Source: Fairyproof
2023 has quietly come to an end, and the crypto market has also ushered in a new year. WithETF With the advancement of 2024the year will be a very eye-catching year, and security will also reach an unprecedented level of attention in the industry. At the turn of the old and new,Fairyproofcombines and analyzes the security dimensions of the2023industry, aiming to provide Audience A comprehensive and in-depth annual security report, the following is the text of the report.
Viewpoint Summary
Compared with 2022, the situation of the crypto market has improved significantly in 2023, and the overall market value of crypto assets has increased. There has been a significant increase, and at the same time, the number of security incidents has also increased significantly.
- In 489 typical cases investigated by Fairyproof, nearly $1.23 billion worth of crypto assets were stolen.
- With the rapid growth of Bitcoin, especially the Inscription ecosystem, the security risks of this ecosystem have become increasingly prominent. In 2023, there were 13 attacks against the Bitcoin ecosystem, especially the Inscription facilities.
- Attacks launched by hackers using private key leaks caused crypto asset losses of US$518 million, which accounted for 45.07% of all losses caused by hacker attacks. Keeping private keys safely and securely is always the top priority for all blockchain users.
- In 2023, Fairyproof conducted extensive research on technologies and applications related to zero-knowledge proof [1], and became familiar with the mainstream solutions and application scenarios in the industry. In terms of development, Fairyproof has polished a complete set of processes and models to quickly develop and deploy solutions based on user needs and application scenarios. In terms of auditing, Fairyproof has accumulated rich experience and is able to skillfully convert target problems into zero-knowledge circuits and professionally audit circuits, proof generation, proof verification, etc. In addition, Fairyproof has also optimized the implementation of zero-knowledge applications and developed its own system, which is better in terms of security and decentralization than existing popular solutions.
- In 2023, Fairyproof also has a bold layout in multi-party secure computing [2] (referred to as MPC) technology, and has also established its own complete set of development processes and models that can respond to customer needs and scenarios. MPC solutions need to be developed and deployed quickly.
Background introduction
Before presenting the results of Fairyproof’s research report in detail, it is necessary to understand the relevant terms in this report Explain and explain.
CCBS
CCBS refers to "centralized crypto-asset or blockchain service organization". It usually refers to an off-chain service platform that is manually operated and managed. Its core technology mainly relies on traditional centralized technology, and its daily operation and maintenance activities are mainly off-chain activities. Traditional crypto asset exchanges (such as Binance) and crypto asset issuance and acceptance platforms (such as Tether) are examples of this type.
FLASHLOAN
Flash loan is a common and popular way for hackers to attack smart contracts on the Ethereum Virtual Machine platform. Flash loan is a contract calling method invented by the well-known DeFi application AAVE[3] team. This contract call allows users to directly lend crypto assets from DeFi applications that support this function without any collateral. As long as the user returns the asset within a block transaction, the transaction will be valid [4]. This function was originally invented to give DeFi users a more flexible and convenient way to conduct financial activities on various necklaces. But later, due to its high flexibility, the most used scenario for flash loans became hackers lending ERC-20[5] tokens and then using them to carry out attacks. Before initiating a flash loan, users need to clearly describe the logic of lending (assets) and returning (assets, interest and related fees) in a contract, and then call the contract to initiate a flash loan.
CROSS-CHAIN BRIDGE
Cross-chain bridge is an infrastructure that connects multiple independent blockchains. It allows deployment on different blockchains Tokens circulate among various blockchains.
As more and more blockchains have their own ecology, applications and encrypted assets, the demand for cross-blockchain communication and transactions among these applications and assets has grown significantly. This also makes cross-chain bridges a popular target for hackers.
Report Highlights
Fairyproof conducted a detailed study of 489 typical security incidents that occurred in 2023. In this report, statistics were collected on various factors such as the amount of losses and causes of these incidents. analysis and provide corresponding prevention suggestions and measures.
Statistics and analysis of security incidents in 2023
The Fairyproof research team conducted a detailed study of 489 prominent security incidents in 2023, listing them from the targets of attacks and the root causes of attacks. The statistical results were obtained and analyzed.
In the whole year of 2023, the total loss of crypto assets caused by these 489 security incidents reached 1.23 billion U.S. dollars, and the total value of mainstream crypto assets displayed by Tradingview reached 1.62 trillion U.S. dollars. The proportion of lost assets to total market value was 0.08%.
Security incidents based on the classification of victim objects
The security incidents studied by Fairyproof can be divided into the following four categories according to their victim objects:
1. ; Centralized Encrypted Assets or Blockchain Service Organization (CCBS, CCBS referred to below is this concept)
2. Blockchains
3. Decentralized Applications (dApps)
4. Cross-chain Bridges
The CCBS security incidents referred to in this report refer to the CCBS system being attacked or compromised. In these incidents, assets held by CCBS are stolen or services are disrupted.
