Source: Chainalysis; Compiled by Deng Tong, Jinse Finance
This article is Part 2 of the 2024 Crypto Crime Mid-Year Report published by Chainalysis. To view the first part, click Chainalysis Report: Why Stolen Funds and Ransomware Keep Rising.
Summary
CSAM Networks
Reports of Chinese CSAM sites have increased since the end of 2023.
Most wallet holders are purchasing access for a month or more, including up to about 20,000 days (equivalent to more than 54 years) of near-permanent access.
Consistent with our past findings, CSAM vendors continue to leverage instant exchangers when cashing out.
Scams
Scammers are adapting their on-chain and off-chain strategies to conduct shorter but more dynamic and profitable scam campaigns.
Pig-killing scams are the largest type of revenue-generating scams so far this year. A Myanmar scam group first discovered on-chain in 2022 has netted at least $101.22 million so far this year.
Most scammers continue to shift from broad Ponzi schemes to more targeted activities such as pig-killing trays, work-from-home scams, drainer theft scams (Golden Finance Note: Drainer is a type of malware specifically designed to illegally empty or "drain" cryptocurrency wallets. This software is offered for rent by its developers, meaning that anyone can pay to use the malicious tool.) Or address poisoning.
Huione Guarantee
We have observed an increase in the use of Chinese marketplaces and money laundering networks. Huione Guarantee is one such marketplace, which is associated with Cambodian conglomerate Huione Group, which connects buyers and sellers who often do little to conceal the illicit nature of their transactions.
Since 2021, Huione Guarantee has processed more than $49 billion in cryptocurrency transactions, far more than previously reported.
Huione’s on-chain connections include scams and other scams, addresses reported as stolen funds, OFAC-approved Russian exchange Garantex, scam shops, CSAM, Chinese gambling sites and casinos, and more.
In the first part of our mid-year crime update, we discussed trends related to ransomware and stolen funds. While total illicit on-chain activity is down nearly 20% year-to-date (YTD), inflows of stolen funds have nearly doubled, with annual ransomware payments on track to be the highest ever for a single year.
In the second half of our update, we’ll examine on-chain activity related to the distribution and consumption of child sexual abuse material (CSAM), including an on-chain analysis of payments received by two CSAM vendors and what those amounts indicate.
Next, we’ll examine the latest trends in cryptocurrency scams. On-chain and off-chain activity suggest that scammers are adapting their tactics and running shorter but more profitable and regenerative campaigns. We’ll discuss one notable scam group – the highest earner so far in 2024 – which highlights the trend in recent years away from elaborate Ponzi schemes to more targeted campaigns such as pig-killing scams.
Pig-killing scams are so called because the criminals “fatten” their victims to extract as much profit as possible. This typically involves establishing a romantic relationship with the victim via text messaging or dating apps until they pressure the victim into sending money to a fake investment opportunity. Chillingly, the scammers on the other end of these conversations are often people who have been kidnapped, trafficked to Southeast Asia and forced to work in labor camps within large compounds to run the pig-killing scams.
Finally, we look at Huione Guarantee, a $49 billion market that was recently exposed as facilitating cybercrime, including CSAM and scams. Let’s get started.
China’s CSAM Shows Signs of Growth
Reports of Chinese CSAM vendors have increased since the end of last year. The chart below shows the proportion of RMB-denominated vendors in all CSAM activity compared to activity in other currencies. These sites provide RMB conversion rates for cryptocurrency payments. Since the end of 2023, Chinese vendors have captured a larger share of global CSAM inflows, peaking in the first quarter of this year so far at 38.8% of total inflows.
