Author: Dilip Kumar Patairya, CoinTelegraph; Compiler: Deng Tong, Golden Finance
1. What is a DDoS attack?
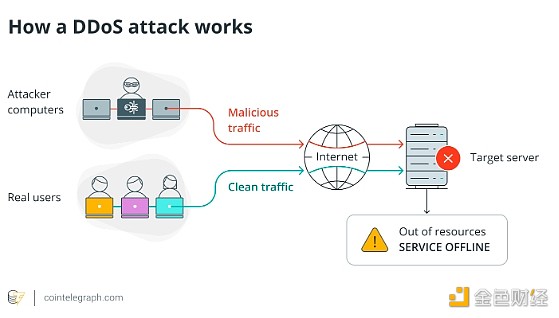
A distributed denial of service (DDoS) attack attempts to destroy a website, computer, or online service by sending a large number of requests to it, exhausting its capacity and affecting its ability to respond to valid requests.
A DDoS attack involves hackers inserting malware into potentially thousands of Internet-enabled devices (collectively known as a botnet) and prompting them to send a large number of requests to the target system at the same time. These infected machines, called robots or zombies, may be mobile phones, desktops, servers, or even Internet of Things (IoT) devices. Attackers establish direct control over robots by infecting them with malware, usually without the victim's knowledge.
The influx of incoming traffic makes it impossible for the target system to respond to valid requests because the attack consumes too much bandwidth, processing power, or memory. In its Q1 2024 DDoS Threat Report, Cloudflare noted that DDoS attacks increased by a shocking 50% overall.
2. Is it possible for a blockchain network to be attacked by DDoS?
It is theoretically possible to attack a blockchain network through a DDoS attack, although it is more difficult than targeting a centralized system such as a website or server. Due to its decentralization, the blockchain network is inherently resistant to such attacks.
As a decentralized distributed ledger, the blockchain runs on a series of nodes responsible for verifying and processing transactions and creating blocks. Unlike traditional systems, there is no central control point within the blockchain network. Decentralization makes the blockchain network more difficult to attack because attackers need to deal with a large number of nodes.
One way to disrupt a network is to flood the blockchain with spam transactions, which overwhelms the network and reduces transaction throughput, hindering the timely verification of legitimate transactions. This queues transactions from real users into the memory pool, a mechanism in blockchain nodes that stores unconfirmed transactions.
A well-known example of a DDoS attack is the Solana blockchain network, which caused a 17-hour downtime in September 2021. During Grape Protocol's first decentralized exchange offering (IDO) on the Solana-based DEX Raydium, bots had a load of 400,000 transactions per second on the network, causing network congestion.
In addition, DDoS attacks may target decentralized applications (DApps), which are applications built on top of blockchains, rather than the blockchain network itself. Cryptocurrency exchanges play a key role in ensuring liquidity in blockchain-based ecosystems and often fall victim to DDoS attacks, resulting in temporary service interruptions.
How do DDoS attacks affect blockchain networks?
DDoS attacks can impact blockchain networks by flooding them with transactions and compromising smart contracts. The goal is to clog the network with fraudulent transactions, slowing it down, or in worse cases, even bringing it to a halt.
Transaction flooding
Malicious actors may intentionally overload a blockchain network with a large number of transactions, disrupting its normal operation. Attackers typically use automated scripts or specialized software to trigger a flurry of transaction requests. These transactions resemble legitimate transactions but are designed to overwhelm the network.
The attacker broadcasts these transactions to nodes. To reach consensus, the network propagates transactions to multiple nodes, which are responsible for processing them. However, the large number of incoming transactions exceeds their processing capacity. The network becomes congested and even genuine transactions are backlogged. This disruption can affect businesses, exchanges, and other services that rely on blockchain networks.
Smart contracts
Hackers can identify vulnerable smart contracts in a blockchain network and flood them with transaction requests. These transactions contain fraudulent instructions or excessive computations to exhaust the functionality of the contract and the underlying network. The execution of the code in the smart contract becomes increasingly burdensome, causing excessive delays in transaction verification.
