Author: day, vernacular blockchain
Recently, users of BN and OK have both had their assets stolen. Asset security-related issues have once again aroused heated discussions. Some users immediately proposed to remove tokens from trading platforms as soon as the news came out. After all, a gentleman should not stand under a dangerous wall.
The development of this wave of market conditions can clearly feel that the industry's big opportunities are mainly concentrated on the chain, and the trading platform is seriously involuted. With the collapse of the value investment system, it is extremely difficult for retail investors to make money on the trading platform. The number of users turning to the chain is also gradually increasing, and on the chain, the most important issue is the security of their own wallets.
Next, we will comprehensively understand how to protect the security of blockchain assets from several aspects, including wallet-related knowledge, theft cases, and knowledge of protecting private keys.
01 Wallet-related knowledge
Before ensuring the security of your own assets, you need to have a certain understanding of some basic knowledge about wallets in the industry in order to better understand how to protect your assets. Next, I will briefly introduce several related concepts.
1. Symmetric encryption and asymmetric encryption
Before understanding public (private) keys, let's first briefly understand symmetric encryption and asymmetric encryption in cryptography.Symmetric encryption means that A can get B through a certain algorithm, and conversely, B can also reversely decrypt A through the same algorithm. Here, encryption and decryption use the same algorithm; and asymmetric encryption means that A can get B through a certain algorithm, but B cannot reversely decrypt B through the same algorithm. Here, encryption and decryption require different algorithms.
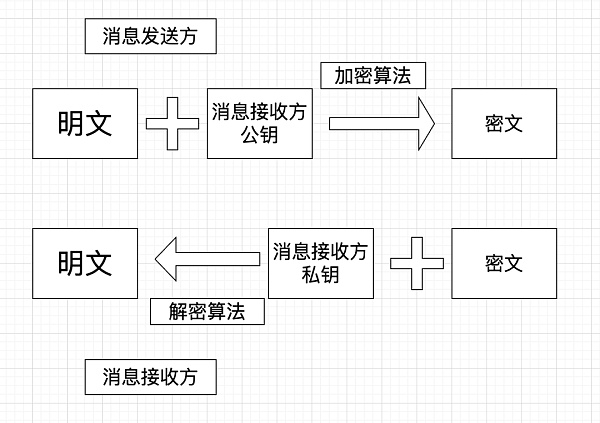 As shown in the figure, the difference between symmetric encryption and asymmetric encryption lies in whether the public key of the message receiver and the private key of the message receiver in the figure are the same key.
As shown in the figure, the difference between symmetric encryption and asymmetric encryption lies in whether the public key of the message receiver and the private key of the message receiver in the figure are the same key.
2. Public (private) key, mnemonic, address
Knowing about symmetric encryption and asymmetric encryption can help you better understand some basic concepts related to wallets.
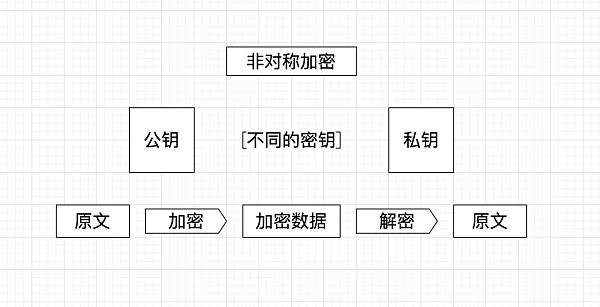
Key pair: In asymmetric encryption, there is a pair of key pairs, namely public key and private key. The public key is public and the private key is not public.
Public key: It is used to encrypt data. Data encrypted with the public key can only be decrypted with the private key.
Private key: The private key can generate the public key, which is used to decrypt the data encrypted by the public key.
Address: Corresponding to the "public key", because the public key is too long, there is an "address", and the address is generated by the public key.
Mnemonic: Corresponding to the "private key", because the private key is a randomly generated string, which is too long and difficult to remember, a group of human-readable words were born to replace the private key to help users remember the private key, usually 12 irregular phrases. (Private key = mnemonic)
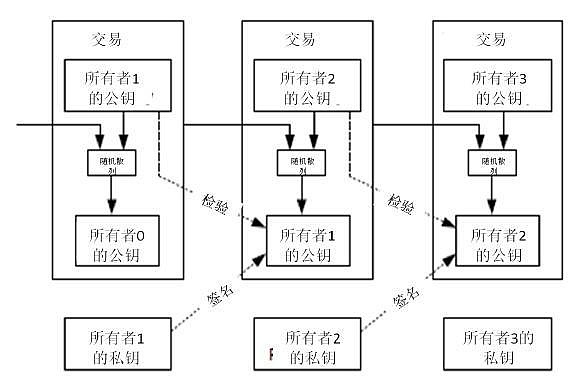 Image source network: On-chain transaction process
Image source network: On-chain transaction process
Electronic signature: A piece of information (you transfer 100 Ethereum to someone), this information needs to be signed by your private key and broadcast to the blockchain.
