Author: Bitrace; Source: PANews
As protocols such as Blast gradually open up pledge unlocking, most investors are about to usher in a good harvest, but for those who have lost their private keys for various reasons, this is a "countdown to death" again and again. ”.
Blast is a second-layer Ethereum network based on Optimistic Rollup, allowing users to stake ETH in Blast to earn points as a reference for airdrops of future project tokens. In the early stages of its launch, it took the market by storm through marketing campaigns. So far, the TVL of this agreement has reached 3 billion US dollars, and the number of users is more than 450,000. Blast’s money-attracting effect has led many Layer 2 players to imitate its “pledge assets and form teams with points” gameplay, and a large number of players have “locked” their funds for several months.
As protocols such as Blast gradually open up pledge unlocking, most investors are about to have a good harvest, but for those who have lost their private keys for various reasons For me, this is a "countdown to death" again and again.
Private key stolen while in pledge state
Recently, Bitrace has received multiple Blast, For assistance requests submitted by Manta users, the victim's private key was illegally obtained by hackers during the pledge period. After the pledge expires, the assets are at risk of being transferred by hackers. According to one of the victims, the wallet had been in normal use for many years and was stolen for unknown reasons. The assets on multiple chains were cleaned by hackers, of which a total of 9 ETH pledged in the Blast and Manta protocols had not yet been stolen.
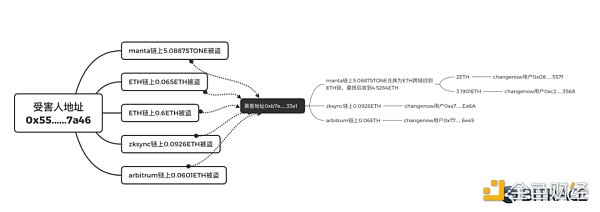
The Bitrace technical team analyzed the address provided by the victim. The victim entered 5.1 ETH into the Manta protocol at 19:45 that day, about 20 minutes later, Manta's pledge certificate stone was stolen. At the same time, the entire chain of assets in the victim's address was cleared and transferred to the hacker's address. From this, it can be seen that the reason for the theft is probably that the private key was leaked.
Subsequently, the hacker braved the wear and tear and exchanged the stone worth 5 ETH across the chain for about 4.5 ETH, and entered changenow in two transactions to clean and cash out. Participating in this type of ETH staking protocol interaction, if the user withdraws it before the official unlocking, he needs to use a third-party cross-chain bridge to bear a certain amount of asset wear and tear. Hackers are eager to keep the stolen money as their own. It can be said that "take away the baht and use it like mud" sand".
Interpretation of case techniques
After further communication with the victim, the Bitrace technical team discovered the private The reason for the key leak was that the private key was stolen due to a Trojan in the victim's computer. The function of the Trojan is to open a backdoor in the Win computer, which can be used to silently download and run any malicious software in the background. This means that private keys are at great risk of exposure.
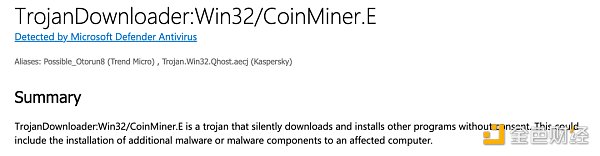
So, how to keep the private key properly and prevent assets from being stolen? The following are some high-risk operations that lead to the disclosure of private keys:
Download the fake wallet APP. Wallets download, install or use virtual currency wallets other than the official website through risky channels, including but not limited to: app stores, search engines, installation files sent by friends, etc. Once the user imports the private key into the fake wallet, the hacker will have a clear view of it in the background, which is tantamount to handing over the assets to others. The correct approach is to download it after confirming the accuracy of the official wallet website through cross-comparison with multiple parties.
The private key is saved online. When a user creates a wallet for the first time, a pop-up window will appear, prompting the user to record and save the mnemonic phrase and private key. Many users will copy and paste or take screenshots and save them to photo albums, mailboxes, QQ space, and WeChat assistants. Such behavior can easily lead to private keys being obtained by others through illegal channels. A relatively safe approach is to write down the mnemonic phrase by hand and save it.
Trojan virus. Computers download risky software from unknown sources, causing malicious code to be run, monitoring computer behavior, stealing clipboard permissions, and thus stealing private keys. Computers used for on-chain interactions should be regularly screened for software.
How to recover the private key if it is lost
Private key Being stolen does not mean that the assets are hopeless to be recovered. At present, some victims have successfully recovered the ETH pledged in the Blast protocol through technical means.
Bitrace’s advice to the sufferers is:
Transfer the remaining assets of multiple chains to stop loss at the first time. The victim should immediately check the remaining assets in the account as soon as they discover the theft. If so, be sure to move it to another safe place immediately.
Determine the cause of the theft and promptly request law enforcement intervention. The victim can seek help from a professional security company to determine the cause of the theft and analyze the address behavior on the chain to determine the hierarchical flow of funds. On this basis, prepare a report document explaining the whole story of the incident, go to the law enforcement unit in the jurisdiction where the individual lives and where the theft occurred, report the incident, and try to make a record. Only when the case information is entered into the public security system will there be a possibility of returning the stolen goods in the future.
Find professional technology companies to execute front-running transactions. For situations like the one mentioned in this article where the private key is stolen but there are still unlocked assets in the wallet, the victim can ask a technology company to write code to defeat the hacker in order to recover the assets.
Write at the end
Bitrace reminds everyone, be sure to Do a good job of wallet separation, use separate wallets to store large funds, and only use daily wallets to interact with other contracts. If unfortunately it is stolen, you should actively track the whereabouts of your assets, monitor the behavior of key addresses at all times, or contact a security company for help.
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance JinseFinance
JinseFinance Bernice
Bernice Aaron
Aaron JinseFinance
JinseFinance Bitcoinist
Bitcoinist 链向资讯
链向资讯 Ftftx
Ftftx Cointelegraph
Cointelegraph Cointelegraph
Cointelegraph