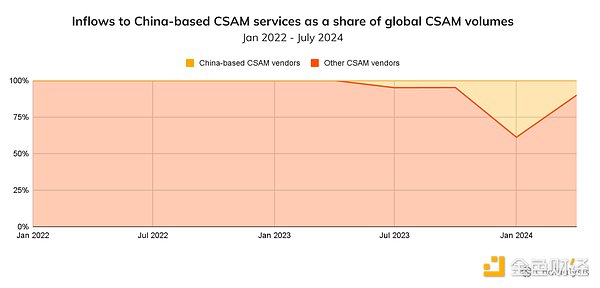
According to the Internet Watch Foundation (IWF), an organization dedicated to preventing online child sexual abuse, it is difficult to determine why these networks have grown in China. "We have seen an increase in reports of such sites," said an IWF spokesperson. "Based on the reporting channels alone, it is difficult to definitively say whether there is an emerging trend or whether these sites have been around for some time but have not been reported to the authorities." While the sites themselves may have been around for some time without the public noticing, the on-chain infrastructure for these services is all relatively new, with the oldest Chinese wallet dating back to July 18, 2023, and most of the other addresses from late 2023. At least in terms of the on-chain dimension, the timeframe of these wallets suggests that these services are emerging, represent a real trend, and are likely not simply the product of new reporting channels.
On-chain examination of Chinese CSAM suppliers
Beyond the numbers, we cannot quantify the harm caused by child sexual abuse on a global scale. Given its redistribution potential, small purchases of tens of dollars (as shown in the Chainalysis Investigations chart below) can still lead to long-term exploitation of children.
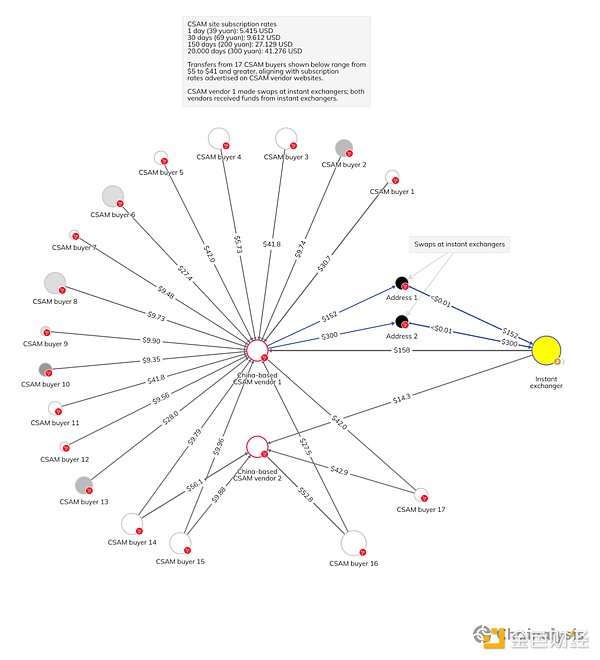
The network shown in the above chart includes two suspected CSAM suppliers that sell materials in Chinese yuan. Transfers from individual wallets to vendors, compared to subscription rates on CSAM vendors’ websites, indicate what kind of access CSAM buyers are purchasing. As mentioned earlier, buyers can get one day’s access to CSAM material from these vendors for just $5. They can also purchase nearly perpetual access (about 20,000 days, or more than 54 years) for just $41. In this example, most wallet holders purchased access for a month or more. As for CSAM vendors, they utilized instant exchangers when cashing out, consistent with our reporting earlier this year.
Scammers Employ On-Chain and Off-Chain Strategies; Large-Scale Scams Persist
With billions of dollars flowing in, cryptocurrency-related scams have been on the rise in 2024, making them one of the largest areas of illegal activity so far this year. The most notable feature of this year’s scam landscape is the rapid evolution of the scammers’ on-chain footprint — the crypto wallets and addresses used to receive payments from scam victims — and the off-chain tools, such as domain names and social media accounts, they use to manipulate victims. This activity reveals how scammers are adapting both on-chain and off-chain to conduct shorter-duration, more destructive scams. To avoid detection and disruption, many of these operations regenerate or maintain numerous smaller, concurrent campaigns to keep larger organized scam rings operating.
