Author: Jagjit Singh, CoinTelegraph; Compiler: Wuzhu, Golden Finance
1. Potential vulnerabilities in smart contracts
Despite the groundbreaking nature of smart contracts, it is not immune to flaws that can be exploited by malicious parties.
Insufficient input validation is a common weakness that enables attackers to affect the execution of contracts by providing unexpected inputs. In addition, improper application of business logic can produce unexpected behavior or logic gaps in contracts, leading to vulnerabilities. In addition, unsafe external calls (such as those involving interfaces with external data sources or other contracts) can cause vulnerabilities if not handled properly.
A reentrancy attack is a weakness that occurs when a contract calls another contract externally before completing its own state changes. This allows the called contract to reenter the calling contract and potentially perform some of its operations again. This can cause unexpected behavior and allow an attacker to change the state of the contract, draining funds or having other negative effects.
Given the possibility of such attacks, developers should also exercise caution when using external contracts or data sources, ensuring that external calls are properly handled to avoid unexpected behavior and vulnerabilities. They can help protect smart contracts from evolving threats by paying close attention to security procedures such as smart contract testing.
What is a reentrancy attack in smart contracts?
In a smart contract, a reentrancy attack occurs when a contract calls another contract or function from the outside before completing its own state change.
This allows the called contract to reenter the calling contract and potentially execute parts of its operations again, which can lead to unforeseen and frequent malicious behavior. For example, contract A calls contract B to send funds and then modifies its own state.
Contract B's code may contain a callback function that allows it to reenter contract A and potentially re-execute the transfer function before contract A completes its state change. This would allow an attacker to extract funds from the contract multiple times before completing the initial transaction.
The infamous 2016 Decentralized Autonomous Organization (DAO) hack on the Ethereum blockchain is another well-known example. The attacker exploited a reentrancy flaw in the smart contract code to recursively remove funds from the DAO, ultimately resulting in the theft of millions of dollars worth of Ethereum (ETH).
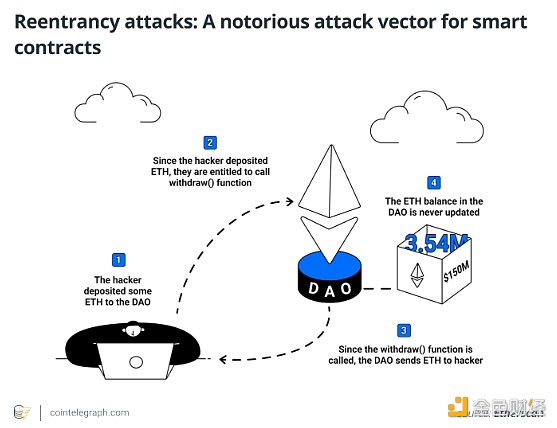
In addition, multiple decentralized finance (DeFi) protocols, including Uniswap, Lendf.Me, BurgerSwap, SURGEBNB, Cream Finance, and Siren Protocol, have suffered significant financial losses due to reentrancy vulnerabilities. These breaches have resulted in losses ranging from $3.5 million to $25 million, highlighting the ongoing threat posed by reentrancy vulnerabilities in the DeFi space.
3. How reentrancy attacks work
Reentrancy attacks exploit the sequential execution of smart contract functions and external calls to form a loop, where an attacker can execute a specific function multiple times before completion, which can lead to malicious behavior and unapproved fund withdrawals.
The attacker's contract effectively "tricks" the victim's contract into calling back the attacker's contract before the victim has completed the state modification. This action can result in repeated withdrawals or other negligent behavior.
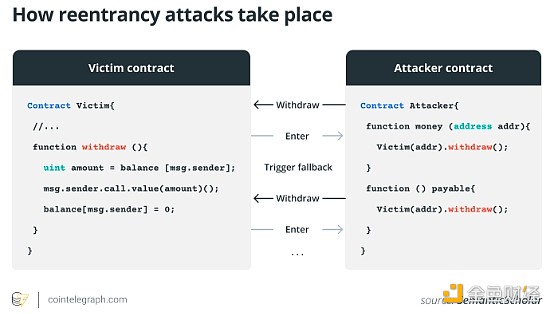
The above figure demonstrates a reentrancy attack on a smart contract. The attacker's contract calls the victim's "withdraw()" function, which sends Ethereum before updating the balance. The attacker's fallback function is then triggered, recursively calling withdraw() again to drain funds from the victim contract. This attack exploits the situation where the victim fails to update the balance before sending funds.
