Source: CertiK Chinese Community
On January 16, 2024, Socket Tech was attacked, causing a loss of approximately US$3.3 million. The attacker took advantage of a vulnerability in the data verification link of a Socket contract and stole user funds of the authorized contract through malicious data input. This attack caused losses to a total of 230 addresses, and the largest single address loss was approximately US$656,000.
Background introduction
Socket is an interoperability protocol that serves cross-chain security and efficient data and asset transmission. The Socket Gateway contract is the access point for all interactions with the Socket liquidity layer, where all asset bridges and DEXs converge into a single meta-bridge and select the best transactions based on user preferences such as cost, latency or security routing.
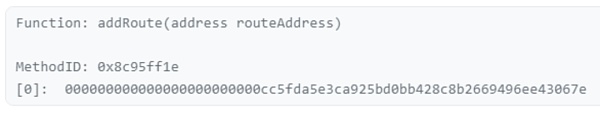
Three days before the hacker attack, the Socket contract administrator executed the addRoute command to add a new route to the system. The purpose of adding routing is to extend the functionality of the Socket gateway, but it inadvertently introduces a critical vulnerability.
The following picture shows the record of adding routing through the contract administrator:
Outline of the incident
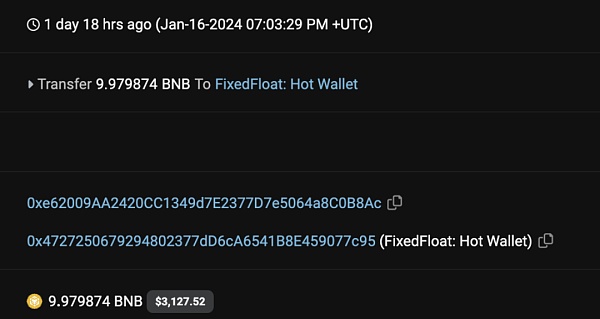
1. At 15:03 on January 16, Beijing time, the attacker’s wallet transferred the funds used for the attack. Our time analysis shows that The funds came from 0xe620 and were related to the withdrawal of 10 BNB from Tornado Cash.
2.These funds were used to create and execute two contracts to exploit Socket vulnerabilities. The first contract is for the USDC in the address authorized by SocketGateway (screenshot below). 127 victims were defrauded of approximately $2.5 million.
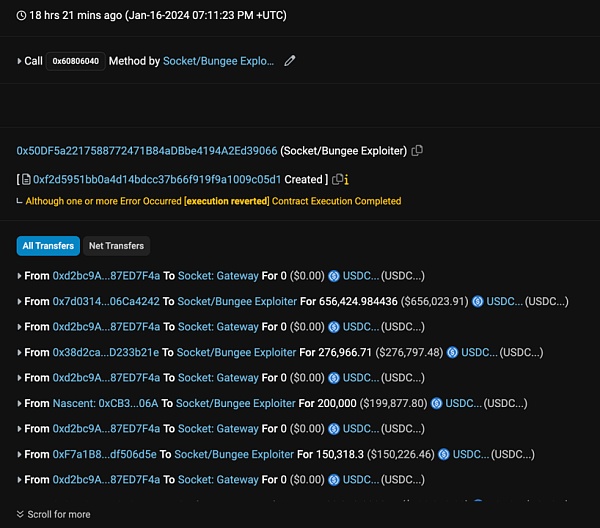
3. Next, the second contract will The target is WETH, USDT, WBTC, DAI and MATIC in the victim's address. As a result, another 104 victims lost approximately the following assets:
