Author: INSIGHTFUL; Compiler: TechFlow
Disclaimer
This guide cannot guarantee anything and is not written from the perspective of a "crypto or cybersecurity expert", but is based on continuous learning from multiple sources and personal experience.
For example, I myself was deceived by fear of missing out (FOMO) and greed (fake live broadcast scams and fake MEV robot scams) when I first entered this field, so I took the time to study, set up and understand security seriously.
Don't be the person who is forced to learn security because he lost everything or a lot of assets.
Hacker attack or user error?
All types of wallet, token, or NFT "hacks" or compromises can be roughly divided into two categories:
Token Approvals
Token approvals are essentially permissions that allow a smart contract to access and move a specific type or amount of tokens in your wallet.
For example:
As background information, basically everything on the Ethereum network, except ETH, is an ERC-20 token.
One of the features of ERC-20 tokens is the ability to grant approval permissions to other smart contracts.
These approvals will be required at some point if you want to do core DeFi interactions (like swapping or bridging tokens).
NFTs are ERC-721 and ERC-1155 tokens respectively; their approval mechanisms are similar to ERC-20, but for NFT markets.
The initial token approval prompt of MetaMask (MM) provides several pieces of information, the most relevant of which are:
The tokens you are granting approval
The website you are interacting with
The smart contract you are interacting with
The ability to edit the number of token permissions
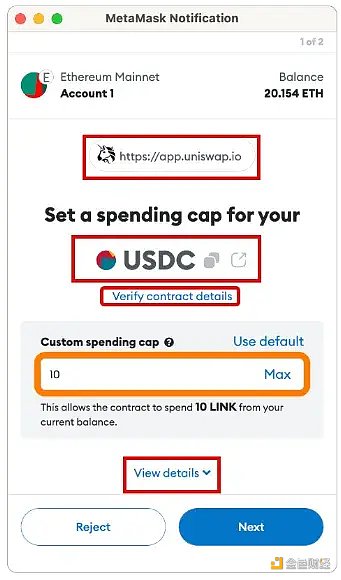
In the Full Details drop-down menu, we see an additional information: Approval Function.
All ERC-20 tokens must have certain features and properties outlined by the ERC-20 standard.
One of these is the ability for smart contracts to move tokens based on approved quantities.
The danger of these approvals is that if you grant token permissions to a malicious smart contract, your assets could be stolen or drained.
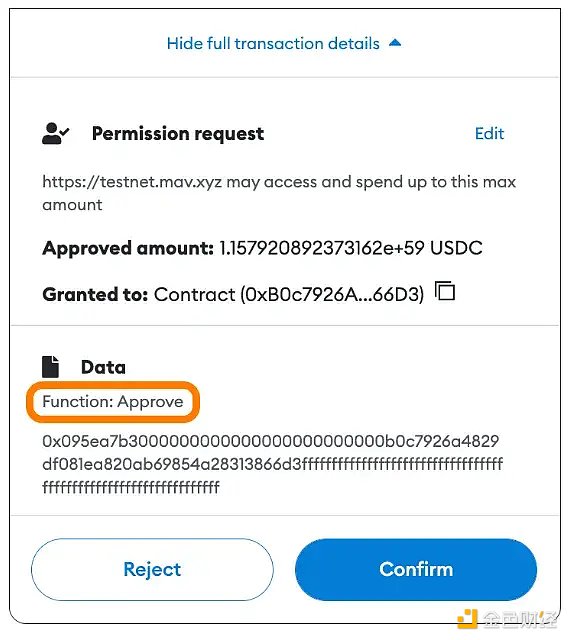
Unrestricted vs. Custom Restricted Approvals (ERC-20 Tokens)
Many DeFi applications will prompt you for unlimited approvals for ERC-20 tokens by default.
This is done to improve the user experience because it is more convenient and does not require possible additional approvals in the future, saving time and gas fees.
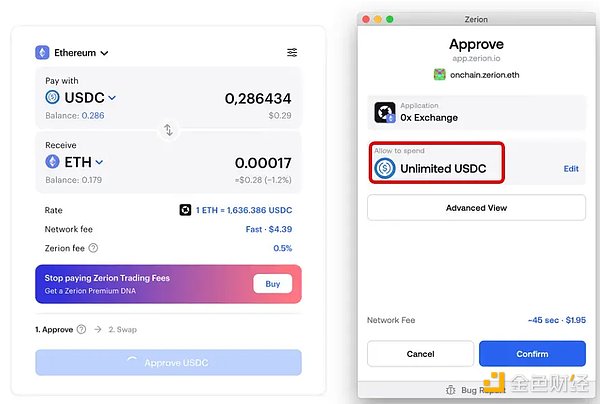
Why is this important?
Allowing approval for an unlimited number of tokens may put your funds at risk.
Manually setting token approvals to a specific amount can limit the maximum number of tokens that the dApp can move before signing a new, larger approval.
This reduces your risk when a smart contract is exploited. If you grant unrestricted approval to a dApp and that dApp has a vulnerability, you could lose all approved tokens from the wallet that holds those assets and granted the approval.
