Author: Climber, Golden Finance
On June 19, Kraken Chief Security Officer Nick Percoco said that an employee of a security company used a platform loophole to withdraw more than 3 million US dollars in digital assets, which is a case of extortion in criminal liability.
The incident was directed at the blockchain security agency CertiK. In response, the agency said that this behavior was a white hat hacker action aimed at helping the crypto trading platform Kraken discover system loopholes and prevent greater losses. The necessary transaction crypto assets generated by the test have also been returned in full, but they are different from the total amount required by Kraken.
For the debate between the two parties, some people tend to believe that CertiK may have embezzled, but some people think that it is illogical to say that CertiK stole. Black hat and white hat are just a thought away. The focus of the problem may be on the amount of the bounty.
Each side has its own story
The incident started when a security researcher reported a security vulnerability to Kraken on June 9, which allowed real assets to be withdrawn by forging deposits. Afterwards, Kraken discovered and fixed the vulnerability and also noticed that related account addresses had already used the vulnerability to withdraw a large amount of assets.
So on June 19, Kraken Chief Security Officer Nick Percoco said that two accounts associated with the security researcher had used the vulnerability to withdraw digital assets worth more than $3 million. We asked to speak to the other party's company, but the other party did not agree to return any funds.
In view of this, Kraken believes that this behavior is no longer a white hat hacker, but extortion.
In response to Kraken's remarks and community opinion, CertiK has repeatedly stated that it is innocent and has published an article to explain the ins and outs of the incident.
CertiK said that it had previously discovered a series of serious vulnerabilities in Kraken, which may result in hundreds of millions of dollars in losses. The Kraken deposit system cannot effectively distinguish between different internal transfer states, and there is a risk that malicious actors can forge deposit transactions and withdraw forged funds.
During the test, millions of dollars of fake funds can be deposited into Kraken accounts, and more than $1 million of forged cryptocurrencies can be withdrawn and converted into valid assets, and the Kraken system did not trigger any alarms. After CertiK notified Kraken, Kraken classified the vulnerability as "Critical" and initially fixed the problem.
However, CertiK pointed out that the Kraken security team subsequently threatened CertiK employees, demanding repayment of the unmatched cryptocurrencies within an unreasonable period of time, and did not provide a repayment address. In order to protect user safety, CertiK decided to make the matter public, calling on Kraken to stop any threats to white hat hackers and emphasizing the need to address risks through cooperation.
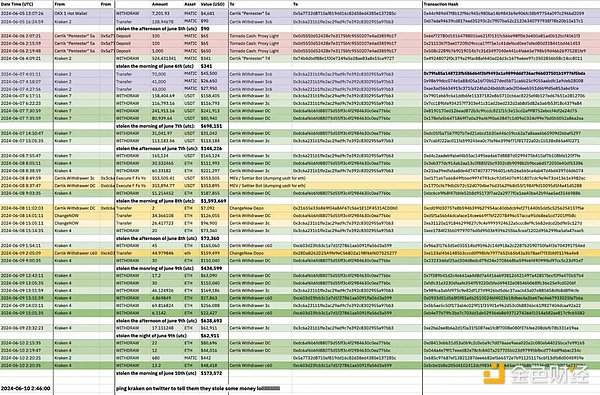
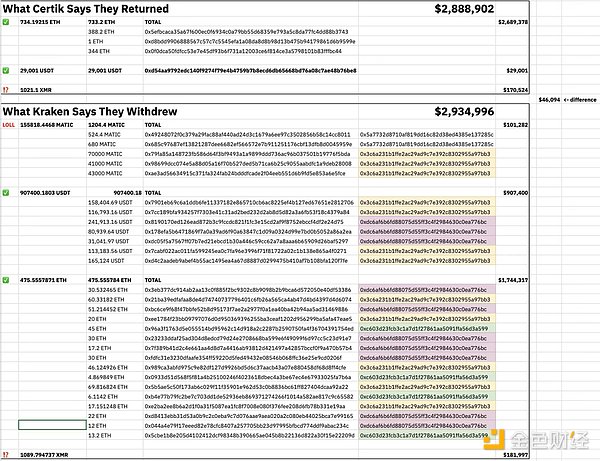
In addition, CertiK also stated that it confirmed that it had returned all the funds it held, but the total amount was inconsistent with Kraken's requirements. The refunded amount includes 734.19215 ETH, 29,001 USDT and 1021.1 XMR, while Kraken requested a refund of 155818.4468 MATIC, 907400.1803 USDT, 475.5557871 ETH and 1089.794737 XMR.
In the latest public response letter, CertiK answered 10 core questions of the incident, especially mentioning that they did not participate in the Kraken bounty program and had made all test deposit addresses public from the beginning.
Community opinions are divided
Certik listed a complete line of events for this incident, but several community members, including security researcher @tayvano, questioned it.

According to Certik, they started testing and informing Kraken on June 5. However, when @tayvano studied the on-chain transfer addresses, he not only found that these addresses had large withdrawals through other trading platforms, but also that the test of Kraken had been carried out long before.