Signature verification: The receiving end can verify that the message is indeed signed by your private key through your public key, that is, you published it, and the transaction record is on the chain. Therefore, whoever has the private key has the wallet.
To put it simply, the public key (address) is equivalent to your account number, and the private key (mnemonic) is equivalent to your account number + password (private key can generate public key).
Using a bank card as an analogy, public key = bank account, address = bank card number, password = bank card password, private key = bank card number + bank card password, mnemonic = private key = bank card number + bank card password, Keystore + password = private key.
3. Preservation of private key (mnemonic)
Your Token is not stored in your wallet APP, but in the address corresponding to the private key in the blockchain network. As long as you have the private key, you can log in to all wallets through the private key (the wallet supports the chain where you have the Token). The wallet is only the front end of the account funds display and does not save your private key.
If the private key is lost, it means that your assets will also be lost and cannot be retrieved through the wallet. When registering a wallet for the first time, the wallet page will generally remind users to pay attention to this. This is completely different from the QQ and WeChat we used before. If the password is lost, it can be retrieved through mobile phone verification, questions and friend verification. Of course, this is also the charm of blockchain decentralization. Your assets belong entirely to you.
4. Wallet types
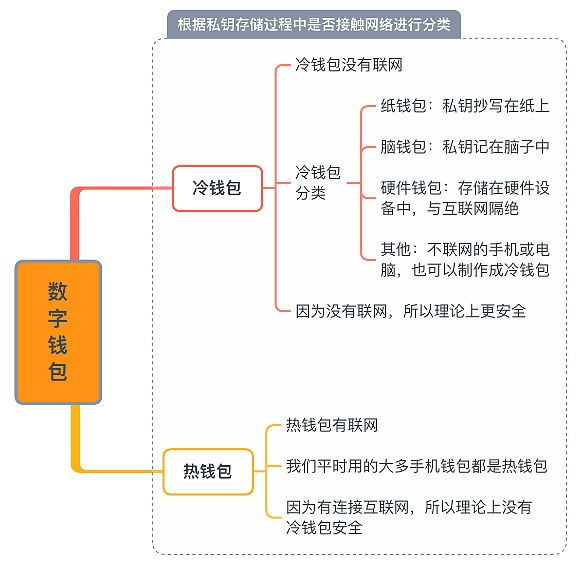 According to whether the private key is online, the wallet can be divided into hot wallets and cold wallets, as shown above.
According to whether the private key is online, the wallet can be divided into hot wallets and cold wallets, as shown above.
Hot wallet: client wallet, plug-in wallet, mobile APP.
Easy to use, easy for novices to operate, high efficiency of transaction transfer, poor security, easy to be stolen.
Cold wallet: hardware wallet.
High security, suitable for storing large assets, complex creation, troublesome transfer, hardware damage or loss of private keys may cause the loss of digital assets.
Through the above, we can know that private key is everything, and all our measures to protect assets are actually to protect private key, protect private key, and protect private key. (Prevent the loss of private key and acquisition by others)
02 Theft Case
After understanding the relevant concepts, let's take a look at the main cases of loss at present. Through the cases, we can better protect our own wallets.
1. Private key (mnemonic) leakage
In early 2021, Yiren, the founder of Shengcaiyoushu, saved the Bitcoin private key in the cloud notebook, resulting in the loss of eight-digit BTC assets.

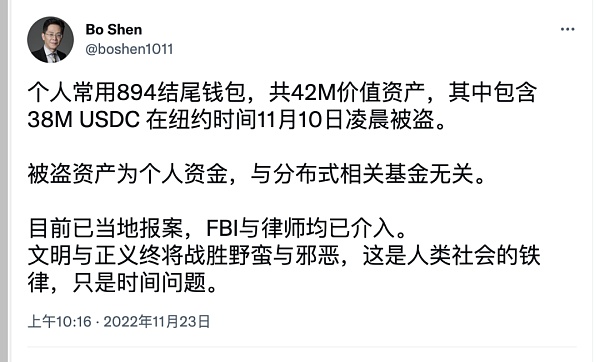
In November 22, Shen Bo, the founder of Distributed Capital, had his digital assets worth $42 million stolen, including 38,233,180 USDC, 1,607 ETH, 719,760 USDT and 4.13 BTC. According to the subsequent analysis of the security agency SlowMist, the theft was caused by the leakage of the mnemonic phrase.
