Surpassing Filecoin? New storage protocol Walrus released
On March 27, 2025, the decentralized storage protocol Walrus of Sui public chain was launched. Mysten Labs made another move after Sui network and DeepBook, this time aiming at the storage track of Web3. Built on the Sui blockchain, Walrus is trying to optimize and improve existing storage solutions in terms of storage cost efficiency, programmability, data access and deletion. It not only wants to be the storage layer of Sui network, but also aims to become the leading protocol of decentralized storage of Web3.
According to the "2020 Data Breach Cost Report" released by IBM, there were about 99,730 data breaches in the world that year, causing a total economic loss of hundreds of billions of dollars. In 2018, a Google data center in Belgium was struck by lightning, causing disk damage and data loss. The fragility of centralized storage is a headache, and distributed storage - encrypting, slicing, and distributing data to global nodes - sounds like a tailor-made answer for privacy and security.
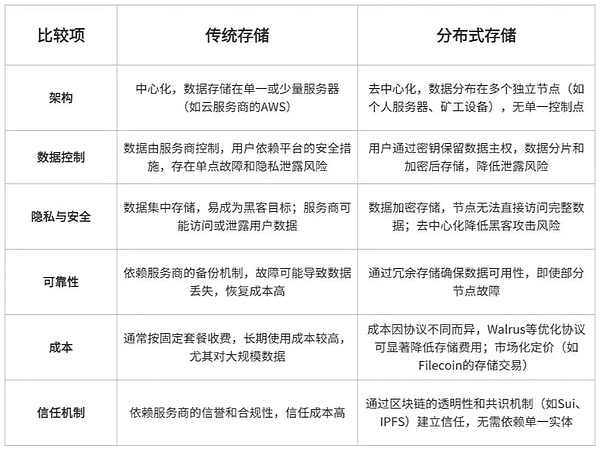
By dispersing and storing data in multiple physical nodes (usually servers or devices around the world), combined with encryption and blockchain mechanisms to achieve high data availability and privacy security, compared with traditional storage methods, there are many advantages:
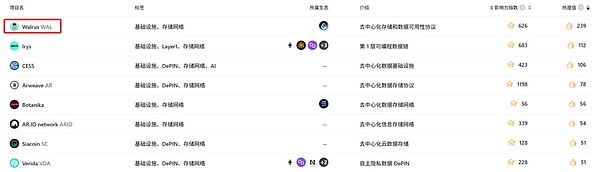
As one of the most advanced projects in the decentralized storage protocol, Walrus has also become the most popular in the Rootdata storage track, bringing a lot of voice to the long-dormant decentralized storage track. Many people recalled the craze that Filecoin set off back then.
In 2017, Filecoin was launched, causing a sensation in the crypto industry through a record-breaking $200 million ICO. The vision was to combine IPFS (InterPlanetary File System) with blockchain incentives to build a global distributed storage market. After the mainnet was launched in 2020, Filecoin quickly attracted a large number of miners and developers, and the storage capacity exceeded 1EB (1 billion GB) within a year. The community had high hopes for it, and the price of FIL tokens soared, driving a storage mining boom. At that time, even Chinese aunts went to buy mining machines, and the saying that Filecoin was the next Bitcoin was even more rampant.
However, Filecoin has gradually lost popularity due to high storage costs, complex incentive mechanisms and intensified market competition. In many regions, it has even been questioned as a scam and was once associated with pyramid schemes. This is mainly because some bad actors have exaggerated its mining mechanism and expectations of token appreciation, misleading investors, which has impacted its reputation and left a mess.
Despite this, distributed storage, as an important track of Web3 infrastructure and a key technology to combat the monopoly of centralized cloud services, still attracts the attention of many entrepreneurs and investors. From protecting user privacy to enabling data sovereignty, the rise of emerging projects such as Walrus has further ignited market enthusiasm.
