Source: Shenzhen Lingshi Technology
Background introduction
On March 5, 2024, we detected an abnormal transaction on the arbiscan chain: https://arbiscan.io/tx/0xe80a16678b5008d5be1484ec6e9e77dc6307632030553405863ffb38c1f94266
After analysis, we found that it was an attack on WOOFi, which caused a total loss of approximately 9 million US dollars.
WOOFi is an all-in-one decentralized application (DApp) built by WOO Network. WOOFI aims to optimize users’ experience with decentralized finance (DeFi) by providing ultra-low slippage, competitive exchange fees, and other useful features.
WOOFi users can redeem popular digital assets and have the opportunity to earn income by staking and providing liquidity to the network. One of the major value propositions created by the WOOFi platform for DeFi users is deep liquidity.
The swap contract in WOOFi was attacked this time. The contract address is: https://arbiscan.io/address/0xeff23b4be1091b53205e35f3afcd9c7182bf3062#code< /strong>
Attack and incident analysis
The attacker used flashLoan from Uniswap and TraderJoe Initial funds for the attack were obtained, totaling 10504796 USDC.e and 2721172 WOO.
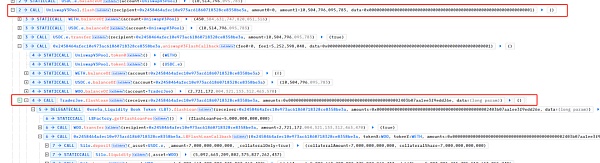
Then , the attacker mortgaged the borrowed USDC.e in Slio Finance (a total of 7,000,000 USDC.e was mortgaged) and lent 5,092,663 WOO.
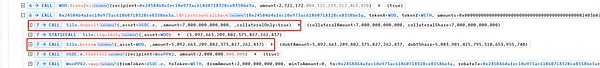
Continue , the attacker used the remaining USDC.e to exchange it for WOO through WOOFi's swap function, thereby increasing the price of WOO.
Pass Three swap operations raised the price of WOO from 56884100 to 60400479, creating conditions for subsequent attacks.
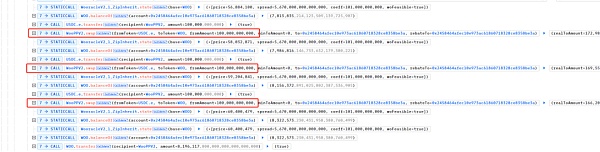
The real attack occurs when the attacker exchanges WOO for USDC.e,

As you can see, after this swap, the price of WOO has changed to 7, which is 0.00000007 USD. Compared with the previous price, it has plummeted by 8.62 million times.
By looking at the contract code, we found that there was a data processing flaw in the WOOFi contract when converting BaseToken into QuoteToken.
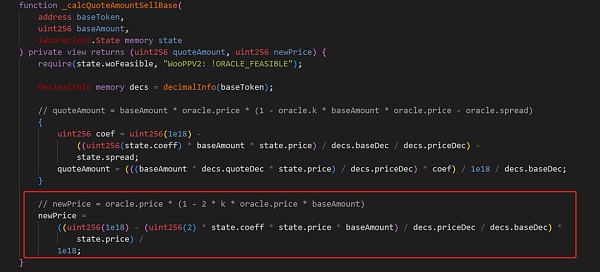
Us See the price calculation method of BaseToken when selling BaseToken to get QuoteToken
newPrice = (1 - 2 * k * oracle.price * baseAmount) * oracle.price< /p>
The attacker can control oracle.price and baseAmount because the k value does not change. An attacker can manipulate oracle.price, which is the price of BaseToken, through multiple swaps, and can manipulate baseAmount. It can be seen from this formula that newPrice must be less than oracle.price. Therefore, the attacker can control the combination of oracle.price and baseAmount to manipulate newPrice to an extremely low level.
Finally, the attacker used a small amount of USDC.e to exchange a large amount of WOO, return the loan principal and cash out.
Two days later, WOOFi official staff communicated with the attacker and stated that they could provide 10% as a Whitehat bonus. However, as of the time of publishing, the attacker has not returned the stolen funds.
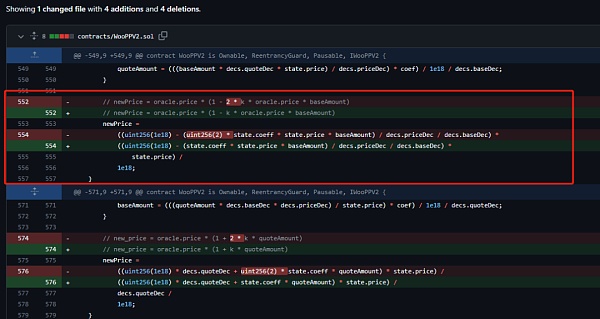
Then , the official fixed this problem. You can see that the official fix is to cancel the 2x coefficient. https://github.com/woonetwork/WooPoolV2/commit/f5fe28acc77cf3801ac379db9bf99bb61b73ba17
Summary
The cause of this vulnerability is a loophole in the calculation of the economic model , the attacker can control the price of buying and selling quantity, causing the token price to shrink significantly, which ultimately leads to the attacker using very little USDC.e to empty out the project's WOO tokens. It is recommended that the project party conduct multi-party verification when designing the economic model and code operation logic, and try to select multiple audit companies for cross-auditing before the contract goes online.
 Kikyo
Kikyo
 Kikyo
Kikyo Coindesk
Coindesk Nulltx
Nulltx Cointelegraph
Cointelegraph Cointelegraph
Cointelegraph Cointelegraph
Cointelegraph 链向资讯
链向资讯 链向资讯
链向资讯 链向资讯
链向资讯 Cointelegraph
Cointelegraph