When choosing a blockchain interoperability solution, whether it's a best-in-class protocol or the world's leading financial institution, security should be a top consideration. As asset managers and banks increasingly tokenize real-world assets, end users will continue to pay increased attention to cross-chain security. In this article, we’ll explore some industry best practices for selecting and integrating cross-chain solutions.
1. Use an independent risk management network
Robust security for cross-chain solutions requires independent monitoring of cross-chain transactions, with the ability to detect suspicious activity and halt the network when necessary. This capability is necessary for cross-chain solutions to achieve the fifth and highest level of cross-chain security.
2. Use decentralized infrastructure
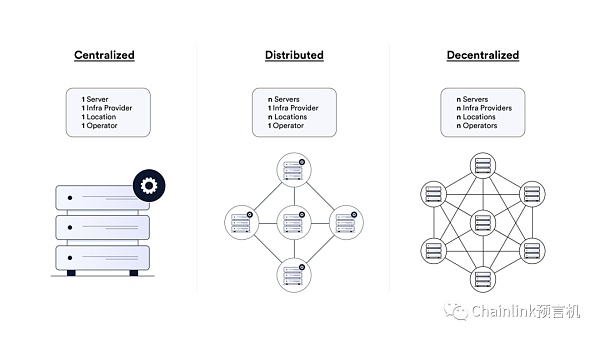
Centralization, distribution and decentralization Comparison of centralized infrastructure
Eliminating single points of failure is critical to maximizing the security, reliability, and independence of cross-chain protocols. A decentralized architecture with multiple nodes makes malicious insider attacks more difficult and ensures that centralized parties cannot control the network to gain an unfair advantage, such as front-running transactions by instructing end users to execute before they are executed.
3. Use established protocols
It is necessary to use only those established protocols whose availability, reliability, security, and high-integrity behavior have been proven. Not only is this critical to safeguarding your protocol, but it’s also important to attract liquidity from users who value the high security standards provided by established protocols.
4. Understand the impact of vendor lock-in
Cross-chain vendor lock-in occurs when a protocol becomes dependent on a specific cross-chain solution and cannot quickly move to an alternative solution due to switching costs and/or operational impact that are too high. This is critical in the Web3 space, as applications must maintain their ability to quickly and easily integrate alternative cross-chain solutions to address security vulnerabilities and reliability issues. Historically, assuming that your cross-chain solution will outlive your protocol has been a costly mistake for many. Furthermore, granting token authority to a cross-chain solution that is neither fully secure nor future-proof is inherently high-risk.
In addition, since the blockchain industry is constantly developing dynamically, new chains often emerge, and it is important for dApps to be able to connect to the most liquid and demanding Ecology is very important. The easiest way to avoid vendor lock-in is to leverage cross-chain solutions that adhere to open standards to prevent getting stuck in obsolescence.
5. Consider the risks of multi-bridge architecture
In addition to introducing unnecessary trust assumptions, multi-bridge architecture also reduces the security of the protocol in many aspects. Architectures that allow any cross-chain bridge to mint and burn tokens increase the attack surface for malicious actors, while cross-chain bridges that use multiple cross-chain solutions to reach consensus in a multi-signature mode reduce activity and increase costs while auditing , implementation and maintenance are more complex. Additionally, a multi-bridge architecture increases integration time and maintenance costs, makes it more difficult for users to verify an application’s security assumptions, and gives users access to potentially unsafe cross-chain bridges.
Interacting with the on-chain economy only through a single high-security cross-chain solution without using cross-chain bridges, protocols and institutions can improve the performance of applications. security while reducing development needs and ongoing maintenance costs.
6. Carry out code audit
Smart contract auditing is a detailed analysis and review of application code to identify security vulnerabilities beforehand. This allows you to address vulnerabilities before deploying to mainnet and prevent malicious actors from causing costly attacks on you. Auditing is very important for all Web3 applications responsible for safeguarding value, especially for cross-chain applications, as up to $2.75 billion in value has been stolen from these applications. Learn more about how to audit smart contracts.
Detailed video:
https://youtu.be/ylP44hSbI1o
(Copy the link to the browser to open)
7, Set rate limits for token transfers
Rate limits refer to the ability to limit the amount of value flowing on a cross-chain solution within a certain period of time. This adds an extra layer of security, limits the impact of an attack, and is especially important for protocols that guarantee a large amount of value.
8. Plan a multi-chain ecosystem in advance
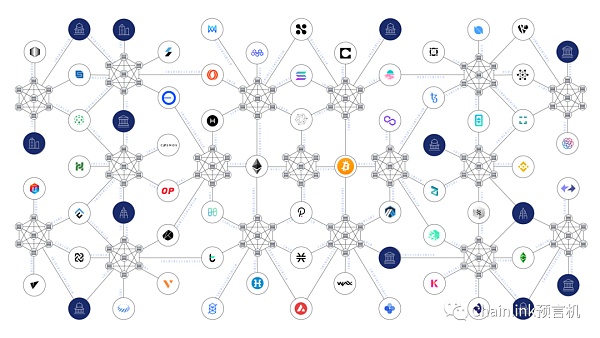
Multi-chain ecological overview
As the future of Web3 will become a multi-chain ecosystem with hundreds or even thousands of public and private blockchains, the chosen cross-chain solution should be able to secure Efficiently connect the chains. In contrast, local cross-chain bridges only provide a single channel on each bridge, which means that a multi-chain ecosystem relying on local cross-chain bridges will require many independent cross-chain bridges, increasing complexity and expanding the attack surface. In order to send tokens between Layer 2 of a multi-chain ecosystem that relies on local cross-chain bridges, they need to send through Layer 1 or use wrapped tokens, which brings liquidity management issues.
For multi-chain ecology, compared with cross-chain bridges, cross-chain solutions with secure destruction and minting mechanisms can be simply deployed on multiple on the chain, and achieve seamless flow of liquidity between Layer 2.
Conclusion
The reason why protocols like Swell turn Chainlink Cross-Chain Interoperability Protocol (CCIP), because CCIP provides an open standard for cross-chain communication, can seamlessly connect any public chain, private chain and traditional systems, and is actively monitored by the risk management network, with unparalleled Level of decentralization. Taking into account the above factors, as well as a series of defense-in-depth methods, CCIP is currently the most secure cross-chain solution. This is why leading organizations in the global economy, such as Swift, DTCC, ANZ Bank and Vodafone, are actively exploring CCIP.
 JinseFinance
JinseFinance







