Initial access (phishing emails, vulnerability exploits, weak RDP passwords)
Lateral movement (Mimikatz, Cobalt Strike, etc.)
Privilege escalation
="">Data theft
File encryption
Pop-up ransom note
Publish information to leak sites (if no payment is made)
LockBit has caused many sensational incidents during its active period:
In 2022, it attacked the Italian tax bureau, affecting the data of millions of taxpayers;
Once claimed to have hacked into the SickKids hospital in Canada, then apologized and provided a decryptor;
Multiple manufacturers (such as defense and medical equipment companies) were encrypted by LockBit;
In 2022, it attacked the Italian tax bureau, affecting the data of millions of taxpayers;
Once claimed to have hacked into the SickKids hospital in Canada, then apologized and provided a decryptor;
Multiple manufacturers (such as defense and medical equipment companies) were encrypted by LockBit;
In the second quarter of 2020, it accounted for more than 40% of global ransomware attacks;
It has cumulatively affected more than 1,000 companies, far exceeding old gangs such as Conti and REvil;
It has a very high success rate in ransomware, and more than half of the $100 million ransom it proposed in 2022 was successfully received.
However, even a strong one like LockBit is not invulnerable. On February 19, 2024, the LockBit website was seized in a joint law enforcement operation by the UK National Crime Agency, the US Federal Bureau of Investigation, Europol and the International Police Agency Alliance. Several LockBit members were arrested or wanted, but the core development team has not been completely disintegrated. Some samples are still circulating on the dark web and are still being used by branch groups.
Breaking news: LockBit site hacked
Today, SlowMist received intelligence: LockBit's onion site was hacked. The attacker not only took over its control panel, but also released a package file containing the database, which led to the leakage of LockBit's database, including sensitive information such as Bitcoin addresses, private keys, chat records, and its affiliated companies.
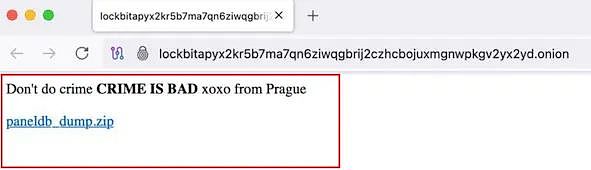
What is even more dramatic is that the hacker left a meaningful message on the tampered site: "Don't commit a crime, crime is bad, from Prague."
Soon after, the relevant data was uploaded to platforms such as GitHub and quickly spread.
LockBit officials subsequently responded in Russian on their channel, which roughly means as follows:

Rey: LockBit was hacked? Any progress?
LockBitSupp: Only a lightweight control panel with authorization codes was compromised, no decryptors were stolen, and no company data was compromised.
Rey: Yes, but this means that Bitcoin addresses, conversations, keys, etc. were leaked... This will also affect reputation, right?
Rey: Was Locker Builder or source code stolen?
Rey:Will you guys get back online? If so, how long will it take?
LockBitSupp:Only the bitcoin addresses and conversations were stolen, no decryptor was stolen. Yes, it does affect reputation, but so does getting back online after a fix. The source code was not stolen. We are already working on recovery.
Rey:Okay, good luck to you guys. Thanks for your answer.
Leak Analysis
SlowMist downloaded the relevant leaked files as soon as possible (for internal research purposes only, the backup has been deleted in time). We conducted a preliminary analysis of the directory structure, code files and database contents, trying to restore the architecture of LockBit's internal operating platform and its functional components.
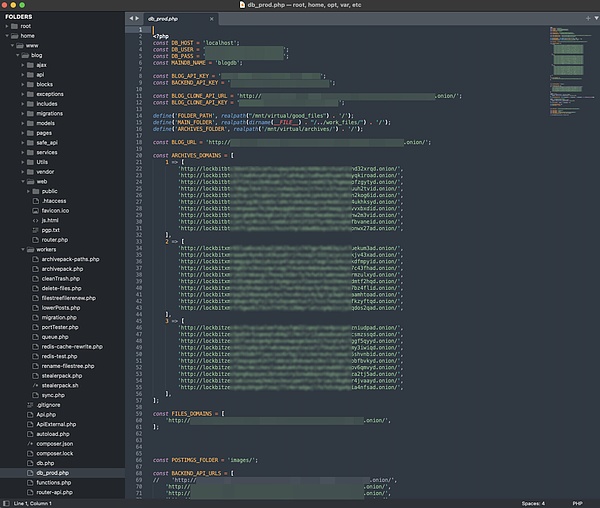
From the directory structure, this looks like a LockBit victim management platform written in a lightweight PHP architecture.
Directory structure analysis:
api/, ajax/, services/, models/, workers/ show that the project has a certain degree of modularity, but does not conform to the structure agreed upon by frameworks such as Laravel (such as app/Http/Controllers);
DB.php, prodDB.php, autoload.php, functions.php indicate that the database and function boot are manually managed;
left;">vendor/ + composer.json uses Composer, which means that a third-party library may be introduced, but the entire framework may be written by itself;
victim/, notifications-host/ and other folder names are suspicious (especially in security research).
