Background
Wallets play a vital role in the Web3 world. They are not only a storage tool for digital assets, but also a necessary tool for users to conduct transactions and access DApps. In the previous issue of the Web3 Security Guide, we mainly introduced the classification of wallets and listed common risk points to help readers form a basic concept of wallet security. With the popularity of cryptocurrency and blockchain technology, the black industry has also set its sights on the funds of Web3 users. According to the theft forms received by the SlowMist Security Team, it can be seen that many users have been stolen due to downloading/purchasing fake wallets. Therefore, in this issue, we will explore why fake wallets are downloaded/purchased, as well as the risk of private key/mnemonic leakage, and will also provide a series of security suggestions to help users ensure the safety of their funds.
Download to fake wallets
Since many mobile phones do not support Google Play Store or because of network problems, many people will download wallets from other channels, such as:
Third-party download sites
Some users will download wallets through third-party download sites such as apkcombo, apkpure, etc. These sites often claim that their apps are downloaded from Google Play Store mirrors, but how safe are they? The SlowMist security team has investigated and analyzed third-party sources of Web3 fake wallets, and the results show that the wallet version provided by the third-party download site apkcombo does not actually exist. Once a user creates a wallet or imports a wallet mnemonic on the start interface, the fake wallet will send the mnemonic and other information to the server of the phishing website.

Search Engines
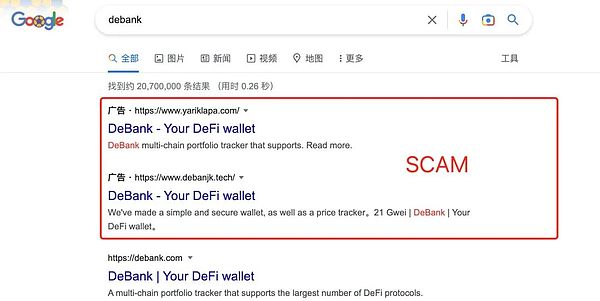
The ranking of search engine results can be bought, which has led to the situation where fake official websites are ranked higher than the real official websites. Therefore, it is not recommended that users search for wallets directly through search engines and then click on the top-ranked links to download wallets. This is likely to lead to a fake official website and then download a fake wallet. If users do not know what the official website address is, it is difficult to determine whether it is a fake website based on the website's display page alone, because the fake websites created by scammers are very similar to the real official websites and can be mistaken for the real ones. Therefore, it is also not recommended that users click on links shared by other users on Twitter or other platforms, which are mostly phishing links.
Friends and relatives/pig-killing
In the blockchain dark forest, you must maintain zero trust. Your friends and relatives may not have the intention to harm you, but the wallet they download may be fake, but it has not been stolen yet. So if you download the wallet through the QR code/link they share, you may also download a fake wallet.
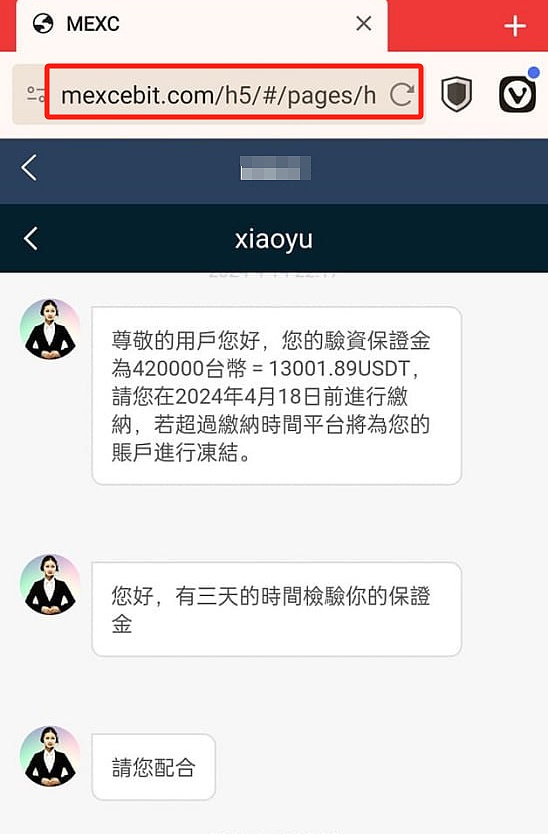
The SlowMist Security Team has received many stolen forms from the pig-killing incident. The scammers often gain the trust of the victim first, then guide the victim to participate in cryptocurrency investment and share the download link of the fake wallet. In the end, the victim is deceived and loses money. Therefore, the majority of users should be vigilant against netizens, especially when the other party pulls you to invest or sends you an unknown link, don't believe it easily.

