Author: CertiK Chinese Community
In 2024, the Web3.0 world ushered in a wave of new opportunities, but many hidden crises also emerged. According to the data from CertiK's latest "Hack3d: 2024 Annual Security Report", a total of 760 on-chain security incidents occurred throughout the year, causing a total loss of US$2.36 billion. Among them, the losses caused by phishing attacks accounted for nearly half, an increase of 31% year-on-year, becoming one of the biggest threats to the security of user assets.
In this situation, how to effectively deal with phishing attacks has become an issue that every Web3.0 user and project party must pay attention to. This article will explore how to prevent phishing attacks, help everyone master the core protection strategies, and establish a stronger security barrier for digital assets.
Beware of phishing attacks: identification and prevention
The means of phishing attacks are becoming increasingly complex and are no longer limited to suspicious emails. Today, hackers use a variety of methods to deceive Web3.0 users and steal their digital assets. Here are some common attack methods:
Spear Phishing:This is a highly targeted attack method. The attacker disguises himself as a trusted individual or entity and uses a carefully designed scam to induce users to disclose sensitive information or authorize access, thereby stealing digital assets. This attack is often highly deceptive and gains the trust of the victim through a highly customized credible disguise.
Decentralized Application Phishing (DApp Phishing):The attacker creates a fake decentralized application (DApp) to induce users to connect to their wallets. Once the user authorizes, the attacker can obtain access rights and complete the theft. This attack takes advantage of users' trust in decentralized applications and their unfamiliarity with new technologies.
Social media account hacking: The social media accounts of KOLs or project organizations in the Web3.0 field may be hacked. Hackers use these accounts to post false information, promote scams, phishing links, or fake giveaways to deceive fans. Since these accounts usually have high attention, this attack can spread widely and cause serious damage to user assets and brand reputation.
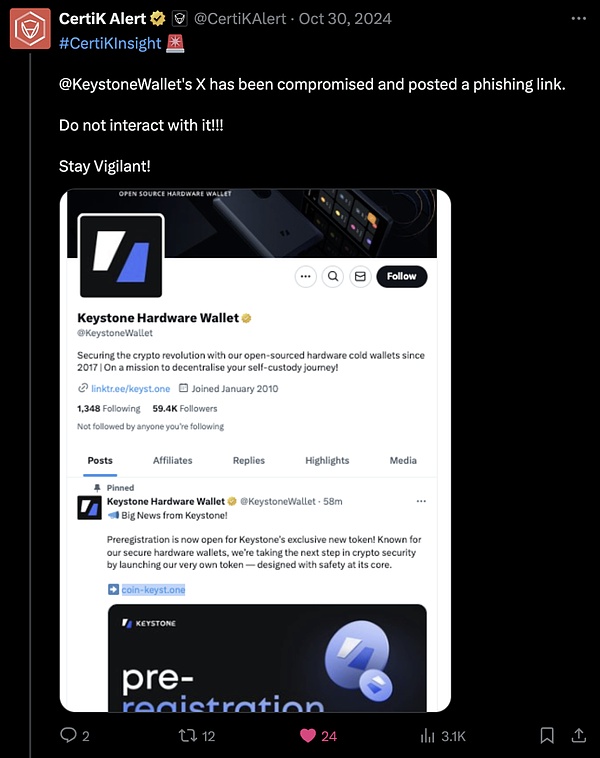
To effectively prevent phishing attacks, users must always remain vigilant and take the following measures:
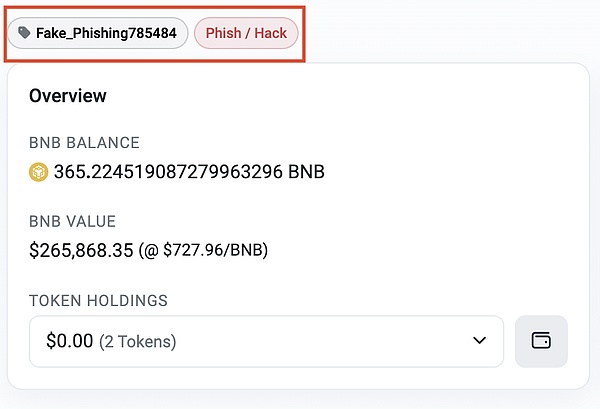
Verify the authenticity of the URL and smart contract: Before making any transactions, be sure to use blockchain browser platforms such as Etherscan[1], Bscscan[2] or Solscan[3] to verify the legitimacy of the address. This step is crucial because fake addresses may direct your assets to the control of hackers.
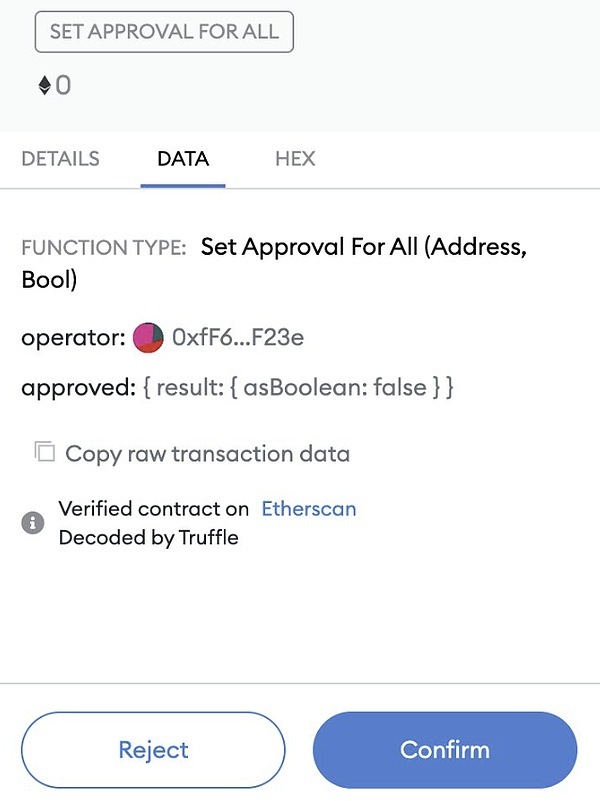
Be careful when authorizing transactions:Never approve or authorize any transaction that is not initiated by you. Before approving a transaction, carefully check the accuracy of the information to ensure that the initiator and destination address of the transaction are credible. This step can effectively prevent hackers from stealing your assets by forging transaction authorization.
