Author: Duncan Nevada, Hack VC Partner; Translation: Golden Finance xiaozou
Transparent encrypted ledgers fundamentally change how we think about trust systems. As the old saying goes: "don't trust, verify", and transparency allows us to trust. If everything is open, any fraud can be marked. However, this transparency has been shown to be one of several constraints on usability. Of course, some things should be public, such as settlement, reserves, reputation (and perhaps identity), but we don't want all of everyone's financial status and health records to be made public along with personal information.
1. Privacy needs of blockchain
Privacy is a basic human right. Without privacy, there is no freedom and democracy.
Just as the early Internet needed encryption (or SSL) to enable secure e-commerce and protect user data, blockchain requires strong privacy technology to fully realize its potential. SSL allows websites to encrypt data in transit, ensuring that sensitive information such as credit card numbers cannot be intercepted by malicious actors. Similarly, blockchains require privacy technologies to protect transaction details and interactions while maintaining the integrity and verifiability of the underlying system.
Privacy protection on blockchains is not just for protecting individual users, it is critical for enterprise adoption, data protection compliance, and unlocking new design spaces. No company in the world wants every employee to see everyone else's salary, and no company wants competitors to know and rank their most valuable customers and poach them. In addition, certain industries such as healthcare and finance have strict regulatory requirements for data privacy, and blockchain solutions must meet these requirements to become a viable tool.
2. Privacy Enhancement Technology (PET) Map
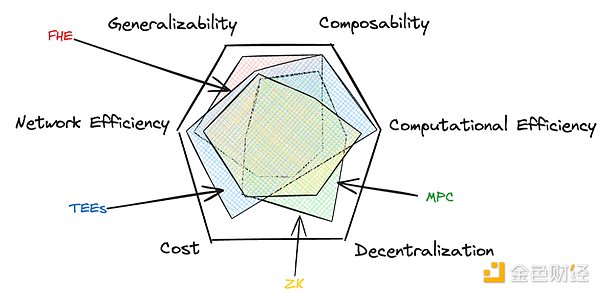
As the blockchain ecosystem develops, several key PET technologies have emerged, each with its own advantages and trade-offs. These technologies - zero-knowledge proof (ZK), multi-party computation (MPC), fully homomorphic encryption (FHE), and trusted execution environment (TEE) - span six key properties.
Generality:How easily the solution can be applied to a wide range of use cases and computations.
Composability:How easily the technology can be combined with other technologies to mitigate weaknesses or unlock new design space.
Computational efficiency:How efficiently the system performs computations.
Network efficiency:How well the system scales as the number of participants or data increases.
Degree of decentralization:How distributed the security model is.
Cost:The actual cost of privacy.
As with the blockchain trilemma of scalability, security, and decentralization, achieving all six properties simultaneously is challenging. However, recent developments and hybrid approaches are pushing the boundaries of possibility, bringing us closer to affordable, high-performance, comprehensive privacy solutions.
Now that we have the map in hand, let’s take a look at the big picture and explore the future prospects of these PET technologies.
3. PET Landscape
I think I need to add some definitions here.
(1) Zero-knowledge Proof
Zero-knowledge (ZK) is a technique that allows verification that a computation actually occurred and achieved a result without revealing the input information.
Generality: Medium. The circuits are highly application-specific, but work well with hardware-based abstraction layers like Ulvatana and Irreducible and general-purpose interpreters like Nil’s zkLLVM.
Composability: Medium. It works independently of a trusted prover, but the prover must see all the raw data in a network setting.
Computational Efficiency: Medium. With real ZK applications like Leo Wallet coming online, proofs are growing exponentially through novel deployments. We look forward to further developments as customer adoption increases.
Network Efficiency: High. Recent advances in Folding bring great potential for parallelization. Folding is essentially a more efficient way to construct iterative proofs, so its development can build on the work that has already been done. Nexus is one such project worth watching.
