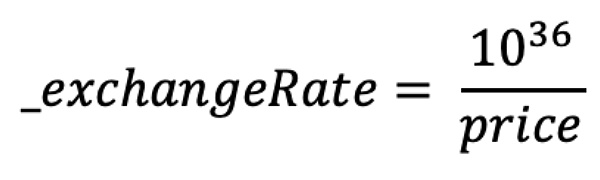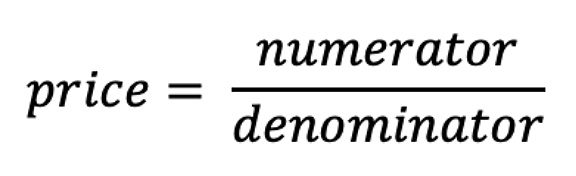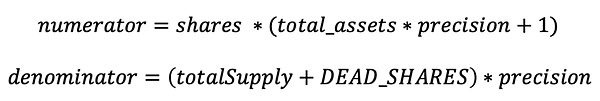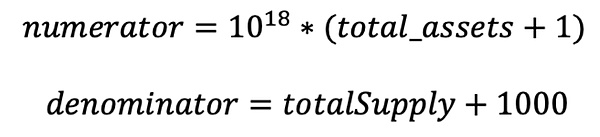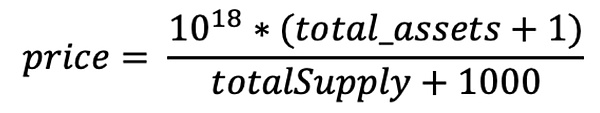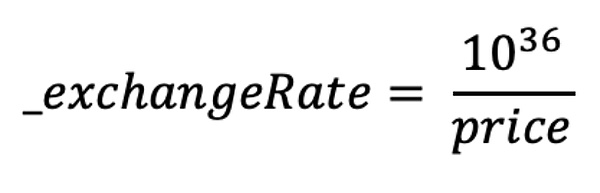On June 26, 2025, the contract deployed by the stablecoin protocol Resupply on the Ethereum mainnet was attacked, and about $10M of assets were lost. Due to problems in the implementation of the price oracle of the relevant contract, for the newly created low-liquidity Market, the attacker can manipulate the relative price (i.e. the exchange rate between the loaned asset and the mortgaged asset) of the loaned asset (the stablecoin reUSD issued by Resupply) to 0 through a donation attack, thereby bypassing the asset health check and lending a large amount of reUSD for profit.
BlockSec provided a preliminary analysis after the first public warning on the entire network[2, 3]. Resupply also released an official announcement later[4], but many technical details were not elaborated in detail. This article will provide a more detailed analysis. On the other hand, after the attack, there was also a fierce community dispute between the project party and its related parties[5]. This article will deeply analyze and explore the complex ecological relationship behind the protocol for readers' reference.
Background
1.1 About Resupply Protocol
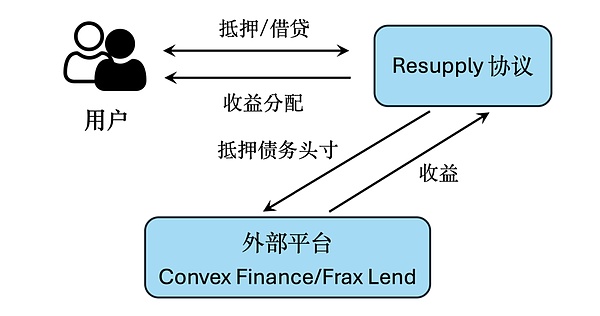
Resupply is a decentralized stablecoin protocol[1], part of the Curve ecosystem. The stablecoin issued by Resupply is called reUSD, which is a decentralized stablecoin backed by collateralized debt positions (CDPs) and supported by other stablecoins that earn interest in the lending market of external platforms, including crvUSD and frxUSD. Users can provide crvUSD and frxUSD to borrow reUSD and achieve stablecoin asset refinancing.
