Source: SharkTeam
On June 10, 2024, UwU Lend was attacked and the project owner lost approximately US$19.3 million.
1. Analysis of attack transactions
Attacker: 0x841dDf093f5188989fA1524e7B893de64B421f47
The attacker initiated a total of 3 attack transactions:
Attack transaction 1:
0x242a0fb4fde9de0dc2fd42e8db743cbc197ffa2bf6a036ba0bba303df296408b
Attack transaction 2:
uSUSDE: 0xf1293141fc6ab23b2a0143acc196e3429e0b67a6
uDAI: 0xb95bd0793bcc5524af358ffaae3e38c3903c7626
uUSDT: 0x24959f75d7bda1884f1ec9861f644821ce233c7d
The attack process is as follows:
1. Flash loans of multiple tokens from different platforms, including WETH, WBTC, sUSDe, USDe, DAI, FRAX, USDC, GHO
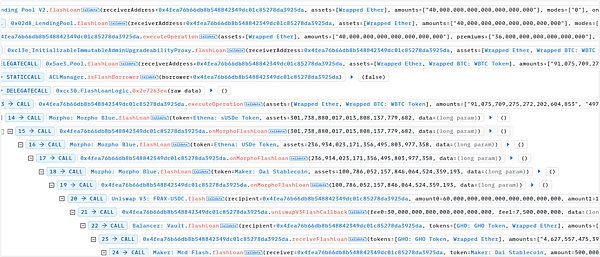
The tokens and amounts of the flash loan are as follows:
159,053.16 WETH and 14,800 WBTC were flash loaned from AaveV3
40,000 WETH were flash loaned from AaveV2
91,075.70 WETH and 4,979.79 WBTC were flash loaned from Spark
Flash loan of 60,000,000 FRAX and 15,000,000 USDC from Uniswap V3: FRAX-USDC
Flash loan of 4,627,557.47 GHO and 38,413.34 WETH from Balancer
Flash loan of 500,000,000 DAI from Maker
A total of approximately 328,542.2 WETH, 19779.79 WBTC, 600786052.15 DAI, 301,738,880.01 sUSDe, 236,934,023.17 USDe, 4,627,557.47 GHO, 60,000,000 FRAX, 15,000,000 USDC
2. Transfer the flash loan token to the contract 0xf19d66e82ffe8e203b30df9e81359f8a201517ad (abbreviated as 0xf19d) to prepare for the attack.
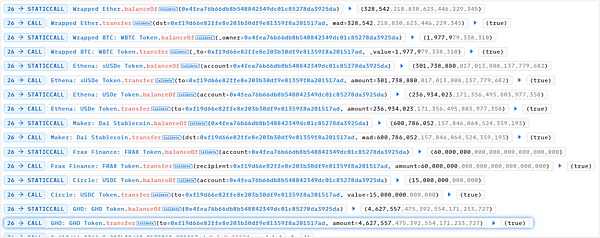
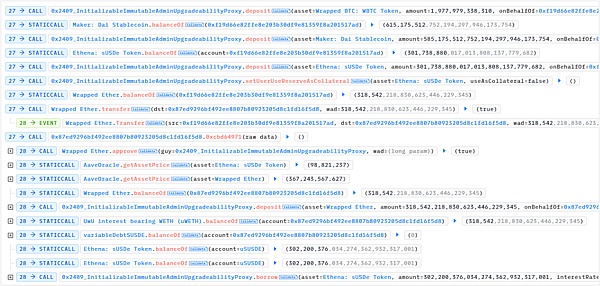
3. Control the price of sUSDe (lower the price) by exchanging tokens
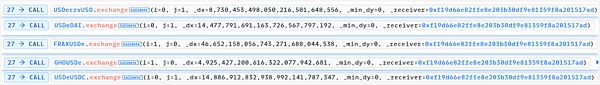
(1) USDecrvUSD.exchange

Convert 8,676,504.84 USDe to 8,730,453.49 crvUSD. The amount of USDe in USDecrvUSD increases, the price decreases, the amount of crvUSD decreases, and the price increases.
(2) USDeDAI.exchange

Convert 46,452,158.05 USDe to 14,389,460.59 DAI. The amount of USDe in USDeDAI increases, the price decreases, the amount of DAI decreases, and the price increases.
(3) FRAXUSDe.exchange
14,477,791.69 USDe is converted into 46,309,490.86 FRAX. The amount of USDe in USDeDAI increases, the price decreases, the amount of FRAX decreases, and the price increases.
