Author: Julia Wu
Source: medium
MPC is the new hot acronym being chased by giants like Coinbase and Fireblocks. A tool for building large-scale, privacy-preserving applications.
Simply put, MPC allows an organization to perform computations without revealing each participant's private input.
MPC also supports "semi-custodial" wallets as an alternative to fully non-custodial wallets with mnemonic phrases.
This post is intended to provide an initial look at MPC, but rabbit holes can go very deep. Links to additional resources are provided at the end of the article for interested readers.
Introduction to MPC
It has been a big topic in cryptography (pioneered by Andrew Yao) since the 80s and has recently been applied to digital assets. The protocol stayed mostly in the academic and theoretical realm until improvements in computing power and algorithms in the 2000s made it possible to put it into practice.
As the name suggests, the goal of MPC is to allow multiple parties to share the ability to compute certain data. Multiple participants can hold a piece of private data, such as part of a private key. Each segment can be used to sign a transaction without revealing the entire private key, or even individual parts.
There is a hypothetical use case known as Yao's millionaires' problem: imagine two friends, Alice and Bob, who want to compare who is richer without revealing their exact net worth (Try it with your friends at your own risk).
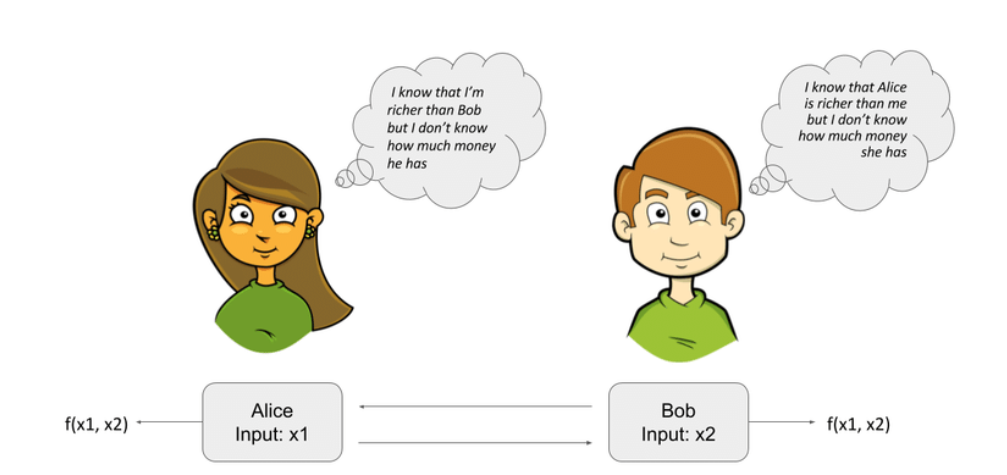
https://www.researchgate.net/figure/Millionaires-problem_fig1_320290997
In this case, the calculated function is:
F (x1, x2) = max (x1, x2)
Using MPC, the two millionaires can figure out who makes the most money without having to share everyone's exact income. Everyone brings their salary data, and this function works out who's spending the most.
The first large-scale commercial use case for MPC came in 2008, when the protocol was used in a sealed auction of sugar beets in Denmark. The highest bidder wins the auction but pays the price proposed by the second highest bidder. MPC is used to keep bid prices private while determining the ranking of bids.
Relevance to key management
When it comes to crypto wallets, one of the biggest problems today is how easily seed phrases can be lost or compromised. This becomes a single point of compromise.