Decentralization:Medium. In theory, proofs can be generated on any hardware, but in practice, GPUs are more popular. Although hardware is becoming more uniform, it can be further decentralized at an economic level through AVS (such as Aligned Layer). Inputs are only private when used in conjunction with other technologies (see below for details).
Cost:Medium. The initial deployment cost of circuit design and optimization is high. Operational costs are moderate, with relatively high proof generation costs but high verification efficiency. A significant factor contributing to this cost structure is proof storage on Ethereum, but this can be mitigated by other methods, such as using a data availability layer such as EigenDA or AVS.
Take Dune as an example: Imagine that Stilgar needs to prove to Duke Leto that he knows the location of a spice field, but does not want to reveal the exact location. Stilgar takes Leto, blindfolded, on an ornithopter and flies over the spice fields until the scent of cinnamon fills the cabin. Then he takes Leto back to Arrakeen. Leto now knows that Stilgar can find the spices, but he has no idea how to get there.
(2) Multi-party computation
Multi-party computation (MPC) is a process where multiple parties can work together to compute a result without revealing their inputs to each other.
Generality: High. Given the special features of MPC (such as secret sharing, etc.).
Composability: Medium. MPC is secure, but composability decreases with complexity because complexity introduces exponential network overhead. However, MPC has the ability to process private inputs from multiple users in the same computation, which is a fairly common use case.
Computational efficiency: Medium.
Networking efficiency: Low. The number of participants scales quadratically with the amount of networking that must be done. Projects such as Nillion are working to address this. Erasure coding/Reed-Solomon codes—or more loosely, splitting data into shards and then saving those shards—can also be used to reduce errors, although it is not a traditional MPC technique.
Decentralization: High. But there is also the possibility that participants can collude and compromise security.
Cost: High. Medium to high implementation cost. High operating cost due to communication overhead and computation requirements.
Take Dune as an example: Consider that the large families of Landsraad make sure they have enough spice reserves between them so that they can help each other, but they don’t want to reveal the details of their individual reserves. The first family can send a message to the second family to add a large random number to their actual reserves. The second family then adds their actual reserves, and so on. When the first family receives the final total, they only need to subtract the large random number they added before to know the actual total amount of spice reserves.
(3) Fully Homomorphic Encryption
Fully Homomorphic Encryption (FHE) allows computations to be performed on encrypted data without first decrypting it.
Generality:High.
Combinability:High composability of single user inputs. Must be combined with other multi-user privacy input techniques.
Computational efficiency: Low. But it has been optimized consistently from the math layer to the hardware layer, which will unlock a huge potential. Zama and Fhenix have done a lot of great work in this regard.
Network efficiency: High.
Decentralization: Low. Part of this is because of the computational requirements and complexity, but as the technology advances, FHE's decentralization may approach ZK's decentralization.
Cost: Very high. Deployment costs are high due to complex encryption and strict hardware requirements. Operational costs are high due to the large amount of computation.
Take Dune as an example: Imagine a device similar to the Holtzmann shield, but for numbers. You can enter digital data into this shield, activate it, and then give it to a Mentat. The Mentat can perform calculations without seeing the shielded numbers. After the calculation is completed, they will return the shield to you. Only you can restore the shield and see the results of the computation.
(4) Trusted Execution Environment
A trusted execution environment (TEE) is a secure enclave or area within a computer processor that is isolated from the rest of the system and in which sensitive operations can be performed. TEEs are unique in that they rely on silicon and metals rather than polynomials and curves. So while they may be a powerful technology today, in theory they should be slower to optimize due to the limitations of expensive hardware.
Versatile:Medium.
Composability:High.
But security is low due to potential side channel attacks.
Computational efficiency:High. Close to server-side efficiency, so much so that Nvidia's latest H100 chipset series is equipped with a TEE.
Network efficiency:High.
Decentralization:Low. But it is limited by specific chipsets, such as Intel's SGX, which means it is vulnerable to side-channel attacks.