So we speculate that the hacker from "Prague" may have used PHP 0 day or 1 day to hack the Web site and console.
The management console is as follows:
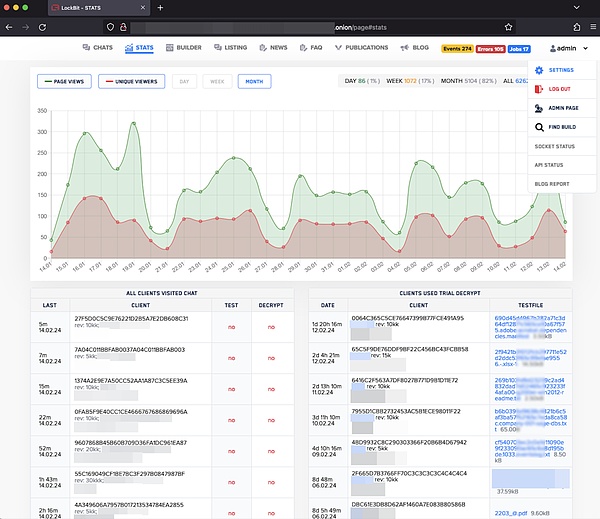
Part of the chat communication information:
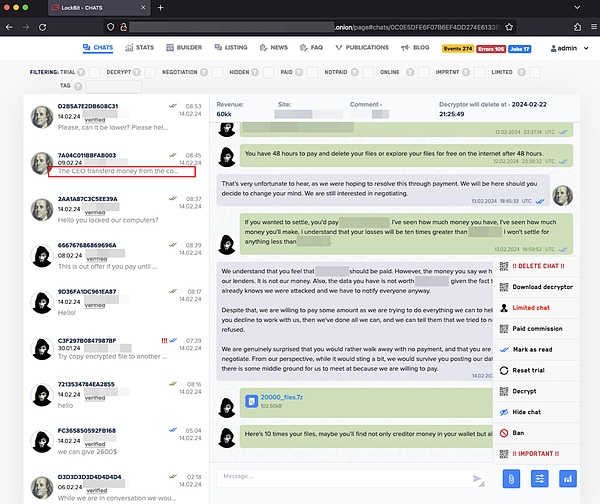
Let's take a look at the information circled in red: Victim CEO From co ... coinbase? Pay the ransom?
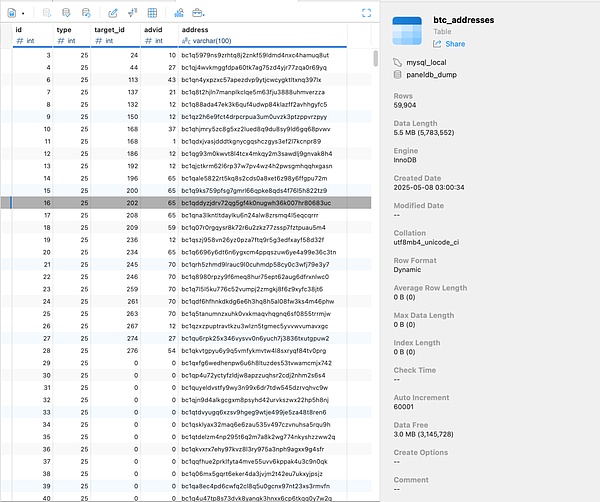
At the same time, the leaked database also involves about 60,000 BTC addresses:
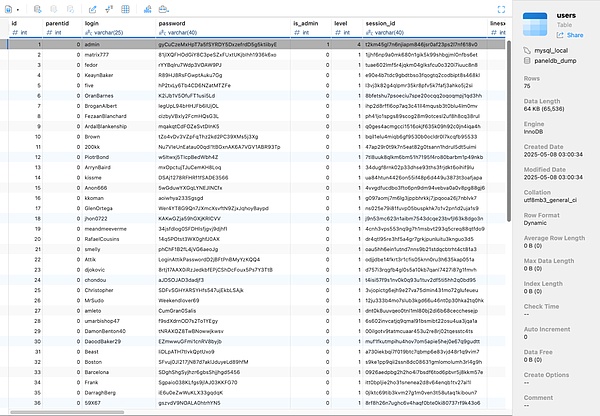
There are 75 users' account passwords in the leaked database:

Interesting bargaining chat:

Randomly find orders with successful payments:
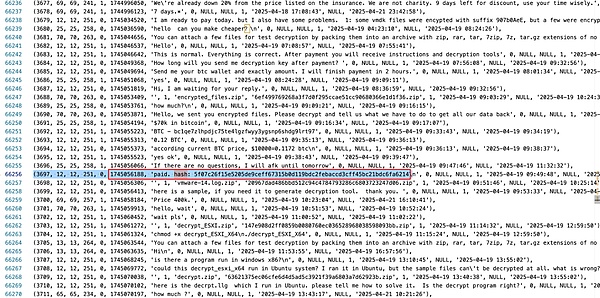
Order address:
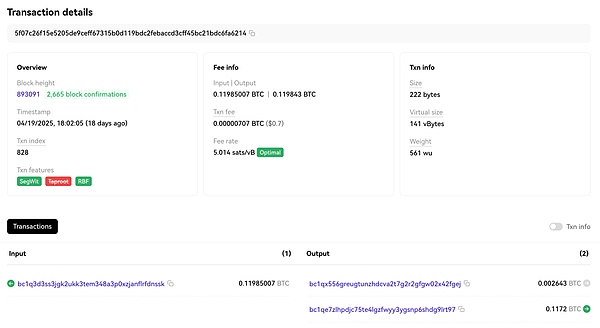
And use MistTrack to track the Bitcoin payment address:
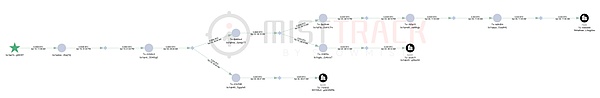
The flow of money laundering funds is relatively clear and eventually flows into the trading platform. Due to space limitations, MistTrack will conduct more analysis on cryptocurrency addresses in the future. If you are interested, you can follow X: @MistTrack_io.