-42.48 WETH
-347,005.65 USDT
-2.89 WBTC
-13,821.01 DAI
-165,356.99 MATIC
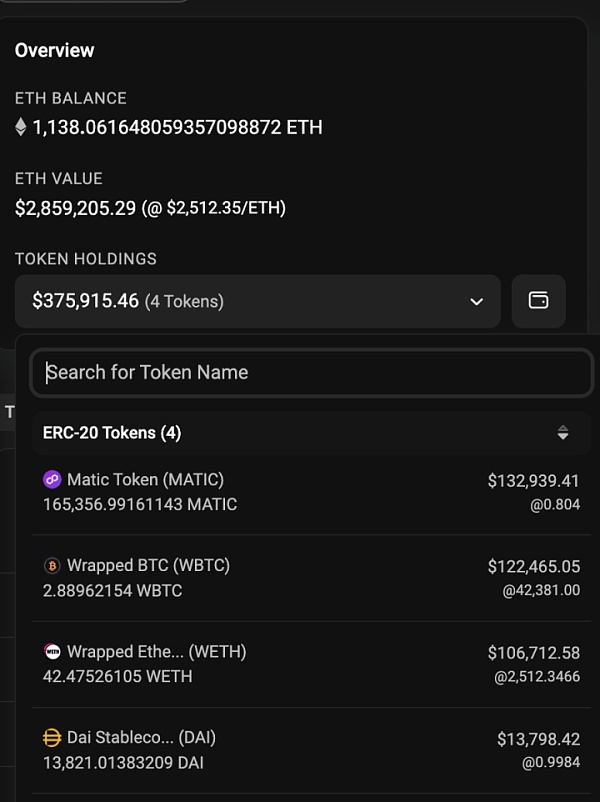
4. The attacker converted USDC and USDT into ETH.
Vulnerability source
The vulnerability exploited by attackers exists in the performAction function in the newly added routing address routeAddress.
The original function of the performAction function in this address is to assist in Wrapping and Unwrapping functions.
However, a critical vulnerability appears in this function: the user directly calls external data through swapExtraData in .call() without verification. This Meaning an attacker can execute arbitrary malicious functions.
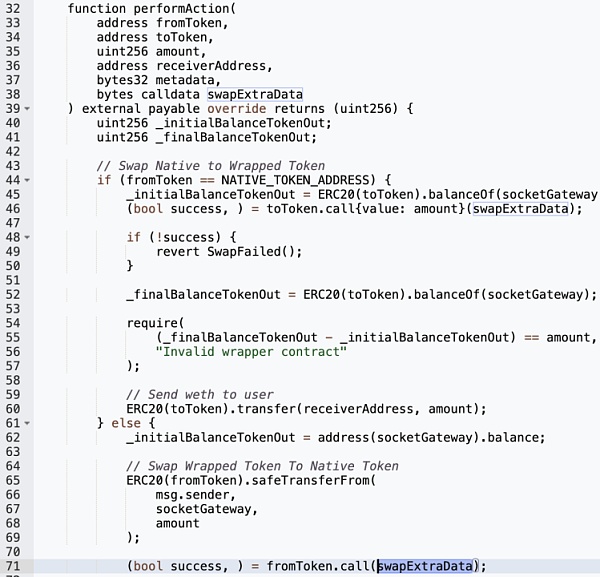
In this incident, the attacker created a Malicious swapExtraData input triggers the transferFrom function. The malicious call exploited the user's authorization to the SocketGateway contract and stole funds from them.
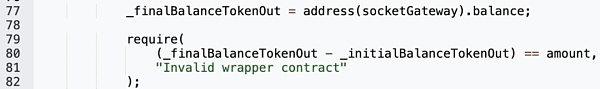
Although the contract will ensure that the user's balance will change correctly after fromToken.call() is called by checking the balance, this function does not consider the situation where the attacker sets the amount to 0.
Restore attack process< /h2>
1. Using the attack contract, the attacker called 0x00000196() on the Socket Gateway contract.
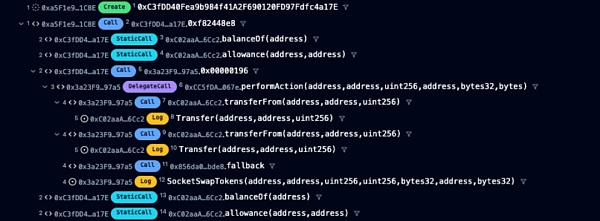
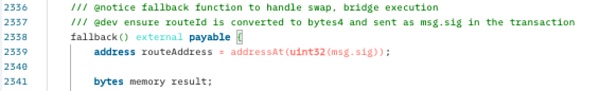
2.fallback() uses hexadecimal signature 196 The vulnerable routing address contract (routerAddress) was called.