For example, Multichain WETH (WETH is an ERC-20 token wrapper for ETH) has experienced such a vulnerability.
This commonly used bridge was attacked by abusing the previously unrestricted token permissions, resulting in user funds being stolen.
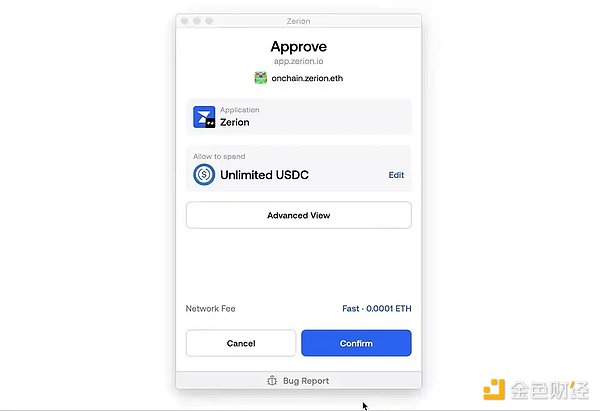
Here is an example (using the Zerion wallet) showing how to change the default unrestricted approval to manual approval.
NFT Approvals
「setApprovalForAll」for NFTs
This is a commonly used but potentially dangerous approval that is typically granted to trusted NFT marketplaces when you want to sell your NFT.
This enables the marketplace's smart contract to transfer your NFT. So when you sell your NFT to a buyer, the marketplace's smart contract can automatically move the NFT to the buyer.
This approval grants access to all NFT tokens in a specific collection or contract address.
This can also be used by malicious sites or contracts to steal your NFTs.
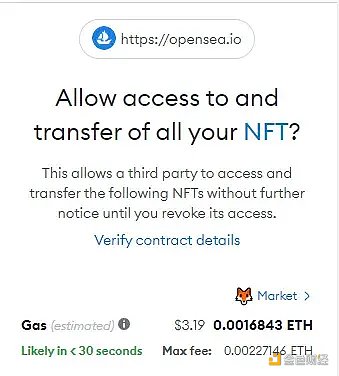
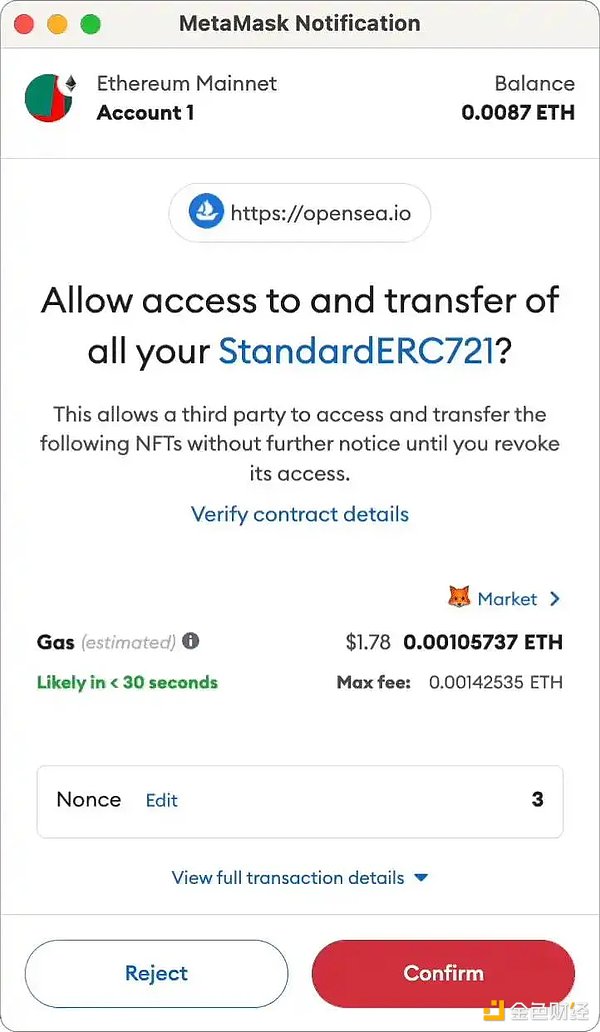
An example of malicious actors abusing "setApprovalForAll"
The classic "wallet account shrinkage" in the case of FOMO free casting looks like this:
Users visit a malicious website that they believe is legitimate.
When they connect their wallet to the website, the website can only view the contents of the wallet.
However, the malicious website scans the wallet for the highest value NFT and prompts the user to "Set All Approvals" from MetaMask (MM) for the contract address for that NFT.
The user thinks they are minting NFTs, but is actually granting the malicious contract permission to move those tokens.
The scammer then steals the tokens and liquidates them into bids on OpenSea or Blur before the items are marked as stolen.
Signatures vs. Approvals
Approvals cost gas fees because they are involved in transaction processing.
Signatures are gas-free and are often used to log into dApps to prove your control over that wallet.
Signatures are generally low-risk operations, but could still potentially be used to exploit previously granted approvals on trusted sites like OpenSea.