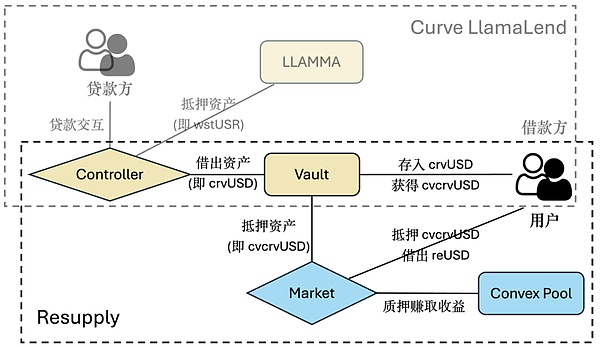
Specifically, users can perform lending and borrowing operations in a Resupply Market deployed on the chain. The creation and behavior of the Market are managed by DAO. Each Market specifies an ERC-4626 Vault as a collateral asset (collateral) and uses the asset corresponding to the Vault as the underlying asset (underlying). Users borrow reUSD by depositing collateral (Vault or Vault's asset) in the Market.
Taking Market 0x6e90 and Vault 0x0114 involved in the attack as an example, the related assets (tokens) involved are as follows:
Market 0x6e90:
Vault 0x0114:
asset: crvUSD (actually stored in Curve LlamaLend Controller, which is also a Market, not important for understanding the attack)
collateral: wstUSR (i.e. the collateral assets of Curve LlamaLend Controller)
borrowed: crvUSD (i.e. the collateral assets of Curve LlamaLend Controller
share: cvcrvUSD (i.e. Vault itself, ERC-4626 token), is the share corresponding to the asset
That is to say, users can pledge a certain amount of cvcrvUSD (or crvUSD, but it will actually be converted into cvcrvUSD through Vault) in the Market to borrow reUSD, as shown in the figure:
1.2 How to determine whether a user is eligible to lend a certain asset?
Similar to general lending protocols, Resupply Market will also perform asset health checks on users' positions (through modifier isSolvent).
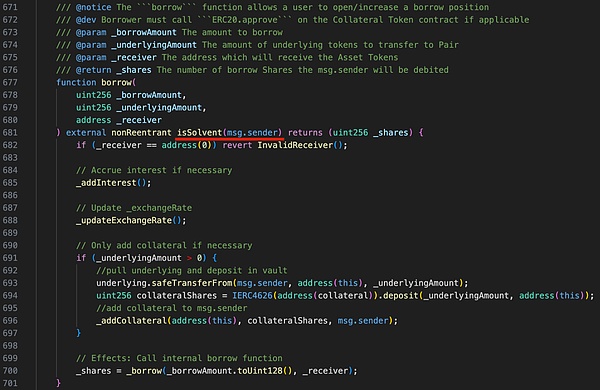
isSolvent will eventually call the _isSolvent function, where it checks the LTV (Loan-to-Value, loan-to-value ratio or lending rate), requiring that the ratio LTV between the user's lent assets and mortgage assets cannot exceed the maximum value set by the system (_ltv <= maxLTV).
It can be seen that the above LTV calculation depends on the exchange rate (_exchangeRate in the code), that is, the price of the lent asset compared to the mortgage asset (exchange ratio).
Attack Analysis
2.1 Root Cause Analysis
From the perspective of contract code, the key to the attack is that there is a problem with the price oracle implementation of the Resupply Market. For a newly created low-liquidity Market, an attacker can manipulate the exchange rate through a donation attack, thereby bypassing the health check and lending a large amount of reUSD for profit.
How to calculate the exchange rate in Resupply Market?
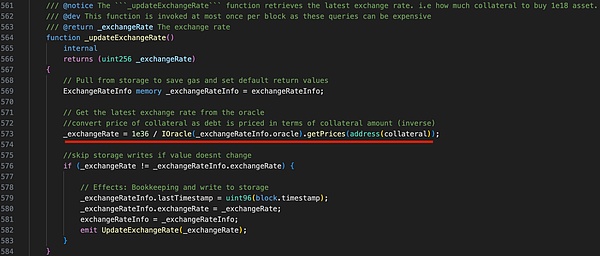
According to the above code, the calculation formula of the exchange rate is as follows:
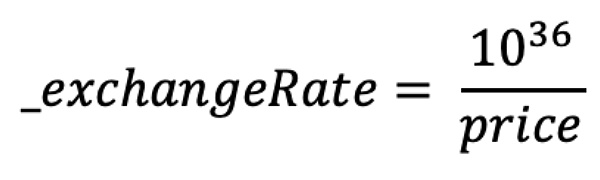
style="">Obviously, if the price returned by getPrices is greater than 1e36, rounding down from the integer division will result in _exchangeRate = 0.