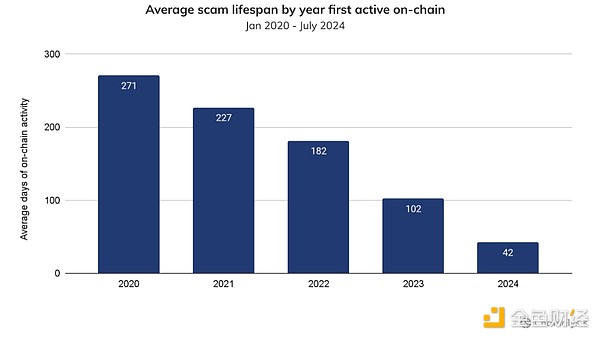
A notable feature of the 2024 scam landscape is how much of the total scam inflows so far this year have gone to wallets that were active this year, indicating a surge in new scams. The chart below shows the share of total scam revenues accounted for by wallets that first appeared in the year the scam received cryptocurrency. Notably, 43% of year-to-date scam inflows went to wallets that were active this year. This trend is significant because the next highest year, 2022, saw only 29.9% of total year-to-date inflows go to wallets that were active that year. This trend is well captured by the significantly shorter average lifespan of scam campaigns, as shown in the chart below. We plotted this trend by counting the number of days between when a scam campaign was first and last observed on-chain. The average number of active days for scam campaigns has decreased significantly from 2020 to 2024 so far, with 271 days for scams that started in 2020 and 42 days so far for scams that started in 2024. This macro trend is consistent with scammers continuing to shift away from elaborate Ponzi schemes and toward more targeted campaigns such as pig-killing or poisoning addresses, partly due to increased enforcement and blacklisting of scam addresses by stablecoin issuers.
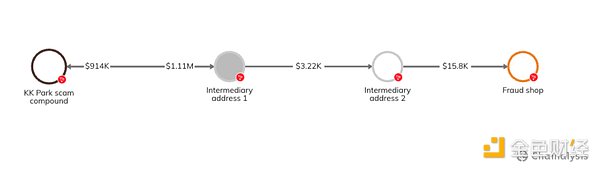
Although scammers tend to use new on-chain addresses, about 57% of scam fund inflows so far in 2024 still flow to wallets active before 2024. One of the largest single wallets active this year consolidates funds from many scams of Myanmar's most notorious pig-killing plate KK Park. This wallet was first discovered on-chain in 2022, and scams using this address continue to generate significant revenue, netting more than $100 million so far this year. These funds may come from scam victims or from ransoms submitted by families trying to rescue trafficked family members.
In addition, it is worth noting that scam activity from KK Park and similar venues has been very active in adapting their off-chain scam presence, often purchasing mature Facebook, Tinder, and Match.com profiles from Chinese services for use in their activities. The chart below shows the flow of value from KK Park scam wallets to scam shops selling illegal products, which scammers use to devastating effect.
A screenshot of the scam shop's website also shows the pricing of the social media accounts it sells.
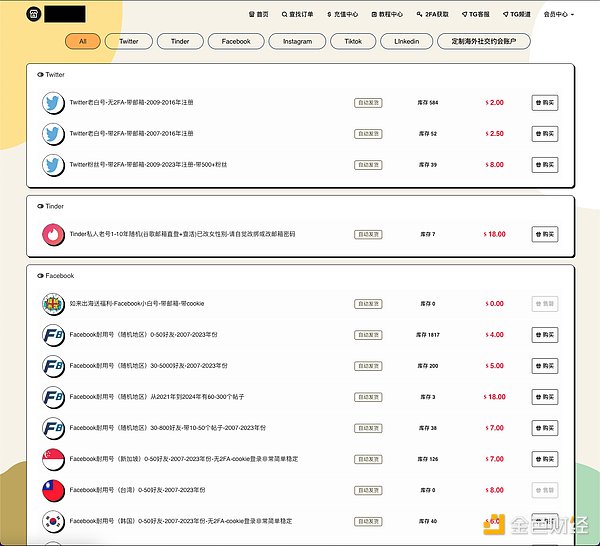
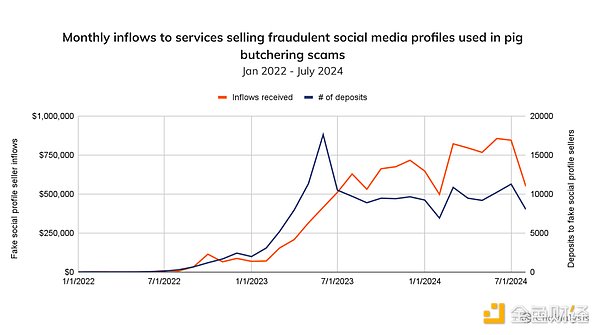
By looking at the total inflows to services like this scam shop that sell social media accounts, we see more evidence to support this trend. The chart below shows that cryptocurrency sent to these services has steadily increased over the past two years, with 178,000 deposits totaling approximately $10.5 million from 2022 to 2024. Social media profiles on these sites are priced between $5 and $20 per account, meaning scammers may have purchased between 525,000 and 2.1 million social media profiles that they can use to target victims.