Cost:Low. If you use existing TEE hardware, the deployment cost is low. Due to the close to native performance, the operating cost is low.
Take Dune as an example: Imagine the Heighliner cabin of the Space Guild. Even the Guild's own navigator cannot see or interfere with what is happening inside when it is in use. The navigator enters the cabin and performs the complex calculations required to fold space, and the cabin itself ensures that everything done inside is private and secure. The Guild provides and maintains this cabin and ensures its security, but they cannot see or interfere with the navigator's work in the cabin.
4. Actual use cases
Perhaps we don't need to compete with the spice giants, but only need to ensure that privileged data such as key spices remain privileged. In our real world, some actual use cases corresponding to each technology are as follows.
ZK is great when we need to verify that a process produced the correct result. It is an excellent privacy technology when combined with other techniques, but used alone it sacrifices trust and is more akin to compression. Typically we use it to verify that two states are the same (i.e. an "uncompressed" L2 state and a block header published to L1, or to prove that a user is over 18 without revealing any actual personally identifiable information about the user).
MPC is often used for key management, either private keys or decryption keys used in combination with other techniques, but it is also used for distributed random number generation, (smaller) privacy-focused computation operations, and oracle aggregation. Essentially, any approach to lightweight aggregation-based computation using multiple parties that shouldn't be colluding with each other is a good fit for MPC.
FHE is a good choice when simple general-purpose computations need to be done without the computer seeing the data (e.g. credit scoring, smart contract games for the Mafia, or ordering transactions in a memory pool without revealing what the transactions are).
Finally, TEEs are great for more complex operations if you're willing to trust the hardware. For example, this is the only viable solution for a private equity model (LLMs that exist in enterprises or financial/healthcare/national security agencies). The trade-off is that since TEE is the only hardware-based solution, improvements should, in theory, be slower and more expensive than with other technologies.
5. Other Solutions
It is clear that there is no perfect solution, and it is unlikely that one technology will grow into a perfect solution. Hybrid solutions are exciting because they can leverage the strengths of one approach to mitigate the weaknesses of another. The table below shows some of the new design spaces that can be unlocked by combining different approaches. The actual practices are quite different (for example, combining ZK and FHE may require finding the right curve parameters, while combining MPC and ZK may require finding a certain set of settings to reduce the final network RTT time.
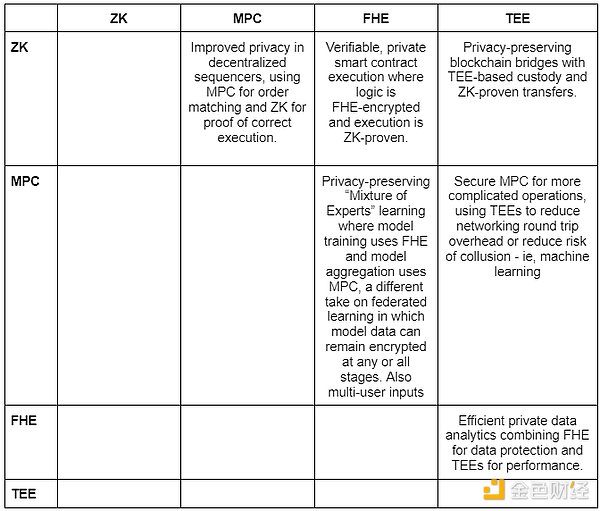
In short, high-performance general privacy schemes can unlock countless applications ranging from gaming, governance, fairer transaction lifecycles, identity authentication, non-financial services, collaboration and coordination. This can partly explain why we found Nillion, Lit Protocol and Zama are so fascinating.
6. Conclusion
In summary, we see great potential, but we are still in the early stages of exploring possibilities. Individual technologies may be nearly mature to some extent, but staking technology is still an area for exploration. PET will be tailored to this field, and from an industry perspective, we still have a lot to do.
 Davin
Davin