How do I manipulate price?
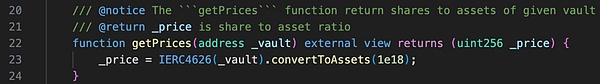
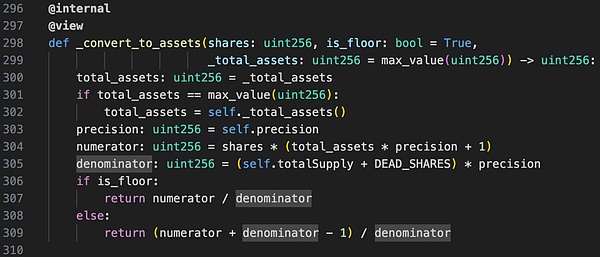
According to the above code, the calculation method of price is as follows:
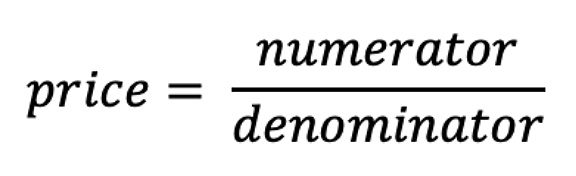
Among them:
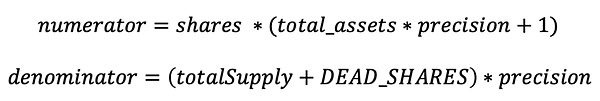
Since precision = 1, DEAD_SHARES = 1000, shares = 1e18 are set in the code, therefore:
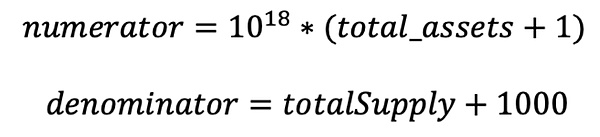
Finally, after substituting the variables, the calculation formula for price is as follows:
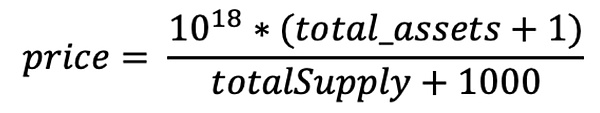
It can be seen that the key to amplifying the value of price is how to expand the gap between total_assets and totalSupply, so that total_assets is extremely large and totalSupply is extremely small. In the actual protocol implementation of Resupply, the total_assets in the formula depends on underlying (crvUSD), and totalSupply depends on the share (cvcrvUSD) corresponding to the overall liquidity in the Market. This is the classic donation attack scenario. 2.2 Analysis of attack transactions Based on the attack transactions [4], we can analyze that the attacker performed the following core operations: 1. Borrowed 4,000 USDC through flash loan and exchanged it for 3,999 crvUSD. 2. Donated 2,000 crvUSD to Controller 0x8970.
3. Deposited ~2 crvUSD into Vault 0x0114 and obtained 1 share (cvcrvUSD).
4. Add 1 unit (i.e. 1 share of Vault 0x0114) of collateral to Market 0x6e90.
5. Borrow 10,000,000 reUSD from Market 0x6e90.
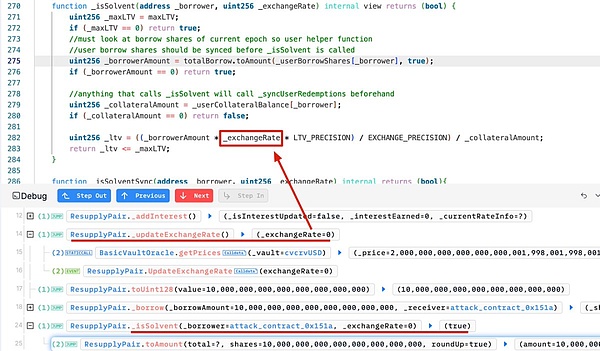
Why is _exchangeRate 0 at this time? Because the attacker manipulated the contract to the following state through the previous steps:
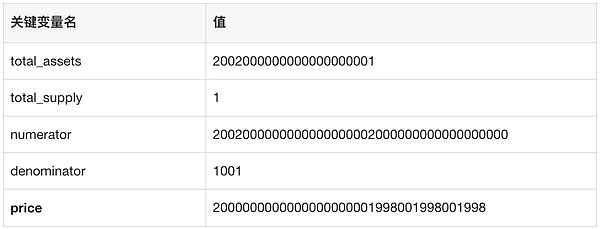
Review the calculation of the exchange rate:
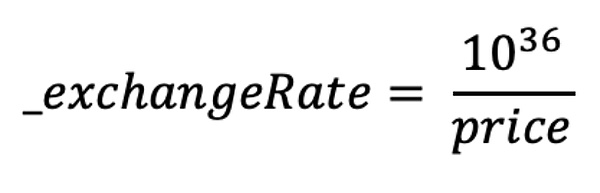
Since price > 1e36 at this time, _exchangeRate = 0.
