By: Sissice
Background
On April 24, 2024, according to the intelligence of the SlowMist security team, the YIEDL project on the BSC chain was attacked, and the attacker made a profit of approximately US$300,000. The SlowMist security team analyzed the attack and shared the results as follows:
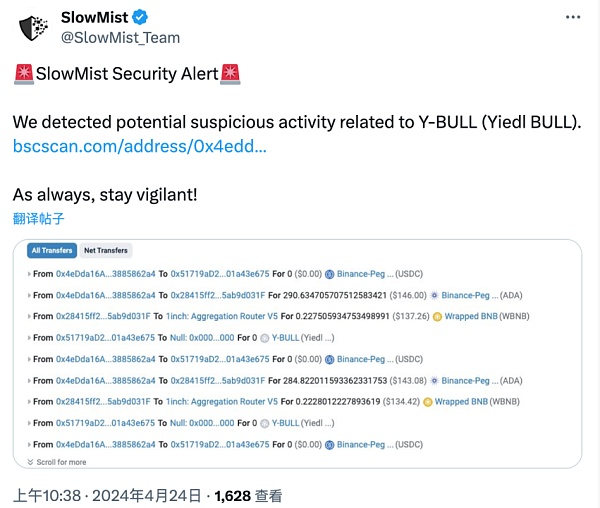
(https://twitter.com/SlowMist_Team/status/1782962346039898473)
Related information
Attacker address:
0x322696471792440499b1979e0a440491e870667a
Attacked contract address:
Part of the attack transaction:
0x49ca5e188c538b4f2efb45552f13309cc0dd1f3592eee54decfc9da54620c2ec
0x3629ad588ac120163792e92b6c43bd4bdc5bf35cac66eb7f3a0267df93abc849
0x4edda16ab4f4cc46b160abc42763ba63885862a4
Part of the attack transaction:
0x49ca5e188c538b4f2efb45552f13309cc0dd1f3592eee54decfc9da54620c2ec left;">0x0a89b8670c40b4067b9522a5933c3bf8c44c968103aa642b04c65d49ad9e6457
0x5e468cba495e5f6165418fb9d87d824309c54261055425f33f588dd3b3abbcea
0x8710034dadecfc8c26f651c612f613fffdece6e2f9957b9ec8ab843218168c1d
0x2e3d4332f66a334e0170187011ed673dc222f95bf4443b618e08f8052437ef7a
0x5a15fdc57c35f2305aaa0bb95b109ad412b17406d737d137190fe5867393339d
0x9da398ed274c8cfa774b36003fa8c930d3430d0fc5889b5008830fd6463f68a9 The core of the attack is to exploit the failure to fully verify the external parameters input by the user when the contract processes the redeem function call. This parameter is the key data for controlling asset exchange and usually contains specific transaction instructions or routing information. The attacker maliciously constructed this external parameter to achieve unauthorized asset transfer.
Transaction Analysis
The attacker called the redeem function multiple times to apply for the redemption of an asset with a quantity of 0. This behavior itself seems harmless because a redemption quantity of zero usually does not trigger any actual fund flow:
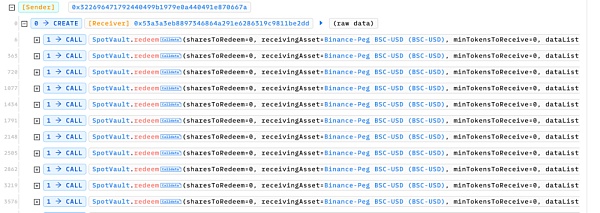
However, following up on the redeem function, it can be found that the function will traverse the list of assets allowed by the contract, and when the current asset is not the asset the user wants to receive, it will parse according to the passed in dataList parameter and externally call the corresponding function in 1inch Router to perform the asset exchange operation.
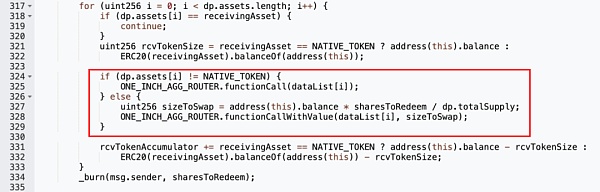
Since the dataList passed in here has not been checked and verified, the attacker can construct malicious values to execute the unoswapTo function of the 1inch Router contract to perform any controllable token exchange operation.
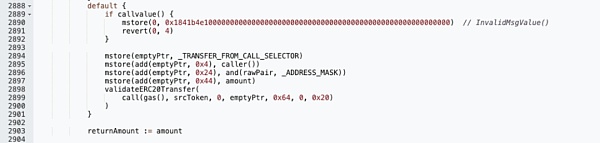
As a result, the WBNB-ADA Token in the Yiedl BULL contract was exchanged for BNB to the attacker's address.
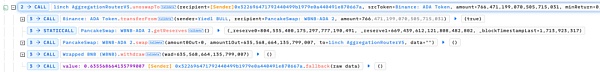
In this way, the attacker can trigger the token exchange operation controlled by the dataList parameter without actually owning any redemption shares, and mobilize the contract funds multiple times without consuming their own assets to make a profit.
Summary
The core of this attack is that the function failed to fully verify the dataList parameter input by the user, allowing the attacker to construct malicious external data and use 1inch to arbitrage the tokens in the contract. The SlowMist Security Team recommends that project parties implement a strict parameter verification mechanism in development, especially when it comes to fund operations in contracts, to ensure that all external calls meet the expected behavioral specifications, and conduct a thorough security audit of the contract logic to avoid similar incidents from happening again.
 WenJun
WenJun
 WenJun
WenJun WenJun
WenJun ZeZheng
ZeZheng ZeZheng
ZeZheng JinseFinance
JinseFinance Others
Others Coindesk
Coindesk Bitcoinist
Bitcoinist Bitcoinist
Bitcoinist Cointelegraph
Cointelegraph