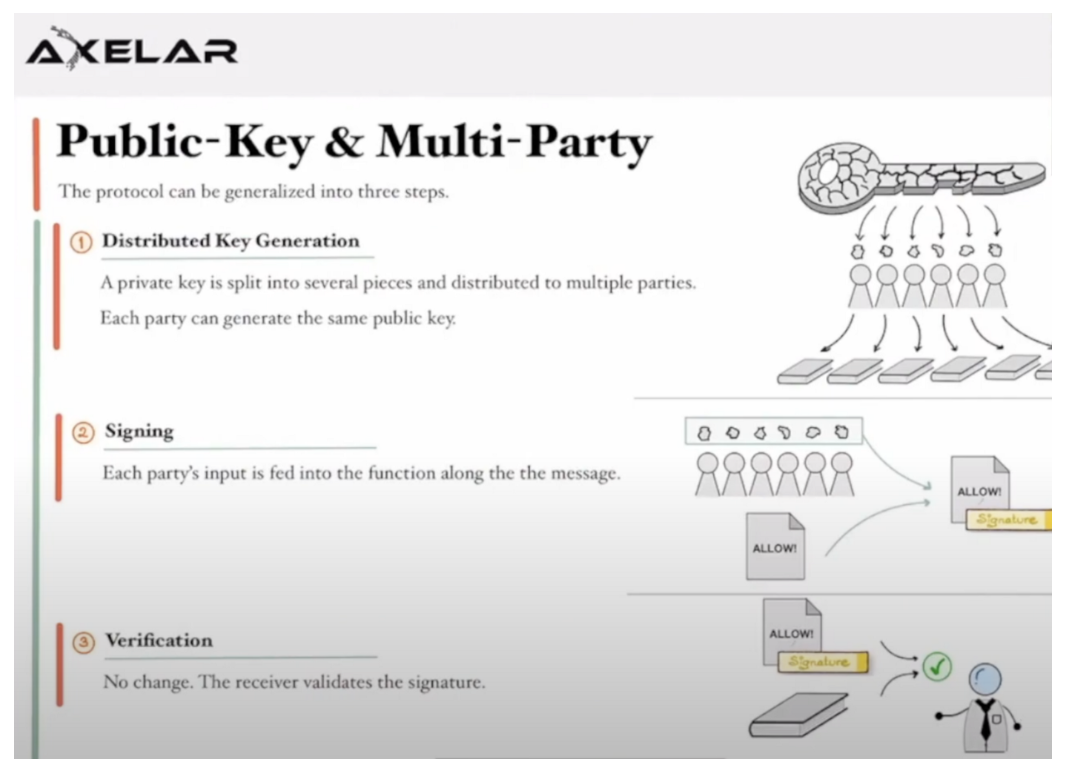
With MPC, the private key no longer needs to be stored in one place, because MPC breaks the key into pieces through distributed key generation. These fragments can be stored in different places by multiple parties.
A single secret (private key share) is randomly assigned by a set of endpoints, either computers or mobile devices. Endpoints can compute the public key (wallet address) from a single private share—using only their portion of the private key! The entire "bare" key is never formed or revealed in one place.
When a transaction needs to be signed, the MPC protocol will convene each independent private key share owner to sign the transaction in a distributed and private manner.
Each side's input is fed into a function. This information includes their private shares and private information. The output is a signed message. Digital signatures appear as if done with a single private key. It is then sent to the blockchain network to approve the transaction.
MPC can be configured to require all or a threshold of key shares to occur at the same time, or to perform computations at respective times.
If hackers want to gain access to the wallet, they must now find a way to gain access to all parts of the key. It's not enough just to get the key from one person. In the case of organizations and teams, multiple people now have access to one wallet without the ability for one person to run away with funds.
Related: Threshold Signatures (TSS)
TSS refers to generating signatures at a threshold requiring at least m of n parties, thereby removing trust in a single entity. The protocol can be combined with MPC to require a minimum number of signatures to approve a transaction.
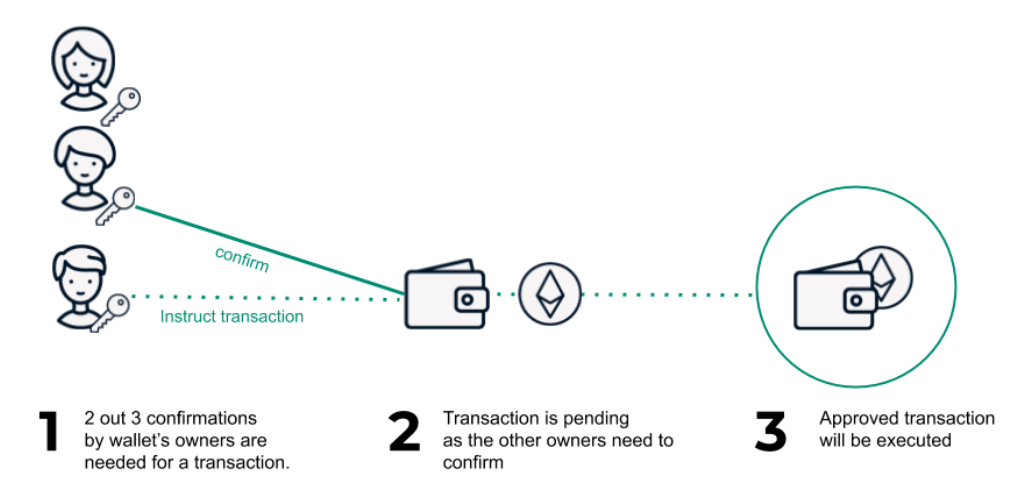
Multisig vs. MPC
The difference between multisig and MPC is that instead of dividing one key into multiple shares held by multiple parties (MPC), each party in multisig has its own private key. In order for a transaction to be successful, there needs to be a minimum threshold of signers to approve.