6. Exchange the borrowed reUSD for profit.
Lessons Learned
Resupply The price oracle implementation in the attacked Market is similar to the template contract provided by Curve[11]:
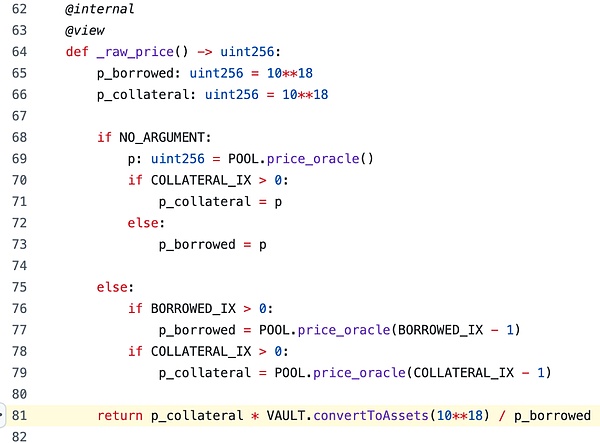
However, Curve gave the scope of application of this implementation:
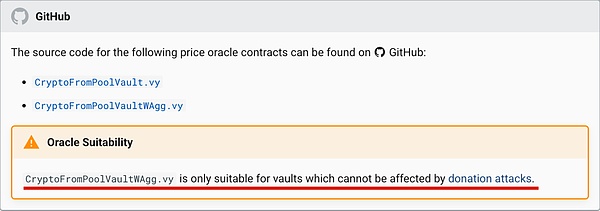
Unfortunately, the Resupply protocol does not appear to have been implemented with this applicability caveat in mind.
Relationships and community disputes
4.1 The complex relationship network of the five major projects in the Curve ecosystem
To understand the deep impact of the Resupply incident, let’s first look at the complex relationship between the five core protocols in the Curve ecosystem:
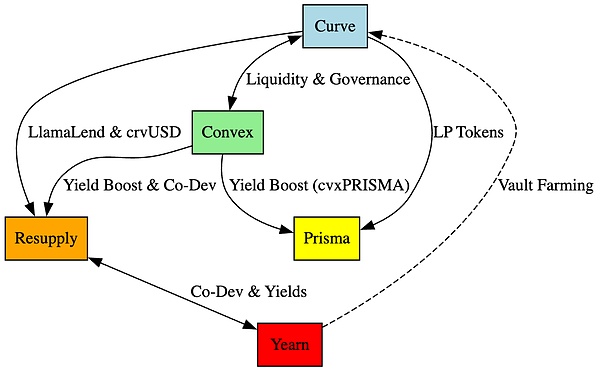
Curve Finance is the core of the entire ecosystem, providing liquidity pools, crvUSD and LlamaLend The Curve protocol supports the operation of Resupply, Prisma, Convex, and Yearn. Convex optimizes Curve's returns through staking and governance, and provides additional reward mechanisms for Prisma and Resupply. Prisma relies on Curve's LP tokens and Convex's yield enhancement functions, while Resupply issues reUSD directly based on Curve's LlamaLend and is jointly developed by Convex and Yearn. Yearn not only optimizes the returns of the Curve pool, but also promotes the development of Resupply through cooperation with Convex.
Curve Finance: As a core platform, Curve's liquidity pools (such as crvUSD pools) and LlamaLend protocols are directly used by Resupply to issue reUSD, Prisma is used to stake LP tokens, Yearn is used for yield optimization, and Convex is used for voting governance.
Convex Finance: Convex is Curve's yield enhancement protocol. Users can obtain higher CRV rewards and Convex's CVX tokens by staking Curve LP tokens. Convex controls nearly 50% of Curve's governance weight and provides a yield enhancement mechanism for Prisma and Resupply.