(4)GHOUSDe.exchange

4,925,427.20 USDe is converted into 4,825,479.07 GHO. The amount of USDe in USDeDAI increases, the price decreases, the amount of GHO decreases, and the price increases.
(5)USDeUSDC.exchange
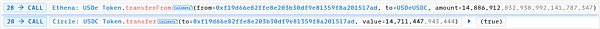
Convert 14,886,912.83 USDe to 14,711,447.94 USDC, the amount of USDe in USDeDAI increases, the price decreases, the amount of USDC decreases, and the price increases
After the above exchange, the USDe price in the five fund pools decreases. Eventually, the price of sUSDe plummets.
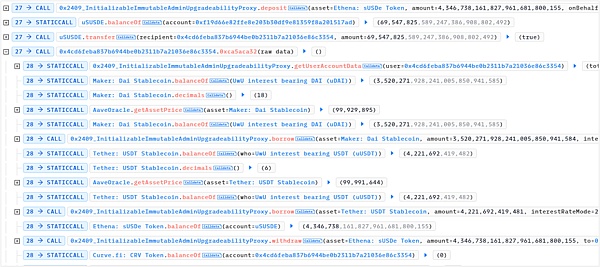
4. Continuously create lending positions, that is, deposit other assets (WETH, WBTC and DAI) into the LendingPool contract, and then borrow sUSDe. Because the price of sUSDe plummeted, the amount of sUSDe borrowed was much more than before the price plummeted.
5. Similar to step 3, the reverse operation will increase the price of sUSDe.
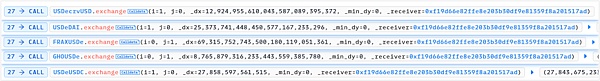
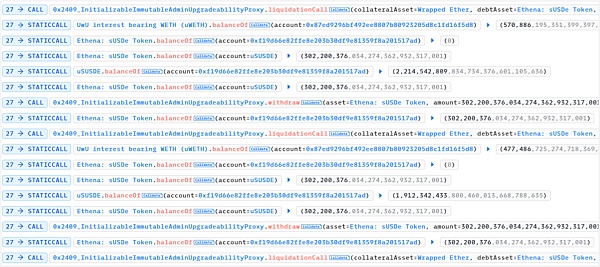
Due to the increase in sUSDe, the position value of the loan in step 4 exceeds the collateral value and meets the liquidation standard.
6. Liquidate the loan positions in batches and obtain the liquidation reward uWETH
7. Repay the loan and withdraw the underlying assets WETH, WBTC, DAI and sUSDe.
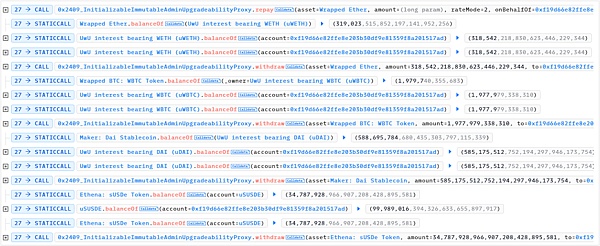
8. Deposit sUSDe into LendingPool again. At this time, the price of sUSDe is raised, so more other assets can be borrowed, including DAI and USDT.
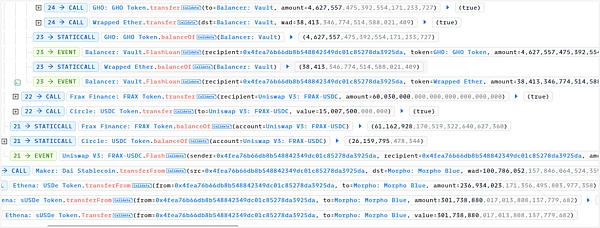
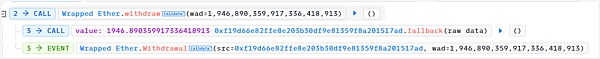
9. Exchange tokens and repay flash loans. The final profit was 1,946.89 ETH
II. Vulnerability Analysis
Through the above analysis, it is found that there are a large number of flash loans and multiple manipulations of the sUSDe price throughout the attack process. When sUSDe is pledged, the amount of borrowed assets will be affected; when sUSDe is borrowed, the borrowing rate will be affected, and then the liquidation coefficient (health factor) will be affected.