Blockchain security incidents refer to attacks or damage to the blockchain main network, side chains, or second-layer extension systems attached to the blockchain main network. Usually in these incidents, hackers launch attacks from inside the system, outside the system, or both, causing system software or hardware malfunctions and asset losses.
A dApp security incident refers to a dApp being attacked and unable to function properly, giving hackers the opportunity to steal the encrypted assets managed in the dApp.
Cross-chain bridge security incidents refer to cross-chain bridges being attacked, causing them to be unable to work properly, and even leading to the theft of the crypto-assets they handle.
Fairyproof divided a total of 489 incidents into the above four categories, and the proportion distribution chart is as follows:

As can be seen from the figure, the number of dApp security incidents accounts for 88.34% of the total. Among them, 20 were CCBS security incidents, 26 were blockchain security incidents, and 432 were Dapp security incidents.
Blockchain Security Incidents
Security incidents involving blockchain can be further subdivided into the following three categories :
i. Blockchain mainnets
ii. Side chains
iii. Layer 2 expansion system (Layer 2 solutions)
The blockchain main network is also called Layer 1. It is an independent blockchain with its own network, protocol, consensus and verifiers. The blockchain mainnet can verify transactions, data and blocks, all of which are completed by its own validators and ultimately achieve consistency. Bitcoin and Ethereum are typical blockchain mainnets.
A sidechain is a separate blockchain that operates in parallel with the main blockchain network. It also has its own consensus and validators, but it will be connected to the blockchain main network in some way (such as two-way anchoring [6]).
The second layer expansion system relies on blocks A system based on the chain main network, which requires the blockchain main network to provide security and eventual consistency [7]. It is mainly designed to solve the scalability of the blockchain main network and process transactions at lower fees and prices. Since 2021, the second-layer scaling system attached to Ethereum has developed rapidly.
Both the side chain and the second-layer expansion system are designed to solve the scalability of the blockchain main network. The main difference between the two is that sidechains do not rely on the main blockchain to provide security and consistency, but second-layer scaling systems do.
There will be a total of 26 blockchain-related security incidents in 2023. The figure below shows the proportions of the blockchain main network, side chains and second-layer expansion systems.
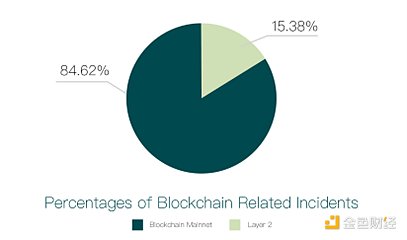
As shown in the picture It can be seen that the blockchain main network and second-layer expansion accounted for 84.62% (22 cases) and 15.38% (4 cases) respectively, and no serious side chain incidents occurred. The four cases involving the second layer extension of Ethereum are Metis [8], zkLink [9], Boba [10] and Arbitrum [11]. Among the incidents involving the blockchain main network, Mixin suffered the largest attack losses. Other attacks on main network projects were mainly social attacks and did not cause large asset losses.
DAPP Security Incidents
Among the 432 security incidents involving dApps, 45 were runaways, 263 were implicated, and 124 were directly attacked. Direct attacks on dApps usually involve three aspects: the Dapp’s front-end, back-end, and smart contracts. Therefore, we divided the 124 direct attack incidents into the following three categories:
i. dApp frontend
ii. dApp backend
iii. dApp Contract
In the case of dApp front-end attacks, hackers mainly launch attacks through front-end vulnerabilities to steal assets or paralyze its services.
In the case of attacks on the dApp backend, hackers mainly launch attacks through backend vulnerabilities, such as hijacking the communication between the backend and the contract, hijacking assets or paralyzing services.
In the case of attacks on dApp contracts, hackers mainly launch attacks through contract vulnerabilities, stealing assets or paralyzing their services.
The following figure shows the proportion of attack events in these three categories:
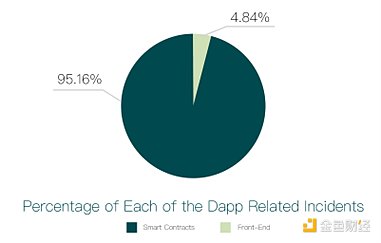
As shown in the above figure, the proportion of contract, backend and front-end attacks are 95.16%, 0% and 4.84% respectively. Of the total 124 incidents, 6 were front-end attacks and 118 were contract attacks.
We further studied the amount of crypto asset losses caused by various incidents. Among them, losses caused by front-end attacks amounted to US$238,000, and losses caused by contract attacks amounted to US$542 million.
