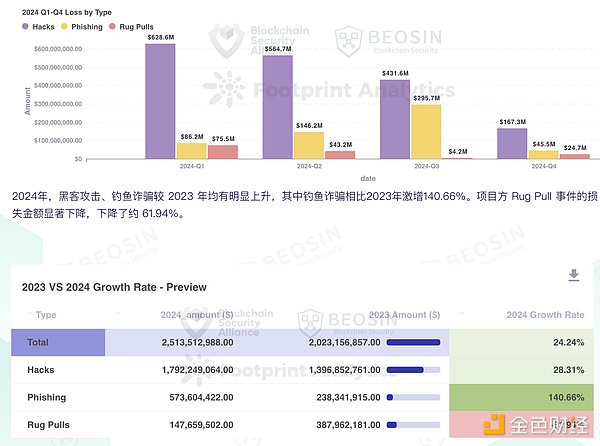
The "2025 Five Major Trends in Cybersecurity Forecast" predicts that global cybercrime losses will exceed $12 trillion in 2025, and the crypto industry will be the first to bear the brunt due to its digital nature.
4.2 Amount of loss
The loss of a single pollution attack ranges from thousands of dollars to hundreds of thousands of dollars. Cross-chain bridge attacks (such as a DeFi platform that lost $150 million in 2023) show that pollution combined with other vulnerabilities can cause greater damage.
4.3 Distribution of victims
Data shows that retail users are more vulnerable to contamination attacks due to their lack of security awareness, accounting for about 70%; institutional users (exchanges, custody platforms) have also become key targets due to their concentrated assets.
V. Preventive measures: both technology and awareness
5.1 User-level protection
Verify the source of the address: manually check the address before each transfer to avoid directly copying historical records.
Use a multi-signature wallet: increase the transaction confirmation link to reduce the risk of mistransfer.
Be wary of small transfers: avoid interacting or clicking on related links when receiving trace tokens from unknown sources.
5.2 Technical improvements
Wallet filtering mechanism: Develop intelligent filtering functions to mark suspicious transactions or addresses. For example, MetaMask can prompt "potential phishing addresses".
On-chain analysis tools: Use tools such as Chainalysis or Elliptic to detect contaminated transaction patterns in real time.
5.3 Industry and regulatory collaboration
Education and popularization: Exchanges and communities should strengthen user security education and promote the habit of "cold storage".
Regulatory sandbox: The government can test new technologies (such as AI countermeasures tools) through sandboxes to accelerate defense deployment.
Sharing threat intelligence: Industry alliances (such as Crypto ISAC) can share contaminated attack data to improve overall protection capabilities.
VI. Future Outlook: Challenges in 2025
6.1 Challenges
Intelligent attacks: Forged transactions generated by AI will be more difficult to identify, and may be combined with deep fake technology to amplify the impact.
Ecological complexity: The popularity of cross-chain and L2 will increase the potential entry point for pollution attacks.
Regulatory lag: The global legal framework may not keep up with the speed of attack evolution, resulting in a longer vulnerability window.
6.2 Response
Technical countermeasures: Zero-knowledge proof (ZKP) and modular blockchains can improve transaction privacy and verification efficiency and reduce pollution space.
Community awakening: Improved user security awareness will reduce the success rate of attacks.
VII. Conclusion
"Transaction history pollution attacks" originate from blockchain transparency, user habit loopholes and economic motivations. Their scale and complexity are expected to increase significantly in 2025. From phishing misleading to cross-chain pollution, the attack scenarios are diverse, and data trends show that both losses and frequency are rising. Prevention requires a three-pronged approach from user habits, technology upgrades and industry collaboration. Facing the future, the crypto industry needs to find a balance between innovation and security to deal with this hidden and dangerous threat.
 Kikyo
Kikyo






