Privacy is a fundamental right for humans and organizations. For individuals, it helps people express themselves freely without having to reveal any information they don’t want to share to third parties. For most organizations today, data is considered a primary commodity, and data privacy is critical to protecting this commodity. The cypherpunk movement and data commodification have accelerated the research and development of cryptographic primitives.
Cryptography is a fairly broad field, and when we look at cryptography in the context of computing, we have seen many different schemes, such as zero-knowledge proofs , homomorphic encryption, Secret sharing, etc., these solutions have been continuously improved since their birth in the 1960s. These solutions are critical to unlocking private computing methods (data is a primary commodity because people can discover and generate insights from it). To this day, the field of Private Computing has made significant developments in multi-party computation and zero-knowledge proofs, but there have always been privacy issues with the input data itself.
When the most important commodity is public, it is very difficult for any data owner to outsource the calculation of this data without a legal agreement. Today, everyone relies on data privacy compliance standards such as HIPAA for health data and GDPR specifically for data privacy in the European region.
In the field of blockchain, we believe more in the integrity of technology than in the integrity of regulatory agencies. As believers in permissionless and maximizing ownership, if we believe in a future where users own data, we need trustless ways to perform computation on that data. Until Craig Gentry's work in 2009, the concept of performing computations on encrypted data had not been a breakthrough. This was the first time anyone had been able to perform calculations (addition and multiplication) on ciphertext (i.e. encrypted data).

1. How FullHomomorphic Encryption (FHE) works
So, this What exactly is the "magic math" that allows computers to perform calculations without knowing anything about the input?
Fully homomorphic encryption (FHE) is a type of encryption scheme that allows calculations to be performed on encrypted data (ciphertext) without decrypting the data, providing privacy and Data protection opens up a range of use cases.
During the FHE process, when data is encrypted, additional data called noise is added to the original data. This is the process of encrypting data.
Every time a homomorphic calculation (addition or multiplication) is performed, additional noise is added. If the calculation is too complex and noise is added every time, it will eventually become very difficult to decrypt the ciphertext (which is computationally very heavy). This process is better suited for addition because the noise grows linearly, whereas for multiplication the noise grows exponentially. Therefore, if there are complex polynomial multiplications, decrypting the output will be very difficult.
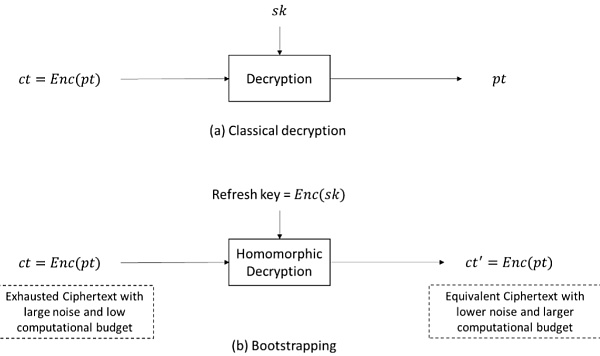
If noise is a major problem and its growth makes FHE difficult to use, it must be controlled. This gave rise to a new process called "Bootstrapping". Bootstrapping is the process of encrypting encrypted data using a new key and decrypting it within the encryption. This is very important as it significantly reduces the computational overhead as well as the decryption overhead of the final output. Although Bootstrapping reduces the final decryption overhead, there will be a large amount of operational overhead in the process. This can be expensive and time-consuming.
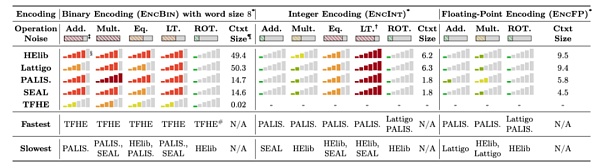
The current main FHE solutions are: BFV, BGV, CKKS, FHEW, and TFHE. Except for TFHE, the abbreviations of these schemes are the names of the authors of their papers.
Think of these scenarios as different languages spoken in the same country, each optimized for different things. The ideal would be to unify the country, where all these languages can be understood by the same machine. Many FHE working groups are working to achieve composability of these different scenarios. Libraries like SEAL (combined BFV and CKKS schemes) and HElib (BGV + approximation CKKS) help implement FHE schemes or combinations of schemes for different calculations. For example, Zama's Concrete library is a Rust compiler for TFHE.

