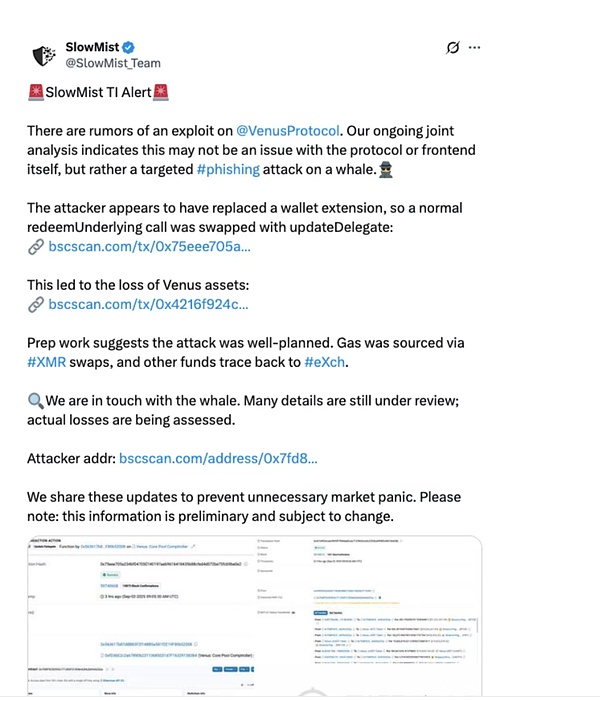
Background: On September 2, 2025, community user @KuanSun1990 was attacked, resulting in the transfer of multiple positions on the Venus Protocol, resulting in a loss of approximately $13 million. SlowMist's proprietary Web3 threat intelligence and dynamic security monitoring tool, MistEye, successfully captured the anomaly and assisted the user with analysis. The following provides detailed analysis.
(https://x.com/SlowMist_Team/status/1962854755585429877)
Root Cause
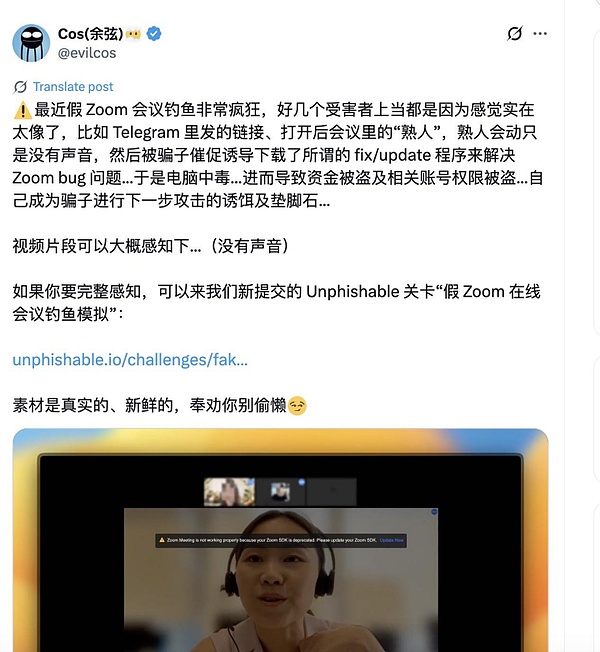
After gaining control of the victim's computer, the attacker somehow modified the browser extension's wallet code on the victim's computer, allowing them to hijack and replace the victim's original transaction data. Because the hardware wallet used by the victim lacked a complete "what you see is what you sign" verification mechanism, the victim ultimately signed a tampered transaction.
So how did the attacker modify the browser extension wallet code?
We know that Chrome has a security mechanism. If the extension is downloaded from the Chrome Store, as long as the code is modified, the browser will prompt that the extension is damaged and cannot be used. In addition, this integrity check cannot be turned off. Therefore, we initially suspected the attacker might not have modified the code of a well-known official browser extension wallet, but rather employed other attack methods. Since many traces of the attack had been removed from the victim's computer, a complete reconstruction of the truth was difficult. However, through further research and communication with partners in our threat intelligence network, we confirmed that the browser extension ID used by the attacker to tamper with transactions matched the official extension ID. We then began researching how to maintain the consistency of the browser extension ID while allowing code modification: With developer mode enabled on the browser extension page, you can create an additional copy of the official extension file and import it into the browser. This creates a new extension that is both code-modifiable and has the same ID as the official extension. This is because Chrome generates extension IDs based on the key in the manifest.json file. As long as the key of the manifest.json file in the extension is the same as the official one (the same key is the key to ensuring that the extension has the same ID), the code in the new extension (with the same ID as the official one) can be modified arbitrarily without triggering the integrity check.
By patching Chrome's function for browser extension content verification, the extension's content integrity check can be globally disabled. Of course, on macOS, this part of the operation requires re-signing to ensure the program is usable.