https://docs.gnosis-safe.io/introduction/the-programmable-account/eoas-vs.-contract-accounts
With MPC, the signing process is distributed across multiple computers, with each computer processing a piece of private data using a single key share. These shares work together to sign transactions in a distributed fashion.
A multi-signature wallet will use different private keys to create different signatures, while MPC is a single signature composed of multiple shares of one private key.
In order for multisig to work, the blockchain needs to support it. But not all chains support multi-signature wallets, which usually come in the form of smart contracts. MPC uses a standardized cryptographic signature algorithm ( ECDSA : Elliptic Curve Digital Signature Algorithm), which can be implemented by most blockchains.
With multisig, it’s not as easy to support dApps or most DeFi services, as a transaction requires multiple signatures to be approved — unlike the usual one-click process on MetaMask.
Coinbase’s Pete Kim explained it well:
“An MPC-powered wallet (we call it a dApp wallet) can support everything a normal self-hosted wallet can. Not just send, receive and trade, but also use dApps, DEX, store and trade NFT, Voting in governance, liquidity mining, web3 games, and more.”
Even though MPC only outputs a signature, it has a more complex approval structure. MPC wallets may lack the ability to determine which key share was used to sign a transaction, since all key shares participate in the same signature. MPC wallets also lack hardware security module (HSM, also known as hardware wallet) support.
Multi-signature example: Gnosis Safe
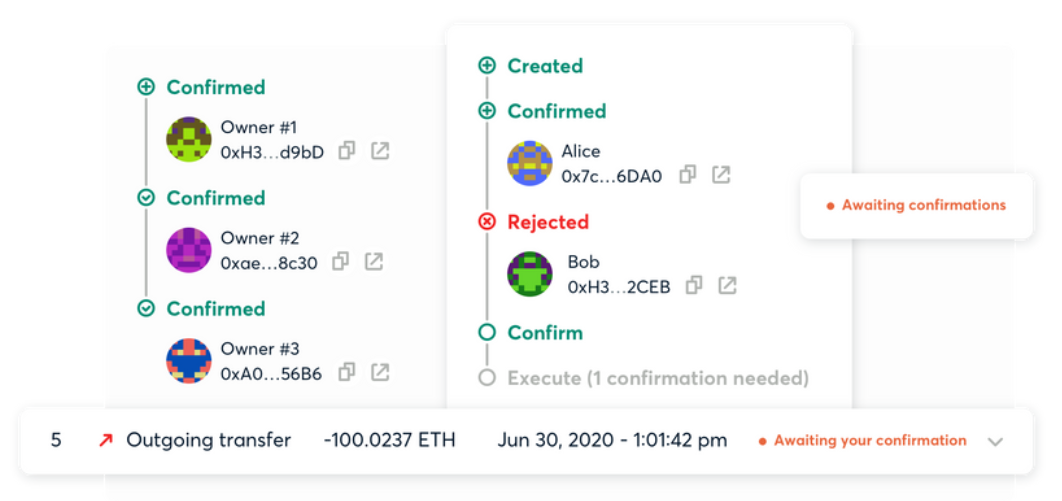
Gnosis Safe allows users to define a list of owner accounts and a minimum signature threshold required to confirm transactions. When the threshold is reached, Safe transactions can be executed.
Multisig requires a minimum number of people to approve a transaction before it can be processed. If a business has 3 stakeholders, you can configure Gnosis so that approval from all 3 is required for a transaction to succeed. This is also self-hosted.