In this article, Mankiw will discuss how distributed storage protects user privacy through encryption and decentralization, the regulatory attitude of the Chinese mainland government towards this technology, the commercial potential of distributed storage, and more importantly, the legal compliance points that Web3 entrepreneurs need to pay special attention to when developing distributed storage projects. Distributed storage has prospects and is the future, but only by being legal and compliant can the project be made bigger and stronger.
Why distributed storage is needed: We all want privacy
Have you ever had such an experience? One day I just searched for teeth whitening casually, but after that I received harassing calls from various dental institutions every day, and the sales service was so accurate that it was disturbing. When and where was your data leaked? This year's 315 Gala tore open the technical veil of data black industry and exposed the chaos of personal information being traded wantonly. When data becomes the core production factor, security and privacy should become the bottom line that cannot be crossed. More and more people are beginning to realize that privacy, data privacy, is very important. At this year's 315 Gala, we were shocked to see that many technology companies illegally processed more than 10 billion user information every day through various means, including sensitive data such as mobile phone numbers, consumption records, and social accounts. There are also systems that steal corporate public accounts and WeChat group member information, forming a black industry closed loop of "data theft-precision marketing-commercial realization". Privacy is a topic that continues to be discussed. Ethereum founder Vitalik also recently wrote in his personal blog, "Why I Support Privacy", a 10,000-word article: "Privacy does not mean alienation from each other, but solidarity. Privacy is not an independent existence, but a common foothold." Why do we want privacy? Everyone has a different answer. He divided his answer into three parts: Privacy is freedom: Privacy provides us with space to live in a way that best suits our needs without having to worry about how our actions will be viewed in various political and social games. Privacy is order: A series of mechanisms that support the basic operation of society rely on privacy to function properly.
Vitalik also put his overall argument for privacy in one sentence as follows: Privacy provides you with the freedom to live your life in the way that best suits your personal goals and needs, without having to constantly balance between the "private game" (your own needs) and the "public game" (the reactions and views of various other people, through various mechanisms, including social media emergence, business incentives, politics, institutions, etc.)
Looking back, as early as 1993, the Cypherpunk Manifesto launched a call for privacy and freedom———— "Privacy is the power to selectively show yourself to the world... We are using cryptography, anonymous email forwarding systems, digital signatures and electronic currencies to defend our privacy." Bitcoin is not a sudden emergence, but a culmination of historical arduous exploration. Now this privacy road is going further and further.
We need distributed storage because we all desire privacy.
Look at the data: How broad is the business prospect
The essence of blockchain technology is decentralization. The characteristics of distributed storage that cannot be tampered with and information encryption are in line with the development direction of "decentralization" in the Web3.0 era. It is an indispensable part of the future development and implementation of blockchain, and the business prospects are naturally very broad.
Let's look at the data:
According to Grand View Research, the global data storage market will be worth $62.83 billion in 2023, with a compound annual growth rate (CAGR) of 9.8% from 2024 to 2030, and the market size will exceed $100 billion by 2030.
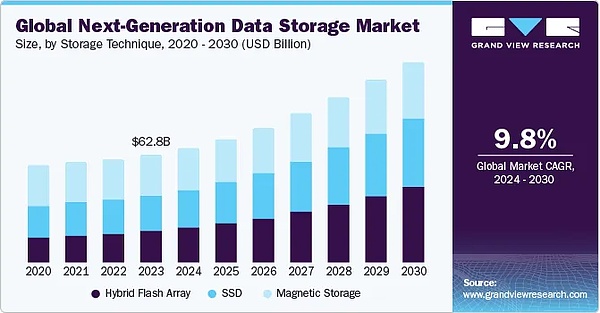
According to the latest research by MRA, the distributed storage market alone is expected to grow from approximately $15 billion in 2025 to over $50 billion in 2033, with a CAGR of approximately 16%, and the highest adoption rate in the commercial sector.