Revoke suspicious permissions:If there is any doubt about any permissions that have been granted, users can use tools such as revoke.cash[4] to revoke the permissions granted to the DApp. Revoking unnecessary permissions in a timely manner can reduce potential security risks.
Beware of suspicious links:Never click on links sent in private messages. Hackers often use fake interfaces and fraudulent URLs to deceive users. Always check unsafe or suspicious URLs, fake SSL certificates, and links from unknown sources to avoid falling into traps set by hackers.
Use cold wallets: provide isolation protection for digital assets
A cold wallet is an offline wallet that can completely isolate and securely store private keys. It is a dedicated physical device that allows users to sign transactions without exposing their private keys. Unlike hot wallets, cold wallets do not allow remote attackers to access them at any time, so they can effectively reduce the risk of being attacked. This feature of cold wallets makes them ideal for long-term storage needs or for saving infrequently used assets. It can help users avoid relying on online third parties, thereby significantly improving the security of digital assets.
However, cold wallets are not a panacea. The security of digital currencies requires multiple levels of protection. For example, users can add multi-signature authentication or two-factor authentication (2FA) to further enhance the security of their wallets. Through these measures, users can build a more solid security line of defense to effectively resist various potential threats.
Social Media Security: Beware of Disguised Scams
On social media platforms, hackers often target users by impersonating well-known figures or creating fake accounts. The most common scams include fake "giveaway" events, which often promise users high returns for just a certain amount of money. Other methods include sending private messages, phishing links, or false promises of cooperation. Scammers often use a sense of urgency to force victims to take action without careful consideration, thus falling into the trap.
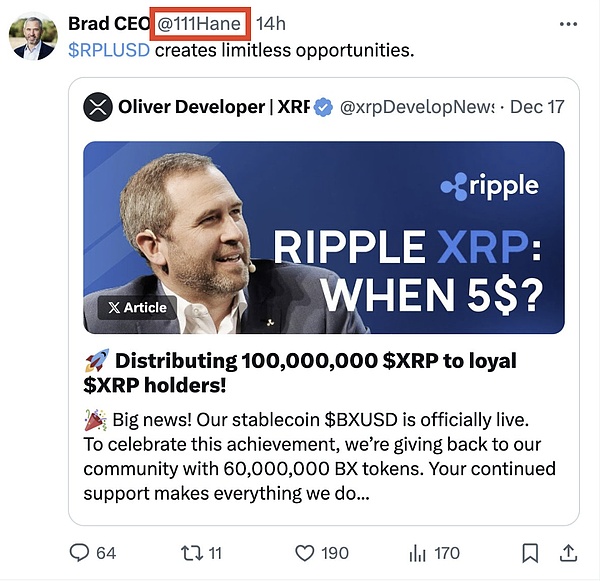
In addition, users should also be wary of scam discussion groups on platforms such as Telegram and Discord. These groups may spread false information or share phishing links, imitating official Web3.0 project channels. To prevent these risks, CertiK recommends users to take the following measures:
Disable private messages:It is recommended to turn off private messages from members of large shared groups and be wary of any unsolicited interactions. This can effectively reduce the chances of being contacted directly by scammers.
Follow official channels:When tracking project information, only follow verified official accounts and give priority to announcements directly from official websites. This can effectively avoid being misled by false information.
Protect personal information:Never share screenshots or personal information related to wallets on social media. This information may be used by scammers to conduct phishing attacks and may even pose a threat to the user's personal safety.
Learn security knowledge: Improve self-protection capabilities
In the Web3.0 world, mastering security knowledge is one of the keys to protecting digital assets. CertiKSkynet[5] can help users understand the reliability of the project and check the risks of the project code by viewing the key points summarized by Skynet and the detailed audit report.
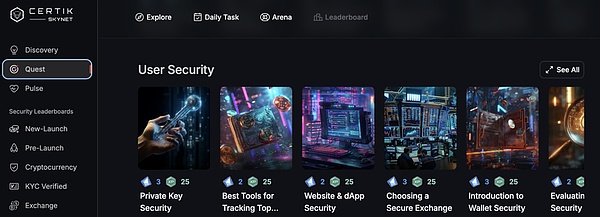
Skynet Quest helps users master the core knowledge of Web3.0 security through interactive learning, such as private key protection, selection of secure exchanges, and identification of crypto drainers. Through these tools and resources, users can improve their security awareness and better deal with various risks.
In addition, users should continue to learn and identify new fraud methods. In order to keep up to date with the latest event alerts and security data statistics, users can follow @certikalert on X[6] and read the latest security event analysis published on the CertiK official website[7]. By continuously learning and updating knowledge, users can better cope with the ever-changing cybersecurity threats and ensure the safety of their digital assets.
 Kikyo
Kikyo
 Kikyo
Kikyo Alex
Alex Kikyo
Kikyo Brian
Brian Alex
Alex Hui Xin
Hui Xin Kikyo
Kikyo Brian
Brian Alex
Alex Joy
Joy