CyversAlerts, an encrypted data security platform, provided @tayvano with three withdrawal addresses related to the incident:
0x3c6a231b1ffe2ac29ad9c7e392c8302955a97bb3 0xdc6af6b6fd88075d55ff3c4f2984630c0ea776bc 0xc603d23fcb3c1a7d1f27861aa5091ffa56d3a599
@tayvano said she often saw this pattern and used it as a way to distinguish between victim addresses and hacker addresses when investigating chaotic key leaks.
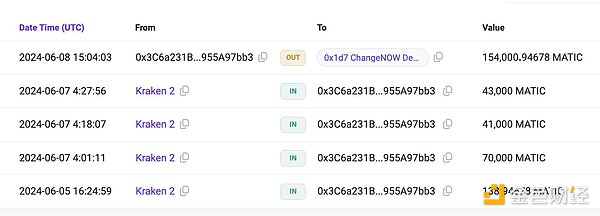
@tayvano also found that 0x3c6a231b1ffe2ac29ad9c7e392c8302955a97bb3 transferred 154,000 MATIC to ChangeNOW.
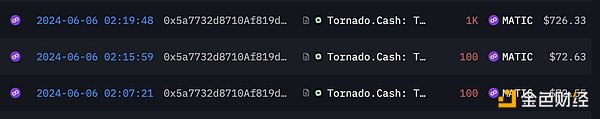
Coinbase insider @jconorgrogan said that the address of the relevant personnel transferred 1,200 MATIC to Tornadocash, intending to exchange funds through the mixer.
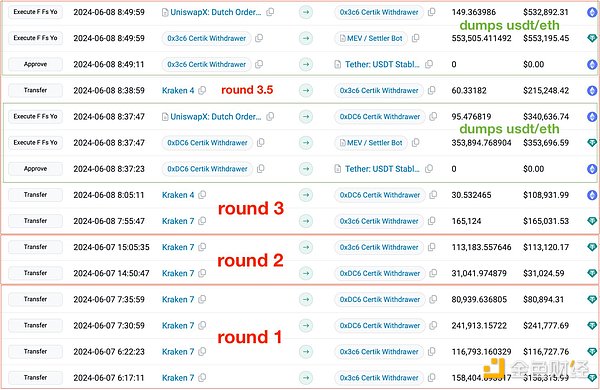
In addition, @tayvano also found that Certik had been doing this before June 5 by comparing the test time of the deposit address of Certik security personnel. He said that if we go back to the timeline released by certik, the so-called "Round 1" and "Round 2" withdrawals are not actually Round 1 and Round 2, but more like Round 7.
In response, Meir Dolev, CTO of security company Cyvers, also questioned the time when CertiK discovered the Kraken vulnerability, and said that CertiK suspected that it had done the same test on OKX and Coinbase.
Meir Dolev cited the content shared by @tayvano, namely: the 0x1d…7ac9 address created the contract 0x45…CeA9 on the Base network on May 24 and conducted related activities, and the Certik test address also used the same signature hash of the unknown address.
It is suspected that this contract (0x45…CeA9) deployed on Base has also done the same test on OKX and Coinbase to determine whether these two exchanges have the same vulnerability as Kraken.
Another community member @0xBoboShanti also said that an address previously posted by a Certik security researcher on Twitter was being probed and tested as early as May 27. This already contradicts Certik's timeline of events. One of the Certik tornado txs funded a wallet that has recently been interacting with the same contract.
Taylor Monahan, CEO and founder of Ethereum wallet manager MyCrypto, also analyzed the possible causes of the incident, saying that CertiK should be afraid of Kraken's lawyers, damage to its reputation, and how the storm may affect CertiK's internal culture.
She also pointed out that since several crypto projects audited by CertiK have been attacked in the past, speculation about the possibility of previous insider operations has begun to circulate online.
However, some well-known industry KOLs have expressed different opinions, believing that CertiK may not be a real hacker, and they have made possible speculations about the incident. Crypto researcher @BoxMrChen said that he can understand CertiK, who may not be a hacker, but may want more bounties. He would rather know how much white hat bounty Kraken is willing to pay CertiK to see whether CertiK is greedy and cunning, or Kraken is stingy.
CryptoInsight researcher Haotian said that Certik did discover and report the vulnerability to Kraken, indicating that the intention was not a "hacker" behavior. The account marked as Certik staff KYC only added $4, indicating that the vulnerability test was within a reasonable limit at the beginning, so the two sides probably did not reach an agreement on the vulnerability bounty and the division of labor for fixing the vulnerability.
Conclusion
For the "dark forest" of the crypto market, hacker attacks are endless and not surprising, but hacking under the banner of "white hat" is undoubtedly easy to attract criticism. Although CertiK has tried its best to clarify its "righteous" behavior of helping the project party, CertiK does need to give a reasonable explanation for the doubts raised by the above community members.
However, as CertiK said, Kraken's deep defense system failed to detect so many test transactions, which may indeed lead to greater risk losses. Both parties should work together to face risks and safeguard the future of Web3.
 Hui Xin
Hui Xin
 Hui Xin
Hui Xin YouQuan
YouQuan Joy
Joy Hui Xin
Hui Xin YouQuan
YouQuan Brian
Brian Joy
Joy YouQuan
YouQuan Brian
Brian Joy
Joy