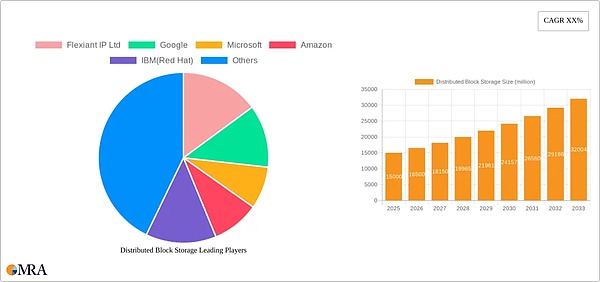
It can be seen that the distributed storage market has strong growth potential and broad business space. More and more blockchain project infrastructures are using distributed storage, and governments, enterprises, and individuals around the world are gradually adopting it. For example, Google Chrome supports built-in IPFS components, Ethereum has achieved full access to the IPFS network, and domestic Internet giants such as Tencent, Baidu, and Alibaba have also begun to deploy related technologies. The increasing integration of distributed storage with other technologies such as artificial intelligence and machine learning will also release more opportunities.
China's attitude towards distributed storage
Friends who often read Mankiw Law Firm's research and analysis must be familiar with the fact that there are three legal bottom lines that cannot be touched when starting a Web3 project in mainland China. In distributed storage projects, users earn tokens by maintaining and improving project infrastructure. Tokens can generate liquidity through exchanges or other means. It seems easy to touch the last two negative lists mentioned above.
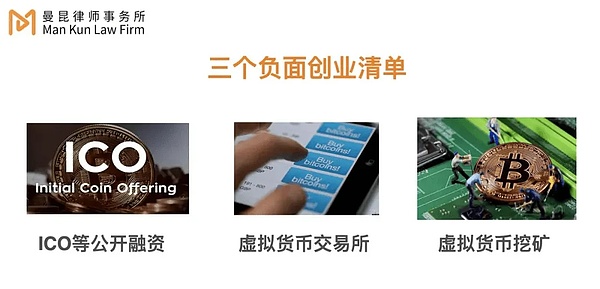
The People's Bank of China and ten other departments also jointly issued the "Notice on the Rectification of Virtual Currency "Mining" Activities" in September 2021. The "Notice" pointed out that the country does not support virtual currency "mining" projects such as Bitcoin in order to achieve the goal of energy conservation and emission reduction.
However, distributed storage projects such as Filecoin, the incentive layer of IPFS, are completely different from Bitcoin in proof of work. They do not consume a lot of electricity resources, but can improve the utilization rate of idle resources. They only need to provide storage space and bandwidth. When the project does not involve too much Token discussion and is viewed purely from a technical perspective, the policy compliance risk is theoretically small. The "Notice" also pointed out that "mining" should be distinguished from blockchain and big data related industries, and the development of high-tech industries with low resource consumption and high added value should be guided. From the national and government levels, distributed storage technology itself is not only not restricted by policies, but has also been optimized and developed to a certain extent.
In addition, although my country does not deny the property attributes of virtual currency, it is strictly prohibited to use virtual currency tokens for financing, which is easy to touch the first category of negative lists, and the judicial practice of the effectiveness of contracts related to currency-related hardware equipment is still inconsistent. The article will explain how entrepreneurial teams can avoid related risks later.
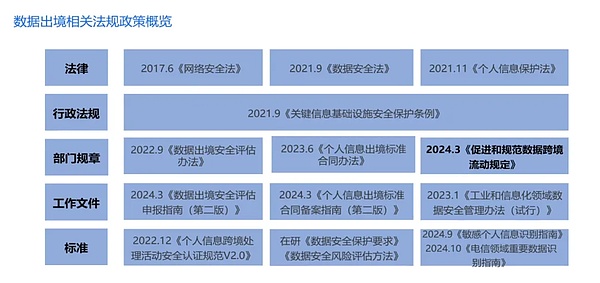
We can also see that the implementation of the "Data Security Law of the People's Republic of China" in September 2021 marks that my country's development and application of data resources has officially entered the track of rule of law. While providing legal protection for the data security of distributed storage, the "Data Security Law" also provides a new code of conduct for the data management of operating companies, leading the standardized reform in the field of IPFS from a legal perspective.