Telegram
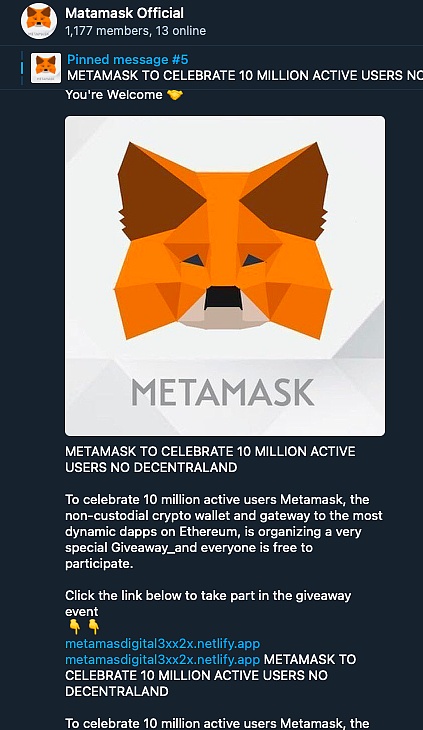
On Telegram, by searching for well-known wallets, we found some fake official groups. The scammers claimed that the group was the official channel of a certain wallet, and even reminded users in the group to identify the only official website link. However, these links are all fake.
Application Store
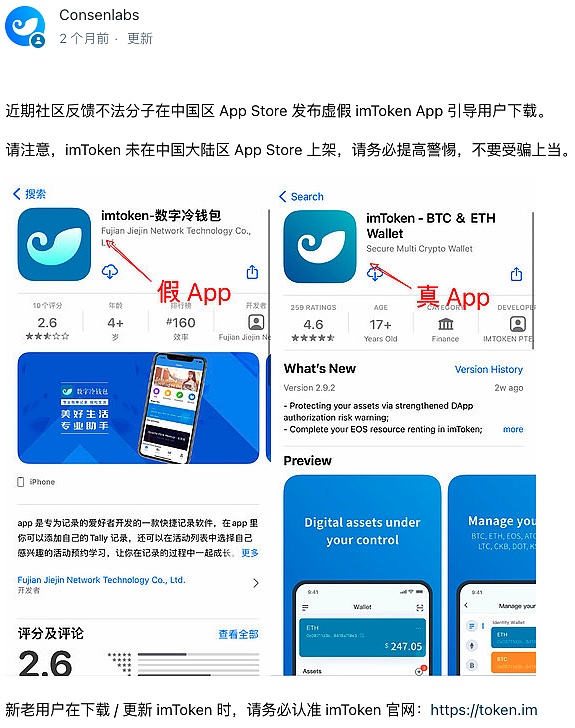
It is important to remind you that the applications in the official application store are not necessarily safe. Some criminals induce users to download fraudulent apps by purchasing keyword rankings and other methods. Please be careful to identify them.
So, how can users avoid downloading fake wallets?
Official website download
The ability to find the real official website is not only used when downloading the wallet, but also when users participate in Web3 projects later, so we will talk about how to find the correct official website here.
Users may search for the project party directly on Twitter, and then judge whether it is an official account based on the number of followers, registration time, and whether there is a blue label or a gold label. However, these can be faked. Previously, we talked about the black and gray industries that sell high-imitation accounts in the article "True and false project parties | Beware of high-imitation account phishing in the comment area". Therefore, it is recommended that newbies first follow some security companies, security practitioners, well-known media, etc. in the industry on Twitter to see if they follow the official account you found.
