Author: Lyndon & Lisa
Background
On February 21, 2025, the cryptocurrency exchange Bybit suffered a large-scale hacker attack, with a total of $1.46 billion stolen, making it one of the most serious attacks on exchanges in history. According to on-chain analysis, the main way hackers launder money is to exchange ETH for BTC through THORChain. It is rumored that in just a few days, the hackers' money laundering activities brought THORChain $2.91 billion in trading volume and $3 million in handling fees. Ben Zhou, co-founder and CEO of Bybit, confirmed on March 4 that hackers exchanged a total of 361,255 ETH (about $900 million) through THORChain, accounting for 72% of the stolen funds.
This incident has once again raised attention to the decentralized cross-chain bridge (Cross-Chain Bridge). This article will explore how THORChain operates, its core components, its security mechanisms, and how to analyze the address after crossing the chain from THORChain.
What is THORChain?
THORChain is a decentralized cross-chain liquidity network built with the Cosmos SDK and operates as a first-layer cross-chain decentralized exchange (DEX), enabling users to exchange assets between different blockchains in a non-custodial manner without trusting third parties.
How it works
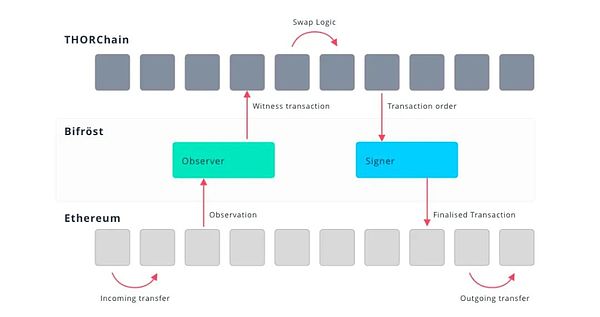
(https://docs.thorchain.org/technology/bifrost-tss-and-vaults)
Suppose Alice wants to exchange ETH for BTC, the workflow of THORChain is as follows:
User initiates cross-chain transaction:Alice sends ETH to THORChain ETH Vault, the transaction is detected by THORChain, and the exchange logic is triggered.
Cross-chain transaction execution:THORChain parses ETH transactions through Bifrost and calculates the BTC price. The AMM mechanism calculates the exchange ratio and determines how much BTC Alice will receive.
Target chain asset release:THORChain signs the transaction on the BTC network through the TSS (Threshold Signature) mechanism and sends BTC to the address specified by Alice.
The entire process is completely decentralized and does not require a third party.
Core Components
RUNE Token and Economic Model:RUNE is the native token of THORChain, which is mainly used to provide liquidity, ensure security, manage governance and provide reward mechanisms. THORChain adopts a slippage-based fee model (CLP), that is, transaction fees are linked to transaction slippage, and will be dynamically adjusted according to the liquidity demand of the transaction pair (paired with RUNE), which is one of the core designs of THORChain's unique automatic market maker (AMM).
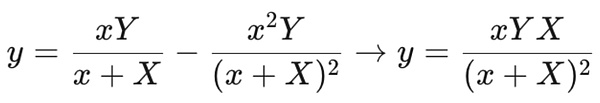
(https://docs.thorchain.org/thorchain-finance/continuous-liquidity-pools)
Cross-chain interoperability mechanisms (Bifrost, TSS, and Vaults):Each node has a "Bifrost" service that handles the nuances of connecting to each chain. Once the nodes are synced, they watch the vault addresses. If they see an incoming transaction, they read it and convert it into a THORChain witness transaction. The state machine processes the finalized transactions and executes the corresponding logic, such as ordering transactions, calculating state changes, and delegating them to specific vault exits. Next, an outgoing transaction is created and stored in the Key-Value store. Once the final transaction is created, the signer loads it from their local copy and serializes it into the correct transaction for the target chain using the corresponding chain client, and then sends it to the TSS module for the coordination key signature. The final signed transaction is broadcast to the corresponding chain.
