Author: Scam Sniffer; Translation: 0xjs@金财经
Introduction
Wallet Drainers is a type of cryptocurrency-related malware that has been used in the past. There was a huge "success" in the middle of the year. The software is deployed on phishing websites to trick users into signing malicious transactions that steal assets from their cryptocurrency wallets. These phishing campaigns continue to attack ordinary users in various forms, resulting in significant financial losses for many who inadvertently sign malicious transactions.
Phishing fraud statistics
 < /p>
< /p>
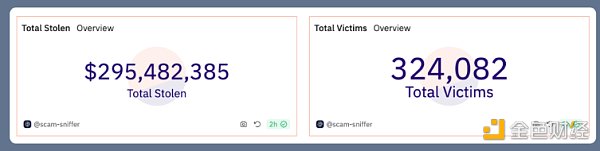
In the past 2023, Scam Sniffer monitored these wallet drainers stealing from approximately 324,000 victims assets of nearly US$295 million.
Phishing scam trends
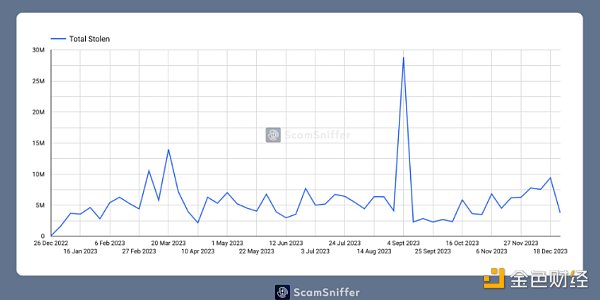
It is worth mentioning that nearly $7 million was stolen on March 11 alone. Much of this was due to USDC exchange rate fluctuations as victims encountered phishing websites impersonating Circle. A major theft occurred near March 24 when Arbitrum's Discord was hacked. Their airdrop date is also close to this date.
Each theft spike is associated with a group-related event. These could be airdrops or hacking events.
Famous Wallet Drainers
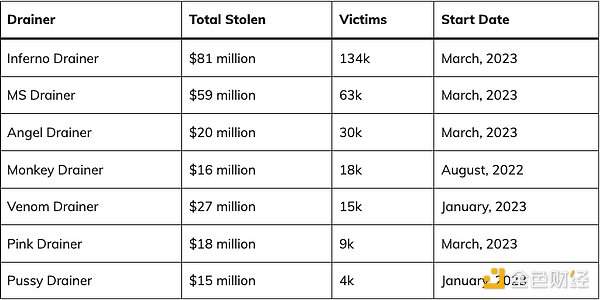
After ZachXBT exposed Monkey Drainer, they announced their withdrawal after being active for 6 months. Venom then took over most of their customers. Then MS, Inferno, Angel, and Pink all appeared around March. As Venom ceased service around April, most phishing gangs moved on to other services.
The scale and speed are staggering. For example, Monkey siphoned off $16 million in 6 months, while Inferno Drainer significantly exceeded this figure, siphoning off $81 million in just 9 months.
Based on a 20% Drainer fee, they made at least $47 million from selling Wallet Drainers services.
Wallet Drainers Trend
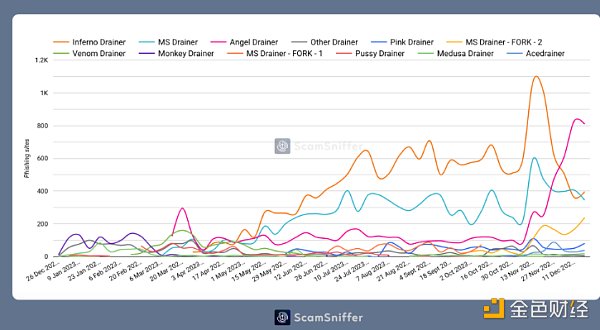
It can be seen from the trend analysis that phishing activities continue to grow. Moreover, Whenever a Drainer exits, a new Drainer will replace them. For example, Angel seems to be the new Drainer after Inferno announced his exit. replacement.
How do they launch phishing campaigns?

These Phishing websites mainly obtain traffic through the following methods:
Hacker attacks
Natural traffic
Paid traffic
Google Search Ads
Twitter Ads
Despite the widespread impact of hacks, the community typically responds quickly, usually within 10 to 50 minutes. However, airdrops, organic traffic, paid ads, and taken-over Discord links are less noticeable.
In addition, there are more targeted personal private message phishing behaviors.
Common phishing signatures
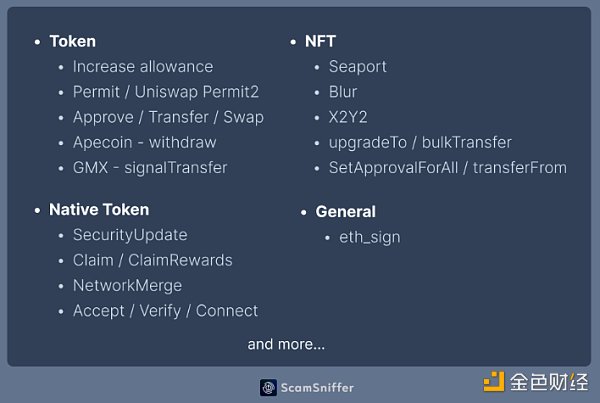
Different types of assets target different phishing signature methods. Pictured above are some common phishing signature methods. The type of assets held by the victim's wallet will determine the type of malicious phishing signature launched.
Looking at the case of using GMX’s signalTransfer to steal Reward LP tokens, it’s clear that they have a very sophisticated way of leveraging a specific asset.
Top 13 Phishing Victims
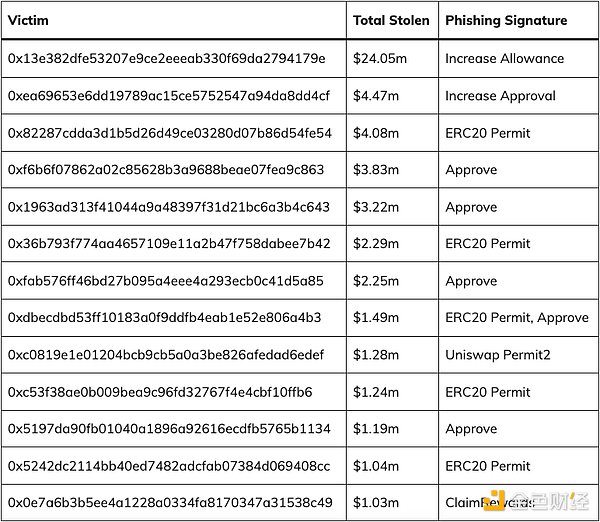
The above are the victims most affected by theft, with cumulative losses reaching US$50 million. It can be seen that the main reason for is to sign phishing signatures such as Permit, Permit2, Approve, and Increase Allowance.
Use smart contracts more
Multicall