2. Private key (mnemonic phrase) lost
British IT engineer James Howells lost his computer hard drive in 2013, which contained 8,000 bitcoins. Nine years later, he planned to spend $74.3 million to search through the garbage dump to retrieve the computer hard drive.
3. Click on the virus link
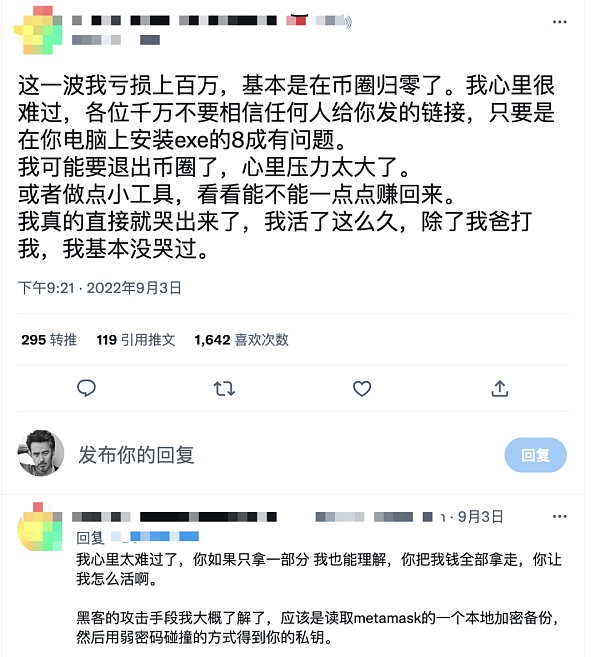
A user randomly clicked on the link sent by others, causing the hacker to read the metamask local encrypted backup and all assets were stolen.
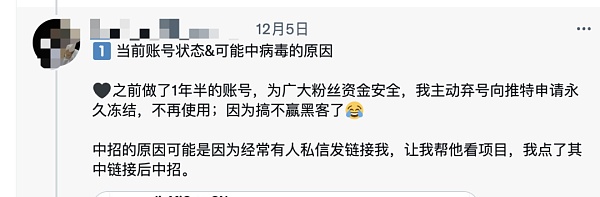
A Twitter KOL clicked on a private link sent by others, causing his Twitter account to be stolen, and then released a virus-infected airdrop information, using the fans' trust in the KOL to click on the link to steal the fans' assets.
4. Random authorization, application vulnerabilities
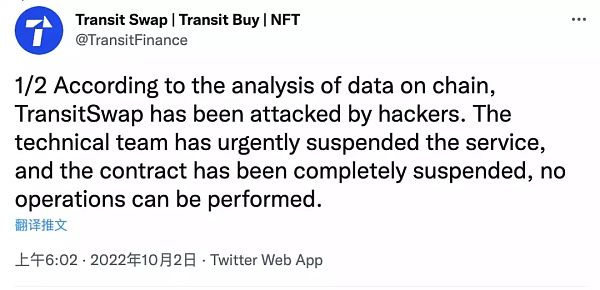
On October 2, Token Pocket's flash exchange DEX Transit Swap officially stated that it was attacked by hackers, with asset losses exceeding 15 million US dollars, and reminded users to cancel authorization.
On October 11, the plug-in wallet Rabby developed by the DeBank team said that there was a vulnerability in its Swap contract and suggested that users cancel the Rabby Swap authorization. In the end, the hacker made a profit of more than 190,000 US dollars.