(https://twitter.com/DefiLlama)
Through the above method, users have a high probability of finding the real official Twitter account, but we still need to do multi-party verification. After all, official Twitter accounts are often hacked, and hackers will also replace the official website link on the official account with a fake official website link. Therefore, users need to compare the official website link they just found with the link found through other channels (such as DefiLlama, CoinGecko, CoinMarketCap, etc.):
(https://twitter.com/DefiLlama)
src="https://img.jinse.cn/7227201_image3.png">
(https://landing.coingecko.com/links/)
After finding and confirming the official website link, it is recommended that users save the link to bookmarks, so that they can find the correct link directly from the bookmarks next time, without having to find and confirm it again every time, reducing the probability of entering a fake official website.
App Store
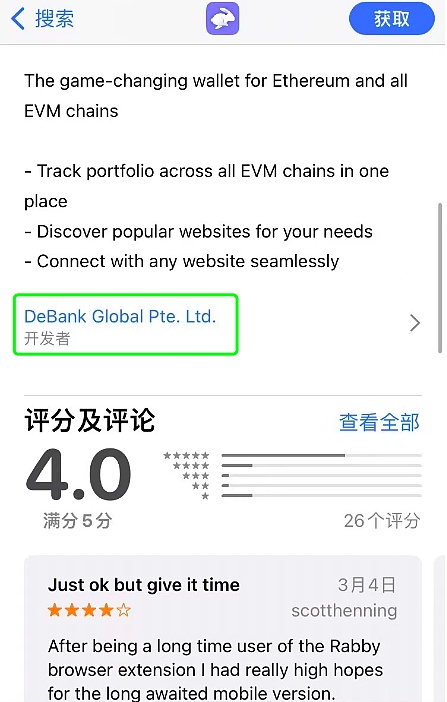
Users can download wallets through official app stores such as Apple Store, Google Play Store, etc., but before downloading, be sure to check the app developer information first to ensure that it is consistent with the official developer identity, and you can also refer to the app rating, download volume and other information.
Official version verification
Some readers who have read this may wonder, how can you verify whether the wallet you downloaded is a real wallet? Users can do a file consistency check, which is to determine whether the file has been changed during transmission or storage by comparing the hash value of the file. Users only need to drag the previously downloaded apk file into the file hash verification tool, and this tool will use hash functions (such as MD5, SHA-256, etc.) to generate the hash value of the file. If this value matches the official hash value, it is a real wallet; if it does not match, it is a fake wallet. What should users do if they verify that their wallet is fake?
1. First, confirm the scope of the leak. If you just downloaded the fake wallet but did not enter the private key/mnemonic, just delete the app and re-download the official version.
2. If the private key/mnemonic has been imported into the fake wallet, it means that the private key/mnemonic has been leaked. Please go to the official website to download the genuine wallet and import the private key/mnemonic, and create a new address to quickly transfer transferable assets.
3. If your cryptocurrency is unfortunately stolen, we will provide free community assistance services for case evaluation. You only need to submit the form according to the classification guidelines (funds stolen/fraud/extortion). At the same time, the hacker address you submitted will also be synchronized to the InMist Threat Intelligence Cooperation Network for risk control. (Note: Submit the Chinese form to https://aml.slowmist.com/cn/recovery-funds.html, and submit the English form to https://aml.slowmist.com/recovery-funds.html)
Purchasing a fake hardware wallet
The above situation is why a fake wallet is downloaded and the solution. Let’s talk about why a fake hardware wallet is purchased.
Some users choose to buy hardware wallets in online malls, but this kind of hardware wallet from unofficial authorized stores has a very big security risk, because before the wallet reaches the user, it will pass through many hands, and whether the internal components have been tampered with, these are all uncertain. If the internal components have been tampered with, it is difficult to see the problem from the appearance and function.