2. FHE scheme comparison
The following are Charles Guth and Dimitris · Mouris and Nectarios George Chusos in their paper "SoK: New Insights into Fully Homomorphic Encryption Libraries via Standardized Benchmark" (2022) Performance comparison of different libraries.
Web3 use cases
When we use blockchain and applications today, all data is public and available to everyone All can be seen. This is beneficial for most use cases, but completely limiting for many use cases that require privacy or data confidentiality by default (e.g. machine learning models, medical databases, genomics, private finance, games that cannot be rigged, etc.). FHE-powered blockchains or virtual machines essentially allow the state of the entire chain to be encrypted from the starting point, ensuring privacy while allowing arbitrary computations to be performed on the encrypted data. All data stored or processed on FHE-powered blockchain networks is inherently secure. Zama has a fhEVM solution that allows EVM computing in a fully homomorphic environment. This ensures privacy at the execution level for any L1/L2 project built using this library. Although Privacy Chain has always been a cool technology, adoption and token performance have not improved significantly.
In terms of outsourcing general computing, FHE itself is not intended to replace ZK and MPC. They can complement each other to create a trustless private computing giant. For example, Sunscreen is building a "privacy engine" that essentially allows any blockchain application to outsource computation to their FHE computing environment and feed the results back. The resulting calculations can be verified via ZK proofs. Octra is doing something similar, but using a different type of encryption scheme called hFHE.
ZK proof is good at proving something without revealing the data, but the prover still has access to the data at some point in time. ZK proofs cannot be used for computations on private data; they can only verify that certain computations were completed correctly.
MPC distributes the calculation of encrypted data across multiple machines, performs the calculations in parallel, and then splices the final calculation results together. As long as the majority of machines doing the calculations are honest, the original data cannot be retrieved, but this is still an assumption of trust. Due to the constant communication required between parties in MPC (data needs to be constantly split, calculated and reconnected), scaling through hardware becomes difficult.
In FHE, all calculations are performed on encrypted data, there is no need to decrypt the data, and this can be done on a single server. The performance of FHE can be expanded through better hardware, more computing resources, and hardware acceleration.
Currently, the best use cases for FHE in the blockchain space are more in outsourcing general computing than building built-in FHE L1/L2. Here are some interesting use cases that FHE can unlock:
First generation (Crypto native): on-chain DID, casino, betting, voting, gaming, Private DeFi, private tokens, dark pools, 2FA, backups, passwords.
Second generation (modular): "Chainlink for privacy", outsourced private computing, blockchain and End-to-end encryption between contracts, encrypted data availability, verifiable secure data storage.
Third generation (enterprise grade): complex consumer applications, crypto and decentralized LLM, artificial intelligence, wearables Equipment, communications, military, medical, privacy protection payment solutions, Private P2P payment.
Current industry projects based on FHE
The development of fully homomorphic encryption (FHE) has inspired several innovative blockchain projects that leverage this technology to enhance data privacy and security. This section delves into the technical details and unique approaches of noteworthy projects such as Inco, Fhenix, and Zama.
Inco

Inco is pioneering the integration of FHE and blockchain, creating a platform that makes data calculations both safe and secure. Private. Inco uses lattice-based encryption technology to implement its FHE scheme, ensuring that operations on ciphertext (encrypted data) can be performed without exposing the underlying plaintext. The platform supports privacy-preserving smart contracts, allowing encrypted data to be processed directly on the blockchain.
Lattice-Based FHE: Inco utilizes lattice-based encryption Its FHE implementation, noted for its post-quantum security properties, ensures resilience against possible future quantum attacks.
Privacy-protecting smart contract: Inco's smart contract can execute any function on the encrypted input, ensuring that neither the contract nor the node executing the contract can Access clear text data.
Noise management and Bootstrapping: In order to deal with the problem of noise growth during homomorphic operations, Inco implemented an efficient Bootstrapping technology refreshes ciphertext, maintains decryptability, and performs complex calculations at the same time.
Fhenix
< img src="https://img.jinse.cn/7240144_image3.png">
Fhenix focuses on providing powerful infrastructure for privacy protection applications, Leverage FHE to provide end-to-end encryption solutions to protect user data. Fhenix's platform is designed to support a wide range of applications from secure messaging to private financial transactions, ensuring data privacy throughout all computing processes.
Coprocessor: Fhenix It also pioneered the development of a specialized co-processor designed to accelerate FHE calculations. These coprocessors specialize in handling the intensive mathematical operations required by FHE, significantly improving the performance and scalability of privacy-preserving applications.
Zama
Zama is a leader in the FHE field and is famous for the fhEVM solution it developed. This solution allows Ethereum EVM calculations to be performed in a fully homomorphic environment, ensuring execution-level privacy for any L1/L2 project built using the library.
fhEVM solution: Zama’s fhEVM The solution integrates FHE with the Ethereum Virtual Machine to implement encrypted smart contract execution. This allows confidential transactions and computations to be conducted within the Ethereum ecosystem.
Concrete library: Zama's Concrete library is a library for TFHE (a variant of FHE) Rust compiler. This library provides a high-performance implementation of homomorphic encryption schemes, making cryptographic calculations more efficient.
Interoperability: Zama is committed to creating projects that can work seamlessly with existing blockchain infrastructure. Collaborative solutions. This includes support for a variety of cryptographic primitives and protocols, ensuring broad compatibility and ease of integration.

