The premise of using isomorphic binding technology is isomorphism. The Cell model of the CKB blockchain is an advanced version of the Bitcoin UTXO model, and the two have the same origin. This similarity allows us to bind or map the UTXO on one blockchain to the UTXO on another blockchain through isomorphic binding technology. Take the RGB++ protocol as an example. Since RGB assets are essentially parasitic on Bitcoin UTXO, the RGB++ protocol can use isomorphic binding technology to map Bitcoin UTXO to the Cell of the CKB blockchain, so that we can use the CKB blockchain to replace the client verification of the RGB protocol.
In order to understand the isomorphic binding technology more intuitively, we use land and title deeds as analogies:
The above 4 steps correspond exactly to the 4 operating processes of the isomorphic binding technology: Map UTXO to Cell, verify transactions, cross-chain verification, and change status on CKB.
From the analogy of land and title deeds above, we can clearly see that the security and prevention of double spending of paper title deeds stored in Bitcoin UTXO mainly rely on the security of the Bitcoin blockchain. And Bitcoin, as the longest-running and most secure PoW chain, has withstood the test of time.
The security and prevention of double spending of the electronic title deeds generated by isomorphic binding technology mainly rely on the security of the CKB blockchain. CKB has adopted the same time-tested PoW consensus mechanism as Bitcoin from the beginning, which guarantees security and decentralization to the greatest extent. Currently, CKB's mining equipment is produced by Bitmain, the world's largest ASIC mining machine manufacturer. The current CKB network computing power has exceeded 440 PH/s, setting a record high. It is extremely difficult to forge or reconstruct a PoW chain, because it requires recalculating the computing power of each block, which is like trying to rebuild a pyramid overnight, which is almost an impossible task. Therefore, we can fully trust the security of the CKB blockchain. Of course, if you still have doubts, you can also choose to verify it yourself, just like the second step in the above example, to confirm whether the deed really says 40 acres, and whether the land traceability certificate provided by Zhang San is authentic and valid. This is also the practice of the RGB protocol, where users need to complete the client verification themselves; the RGB++ protocol just provides an additional option. In addition to choosing to complete the client verification yourself, you can also choose to trust the verification of the CKB blockchain. The CKB blockchain is only used here as a DA layer and status disclosure. The security of paper deed transactions is not even directly related to CKB.
The charm of the RGB++ protocol is not only that the CKB blockchain acts as a DA layer, it also supports Leap operations, allowing RGB++ assets on the Bitcoin blockchain to freely shuttle on the CKB blockchain (of course, the reverse operation is also possible, and it can be extended to other Turing-complete UTXO blockchains in the future). Due to the Turing completeness of the CKB blockchain, developers can build various complex DeFi applications on it, such as lending platforms, decentralized exchanges, etc. This means that RGB++ assets transferred to the CKB blockchain through Leap operations can participate in a wide variety of financial activities, such as mortgage lending, pledge interest, trading, etc.
When you hold RGB++ assets transferred to the CKB chain through Leap operations and participate in various financial activities, the security of these operations mainly depends on the security of the CKB blockchain. As we discussed earlier, the CKB blockchain itself has high security. However, if you still have doubts about the security of the CKB blockchain, you can always choose to transfer the RGB++ assets on the CKB chain back to the Bitcoin blockchain through the Leap operation, so that it can be turned into RGB++ assets on the Bitcoin blockchain again.
Speaking of the Leap function, we have to mention the risk it may face - block reorganization. However, this risk can be effectively avoided by waiting for more block confirmations. In the Bitcoin network, transactions that have been confirmed by 6 blocks are generally considered irreversible. It is worth noting that the number of confirmations of PoW is not linearly related to security, and the difficulty of overturning PoW blocks increases exponentially with the increase of blocks. Therefore, on the CKB blockchain, to achieve the same security as Bitcoin's 6 block confirmations, it is calculated that only about 24 CKB block confirmations are needed. Considering that the average block time of CKB is about 10 seconds, the time required for 24 block confirmations is actually much less than the time required for Bitcoin's 6 block confirmations.
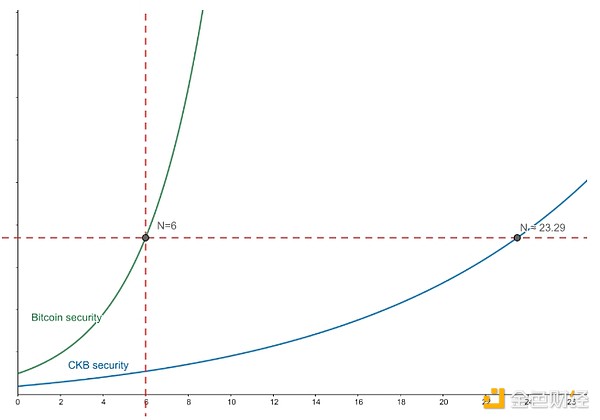
Figure: Schematic diagram of PoW security; Source: https://talk.nervos.org/t/rgb-1/7798
So, if you want to get higher security, just wait for a few more block confirmations.
The isomorphic binding technology used by RGB++ cleverly binds Bitcoin's UTXO to CKB's Cell, which not only simplifies the user's verification operation but also maintains a high degree of security. At the same time, Leap operations provide users with a broader application scenario and open up new avenues for cross-chain interoperability.
As more and more applications choose to build on RGB++, we have reason to believe that it will play an increasingly important role in the future Bitcoin ecosystem.
 Weiliang
Weiliang