In addition to sending funds to services that provide scam tools, scammers ultimately need to send their ill-gotten gains to services to be laundered and converted into fiat currency, primarily through centralized exchanges. This year, we have also seen an increase in the use of Chinese marketplaces and money laundering networks, including Huione Guarantee.
Huione Guarantee: A $49 Billion Online Marketplace
Huione Guarantee, an online marketplace associated with Cambodian conglomerate Huione Group, was recently exposed as a significant player in cybercrime. We have covered the service much more than we have previously reported – we found that the platform has processed over $49 billion in cryptocurrency transactions since 2021.
Historically, Huione Group provided legitimate services, operating as a remittance system for overseas transfers and offering insurance services. At one point the company was involved in the luxury travel business. However, its platform, Huione Guarantee, appears to be heavily used for illegal crypto activities, including scams, investment fraud, and money laundering. Huione Guarantee has grown into a large and diverse ecosystem that supports the lucrative scam business that continues to operate in Southeast Asia.
Huione Guarantee is a peer-to-peer (P2P) marketplace that connects buyers and sellers, often facilitating these transactions through Telegram, which provides a point of contact. In total, there are thousands of Telegram groups advertising or posting information on Huione Guarantee, each operated by a different independent merchant or affiliate, many of whom may have ties to criminal enterprises operating in the region.
Huione Guarantee claims to be a neutral party in these transactions; it reportedly operates like a trading platform, charging fees for each trade performed but not verifying the legitimacy of the goods and services listed.

Note: This image has been machine translated from its original Chinese version.
Many merchants on Huione Guarantee do little to disguise their activities, instead using cryptic code words to advertise the types of services they seek. For example, some ads showed users looking for "convoys," meaning they were looking for money mules to move funds through multiple points and layers to obscure the source and destination of the funds.
Other posts promoted the following:
Offering facial recognition or facial transformation technology in the "Development" section of the platform.
Organizing pig-killing schemes and Ponzi schemes.
Offering global passports, visas, and allegedly assisting with applications.
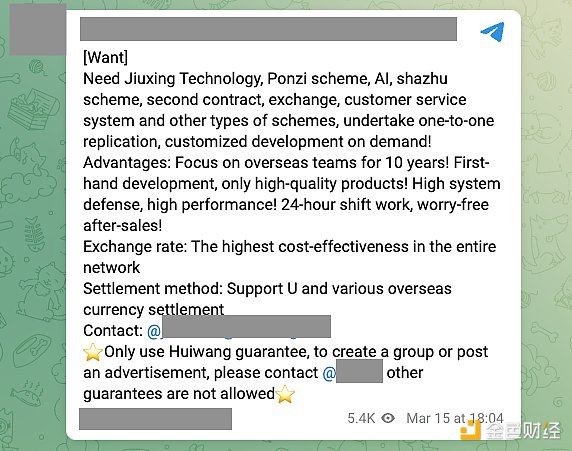
Note: This image is machine translated, the original text is "Shazhu" means "killing pigs".
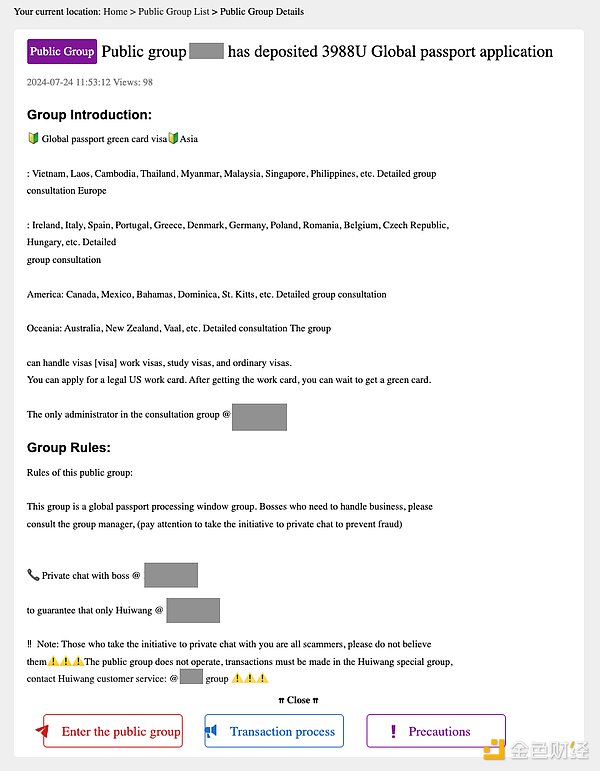
Note: This image is machine translated from the original Chinese version.