In general, mainland China is open to distributed storage and clearly distinguishes its essential difference from high-energy-consuming virtual currency mining. Regulations such as the "Data Security Law" provide legal guarantees for the standardization of the industry. Policies are not obstacles, but sieves, and only compliant projects can take advantage of the favorable conditions. For Chinese Web3 entrepreneurs, distributed storage may be a policy-feasible track.
The upstream and downstream of the project must all be compliant:
Unlike other Web3 projects, distributed storage projects are closely integrated with hardware equipment, forming an upstream and downstream industrial chain with clear division of labor. The project chain is very long, from technology development to hardware distribution to market promotion, every link may step on mines. The following is Mankiw's "Guide to Avoiding Pitfalls":
Upstream: Project team, don't just think about technology
The project team is the core, responsible for protocol design, business model design and operation coordination, but compliance must start from the first step. Focus on compliance from three aspects: company entity design, data security and cross-border compliance, and prevention of financial crimes.
1. Company entity: Going overseas is a way
Some things are restricted in China, and entrepreneurial projects can go overseas to seek development. More and more project parties choose to set up companies and teams overseas, and turn to areas that are more friendly to cryptocurrencies, such as Hong Kong, Singapore, Dubai, etc., which are all good choices. Only some support teams are retained in China. For teams that want to carry out distributed storage business, especially those with plans to issue tokens in the future, it is recommended to plan an overseas plan as soon as possible and arrange the project company entity overseas.
Attorney Mankiw advises:
2. Data security: Privacy is not just a slogan
Although distributed storage projects are decentralized in nature, they still involve a certain degree of centralized management and coordination in actual operations. Moreover, most distributed storage projects involve a large number of overseas users and need to publish data overseas through blockchain. Therefore, the issue of data outbound transfer has to be considered. Therefore, data compliance and data security need to be given priority consideration.
The project should comply with the privacy policy, explain to users how personal information is collected, used, stored and transmitted, and ensure compliance with legal requirements such as the Personal Information Protection Law. It is also necessary to obtain user consent. Before collecting and processing personal information, the purpose, method and scope of information processing should be clearly informed to users, and the user's explicit consent should be obtained. In addition, the principle of data minimization should be followed, and only the minimum amount of personal information required to achieve a specific purpose should be collected and processed.
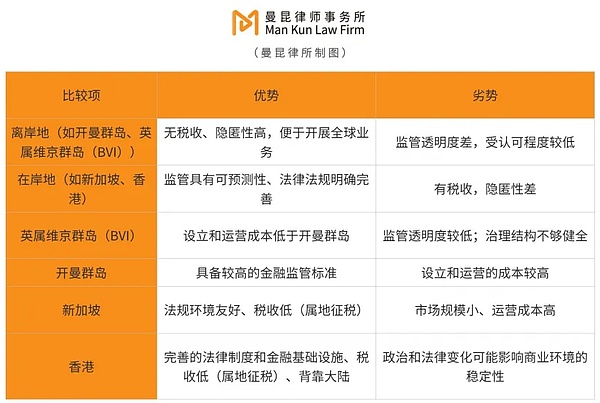
The project must also balance the differences in supervision in multiple jurisdictions. Enterprises going overseas must accurately grasp the compliance requirements of major markets. The Personal Information Protection Law requires that the export of personal information requires user consent and passes a security assessment, while GDPR (EU) emphasizes user privacy rights (such as the "right to be forgotten") and transparency.
Establish a data security management system:According to the requirements of the Cybersecurity Law and the Data Security Law, formulate and implement a comprehensive data security management system to ensure the security of data during storage, transmission and processing.
Data encryption:Use strong encryption technology to protect data in storage and transmission to prevent unauthorized access and data leakage.
Regular security assessment:Perform data security risk assessment and vulnerability scanning regularly, patch security vulnerabilities in a timely manner, and improve the security of the system.