Since smart contracts are a critical part of blockchain, the effects of such attacks can propagate throughout the network, affecting other smart contracts and transactions, disrupting critical operations and making services inaccessible to legitimate users.
Software Crashes
The core application software in blockchains has built-in limits on the memory allocated and the number of transactions it can process in a block and store in the memory pool. When transaction volume surges, the software may behave unexpectedly or crash outright.
In addition, immutability is an inherent feature of blockchain transactions, meaning they cannot be changed once they are recorded in a block. This mechanism creates problems when transactions flood the network during an attack. The network is overloaded with useless transactions, which may be far more than the software can handle.
Node Failures
Nodes that act as validators or miners run the core blockchain software on equipment powerful enough to handle the rigorous demands. When malicious actors stream in large amounts of junk data in a DDoS attack, the node may run out of memory or processing power and crash. The failure of one node due to an attack increases the pressure on other nodes in the network.
A blockchain network is essentially a merger of nodes, where each receiving node tracks the state of the blockchain and broadcasts information about transactions to other nodes. The proliferation of fraudulent transactions has a detrimental effect on the node architecture, slowing down the entire network or even paralyzing it.
How DDoS attacks affect cryptocurrency exchanges
Cryptocurrency exchanges are an integral part of the blockchain ecosystem as they enable liquidity for digital assets. They are often the target of attackers.
When attacking exchanges, the modus operandi of attackers is to exploit vulnerabilities, such as outdated security patches in the exchange infrastructure, disrupt operations, extort ransoms, or manipulate the market. According to Cloudflare, DDoS attacks against cryptocurrency exchanges mainly come from Simple Service Discovery Protocol (SSDP) amplification attacks, Network Time Protocol (NTP) amplification attacks, and application layer attacks.
SSDP attacks are a reflection-based DDoS attack that leverages the Universal Plug and Play (UPnP) network protocol to dispatch large amounts of traffic to the target system. NTP attacks refer to techniques where an attacker sends a series of small queries that trigger large responses from different robots, thereby multiplying traffic. Application layer attacks refer to attacker methods that target the top layer of the Open Systems Interconnection (OSI) model.
Fourth, how to prevent DDoS attacks on blockchain networks
To protect blockchain networks from DDoS attacks, security measures need to be taken at the node and network levels. Regular audits deal with vulnerabilities, while redundant infrastructure and stress testing keep the network running even during attacks.
Node-level security measures
Nodes should have sufficient storage, processing power, and network bandwidth to withstand DDoS attacks. Strong authentication methods and access controls help protect network nodes. Completely Automated Public Turing Test to Tell Computers and Humans Apart (CAPTCHA) is useful for ensuring that only legitimate users can send transaction requests and preventing robots from infiltrating the network. Load balancing helps divide traffic and mitigate the impact of node-level attacks.
Network-level protection
Establishing adequate defense mechanisms at the network level is very important for protecting blockchain networks. To identify and reduce the impact of DDoS attacks, firewalls and intrusion detection/prevention systems (IDS/IPS) can play a good role. Content delivery networks (CDNs) can also help disperse and absorb attack traffic.
Auditing
To find and fix any vulnerabilities, it is important to conduct a thorough audit of all aspects of the blockchain. This should include analyzing smart contracts, auditing the integrity of blockchain data structures, and verifying consensus algorithms. The fault tolerance of the consensus mechanism should be strong enough to withstand attacks. Regular code updates are important to thwart attackers and improve security.
Stress Testing
Networks and Systems
Blockchain protocols should be stress tested regularly to assess their ability to withstand DDoS attacks. This will help identify potential vulnerabilities in a timely manner, allowing the network infrastructure to be patched and defense mechanisms to be upgraded.
Redundancy and Backup
Blockchain protocols and DApps need to have redundant network infrastructure and backup servers to ensure that the system remains operational even when attacked. Nodes located in multiple geographical locations can resist DDoS attacks that are limited to a specific area.
 Xu Lin
Xu Lin