At present, LockBit officials have also issued the latest statement on this incident. The rough translation is as follows:
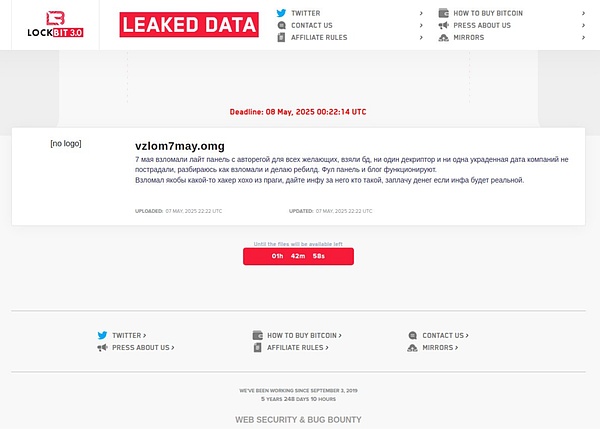
“On May 7, 2025, one of our lightweight control panels with automatic registration function was hacked, and anyone could bypass authorization and directly access the panel. The database was stolen, but no decryptor or sensitive data of the victim company was involved. We are currently investigating the specific method of intrusion and initiating the reconstruction process. The main control panel and blog are still operating normally.”
text="">"The attacker is said to be a man named 'xoxo' from Prague. If you can provide accurate information about his identity - as long as the information is reliable, I am willing to pay for it."
LockBit's response is quite ironic. Previously, the US State Department had issued a reward notice, offering a maximum reward of $10 million for the identity and location information of the core members or key collaborators of the LockBit gang; at the same time, in order to encourage the disclosure of its affiliates' attacks, a maximum reward of $5 million was provided.
Now that LockBit has been hacked, it has turned around and offered a price in the channel to find clues about the attacker - as if the "bounty hunter mechanism" has backfired on itself, which is ridiculous and further exposes the loopholes and chaos of its internal security system.
Summary
LockBit has been active since 2019 and is one of the most dangerous ransomware gangs in the world, with a cumulative ransom estimate (including undisclosed data) of at least $150 million. Its RaaS (Ransomware as a Service) model attracts a large number of franchisees to participate in attacks. Although the group was hit by law enforcement in "Operation Cronos" in early 2024, it remains active. This incident marks a major challenge to the security of LockBit's internal systems, which may affect its reputation, franchisee trust and operational stability. At the same time, it also shows the trend of "reverse attack" against cybercrime organizations in cyberspace.
SlowMist Security Team recommends all parties:
Continue intelligence monitoring: Closely track the reconstruction dynamics and potential variant versions of LockBit;
Pay attention to dark web trends: Real-time monitoring of relevant forums, sites and intelligence sources to prevent secondary leakage and data abuse;
Strengthen RaaS Threat defense: Sort out your own exposure, and strengthen the identification and blocking mechanism of the RaaS tool chain;
Improve the organization's response mechanism: If a direct or indirect connection with your own organization is found, it is recommended to immediately notify the competent authority and initiate an emergency plan;
Fund tracking and anti-fraud linkage: If a suspicious payment path is found to flow into your own platform, you should strengthen anti-money laundering prevention in combination with the on-chain monitoring system.
This incident once again reminds us that even hacker organizations with strong technical capabilities cannot be completely immune to cyber attacks. This is one of the reasons why security practitioners continue to fight.
 Alex
Alex
 Alex
Alex Aaron
Aaron Alex
Alex Joy
Joy Aaron
Aaron Brian
Brian Joy
Joy Aaron
Aaron Joy
Joy Hui Xin
Hui Xin