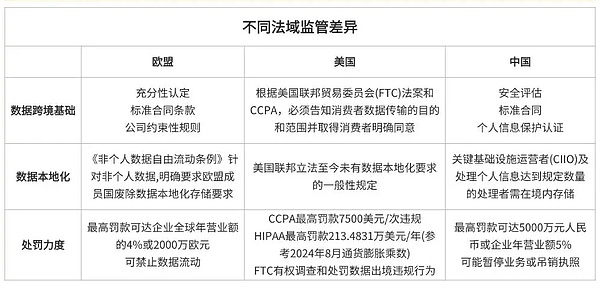
Distributed storage projects cannot do without cross-border data flow, after all, nodes are spread all over the world. However, the "Cybersecurity Law" and the "Data Security Law" mention that "important data" involving national security and public interests, for example, should be stored within the country. It is not that easy to transfer data overseas at will.
For example, if your project involves user information, you must conduct a security assessment before transferring it abroad to prove that the data will not be abused. The EU's GDPR also requires users to have the "right to be forgotten", and non-compliance will start with a fine. Therefore, before the project is launched, a project feasibility assessment must be conducted according to requirements, and a security assessment must be conducted before cross-border data transmission to ensure compliance with the regulations of relevant departments.
3. Anti-financial crime: KYC is not a decoration
Anti-money laundering and counter-terrorist financing are global red lines. Everyone knows KYC (know your customer), and the project should be strictly implemented to prevent fraud, protect the interests of users, and improve platform compliance. Users are required to provide identity documents (such as ID cards, passports, etc.) and proof of address for identity verification. User information is updated and reviewed regularly to ensure the accuracy of data.
A project party felt that it was "decentralized" and that the data was all on the chain, so there was no need to worry about KYC. As a result, a money laundering gang was mixed in with the users, and the project was directly blocked after the supervision was checked. Compliance is not a technical issue, but a survival issue.
Downstream ①: Hardware distributors
In the field of distributed storage, hardware sales, as a key link, often become a hotbed for pyramid schemes and illegal fundraising due to profit-driven.Learning from history, looking back at the Filecoin boom, many illegal companies, in the name of "IPFS" and "Filecoin", only promoted the added value of data storage, deliberately concealed investment risks, and caused a large number of investors to suffer losses. Two typical cases are particularly thought-provoking.
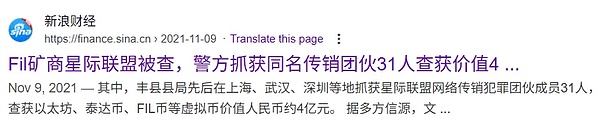
In the 2021 Xuzhou Filecoin mining machine fraud case,some distributors of IPFSUnion used "high returns" and "quick returns" as gimmicks to attract investors to buy Filecoin mining machines, but actually illegally absorbed funds through a multi-level distribution model, and the amount involved was as high as 400 million yuan. After the police intervened, they seized the relevant assets and arrested 31 people. Although IPFSUnion claimed that its employees only "assisted in the investigation", the incident has caused serious damage to the reputation of the project.
The Shenzhen Space Cloud Company case in 2023 was equally shocking. Space Cloud Company used the filpool.io platform to promote the "joint mining" project under the guise of selling Filecoin mining machines, which was actually a pyramid scheme. The case involved 607 million yuan (about 83 million US dollars), 62 million yuan in digital currency, and more than 57,000 registered members, further damaging the reputation of the Filecoin ecosystem.
The public prosecution agency determined that the defendants Lai Mouhang and others, on the grounds of mining FIL coins, required participants to pay mining machine fees or rental fees to obtain membership qualifications, developed downlines according to levels, used the number of people developed as the basis for rebates, and lured others to participate through high returns. Their actions have violated criminal law and they should be held criminally responsible for organizing and leading pyramid schemes.