Obviously, contract security remains the biggest issue. Among the many contract vulnerabilities, logical flaws, private key leaks, flash loan attacks, and reentrancy attacks are typical vulnerabilities.
We studied 118 security incidents involving contracts being attacked and obtained the following proportion chart:
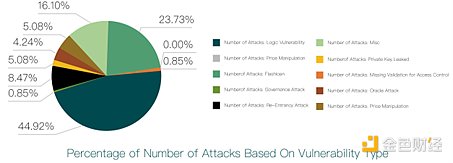
As shown in the figure above, logical flaws lead to the highest proportion of contract security incidents, followed by flash loan attacks. Logic defects usually include lack of parameter verification, lack of permission verification, etc. 53 incidents were related to logic flaws, and 28 incidents were related to flash loans.
The following figure shows the loss ratio caused by each vulnerability:

As can be seen from the above figure, the amount of losses caused by logical defects ranks first among all categories, with 53 cases. Security incidents caused losses of US$286 million, accounting for 52.83% of the total amount; losses caused by private key leaks ranked second, with 6 incidents causing losses of US$174 million, accounting for 32.1%; losses caused by reentrancy attacks The amount of losses ranked third, with 10 security incidents causing losses of US$29.06 million, accounting for 5.36%.
Safety accidents based on cause classification
Based on the causes of blockchain safety accidents, we divide accidents into three categories:
i. ; Caused by hacker attacks
ii. Escape
iii. Others
Our research results are shown in the figure below:
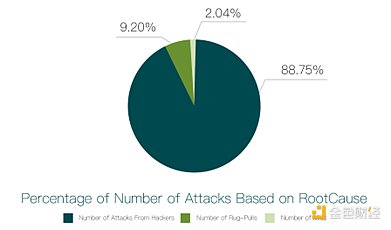
As shown in the picture above, the hacker Safety accidents caused by attacks and escapes accounted for 88.75% (434 incidents) and 9.2% (45 incidents) respectively.
We studied the losses caused by these causes, as shown in the figure below:
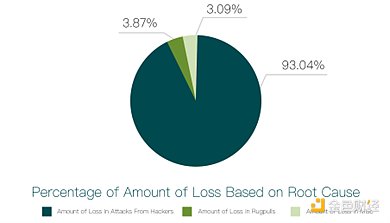
As shown in the figure above, the losses caused by hacker attacks and escapes accounted for 93.04% and 3.87% respectively, with the former resulting in US$1.15 billion. losses, the latter resulting in losses of $47.76 million. This shows that in 2023, hacker attacks will still be the main threat to industry security.
Hacker attack incident
We studied the hacker attack incident, as shown in the following figure:

The asset losses caused by hackers’ attacks on dApp, CCBS and blockchain were 58.95%, 24.03% and 17.02% respectively. The specific The losses were US$694 million, US$283 million and US$200 million respectively.
Runaway incidents
The runaway incidents that occurred in 2023 mainly occurred in dApp projects. A total of 45 starting road incidents caused losses amounting to US$47.76 million. This loss amount is much smaller than the loss caused by hacker attacks.
Research findings
From our statistical data, hackers’ most preferred target in 2023 will still be It is a dApp project. The number of attacks on dApps far exceeds that of any other object. However, the asset losses caused by it are the highest, reaching 694 million US dollars, accounting for 58.95% of the total amount of all attacks. This shows that there are considerable concerns about the current security situation of dApps, and it is a key issue that needs to be paid attention to for the security of the entire blockchain ecosystem.
For the entire blockchain ecosystem, hackers are still the biggest security threat, both in terms of the number of security incidents they cause and the asset losses they cause, caused by hacker attacks The number of security incidents accounted for more than 88.75% of the total number of security incidents, and the amount of asset losses caused by attacks accounted for more than 93.04% of all losses, far exceeding the threat to the ecosystem caused by escape incidents.
In 2023, hacker attacks on second-tier extension systems will be lower than in 2022, both in terms of number and amount of losses. We believe this is the result of the more mature layer-2 extension technology and the greater emphasis on security.
A typical dApp consists of three parts: front-end, back-end and smart contract. When a hacker attacks a dApp, they attack part of it or multiple parts at the same time. According to our statistics, attacks on smart contracts far exceed attacks on front-end and back-end in both quantity and value. This shows that smart contracts are still the main target for hackers to attack dApps.
Typical escape incidents that will occur in 2023 are all dApp projects. This shows that dApp scamming is still a key point that users should guard against when considering the risk of scamming.
Among the incidents where smart contracts are attacked by hackers, the number of attacks and the amount of losses caused by logical flaws top the list, far exceeding other categories.