Prisma Finance: Prisma uses Curve's LP tokens for staking, and users receive enhanced rewards through Convex (cvxPRISMA). Prisma relies on Curve's liquidity and Convex's yield mechanism.
Yearn Finance: Yearn is a yield aggregator that provides users with high returns by optimizing the LP token returns of the Curve pool (such as enhanced by Convex). Yearn worked with Convex to develop Resupply and uses Curve pools extensively in its yield strategy.
Resupply: Developed jointly by Convex and Yearn, it allows users to obtain reUSD by lending stablecoins such as crvUSD, and automatically stake tokens on Convex to earn CRV and CVX rewards, forming a closed loop of yield optimization.
4.2 Controversy and Impact
However, when Resupply was attacked, this complex relationship immediately became the focus of controversy. Curve founder Michael Egorov quickly distanced himself from Resupply, emphasizing: "There is no single person from Curve working on that project... don't generalize to Curve please." This statement of distancing oneself from the project ironically reflects the fragility of the complex collaborative relationships in the DeFi ecosystem when faced with a crisis. The above-mentioned interrelated projects together constitute a highly coupled ecosystem - in such a system, problems in any link may trigger a chain reaction. Therefore, it is not surprising that the Resupply attack incident triggered extensive discussions in the community on the relevance and security of the protocol[5].
More Thoughts
5.1 Timeline
On May 17, 2025, the official address of Resupply 0x1f84 deployed a new LlamaLend Market[6] through Curve’s OneWay Lending Factory, where:
On May 31, 2025, a new proposal wstUSR-long LlamaLend Market[7] was launched on Resupply’s governance page. The proposal aims to allow users to mint reUSD through the LlamaLend Market.
On June 11, 2025, the proposal was released on the chain[8].
On June 26, 2025, 00:18:47 (UTC), the proposal was passed, and the Resupply official address 0x0417 deployed [9] a new ResupplyPair (ie, Resupply crvUSD/wstUSR Market) 0x6e90 on the chain. This Market:
On June 26, 2025, at 01:53:59 (UTC), about 1.5 hours after Market 0x6e90 was deployed on the chain, the attacker successfully carried out the attack[4]; at the same time, BlockSec detected the attack and tried to contact the project party.
On June 26, 2025, at 02:26 (UTC), after the project party failed and confirmed that no further losses could be caused, BlockSec issued a public warning[2].
On June 26, 2025, at 02:53:23 (UTC), the project party suspended the agreement[4]. 5.2 The tragedy could have been avoided if Phalcon had been available The ResupplyFi disaster movie was staged late at night, and the first alarm bell for the entire network was sounded by BlockSec Phalcon [2]: This was not an afterthought, but a warning bell that sounded at the moment the attack occurred.
By monitoring transactions at the memory pool stage, Phalcon can identify abnormal patterns the moment attack transactions enter the memory pool. Based on an AI-driven intelligent analysis engine, the system integrates more than 200 typical attack features and has maintained an ultra-low false alarm rate of less than 0.0001% in the past six months, achieving truly accurate threat detection.
When the threat is identified, Phalcon's automated attack blocking mechanism is immediately activated. The system uses an exclusively developed Gas bidding strategy to ensure that the protective transaction can preempt the attack transaction and automatically trigger the emergency pause function of the protocol. The entire response process supports multiple permission control modes such as EOA and multi-signature wallets, providing flexible security solutions for different types of protocols.
If Resupply had integrated the Phalcon system when the Market was deployed, the attack could have been completely avoided:
Within 1.5 hours after the Market 0x6e90 was deployed, the Phalcon system automatically detected the deployment of the new Market, intelligently analyzed its configuration parameters, and identified potential donation attack risks. The system immediately sent a risk warning to the project party, suggesting to increase initial liquidity protection or adjust relevant parameters. More importantly, when the attack transaction entered the memory pool at 01:53:59 UTC, Phalcon's AI algorithm immediately identified the typical donation attack mode, automatically triggered an emergency suspension of the transaction, and ensured that the protection transaction was executed first through Gas bidding, thus completely avoiding the loss of $10 million.
Resupply Countless attacks, including tens of millions of dollars, tell us that in the world of DeFi, security is not an option, but a necessity for survival. Don't wait until the next attack to regret it.
 Kikyo
Kikyo