3. In the screenshot below, we can see To the fake input used by the attacker, the Swapping number is all 0.
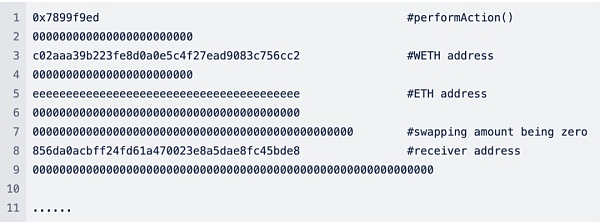
4. Next, WrappedTokenSwapperImpl.performAction() will be called Perform Swap.
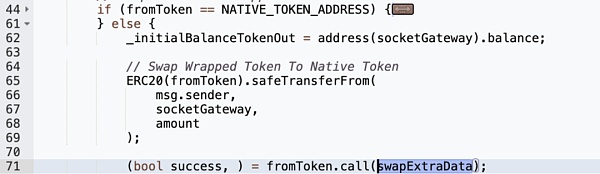
5. Without any verification, False SwapExtraData is accepted and executed by fromToken (WETH).
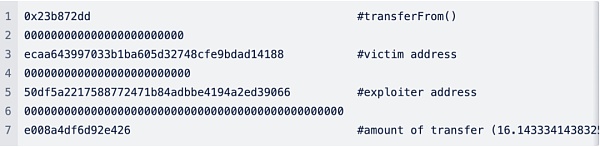
6. The attacker repeats the above process until victimized assets are exhausted. After the malicious transaction appeared, Socket quickly called disableRoute, blocking the previously vulnerable route and preventing a wider range of attacks.
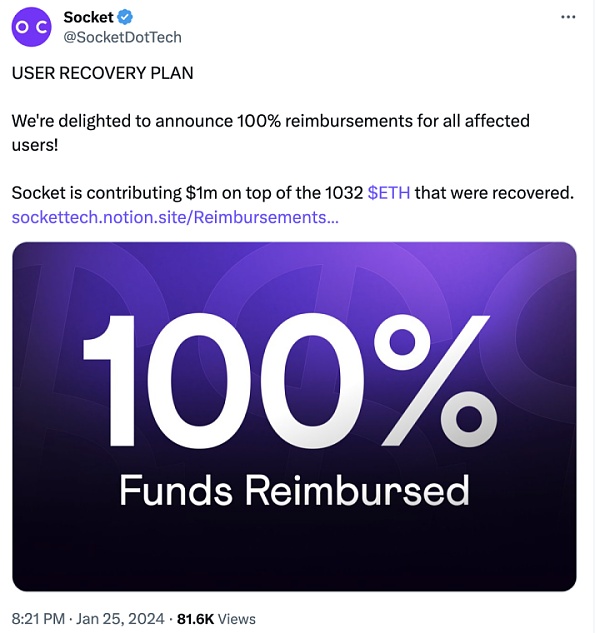
7. On January 23, Socket announced that it had recovered 1,032 ETH, and announced on the 25th that it would fully compensate all losses. This incident has been resolved.
Event Summary
In routing contracts with unlimited user authorization, malicious calldata attacks are not uncommon.
Previous similar attacks include Dexible and Hector Bridge.
On February 17, 2023, the decentralized exchange Dexible was attacked, causing losses of more than $1.5 million. The exploiter inputs malicious calldata into Dexible's fill() function to steal user assets.
On June 2, 2023, the Hector network protocol was attacked. The attacker deployed a fake USDC contract and transferred 652,000 real USDC from the victim's contract through malicious calldata.
Blockchain aggregation platforms usually improve liquidity and reduce losses by encapsulating a series of bridge and routing contracts. However, this complex encapsulation creates more security challenges.
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance Miyuki
Miyuki JinseFinance
JinseFinance JinseFinance
JinseFinance Edmund
Edmund JinseFinance
JinseFinance Joy
Joy Coinlive
Coinlive  Cointelegraph
Cointelegraph Cointelegraph
Cointelegraph