First, you will need a signer wallet, such as MetaMask. Gnosis Safe itself does not hold private keys, so it cannot sign or execute transactions.
https://gnosis-safe.io/static/df5a5bc44d16189df7e6b1cc9556a685/bc8e0/multisig.png
Adoption of MPCs
Fireblocks
Fireblocks provides 1,300 large institutions with a digital asset custody platform, including MPC wallets, token issuance/management, and access to DeFi. Its clients include banks, exchanges, lenders, hedge funds, market makers and others.
One of Fireblocks' clients, Revolut (valued at $5.5 billion and one of the largest fintech companies), is using Fireblocks' MPC to introduce encryption services to 13 million retail customers around the world. This infrastructure is used to provide a secure payment rail for digital asset transfers. Through the MPC wallet, Revolut can increase its product line involving cryptocurrencies and retail-oriented functions.
ZenGo
ZenGo creates two key shares, one stored on your mobile device and the other on ZenGo servers. This means that ZenGo does not have access to your funds, but the user initiates a process in which the server and the device's key share will sign the transaction without revealing each other's private information to the other.
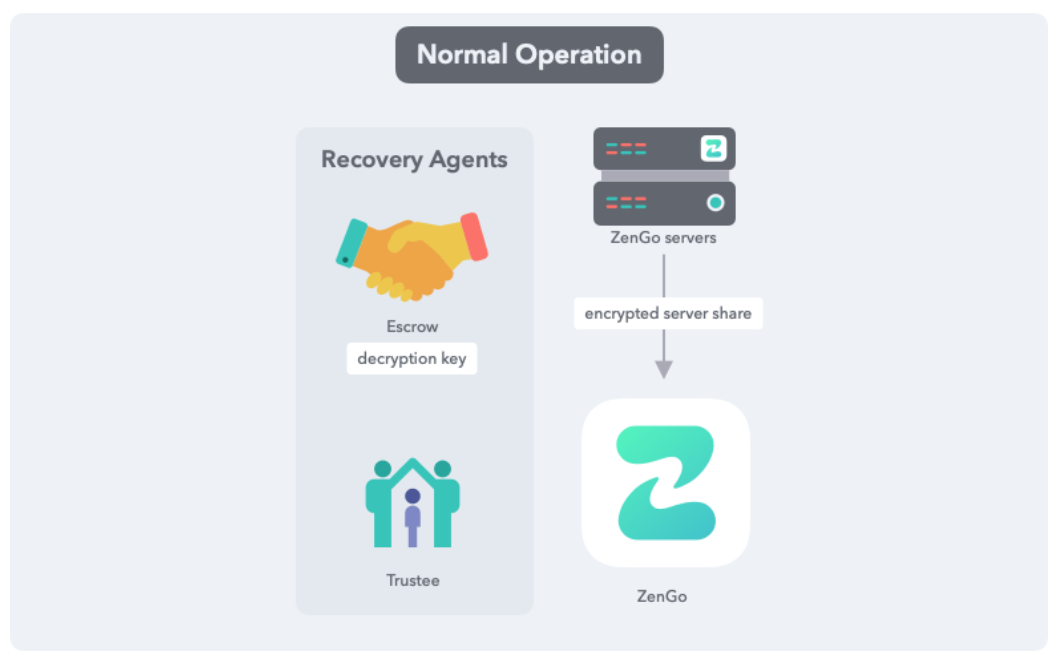
https://zengo.com/a-deep-dive-into-zengo-guaranteed-access-solution/
Coinbase
Coinbase is rolling out a way for users to explore dApps without having to manage seed phrases, and uses MPC to split keys between users and Coinbase.
epilogue
We're still in the early days of MPC, but it's becoming a compelling option for securing digital assets while preserving user experience while avoiding storing entire private keys online, offline, or in a physical device (single point of compromise).
We have yet to see MPC wallets being widely adopted and used for seamless on-chain interactions like MetaMask. However, it is very exciting to witness these efforts around solutions that improve security for users and organizations.
Sources and Further Reading
understand deeper
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance Cheng Yuan
Cheng Yuan Bitcoinist
Bitcoinist Beincrypto
Beincrypto Nulltx
Nulltx