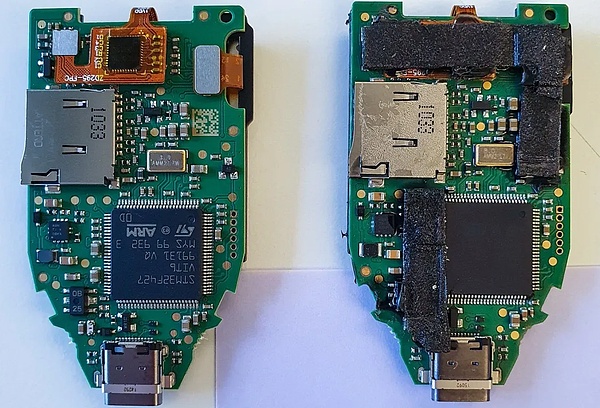
(https://www.kaspersky.com/blog/fake-trezor-hardware-crypto-wallet/48155/)
Here are some of the ways we provide to deal with hardware wallet supply chain attacks:
Purchase from official channels: This is the most effective way to solve supply chain attacks. Do not purchase hardware wallets from unofficial channels, such as online malls, purchasing agents, netizens, etc.
Check the appearance:After getting the wallet, first check whether the outer packaging has been damaged. This is the most basic, although hackers are unlikely to be exposed at this step.
Official website real machine verification:Some hardware wallets provide official website real machine verification services. When the user initializes the wallet, the device will prompt the user to perform official website real machine verification. If the device is tampered with during transportation, it will not pass the official website real machine verification.
Disassembly self-destruction mechanism:You can choose to buy a hardware wallet with a disassembly self-destruction mechanism. When someone tries to open the hardware wallet and tamper with the internal components, the self-destruction mechanism will be triggered, and all sensitive information in the security chip will be automatically erased, and the device will no longer be usable.
Risk of private key/mnemonic leakage
Through the above content, everyone should learn how to download or purchase a real wallet, then how to keep the private key/mnemonic safe is another problem. The private key/mnemonic is the only credential to restore the wallet and control the assets. The private key is a 64-bit hexadecimal string composed of letters and numbers, and the mnemonic is generally composed of 12 words. The SlowMist Security Team hereby reminds that if the private key/mnemonic is leaked, the wallet assets are very likely to be stolen. Let's take a look at some common reasons for the leakage of private keys/mnemonics:
Improper confidentiality: Users may tell their relatives and friends about their private keys/mnemonics and ask them to help keep them, but the funds are stolen by their relatives and friends.
Storing or transmitting private keys/mnemonics on the Internet:Some users, although knowing that private keys/mnemonics should not be told to others, will save private keys/mnemonics through WeChat collection, taking photos, screenshots, cloud storage, memos, etc. Once these platform accounts are collected and successfully hacked by hackers, private keys/mnemonics can be easily stolen.
Copying and pasting private keys/mnemonics:Many clipboard tools and input methods will upload users' clipboard records to the cloud, exposing private keys/mnemonics to an unsafe environment. Moreover, Trojan software can also steal information in the clipboard when users copy private keys/mnemonics. Therefore, it is not recommended that users copy and paste private keys/mnemonics. This seemingly harmless behavior actually poses a great risk of leakage.
So how to avoid private key/mnemonics leakage?
First, do not tell your private key/mnemonic to anyone, including relatives and friends. Secondly, try to choose physical media to save your private key/mnemonic to prevent hackers from obtaining your private key/mnemonic through network attacks and other means. For example, copy your private key/mnemonic onto good quality paper (you can also seal it in plastic) or use a mnemonic secret box to save it. In addition, setting up multiple signatures and decentralized storage of private keys/mnemonics can also improve the security of private keys/mnemonics. For how to back up private keys/mnemonics, you can read the "Blockchain Dark Forest Self-Guard Handbook" produced by SlowMist: https://github.com/slowmist/Blockchain-dark-forest-selfguard-handbook/blob/main/README_CN.md.
Summary
This article mainly explains the risks when downloading/purchasing wallets, how to find the real official website and verify the authenticity of the wallet, and the risk of private key/mnemonic leakage. I hope that the content of this issue can help you take the first step into the dark forest. In the next issue, we will explain the risks when using wallets, such as phishing, signature, and authorization risks. Welcome to follow. (Ps. The brands and pictures mentioned in this article are only for the purpose of assisting readers' understanding and do not constitute recommendations and guarantees).
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance Edmund
Edmund Edmund
Edmund Clement
Clement Bitcoinworld
Bitcoinworld Kikyo
Kikyo Bitcoinist
Bitcoinist Cointelegraph
Cointelegraph Cointelegraph
Cointelegraph Cointelegraph
Cointelegraph