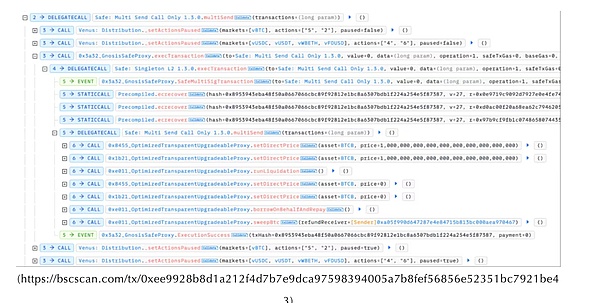
The above are two possible attack methods we have researched. Currently, there is no more clear information to support this, so the above methods only represent the research and speculation within the SlowMist Security Team and do not mean that the attacker actually used this method. Before the attack officially began, the attacker used their own funds to raise approximately 21.18 BTCB and 205,000 XRP on September 1st, preparing to take over the victim's Venus positions. After approximately 10 hours of waiting, the attacker finally got the opportunity for the victim to access their wallet. The victim then used their hardware wallet to connect to their Chrome browser extension wallet and visited the correct Venus website. The victim then attempted to redeem their USDT holdings on Venus. They called the correct redeemUnderlying function. However, because the extended wallet had been tampered with, the signature operation sent to the hardware wallet was replaced with an updateDelegate operation. The victim's hardware wallet did not support detailed signature data parsing and had blind signatures enabled. This allowed the victim to sign the updateDelegate operation without warning and submit the transaction through the extended wallet. Ultimately, their Venus position was delegated to the attacker for management.
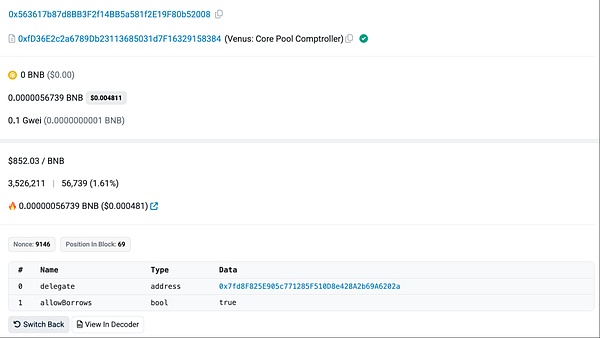
(https://bscscan.com/tx/0x75eee705a234bf047050140197aeb9616418435688cfed4d072be75fcb9be0e2)
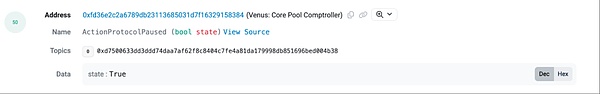
(https://bscscan.com/tx/0xe4a66f370ef2bc098d5f6bf2a532179eea400e00e4be8ea5654fa9e8aeee65bf#eventlog)
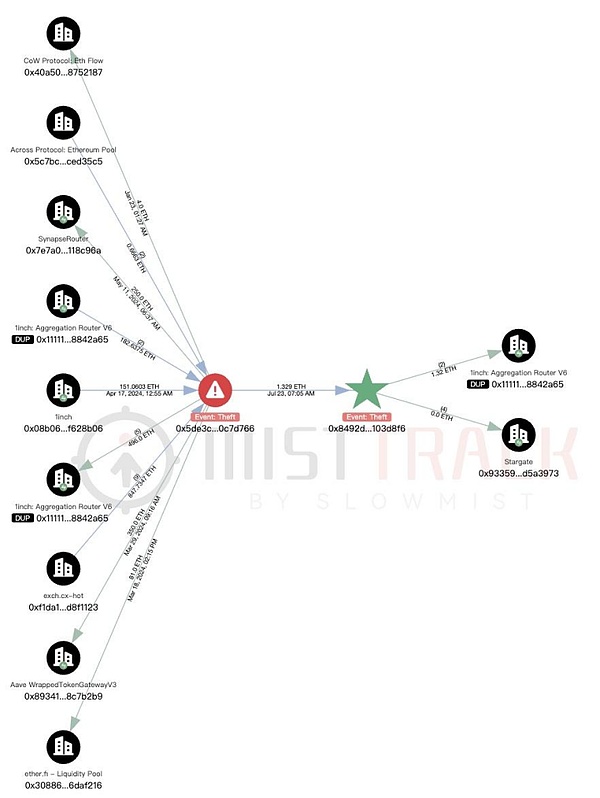
In addition, according to the analysis of the on-chain anti-money laundering tracking tool MistTrack, the addresses related to the attacker have withdrawn money from ChangeNOW:

Other related addresses have been associated with multiple exchange platforms (such as 1inch), cross-chain platforms (such as Across Protocol), and sanctioned exchanges (such as eXch):
Summary
This incident was a carefully planned phishing attack. The attacker used a malicious Zoom client to control the user's device and exploited Chrome's developer mode to tamper with the wallet extension, subtly replacing the user's asset redemption operations with position orders. This was an extremely sophisticated operation. Fortunately, the Venus team demonstrated outstanding emergency response capabilities. Through multi-party collaboration and rapid response, they ultimately helped the user escape danger and avoid potential huge losses.
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance Davin
Davin Nell
Nell Beincrypto
Beincrypto Bitcoinist
Bitcoinist Bitcoinist
Bitcoinist