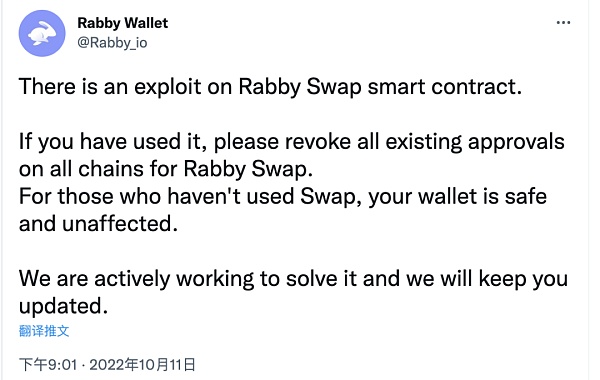
5. Download fake APP (with virus software)
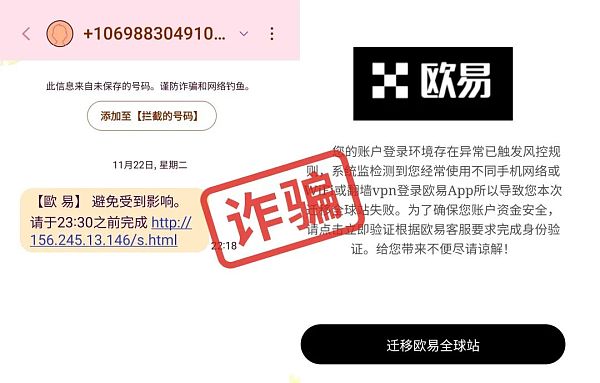
After obtaining the platform user information, some hackers spread panic information to users through text messages, saying that the platform is no longer safe and they need to click on the link to reinstall the application or log in to the account. After logging in, the account funds were stolen.
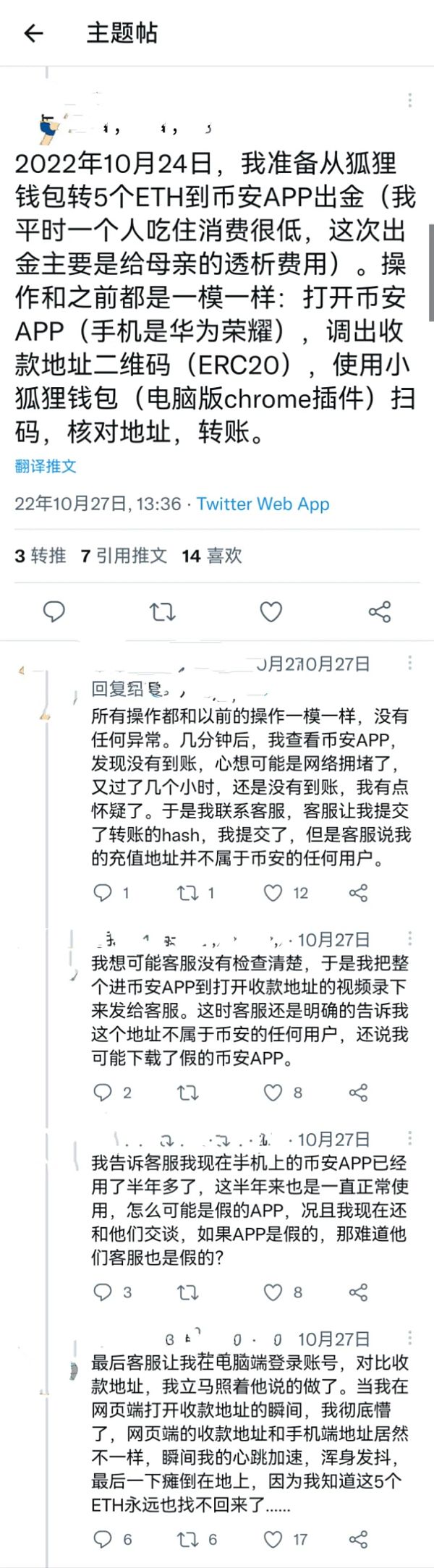
A user downloaded a fake Binance app and transferred money to other people's addresses, and 5 ETH of assets were completely lost.
From the above cases, we can see that user assets are stolen mainly in the following situations: private key (mnemonic) leakage, private key (mnemonic) loss, clicking on virus links, arbitrary authorization, application vulnerabilities, downloading fake APP (with virus software), etc..
Next, let's sort out what methods can be used to avoid the above situations.
03 How to avoid property loss
1. Preservation of private key (core: not easy to lose, not easy to damage, and cannot be accessed or used by others)
Back up the wallet in time after it is generated, double backup, because once lost, it will be impossible to retrieve
The mnemonic is saved on a medium that is not connected to the Internet and is not easy to lose or damage, such as copying it on paper and encrypting it yourself (adding or reducing specific characters for easy memory); find a camera storage for a mobile phone that is never connected to the Internet; some wallet providers will sell iron plates related to mnemonics.
Use a cold wallet (hardware wallet) and choose a well-known cold wallet; it should be purchased from official channels, not through third-party channels (third-party channels may have viruses); set a strong password and back up the private key at the same time to prevent the hardware wallet from being lost or damaged.