To avoid such risks, Mankiw made the following suggestions:
Downstream ②: Promotion Team
In the field of distributed storage, the promotion team, as a key force in marketing and user acquisition, has become a hidden danger to the development of the industry due to the risk of false propaganda. False propaganda will not only mislead users, but may also violate the law and damage the overall reputation of the project.
As early as 2021, IPFS-related promotions attracted regulatory attention due to excessive exaggeration of benefits. Some promoters have launched highly tempting slogans such as "one machine for multiple mining" and "quick return on investment", deliberately magnifying investment returns, but not mentioning potential risks. This one-sided and exaggerated propaganda seriously violates the provisions of the Advertising Law on the authenticity and legality of advertising content, and also infringes on consumers' right to know, touching the red line of the Consumer Rights Protection Law. In the end, these improper propaganda behaviors damaged the reputation of the project and the market order fell into chaos.
In the same year, the China Communications Industry Association issued a warning, pointing out that some Filecoin promoters used "distributed storage value-added" as a gimmick, blindly promoted high returns, but ignored the illegal operation of risk notification. The regulatory authorities quickly intervened and took measures such as fines and rectification orders against companies that engaged in false propaganda, demonstrating their determination to rectify market chaos.
Mankiw lawyers suggest:
Ensure the objectivity of the promotional content: The promotion team should truthfully disclose the performance of the equipment and objectively present the uncertainty of the benefits to avoid misleading users. For example, when introducing a mining machine, it is necessary to clearly inform its actual computing power, operating environment requirements and other information, and at the same time, use historical data to reasonably estimate the profit range.
Strengthen risk warnings:In all promotional advertisements, clearly mark risk warnings in a conspicuous manner, such as "Investment is risky and returns are not guaranteed". Ensure that users can notice the risk warning content as soon as they receive promotional information.
Standardize promotional terms:Strictly avoid using absolute terms, such as "guaranteed returns" and "guaranteed profits" should be resolutely eliminated. Promotional content should be neutral and objective, using rigorous language and data to reduce legal risks and trust crises caused by exaggerated publicity.
Attorney Mankiw's summary
Distributed storage is the core infrastructure of Web3. It protects privacy through encryption and decentralization, meets users' needs for data sovereignty, and shows huge commercial potential.This year, CCTV's 315 Gala exposed the chaos of data black production, highlighting the privacy crisis of centralized storage. Distributed storage has become a key technology to combat data abuse. From the craze and lessons of Filecoin to the rise of Walrus, ensuring the legal operation of the entire upstream and downstream chain is the cornerstone of becoming bigger and stronger.
Upstream project teams can set up company entities by going overseas, design business models that adapt to different regulatory environments at home and abroad, and at the same time ensure data security and cross-border compliance, implement KYC measures, and prevent financial crime risks.
Downstream hardware distributors need to be wary of pyramid schemes and illegal fundraising risks. Sales talk should be standardized, risks should be disclosed, and legal loopholes should be reduced through compliance training and contract review.
Publicity and promotion teams should avoid false propaganda, regulatory penalties and market chaos, which will damage the reputation of the project. It is recommended that the promotion content be true and transparent, and clear risk warnings.
In fact, many people still know that distributed storage is just a branch of the DePIN track. The DePIN track also includes innovative projects such as Render Network (a leading AI computing project) and Hivemapper (decentralized encrypted map). These projects are committed to breaking the centralized monopoly and building a global interconnected physical infrastructure network ecosystem. Most of the DePIN tracks are closely integrated with hardware devices, and they also need to pay attention to upstream and downstream risks.
"Privacy is the cornerstone of freedom, order and progress." The Internet is in a decentralized revolution, and data distributed storage is a key infrastructure for the digital transformation of society. Expanding from distributed storage to the DePIN track is full of business prospects and future. In this entrepreneurial blue ocean, if a project wants to develop sustainably, it must be legal and compliant in order to grow bigger and stronger.
 Jasper
Jasper





















