Source: Bitrace
On February 21, 2025, the cryptocurrency exchange Bybit suffered a large-scale security breach, resulting in the theft of approximately $1.5 billion in assets from its Ethereum cold wallet. This incident is considered to be the largest single theft in the history of cryptocurrency, surpassing previous records such as Poly Network (2021, $611 million) and Ronin Network (2022, $620 million), and has had a shocking impact on the industry.
This article aims to introduce the hacking incident and its fund laundering methods, and warns that in the next few months, there will be a large-scale freeze wave against OTC groups and Crypto payment companies.
Theft process
According to Bybit Ben Zhou's description and Bitrace's preliminary investigation, the theft process is as follows:
Attack preparation: The hacker deployed a malicious smart contract (address: 0xbDd077f651EBe7f7b3cE16fe5F2b025BE2969516) at least three days before the incident (i.e. February 19), laying the groundwork for subsequent attacks.
Invasion of the multi-signature system: Bybit's Ethereum cold wallet uses a multi-signature mechanism, which usually requires multiple authorized parties to sign to execute transactions. The hacker hacked into the computer that manages the multi-signature wallet through unknown means, possibly through a disguised interface or malware.
Disguised transaction: On February 21, Bybit planned to transfer ETH from the cold wallet to the hot wallet to meet daily transaction needs. The hacker took advantage of this opportunity to disguise the transaction interface as normal operation, inducing the signer to confirm a seemingly legitimate transaction. However, the signature actually executed an instruction to change the logic of the cold wallet smart contract.
Fund transfer: After the instruction came into effect, the hacker quickly took control of the cold wallet and transferred ETH and ETH pledge certificates worth about $1.5 billion at the time to an unknown address (initial tracking address: 0x47666Fab8bd0Ac7003bce3f5C3585383F09486E2). Subsequently, the funds were dispersed to multiple wallets and the money laundering process began.
Money laundering techniques
The laundering of funds can be roughly divided into two stages:
The first stage is the early fund splitting stage, in which the attacker quickly exchanged ETH pledge certificate tokens for ETH tokens instead of stablecoins that may be frozen, and then strictly split the ETH and transferred it to the lower-level addresses in preparation for laundering.
It was at this stage that the attacker’s attempt to convert 15,000 mETH into ETH was stopped, and the industry recovered this part of the loss.
The second stage is the fund laundering. The attacker will transfer the acquired ETH through centralized or decentralized industry infrastructure, including Chainflip, Thorchain, Uniswap, eXch, etc. Some protocols are used for fund exchange, while some protocols are used for cross-chain fund transfer.
So far, a large amount of stolen funds have been converted into layer1 tokens such as BTC, DOGE, SOL, and even memecoin has been issued or funds have been transferred to exchange addresses for fund confusion.
Bitrace is monitoring and tracking the addresses related to the stolen funds. This part of the threat information will be pushed synchronously in BitracePro and Detrust to prevent users from accidentally receiving the stolen funds.
Prior Record Analysis
Analysis of 0x457 in the fund link found that the address was related to the theft of BingX exchange in October 2024 and the theft of Phemex exchange in January 2025, indicating that the mastermind behind these three attacks is the same entity.
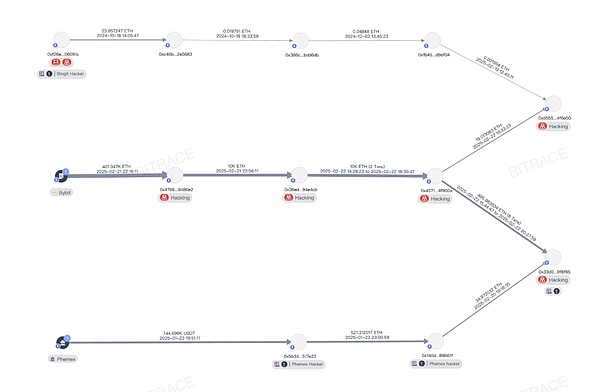
Combined with its highly industrialized fund laundering techniques and attack methods, some blockchain security practitioners attributed this incident to the notorious hacker group Lazarus, which has launched multiple cyber attacks on institutions or infrastructure in the Crypto industry over the past few years and illegally seized billions of dollars worth of cryptocurrencies.
Freezing Crisis
In the past few years of investigation, Bitrace found that in addition to using unlicensed industry infrastructure for fund laundering, the organization also used centralized platforms for dumping, which directly led to a large number of exchange user accounts that intentionally or unintentionally received stolen money being controlled, and the business addresses of OTC merchants and payment institutions were frozen by Tether.
In 2024, the Japanese cryptocurrency exchange DMM was attacked by Lazarus, and Bitcoin worth up to $600 million was illegally transferred. Among them, the attacker bridged the funds to HuionePay, a cryptocurrency payment institution in Southeast Asia, causing the latter's hot wallet address to be frozen by Tether, and more than 29 million US dollars were locked and could not be transferred;
In 2023, Poloniex was attacked, and the attacker was suspected to be the Lazarus Group, and more than 100 million US dollars were illegally transferred. Some of the funds were laundered through over-the-counter transactions, resulting in the freezing of a large number of OTC business addresses, or the risk control of exchange accounts used to store business funds, which had a huge impact on business activities.
Summary
Frequent hacker attacks have caused huge losses to our industry, and subsequent fund laundering activities have also contaminated more personal and institutional addresses. For these innocent people and potential victims, they should pay more attention to these threatening funds in their business activities to prevent themselves from being affected.
This also sounded the alarm for us. It is time to pay attention to Crypto anti-money laundering awareness and KYT procedures.