Huione Guarantee's On-Chain Activity
On-chain analysis shows that Huione Pay is active on Ethereum, with a total inflow of more than $1.9 billion and an inflow of more than $47 billion on TRON. In the image below, we see examples of this activity, with transfers between Huione Pay and a variety of illicit and high-risk counterparties, highlighting Huione’s extensive facilitation network. The P2P network that Huione appears to support off-chain is also mapped on-chain; Huione has received and sent funds to various types of counterparties, including scams, addresses reported as stolen funds, OFAC-approved Russian exchange Garantex, scam shops, CSAM, Chinese gambling sites and casinos, etc.
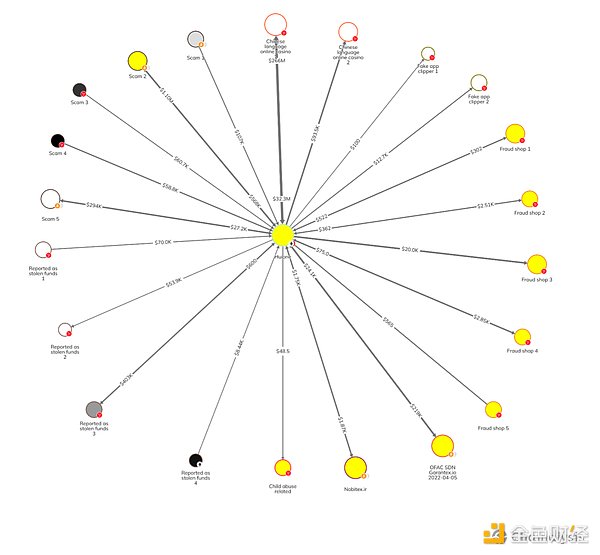
Huione Guarantee has also processed transactions to wallets allegedly associated with large criminal groups such as KK Park. Additionally, Chainalysis found wallets associated with Fully Light Group and Warner International, two entities run by Burmese Kokang families that have reportedly been linked to illicit activities such as gambling venues, secretive financial networks, and money laundering schemes.
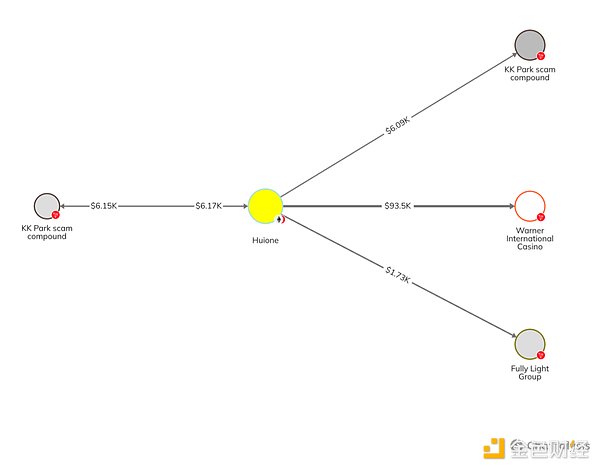
The use of Huione Guarantee by these networks suggests that the service facilitates the activities not only of the scammers and fraudsters themselves, but also of the networks of criminals behind them.
Huione Guarantee stands out because it serves as a point of contact for different types of cybercriminals, including pig-killing scammers and CSAM networks. While it may be the largest, it is not the only service of its kind. Other networks have similarly leveraged Telegram to facilitate P2P transactions, often in exchange for illicit goods and services. Chainalysis is working closely with our partners to closely monitor this ecosystem to uncover this activity.
 JinseFinance
JinseFinance
















