Today, the popular Binance Alpha series of tokens received a cold shoulder. GriffinAI, a Web3 AI project that debuted on Binance Alpha last night, was targeted with a malicious issuance of 5 billion GAIN tokens just 12 hours after its launch. This incident caused the token's price to plummet over 97% in an hour, reaching a low of $0.004185 on Binance. At press time, GAIN was trading around $0.0195. Interestingly, according to Ai Yi's monitoring, the address starting with 0x951 purchased $20,200 worth of GAIN at an average price of $0.00625, near its lowest point, generating a profit of $107,000 within an hour. During the same period, a slight rebound in GAIN's price also indicates that many community investors chose to buy at the bottom. Regarding this phenomenon, crypto influencer "Marktowin" posted on Binance Square, stating that the project had abandoned the project and that those who bought at the bottom would be buried, and that its lifespan would be less than 24 hours.
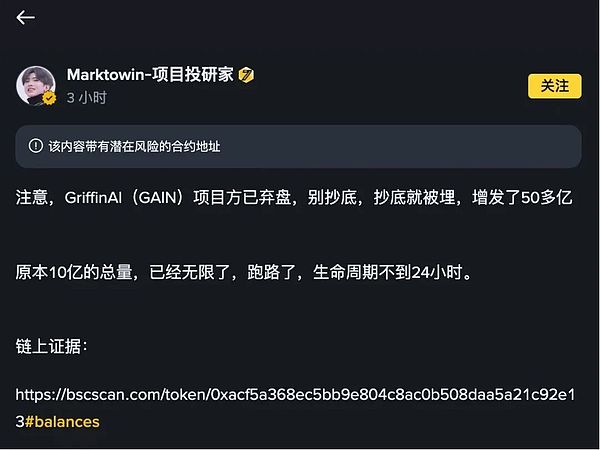
As soon as this statement came out, the GriffinAI project, which was already under scrutiny from the community, was pushed to the forefront of public opinion. So the question is, was the malicious issuance of GriffinAI tokens the result of a hacker attack, or was it malicious behavior by the project?
Let's first review the background of the project and the ins and outs of the incident.
GriffinAI is a decentralized platform that combines artificial intelligence with DeFi automation, providing real-time data, multi-agent workflows, and full on-chain deployment across major blockchains and wallets. The platform has two core products: Agent Builder and Agent Playground. Agent Builder allows users to create, customize, and deploy AI-powered trading and DeFi agents without writing code; Agent Playground allows users to test, optimize, and run their agents in real-world market environments. According to the official website, over 250,000 users have built over 15,000 agents using GriffinAI. On September 22nd, Binance Alpha announced the launch of GriffinAI's token, GAIN, on September 24th. Subsequently, Huobi HTX also announced that it would simultaneously list GAIN at 7:00 PM on September 24th, launching isolated margin trading of GAIN/USDT with up to 10x leverage. The listings on these two exchanges and the airdrop event attracted significant attention to the project. Since its launch, GAIN has lived up to expectations, reaching a high of $0.2764 before stabilizing around $0.16. However, beneath this seemingly stable surface, undercurrents are surging. Aiyi's monitoring revealed that a malicious issuance and dumping address beginning with 0xf3d was created 13 hours ago (around 10 PM yesterday). This address funded its operations by collecting ETH through Tornado and converting it to BNB across chains. This morning around 7 AM, shortly after issuing 5 billion tokens, this address began a frenzied market dump, which lasted for 55 minutes and netted a profit of $3.01 million. The address subsequently used deBridge to transfer profits across multiple networks, including Solana, Ethereum, Base, and Arbitrum. GAIN's original fixed total supply was 1 billion. As of press time, the issuance of additional GAIN has reached approximately 5.298 billion. The largest holding address holds 4.852 billion GAIN, representing 91.58% of the total supply, and continues to transfer GAIN to the PancakeSwap V3 pool. Furthermore, according to Ember monitoring, the GriffinAI issuance address has converted 2,955 BNB tokens, received from the sale of 150 million GAIN tokens, into ETH across chains, valued at approximately $3 million. SlowMist's Chief Information Security Officer, 23pds, noted that GriffinAI's additional issuance address had begun transferring ETH to Tornado Cash. It's important to note that once funds enter Tornado Cash, recovering them becomes extremely difficult. Four hours later, GriffinAI officially released a statement explaining the attack: the attacker introduced an unauthorized LayerZero peer setup, initialized an additional LayerZero peer on Ethereum, and deployed a fake Ethereum contract, TTTTT (address 0x7a8caf). The attacker then exploited this misconfigured peer to bypass cross-chain verification and mint 5 billion GAIN on BSC. The tokens involved in the cross-chain transaction did not originate from GAIN's official Ethereum address (0xccdbb9). As of press time, GriffinAI has taken a series of emergency measures in response to the malicious issuance incident: They have officially requested that all exchanges suspend GAIN trading and deposit/withdrawal services on BNB Chain to disrupt the attacker's trading operations; they have also removed GAIN's official liquidity on BNB Chain and emphasized that GAIN on Ethereum was unaffected by the incident. This official announcement from GriffinAI alone has failed to quell the anger of community investors. Eight hours have passed since the incident, and officials have yet to provide a concrete solution, such as a recovery plan or token contract migration plan. This delay has seemingly exacerbated community suspicions, with many suspecting the team is planning to abscond. "They created a hacked wallet and pretended it was an attack, but it was actually an inside job." Many in the community believe the so-called "hacker attack" was a self-directed drama staged by the project, with insiders stealing the information. As Web3 security infrastructure GoPlus previously pointed out in its analysis of the incident, the attacker may have been an insider or had socially engineered project members. Meanwhile, many investors have pointed the finger at Binance Alpha, hoping it will provide a reasonable explanation. However, Binance has not issued any further response to the matter, aside from the proactive measure of canceling the 4x Alpha trading volume bonus for GAIN tokens. This stance has led more investors to question Binance's ability to audit projects. In fact, not long ago, MYX, once a star project on Binance Alpha and known as the "100x Coin," was embroiled in controversy surrounding the largest airdrop Sybil scam in history. The MYX team was revealed to have direct ties to a wallet that received $170 million in funds from its airdrop, suspected to be an insider operation. This caused the token's price to plummet 38% within 13 hours. This series of incidents has undoubtedly undermined some users' trust in Binance Alpha. As for GriffinAI, with early investors suffering significant losses, what can it do to restore trust?
Their top priority is to clearly state their position and work with exchanges to mark and freeze the over-issued tokens in the attacker's address to prevent further sell-offs. At the same time, they should upgrade the contract, focusing on team control and the security of the token contract, fixing the LayerZero cross-chain bridge vulnerability and redeploying the smart contract. They can also consider implementing solutions such as a 1:1 token airdrop to rebuild community trust. Following this incident, Binance Alpha also needs to strengthen its review of the project team and code to prevent such incidents from happening again.
Finally, if GriffinAI fails to properly handle this incident, it may lead to the project's "death."
 Anais
Anais