3. FHE’s key role in Crypto and AI Infra and applications
Today, the intersection of cryptography and artificial intelligence is in full swing. While not delving into this intersection, it is worth noting that innovation in new models and datasets will be driven by open source collaboration among multiple players. Beyond computation, what ultimately matters most is the data, which is the most important part of this collaborative pipeline. The usefulness of AI applications and models ultimately depends on the data on which they are trained, whether it is a base model, a fine-tuned model, or an AI intelligent agent. Keeping this data secure and private opens up a vast design space for open source collaboration while allowing data owners to continue to monetize training models or final applications. If this data were public in nature, it would be difficult to monetize (since anyone can access valuable data sets), so it is more likely that this data will be tightly guarded.
In this case, FHE can play a key role. Ideally, it would allow training models without revealing the underlying dataset, which could unlock the monetization of datasets and greatly facilitate open source collaboration among dataset owners.
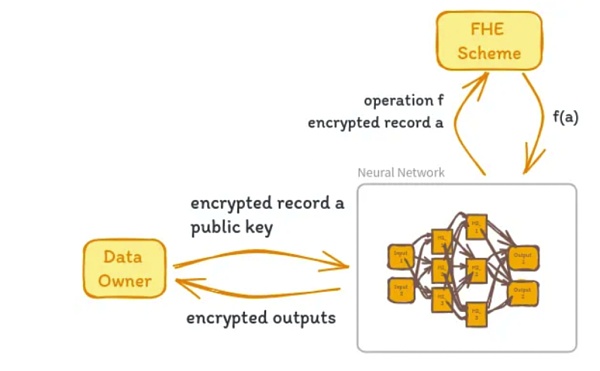
Source: Bagel Network
How FHE enhances privacy-preserving machine learning (PPML )
Data Privacy: By using FHE, sensitive Data such as medical records, financial information, or personal identifiers can be encrypted before being fed into the ML model. This ensures that even if the computing environment is breached, the data remains confidential.
Secure model training: Training ML models usually requires large amounts of data. Using FHE, this data can be encrypted, allowing models to be trained without exposing the original data, critical for industries that handle highly sensitive information and are subject to strict data privacy regulations.
Confidential inference: In addition to training, FHE can also be used for cryptographic inference. This means that once the model is trained, predictions can be made on encrypted input, ensuring user data remains private throughout the inference process.
FHE’s PPML application areas:
FHE problem:
As mentioned before, there is no "uniformity" among FHE schemes. Solutions cannot be combined, and different FHE solutions need to be combined for different types of calculations many times. The process of experimenting with different scenarios for the same calculation is also quite cumbersome. The CHIMERA framework is being developed to allow switching between different FHE schemes such as TFHE, BFV and HEAAN, but is currently far from being usable. This leads to the next issue, which is the lack of benchmarking. Benchmarking is important for developers to adopt this technology. This will help save a lot of developer time. Many existing general purpose hardware are not very suitable due to the computational overhead (encryption, decryption, Bootstrapping, key generation, etc.). Some form of hardware acceleration is required, or specific chips (FPGAs and/or ASICs) may need to be created to enable more mainstream applications of FHE. The problems of these models can be compared to those of the ZK (zero knowledge) industry. As long as a group of smart mathematicians, applied scientists, and engineers are interested in this area, we will continue to be bullish on these two areas: FHE for privacy and ZK for verifiability.

4. What will the future of FHE drive look like?
There will be a FHE solution to rule All? Such discussions are still ongoing in the industry. Although the ideal would be to have a unified solution, the diverse needs of different applications may always require specialized solutions optimized for specific tasks. Is interoperability between scenarios the best solution? Interoperability may indeed be a practical approach, allowing flexibility in handling diverse computing needs while leveraging the strengths of various scenarios.
When will FHE be available? Usability is closely related to progress in reducing computational overhead, improving benchmarking standards, and developing specialized hardware. As these areas progress, FHE will become more accessible and practical.
In summary, FHE provides powerful tools for data privacy protection and secure computing. Although there are currently challenges in interoperability, computational overhead, and hardware support, FHE’s potential for blockchain, privacy-preserving machine learning, and broader Web3 applications cannot be ignored. With the continuous development and innovation of technology, FHE is expected to play a key role in the future privacy protection and secure computing fields.
 JinseFinance
JinseFinance