2. Prevent private key (mnemonic) leakage
Do not copy and paste private keys, some software can read the user's clipboard
Do not save private keys in WeChat collections, transfer files, Baidu Cloud, Evernote and other online platforms
Never tell anyone your private key, remember, it is anyone, some scammers pretend to be official wallet people to cheat your private key, don't believe it, the wallet party has no right to obtain the user's private key
When using public Wi-Fi, do not copy and paste private keys
Download various applications, you should go to official channels, all application stores are sometimes unreliable (remember, all), there are fake applications
Be cautious when signing wallets, DeFi Heavy users of the protocol and NFT interaction, remember to revoke authorization in time to prevent asset theft after a vulnerability in the application
Do not click on links (text messages) sent by others, download files shared by others, and do not click on links from kols at will, as they may contain viruses
Once you find that your wallet has a little asset leakage, you should abandon the wallet as soon as possible, and do not take any chances
Do not use free VPN
Keep up with the news and learn about new stolen information in real time
If you play more on the chain, it is recommended to install the ScamSniffer browser plug-in, which can intercept and prompt you when you visit phishing websites, and will also prompt you when you browse fake official replies.

All of the above measures are actually to protect your private key from being leaked, Not your key, not your money!
3. Dispersed assets
You can disperse your funds among wallets and trading platforms. Although FTX encountered problems, which led to a lack of trust in centralized trading platforms, for most people, it is much safer to keep their assets on several centralized leading trading platforms than to hold them in their own hands. It is also more convenient than a wallet. As long as the losses are not particularly large, several leading platforms can generally afford the compensation.
There are a few points to note when using a centralized trading platform:
Enable triple verification (mobile phone, email, Google secondary verification)
Enable Token withdrawal whitelist
Download the App from the official channel
When transferring money, confirm that the address is correct
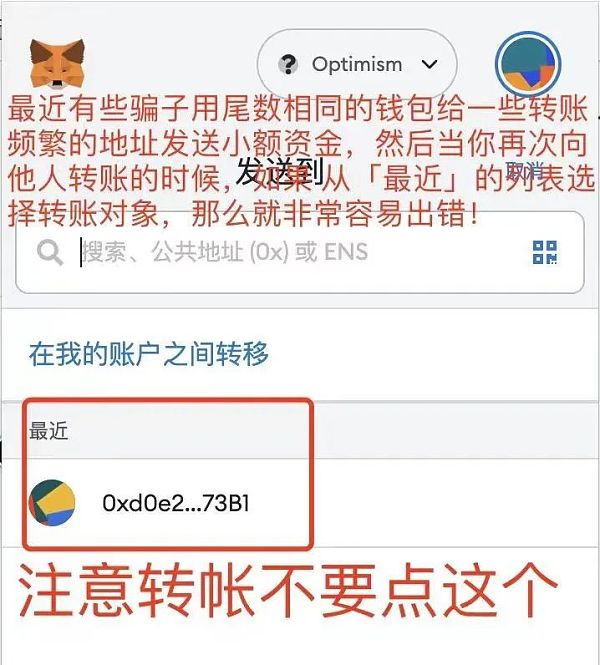 Image source network
Image source network
In addition, when using a browser to log in to the official website of the trading platform, BN officials give several security suggestions:
Isolation— Create a separate chrome user to log in to DAPP, and do not install plug-ins;
Clear — For APPs involving funds, remember to log out in time after logging in to the webpage;
Traceless — Open the webpage in incognito mode and disable any plug-ins;
Privacy — Funds are operated on a separate computer or Apple mobile phone, which is more secure
Permission — When it comes to fund permissions, it is recommended to set it to log out immediately after a few minutes.
04 Conclusion
Through the above-mentioned relevant knowledge, novice users can have a comprehensive understanding of the relevant knowledge of blockchain asset security. With the development of blockchain and the increase of on-chain interactions, the use of wallets will gradually become an important basic skill. Various measures are actually not absolutely safe, but relatively speaking, they can help us avoid most pitfalls. With the development of blockchain, new problems will continue to emerge, and we need to continuously improve our knowledge reserves.
Small amounts of funds may not be kept in the above manner, but you must be very careful when keeping large amounts of funds, because a mistake may cause you to be left behind by the blockchain train forever and never catch up.
 JinseFinance
JinseFinance




