Starting from Inferno, they also began to utilize smart contracts more. For example, splitting a fee requires two transactions. This may not be fast enough, leaving the victim at risk of revoking the authorization before the second transfer. To improve efficiency, they use multicall for more efficient asset transfers.
CREATE2 & CREATE
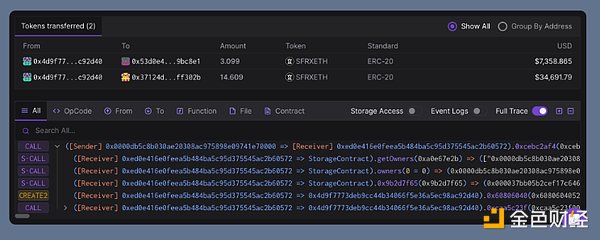
Similarly, in order to bypass some wallet security checks, they also try to use the create2 or create function to dynamically generate temporary addresses. This will render the wallet's blacklist useless, and will also bring more trouble to phishing research, because the asset transfer destination is unknown before you sign, and the temporary address is not meaningful for analysis.
This is a significant change from last year.
Phishing website
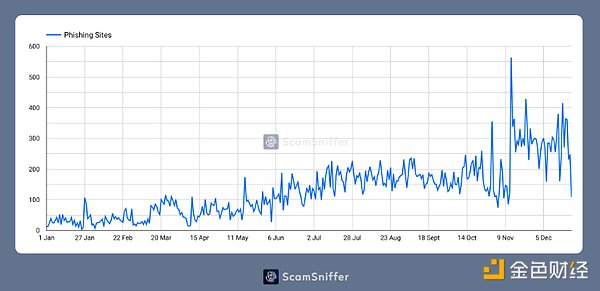 Pass Analyzing the trend in the number of phishing websites shows that phishing activities are gradually increasing every month. This is closely related to the profitability and stability of the Wallet Drainers service.
Pass Analyzing the trend in the number of phishing websites shows that phishing activities are gradually increasing every month. This is closely related to the profitability and stability of the Wallet Drainers service.
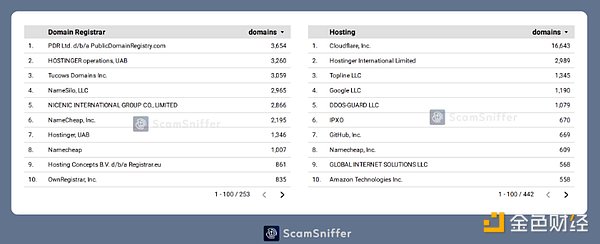
The above are these fishing The primary domain name registrar used by the website. By analyzing the server address, we can also find that most of them use services such as Cloudflare to hide their real server address.
What does Scam Sniffer do?
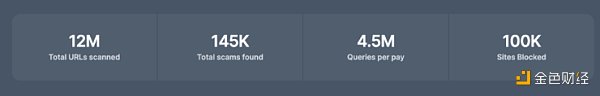
Last year, Scam Sniffer Nearly 12 million URLs were scanned and nearly 145,000 malicious URLs were found. Scam Sniffer’s open source blacklist currently contains nearly 100,000 malicious domain names, and we continue to push these malicious website domain names to platforms such as Chainabuse.
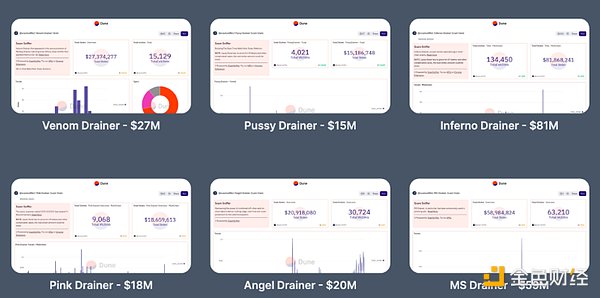
Scam Sniffer continues Report multiple well-known wallet drainers and continue to share information on major theft cases on social media platforms to increase public awareness and understanding of phishing threats.
Currently, Scam Sniffer has assisted some well-known platforms in protecting their users and is committed to providing web3 security for the next billion users.
 JinseFinance
JinseFinance

 < /p>
< /p>







 Pass Analyzing the trend in the number of phishing websites shows that phishing activities are gradually increasing every month. This is closely related to the profitability and stability of the Wallet Drainers service.
Pass Analyzing the trend in the number of phishing websites shows that phishing activities are gradually increasing every month. This is closely related to the profitability and stability of the Wallet Drainers service. 