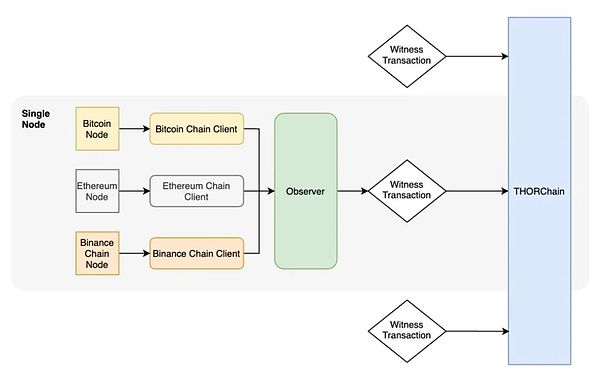
(https://docs.thorchain.org/technology/bifrost-tss-and-vaults)
Cosmos and CosmWasm: Since THORChain is built on the Cosmos SDK, it inherits the flexibility and convenience of the Cosmos ecosystem, and also solves some problems on Cosmos: such as multi-asset representation problems, node software defects, wallet address incompatibility problems, etc. THORChain also supports CosmWasm contracts, in which the module named x/wasm will self-execute the contract ending with .rs. Developers will deploy these contracts according to a biweekly upgrade cycle. They will first be tested on the testnet and deployed to the mainnet after a period of verification.
Security Mechanism
Node Incentive and Penalty Mechanism:Each THORChain node needs to stake RUNE as a guarantee for network security. If a node violates regulations or is attacked, the staked assets will be deducted, which will serve as a deterrent and risk sharing. The system has built-in automated detection and penalty mechanisms. Once malicious behavior is discovered, penalties will be immediately implemented to ensure the healthy operation of the entire network.
Smart Contract and Multi-Signature Mechanism:Asset management and scheduling are achieved through smart contracts to ensure the automatic execution and non-tamperability of cross-chain operations. To prevent single point failure or centralization risks, the multi-signature mechanism plays a key role in the unlocking and transfer of cross-chain assets, ensuring that each link of the transaction is confirmed by multiple nodes.
Continuous Audit and Upgrade:The development team and community will regularly conduct security audits on protocols and contracts to promptly discover and fix vulnerabilities. In the face of emerging security threats and technical challenges, the network continues to upgrade and optimize protocols to adapt to the ever-changing blockchain ecosystem.
How to track THORChain cross-chain?
Take the Bybit hacker's transit address 0x8ab1d1d3e7db399835172576cce0bd1c200a1ce8 as an example. The funds received by this address will be transferred to the BTC address through THORChian through cross-chain:
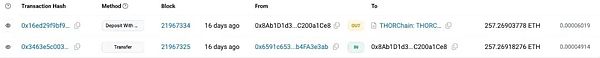
There are several ways to get the hacker's information after the cross-chain through THORChain:
Cross-chain bridge Explorer:The simplest and most direct way is to search whether there is an Explorer for the cross-chain bridge. Enter the hash of the cross-chain transaction in the Explorer for query, and you can clearly see the currency, amount and receiving address after the cross-chain.
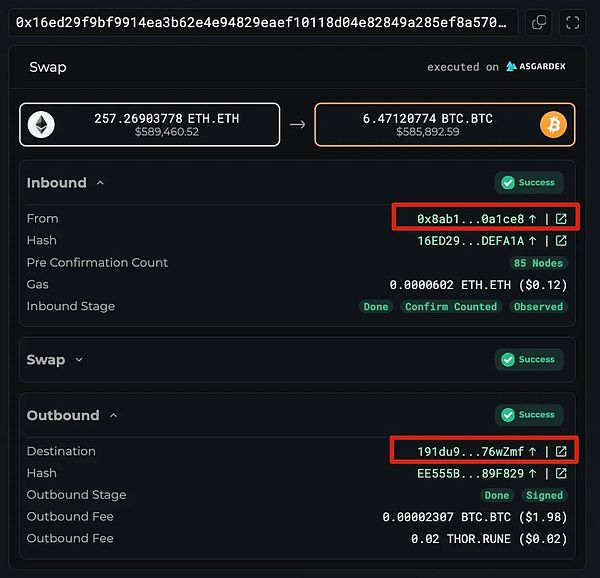
(https://thorchain.net/tx/0x16ed29f9bf9914ea3b62e4e94829eaef10118d04e82849a285ef8a5700defa1a)
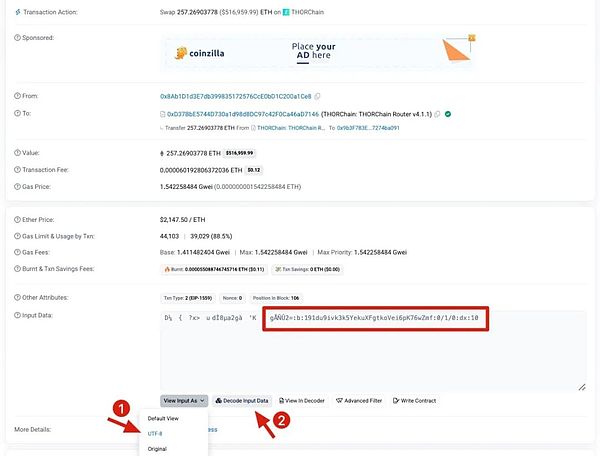
Or click Decode Input Data to get the parsed address:
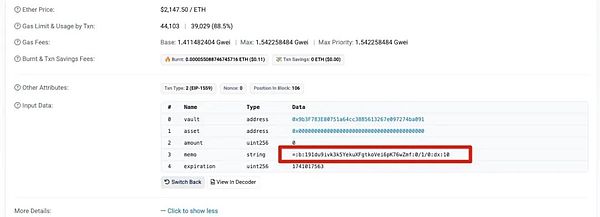
You can also view it through Logs:
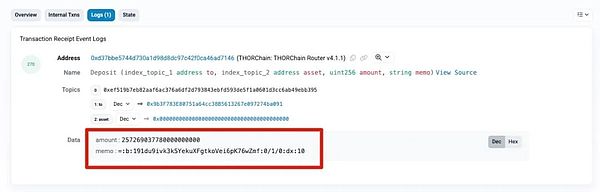
MistTrack: SlowMist's anti-money laundering tracking and analysis system MistTrack (https://misttrack.io/) The cross-chain parsing function is supported. Click the "Read original text" at the end of the article to jump directly to the MistTrack official website. In the Standard plan, right-click "THORChain" and select "Cross-chain Parsing" to see the exchanged assets and receiving addresses:
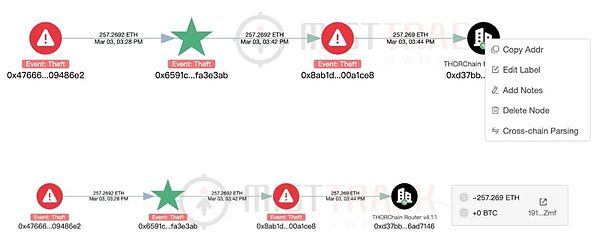
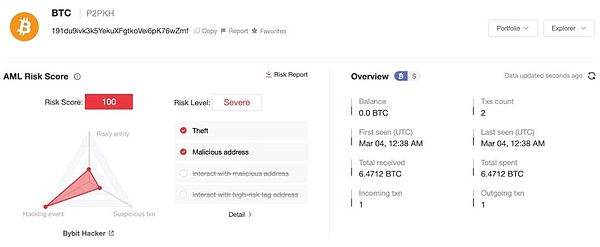
At the same time, click the parsed address to directly enter the details page of the receiving address.
In addition to THORChain, MistTrack currently supports parsing Bridgersxyz, TransitFinance, StargateFinance, AcrossProtocol and deBridgeFinance, and will support more cross-chain bridges in the future.
Summary
THORChain, as a permissionless cross-chain liquidity protocol, provides an efficient and secure way to exchange and transfer assets, but it can also easily become a tool for hackers to launder funds, highlighting the "double-edged sword" nature of decentralized cross-chain. THORChain is just one example. How to find a balance between decentralization, privacy protection and security compliance has become an important challenge facing the crypto ecosystem.
 Alex
Alex
 Alex
Alex Alex
Alex Miyuki
Miyuki Weiliang
Weiliang Brian
Brian Alex
Alex Alex
Alex Catherine
Catherine Kikyo
Kikyo Catherine
Catherine