Author: David C, Source: Bankless, Compiler: Shaw Golden Finance
As concerns about surveillance and data development grow, the crypto space has recently accelerated the pace of integrating privacy-enhancing technologies (PETs) into its core infrastructure.
Blockchains are designed to be completely transparent, and while the crypto industry has long valued privacy approaches (token mixers or privacy-based tokens), it has also been working to expand the scope of privacy (beyond simple DeFi and payments) without limiting privacy to specialized networks.
As blockchains are increasingly used for AI training and institutional financing, applications that employ alternative cryptographic technologies are becoming increasingly popular. Four technologies are particularly popular: multi-party computation (MPC), fully homomorphic encryption (FHE), trusted execution environments (TEE), and zero-knowledge transport security layers (zkTLS).
This article aims to show the role of each technology in enhancing privacy, use cases, and key projects based on each technology.
Multi-party computation (MPC)
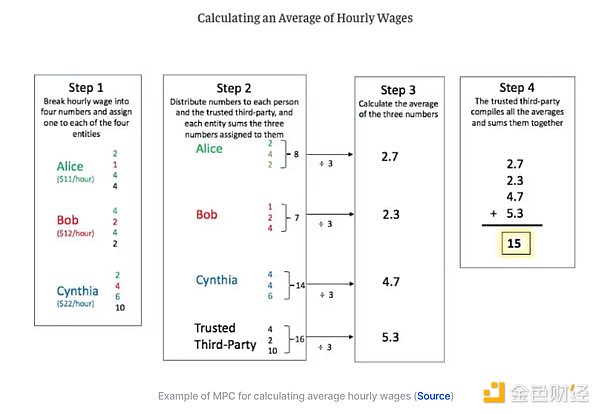
MPC is a type of distributed computing that allows multiple groups to jointly compute something without revealing their own information.
Suppose you and five friends want to calculate your average salary, but don't want to reveal the specific amount. Each person randomly divides his or her salary into six parts and gives one to each person. Everyone holds a share, but no one can recover the salary of others because they only have one of the six required salaries. Instead of calculating the raw salary, each person performs a calculation on the six salaries. The results are combined to calculate the final average salary without anyone having to know the specific salary.
MPC is particularly important when regulatory restrictions or competition concerns prevent direct data sharing, but collective analysis can benefit all parties. A typical example is when multiple hospitals want to use patient data to train AI - laws and regulations prohibit the sharing of sensitive medical data, but MPC enables collective training without actually sharing the data.
MPC Obstacles
As more and more people join multi-party computing networks, management becomes more difficult. The system needs to pass more messages between participants, and Internet capacity limits slow things down. Everyone needs to do more computation, consuming more computing power. While blockchains can discourage cheating by punishing bad actors in the network who might collude to cheat, they don’t solve these resource and computing power problems.
Who’s using MPC? And for what?
Fireblocks - Institutional custodians of private keys that use MPC to split between devices to ensure the full key can never be compromised.
Arcium - Chain-agnostic network using MPC for private AI processing and sensitive tasks.
Renegade - On-chain dark pool using MPC for confidential transactions.
Fully Homomorphic Encryption (FHE)
FHE allows for data processing without decryption, meaning sensitive data remains encrypted while stored, transmitted, and analyzed.
Currently, data is encrypted in transit but must be decrypted to be processed, creating a window of vulnerability. For example, when I send photos to the cloud, they are encrypted in transit but decrypted when they arrive. FHE eliminates this decryption step—the data remains encrypted throughout the computation, protecting the information while it’s actively being used.
Think of FHE as a locked safe with a programmable glove. You put private data and program instructions inside: “Add these numbers together,” “Sort this list.” You give the safe and the glove to someone else. They blindly manipulate the contents of the safe, following the instructions without being able to see what’s inside. When they’re done, they return the safe to you, and you open it to get the correct result.
Hinders of FHE
FHE comes with a severe performance penalty—computations can be slowed down by 10 to 100 times. Adding zero-knowledge proofs (zkFHE) slows things down further by several orders of magnitude. Developers want this combination because while FHE protects the inputs, it doesn’t guarantee the correctness of the operations. In other words, the question is whether the person you authorize to run a computation on FHE-protected data actually did it correctly. While this verifiability is missing, adding it would make an already slow system almost unusable for real-time applications.
Who is using FHE? For what?
Zama - FHE tool provider, using tools like fhEVM to implement cryptographic smart contracts on the EVM network.
Fhenix - Research company bringing FHE to practical applications.
PrivaSea - AI training network using Zama's FHE tools for encrypted machine learning.
Octra — A general-purpose chain with high-speed cryptographic computation using proprietary FHE, machine learning consensus, and rentable services.