For ERC-20 tokens, you can also modify your approvals with gas-free signatures, as the permission feature was recently introduced on Ethereum.
You can see this in action if you use a decentralized exchange (DEX) like 1inch.
Token Approval Tips
Be cautious when giving any approval, make sure you know which tokens you are approving and for which smart contract (use etherscan).
Limit your approval risk:
Use multiple wallets (approvals are wallet specific) - don't sign approvals for your vault or high value wallets.
Ideally, reduce or completely avoid granting unrestricted approvals for ERC-20 tokens.
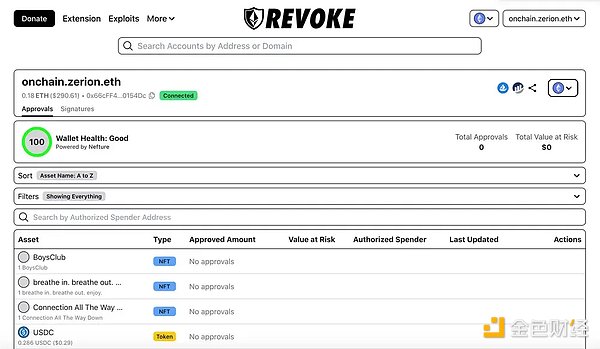
Regularly check and revoke approvals via etherscan or revoke.cash.
Hardware / Cold Wallet
Hot wallets are connected to the internet through your computer or mobile phone, and keys and wallet credentials are stored online or locally in your browser.
Cold wallets are hardware devices where keys are generated and stored completely offline and physically close to you.
Considering that a Ledger costs about $120, if you have more than $1000 in crypto assets, you should probably buy and set up a Ledger. You can connect a Ledger wallet to your MetaMask (MM) to enjoy the same features as other hot wallets while maintaining a certain level of security.
Ledger and Trezor are the most popular choices. I like Ledger because it has the best compatibility with browser wallets (similar to Rabby and MM).

Best Practices When Buying Ledger
Always buy from the official manufacturer website, never buy on Ebay or Amazon - it may be tampered with or pre-installed with malware.
Make sure the packaging is sealed when you receive the item.
When you first set up your Ledger, it will generate a mnemonic phrase.
Only write your recovery phrase on physical paper, or in the future write it on a steel plate to ensure that your recovery phrase is fireproof and waterproof.
Never photograph or type your recovery phrase on any keyboard (including mobile phones) - this will digitize the recovery phrase and your cold wallet will become an insecure hot wallet.
Crypto assets are not stored on hardware wallets, but "in" the wallet generated by the recovery phrase.
The recovery phrase (12-24 words) is the be-all and end-all and must be protected and secure at all costs.
It provides full control and access to all wallets generated under that recovery phrase.
The recovery phrase is not device-specific and you can "import" it into another hardware wallet as a backup (if needed).
If the mnemonic phrase is lost or damaged, and the original hardware wallet is also lost, damaged or locked, you will permanently lose access to all your assets.
There are various ways to store the mnemonic phrase, such as splitting it into multiple parts, increasing the physical distance between the parts, storing it in an inconspicuous place (e.g., a soup can at the bottom of the refrigerator, somewhere under your property, etc.).
At a minimum you should have 2-3 copies, one of which should be made of steel to be resistant to water and fire.
A "private key" is similar to a mnemonic phrase, but only for one specific wallet. It is often used to import a hot wallet into a new MetaMask (MM) account or for use in automated tools such as trading bots.
25th Word - Ledger
In addition to the original 24 word recovery phrase, Ledger offers an optional additional security feature.
Passphrase is an advanced feature that adds a 25th word of your choice of up to 100 characters to your recovery phrase.
Using a passphrase generates a completely different set of addresses that cannot be accessed with the 24 word recovery phrase alone.
In addition to an added layer of security, a passphrase provides plausible deniability in the event that you are compromised.
If using a passphrase, be sure to store it securely or remember it exactly, character by character and case sensitive.
This is the only and final defense against a physical threat scenario such as the "$5 Wrench Attack".
Why go through all the trouble of setting up a hardware wallet?
Hot wallets store private keys in a location that is connected to the internet.
It is extremely easy to be tricked, misled, and manipulated into revealing these credentials over the internet.
Owning a cold wallet means that a scammer would need to physically find and obtain your Ledger or mnemonic phrase to access these wallets and the assets within them.
Once the mnemonic phrase is compromised, all hot wallets and the assets within them are at risk, even those that have not interacted with a malicious website or contract.
Common ways people have been “hacked” in the past
Common ways people have been “hacked” (mnemonic phrase leaks) through hot wallets in the past include:
Being tricked into downloading malware, such as through job opportunity PDFs, beta games, running macros through Google Sheets, or imitating legitimate websites and services.
Interacting with malicious contracts: FOMO minting on imitation websites, or interacting with unknown airdropped or received NFT contracts.
Inserting or sending keys and mnemonics to “customer support” or related programs/forms.
 Bitcoinist
Bitcoinist















