On January 22, Concentric.fi was attacked, causing losses of more than $1.85 million. Concentric announced on its official social account that the attack was a targeted "social engineering attack."
The so-called social engineering attack means that the attacker deceives the victim's trust through normal communication with the victim, affects the victim's psychology and then leaks secrets or makes Certain behaviors to achieve the attacker's goals.
In the attack on Concentric, the wallet of a contract administrator of its team was leaked. After the attacker took control of the wallet, he maliciously upgraded Concentric's treasury contract, causing losses to the liquidity pool and Concentric users.
Event Overview

On January 22, 2024, Concentric issued a warning on its X account that they may have encountered security incident.
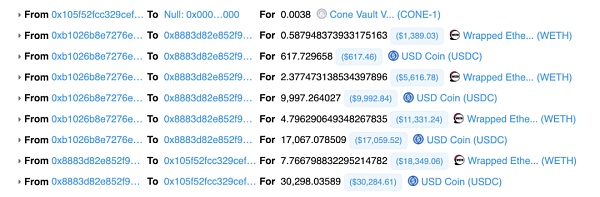
CertiK security team immediately launched an investigation. In the process of studying the activity of its contract address, we discovered a suspicious wallet address that repeatedly minted and burned CONE-1 LP in order to withdraw funds from Concentric’s liquidity pool .
The screenshot below contains some suspicious transactions:

The Concentric team later announced that the incident was caused by the leakage of the private key of one of their administrator wallets of. The wallet transferred its ownership to an address starting with 0x3F06, which upgraded Concentric’s liquidity pool code into a malicious contract that could be controlled by an attacker.
With the upgraded malicious contract, the attacker is able to mint a large number of LP tokens and withdraw the corresponding ERC-20 tokens. The ERC-20 tokens were eventually exchanged for ETH and transferred to the following 3 wallets. These wallets are related to previous attacks:
① 0xFD681A9aA555391Ef772C53144db8404AEC76030
② 0x1F14E38666cDd8e8975f9acC09e24E9a28f bC42d (Marked as "OKX Exploiter 2" on Etherscan)
③ 0x17865c33e40814d691663bC292b2F77000f94c34
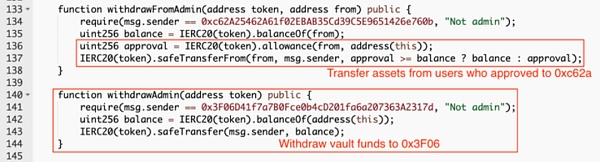
In addition , contract 0xc62A25462A61f02EBAB35Cd39C5E9651426e760b can also steal funds authorized by users on Concentric. The stolen funds were converted into ETH and transferred to an address starting with 0x5c0e. At the time of writing, more than $150,000 had been stolen in this way. The total losses caused by the two methods were more than 1.85 million US dollars.
Recidivist criminals
In the relevant malicious crimes we identified From the wallet address, it can be confirmed that this attack is related to multiple previous attacks.
Prior to this attack, the original funds for the attacker's address came from the wallet address associated with the UnoRe attack earlier in 2023. After completing the attack, the Concentric attackers transferred the stolen funds to the wallet address related to the previous OKX attack.
On December 13, 2023, an abandoned OKX DEX market maker contract was controlled by hackers, and assets were stolen by upgrading the authorization,causing about $2.7 million loss. The attacker in this incident is believed to be related to Lunafi, Uno Re, RVLT and other attacks.
The following figure is a capital flow analysis that can link several events:
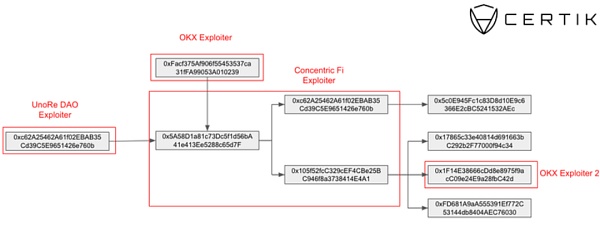
Attack process
① First, the Concentric Deployer address (starting with 0xeaf6) was compromised. The attacker used the access rights to transfer the contract ownership to the address starting with 0x3F06.

② After controlling the contract ownership, 0x3F06 maliciously upgraded the Cone pool contract.
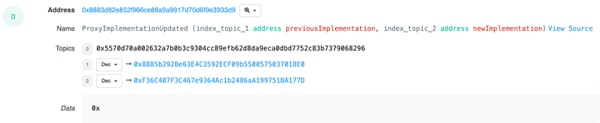
In the new contract, the attacker can destroy CONE-1 at 0x60d8 and re-mint it to 0x105f.
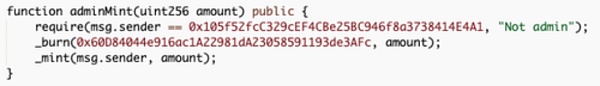
③ After completing the contract upgrade, the attacker can call adminMint() to extract CONE-1 from each liquidity pool, and then call burn() to replace CONE-1 with the corresponding underlying asset.
④ Next, the attacker created a second contract that allowed users to transfer authorized assets to the liquidity pool and transfer specified assets away from the liquidity pool. Both 0xc62a and 0x3F06 are controlled by attackers.
⑤ The address starting with 0x105f exchanged the stolen assets for 715 ETH and transferred them to three wallets. The wallet address to which 300 ETH was sent was confirmed to be related to the previous OKX attack.
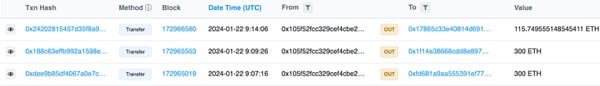
In addition, the address starting with 0xc62a also sent 65.4 ETH to 0x5c0E945Fc1c83D8d10E9c6366E2cBC5241532AEc, making the total loss slightly more than 780 ETH, about 1.85 million US dollars.
Write at the end
In the past we were often on guard. Attackers use phishing and social engineering tactics to control personal assets, but the same tactics can also control ownership of projects.
In January 2024, losses caused by phishing and private key leaks havereached US$170 million, accounting for 15% of the total losses in January. Nearly90%. Among them, the most serious incident was the theft of Chris Larsen’s personal account, causing a loss of approximately US$112.5 million. This incident at Concentric once again proves that if not prevented, traditional social engineering attacks will have a devastating impact on the security of Web3.0 ecological projects.
 Dante
Dante