Trusted Execution Environment (TEE)
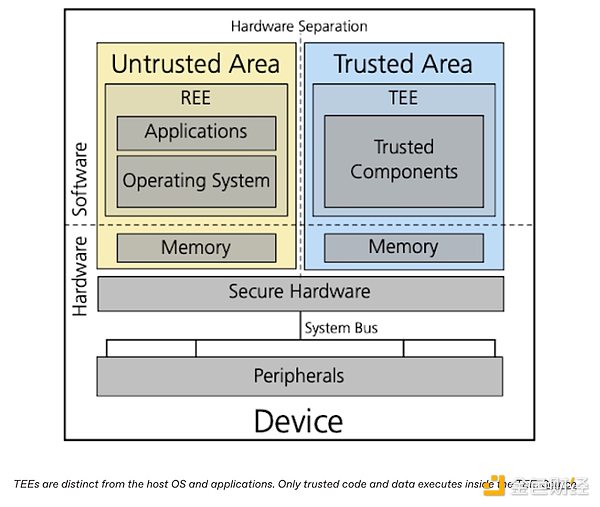
TEEs are secure hardware areas that store and process data in isolation, preventing the rest of the machine (including the operating system and operators) from accessing that data.
If you have an iPhone, you interact with TEEs every day, as Apple uses them to store biometric data. Here’s how they work: A TEE stores a face or fingerprint scan in a secure area of the chip. When an app requests authentication, the new scan is sent to the TEE for comparison. This comparison happens inside sealed hardware — no biometric data can be seen by the app or operating system. The TEE simply returns a “yes” or a “no.”
TEEs have begun to emerge in the cryptocurrency space for confidential smart contracts and computations. Uniswap's Layer-2 Unichain uses TEEs to build blocks fairly and prevent MEV attacks.
TEE Obstacles
TEEs rely on hardware vendors for integrity, not distributed networks, which makes them centralized by cryptographic standards. Someone could compromise a TEE in production or exploit its vulnerabilities. This happened to Secret Network, where researchers discovered an Intel chip vulnerability that decrypted all network transactions.
Who is using TEEs? For what?
Space Computer - A blockchain that uses TEEs on satellite nodes, making the hardware tamper-proof by running in orbit.
Oasis Protocol - Layer 1 uses TEEs to implement confidential smart contracts with EVM-compatible runtimes.
Phala Network - A decentralized cloud platform for confidential computing using TEEs from multiple hardware providers.
Zero-Knowledge Transport Security Layer (zkTLS)
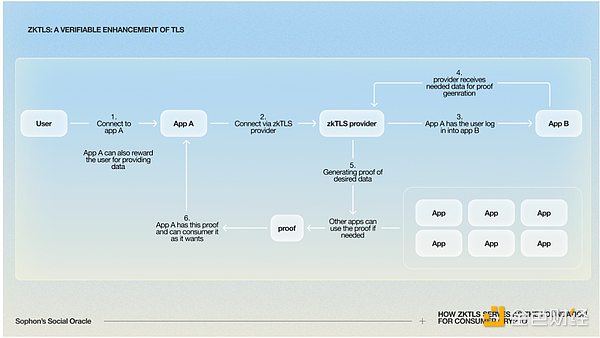
zkTLS merges TLS (already used for internet security in HTTPS) with zero-knowledge proofs (ZKP) to ensure that information is private and verifiable.
By adding zero-knowledge proofs (ZKP), zkTLS allows users to transmit any HTTPS data (95% of web traffic) while controlling the information that is leaked. This allows any Web2 platform data to run as a public API, unrestricted by platform permissions, thus connecting the entire web and bridging Web2 and Web3.
For example, let's say you want to take out an on-chain loan using your bank balance. You can access your bank account through a zkTLS tool, and since the bank uses HTTPS, the tool can analyze any data displayed. The tool generates a zero-knowledge proof (ZKP) of your balance that proves the funds but doesn’t reveal the specific amount or transaction history. You submit this proof to DeFi lending platforms, which verify your creditworthiness without accessing private financial data.
ZkTLS obstacles
zkTLS only works for data that a website has already displayed - it cannot force a website to display hidden information. It relies on the continued use of the TLS protocol and requires the participation of a real-time oracle, introducing latency and trust assumptions.
Who is using zkTLS? For what?
ZKP2P: An on/off ramp protocol using zkTLS for privately moving funds on-chain and off-chain.
EarniFi — A lending platform using zkTLS that provides privacy-preserving loans to employees with earned but unpaid wages.
DaisyPay — An application for influencer collaboration and instant payments using zkTLS.
Overall, each PET serves different goals and has its own trade-offs. An application may combine multiple PETs depending on its data needs. Decentralized AI platforms may use MPC for initial coordination, FHE for computation, and TEE for key management.
There are many different implementations of zkTLS that leverage various PETs in their architecture. Combined, these tools can greatly expand the design space of cryptocurrencies and realize their potential as the next iteration of the Web. As we all know, cryptocurrencies still need to improve user experience, which is critical to increasing the usability and widespread adoption of these privacy services.
 Catherine
Catherine