The attacker took advantage of this and used flash loans to lower the price of sUSDe, mortgaged other assets, borrowed a large amount of sUSDe, and then raised the price of sUSDe, liquidated the mortgaged assets for profit, and mortgaged the remaining sUSDe to borrow other assets, and finally repaid the flash loan to complete the attack.
From step 3 above, it was found that the attacker manipulated the price of sUSDe by controlling the prices of USDe in the five trading pools of Curve Finance: USDe/rvUSD, USDe/AI, FRAX/SDe, GHO/SDe and USDe/SDC. The price reading function is as follows:
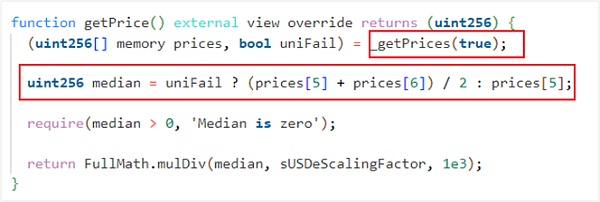
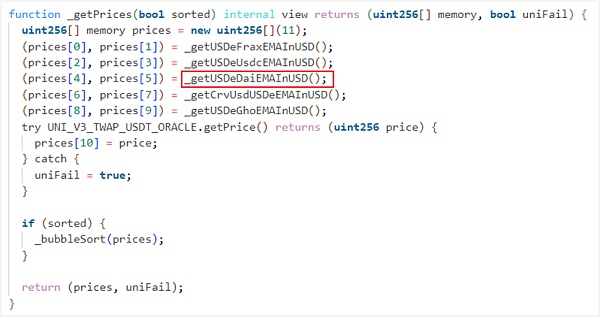
Among them, the sUSDe price is calculated from 11 prices, of which the first 10 are read from CurveFinance, and the last one is provided by UniswapV3.
The price read from CurveFinance is provided by 5 trading pools, namely USDe/rvUSD, USDe/AI, FRAX/SDe, GHO/SDe and USD/SDC, which are also the 5 trading pools manipulated by the attacker in the attack transaction. The returned price is calculated by the price read by uwuOracle, price_oracle(0) and get_p(0) in the CurveFinance trading pool contract.
(1)Price is the price provided by Chainlink and cannot be manipulated;
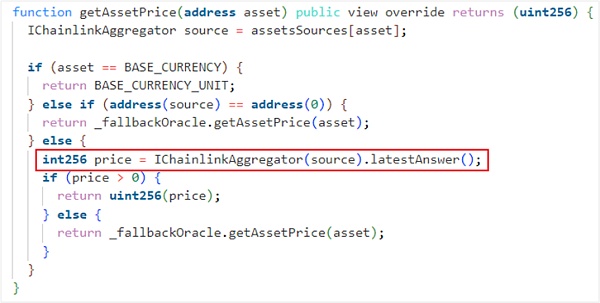
(2)Transaction pool parameters
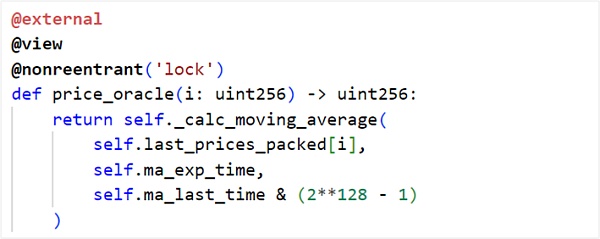
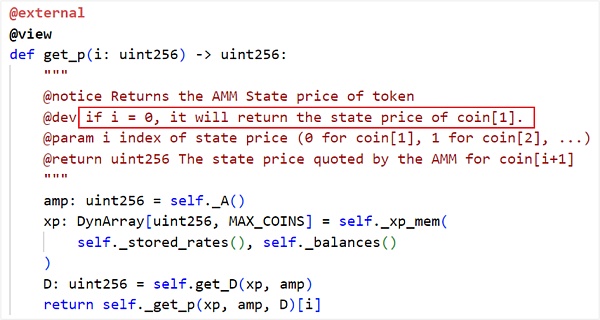
III. Security Recommendations
In response to this attack, the following precautions should be followed during development:
(1) For price manipulation vulnerabilities, an off-chain price oracle can be used to avoid price manipulation.
(2) Before the project goes online, a third-party professional audit company needs to conduct a smart contract audit.
 JinseFinance
JinseFinance






