Exploration and thinking
More and more entrepreneurial teams have and are planning to flock to zero-knowledge proof-related application fields, including the second layer extension of ZK based on Ethereum solutions, ZK-based social applications, etc. We believe that with the explosion and emergence of these applications, the demand for the development and auditing of ZK-based systems will grow rapidly.
Practical plans and measures to prevent safety accidents
In this section, we will base on the safety incidents that occurred in 2023 The characteristics of the accident summarize some plans and measures to help blockchain developers and users manage and prevent blockchain risks. We recommend that both blockchain developers and users actively implement and practice these plans and measures as much as possible in daily operations and work to maximize the protection of project security and crypto-asset security.
Note: "Blockchain developers" refer to both the development engineers of the blockchain project itself, and developers related to the blockchain system or its extension systems (such as encrypted assets, etc.). "Blockchain users" refer to all users who participate in blockchain system activities (such as management, operation, maintenance, etc.) or encrypted asset transactions, etc.
For blockchain developers
Developers of cross-chain bridges need to pay close attention to the security of cross-chain bridges. Cross-chain bridge solutions generally include on-chain operations and off-chain operations. Off-chain operations are relatively more vulnerable to hacker attacks, so cross-chain bridges need to pay special attention to the security and reliability of off-chain operations.
Although the amount of losses caused by second-layer extension attacks in 2023 is not large compared to cross-chain bridges, its security is also worthy of attention. Because in the future, there will be a blowout in the development and implementation of the second-layer expansion solution, and research on the security of the solution will be a major challenge facing the industry.
In blockchain applications, after the project is deployed and has been running stably for a period of time, it is a very necessary step to transfer the authority to control key operations in the project to a multi-signature wallet or DAO organization for management.
When hackers discover vulnerabilities in smart contracts, they often use flash loans to attack the contracts. These vulnerabilities that may be exploited usually include reentrancy vulnerabilities, logical flaws (such as lack of permission verification, wrong price algorithm), etc. Rigorous prevention and handling of these vulnerabilities requires smart contract developers to pay great attention at all times, and even needs to be ranked at the top of the list of importance.
Our statistics also show that more and more hackers will launch phishing attacks through social media software (such as Discord, Twitter, etc.). This phenomenon lasts throughout 2022. Many users suffered losses from it. Project parties need to implement strict and comprehensive management of the social media they operate, deploy corresponding security solutions to ensure the safety and stability of their social media operations, and prevent them from being exploited by hackers.
Blockchain users
More and more users are beginning to participate in various blockchain ecological activities and hold various blockchain ecological assets. In this process, cross-chain transaction activities have also grown rapidly. When users participate in cross-chain transactions, they need to interact with cross-chain bridges, which are often targeted by hackers. Therefore, before initiating cross-chain transactions, users need to conduct detailed investigations and understand the security and operating conditions of the cross-chain bridge they use to ensure the safety, stability, and reliability of the cross-chain bridge.
When users interact with dApps, they must pay close attention to the quality and security of their smart contracts, and they also need to pay attention to the security of the dApp front-end. Be careful with some unknown and highly questionable information, prompts, conversations, etc. displayed on the front end, and do not click or follow their guidance at will.
We strongly recommend that users carefully check and read the audit report of any blockchain project before interacting with or investing in a blockchain project. Be cautious about participating in projects where there is no audit report or where the reporting is questionable.
We recommend that users try to use cold wallets or multi-signature wallets to manage large amounts of assets or assets that are not used for frequent transactions. Always be careful about the operational security of hot wallets and ensure that the hardware platform itself on which the hot wallet is installed is safe, reliable and stable.
Users need to conduct a certain degree of investigation and understanding of the team background of the blockchain project. Be careful with teams with unclear team backgrounds and lack of credibility. Be careful about possible runaway risks for this type of project. For centralized exchanges that are used more frequently, users should pay more attention to their background and credit, and verify the background, information, and data of these exchanges from multiple third-party data sources as much as possible to ensure the long-term and sustainable safe operation of the exchange.
Reference materials
[1] zero-knowledge proof. https://en.wikipedia.org/wiki/Zero- knowledge_proof
[2] MPC. https://en.wikipedia.org/wiki/Secure_multi-party_computation
[3] Aave. https://aave.com/
[4] Flash-loans.. https://aave.com /flash-loans/
[5] ERC-20 TOKEN STANDARD. https://ethereum.org/en/developers/docs/standards/tokens/erc -20/
[6] Sidechains. https://ethereum.org/en/developers/docs/scaling/sidechains/
[7] Layer-2. https://academy.binance.com/en/glossary/layer-2
[8] Metis. https://www.metis.io/
[9] zkLink. https://zk.link/
[10] Boba. https://boba.network/
[11] Arbitrum. https: //arbitrum.io/
 Edmund
Edmund
