Let's break down how a reentrancy attack works using a simplified example:
Smart Contract with a "Withdraw" Function
Suppose there is a digital wallet smart contract that allows users to withdraw funds. In addition to keeping track of user balances, this contract also has a withdraw function that facilitates fund withdrawals. The withdraw function typically allows users to withdraw their tokens or ether from the smart contract to their personal wallet.
User Interaction and Function Execution
Users request withdrawals from their wallets on their own accord. They use the withdraw function to enter the desired withdrawal amount.
The withdraw function verifies that the user has sufficient funds to make the withdrawal when it is called. If the requirements are met, it transfers the required funds to an address of the user's choice.
External Calls
This is where the weakness manifests itself. Before the withdrawal is reflected in the user's balance, the contract makes an external call to another contract or account.
Recursive Calls
If the code of an external contract contains a function that can call the original contract again (such as another withdraw function), a recursive loop is created. This makes it possible to call the withdraw method again before it completes.
Reentrancy Exploitation
The attacker then uses a malicious contract to exploit this loop. The attacker contract quickly calls the wallet's withdraw function again during the wallet contract's call to an external contract, before the balance is updated.
Fallback Function
In some cases, the smart contract's fallback function (a unique function that is initiated when a contract receives a call without any data or Ethereum) may be used by an attacker. Reentrancy attacks can be performed by repeatedly calling the fallback function while funds are still being processed.
Manipulation and Repeated Withdrawals
The attacker's contract can repeatedly use the withdraw function in the same transaction because the wallet contract delays updating the balance until after receiving an external call. Therefore, this makes it easier for funds to be withdrawn without authorization, allowing the attacker to steal funds beyond their legal rights. Subsequently, it causes huge financial losses to the users of the wallet contract.
Fourth, the consequences of reentrancy attacks
Reentrancy attacks have a serious impact on smart contract users because they have the potential to cause significant financial losses.
One of the most direct consequences of a reentrancy attack is the unauthorized withdrawal or manipulation of cash held in a vulnerable smart contract. Attackers exploited the vulnerability to repeatedly withdraw funds from a contract, draining the contract balance and potentially causing significant financial losses to users who have invested or stored assets in the affected contract.
In addition, reentrancy attacks can undermine user confidence in the security and integrity of smart contracts and blockchain technology. Reentrancy vulnerabilities can have catastrophic effects, as demonstrated by high-profile events such as the 2016 DAO hack on the Ethereum blockchain, which caused huge financial losses and damaged the community's reputation.
In addition to short-term financial consequences, reentrancy attacks can also have long-term effects, such as regulatory and legal attention, loss of investor trust, and damage to the reputation of blockchain platforms and projects. The perception of vulnerability to attack may cause users to be cautious when interacting with smart contracts or investing in decentralized applications (DApps), thereby hindering the adoption and expansion of blockchain technology.
V. How to Mitigate Reentrancy Attacks
Implementing best practices in smart contract creation and auditing is necessary to mitigate the threat of reentrancy.
This includes using well-known code libraries with a track record of security as one way to achieve this goal. These libraries have been extensively tested and peer-reviewed, which reduces the chances of introducing vulnerabilities.
Developers should also use security checks such as "check-effect-interaction" design to minimize the chances of reentrancy attacks by ensuring that state modifications occur atomically. If available, reentrancy-safe smart contract development frameworks can be used to add an additional line of defense against such vulnerabilities.
Developers are less likely to add security protections manually because these frameworks often include built-in methods and protections specifically designed to avoid reentrancy attacks. However, because blockchain security is still evolving, developers must continue to look for new threats and weaknesses.
 Kikyo
Kikyo








