Author: Dylan Bane, Messari Analyst and Vinayak Kurup, EV3 Ventures Research Director; Translated by: 0xjs@黄金财经
zk-TLS technology (Zero-Knowledge Transport Layer Security) disrupts Web2 by making all user data verifiable and portable across platforms. The technology can be used to break trillions of dollars worth of monopolies while maximizing user privacy through ZKP. This report delves into zk-TLS and explores how this breakthrough technology can revolutionize the Internet by enabling verifiable, portable, and private user data.
By allowing third parties to access user data without relying on Web2 platforms, zk-TLS is expected to break centralized monopolies, empower users, and unlock new applications in entertainment, DeFi, AI, and more.
zk-TLS has the potential to promote Internet sovereignty and composability, and it is expected to transform industries by breaking down walled gardens and fostering decentralized ecosystems.
The first batch of zk-TLS use cases will enter PMF in 2025, realizing on-chain identity scoring, vampire attacks on platforms such as Uber, etc.
Zk-TLS project overview:

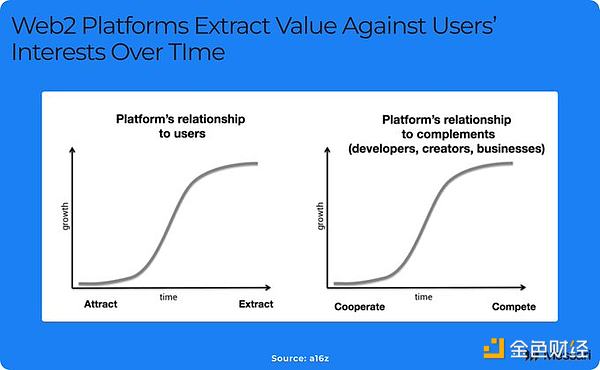
Initially, Web2 was built on the spirit of the open web. Companies quickly realized that profits came from isolated data and built walls to keep users out. Even Twitter shut down its API a few months before its IPO. Web2 has become value-grabbing, depriving users of data sovereignty.
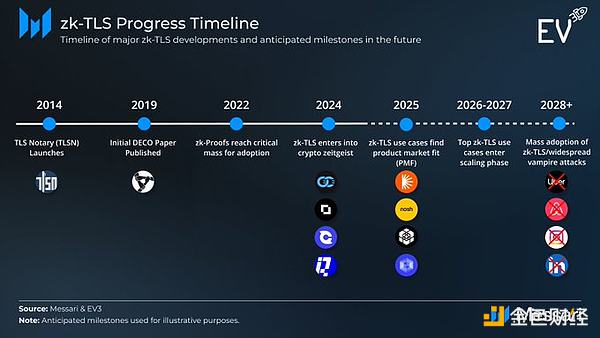
zk-TLS Timeline:
In 2014, Ethereum researchers realized that they could verify previously isolated data by focusing on the network layer.Based on this, researchers at Cornell University released DECO in 2019, eliminating the reliance on server cooperation and introducing ZKP to protect data privacy. Thus, zk-TLS was born.
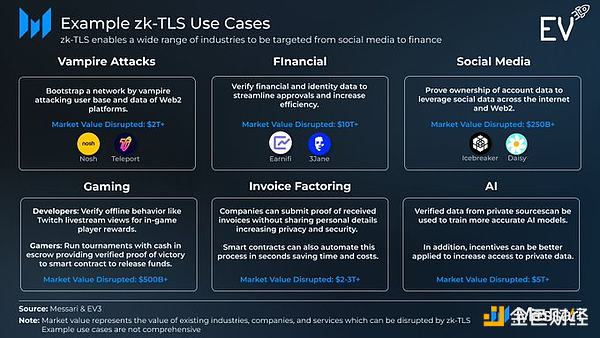
zk-TLS use casesrange widely:
From vampire attacks on Web2 platforms like DoorDash, to enabling on-chain credit scoring, to providing verifiable private data to train LLMs. Any user data on the internet can be leveraged for new use cases via zk-TLS.
zk-TLS Architecture:
When you access your bank account, your computer communicates with the bank’s servers. zk-TLS verifies this process by having validators observe and verify that the data sent is correct. It can do this in 3 ways: Multi-party computation (MPC), proxy, or just using TEE.
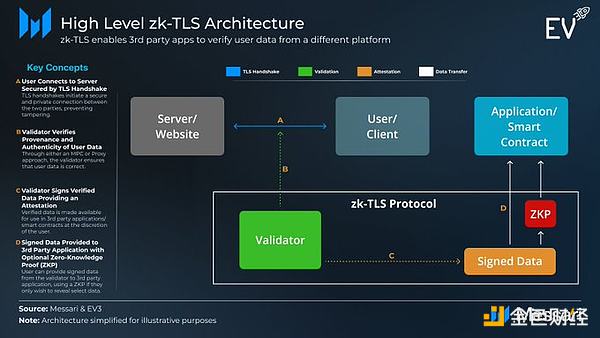
For example, Opacity uses MPC to solve this problem. Validators ensure that logins and information access are handled correctly. Validators are randomly selected, minimizing the possibility of collusion.
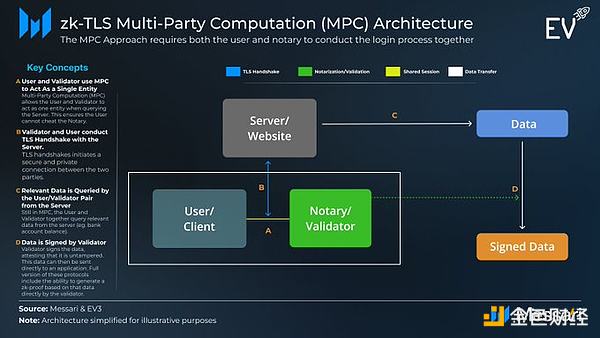
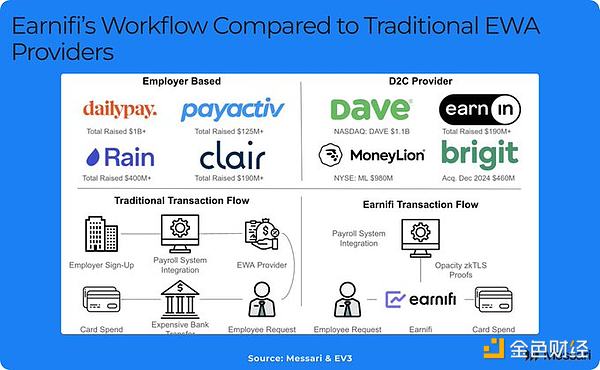
Take Earnifi as an example, it uses Opacity’s MPC model to ensure that people work the hours they claim. zk-TLS enables them to underwrite loans more efficiently than earned-wage-access (EWA) and payday loan companies that charge high fees. The entire industry will be disrupted.
While we expect the first use case to find PMF in 2025,zk-TLS faces many challenges.
For example: scalability issues, servers may detect a large number of proxy sessions; strong opposition from Web2; and addressing the friction of being unfamiliar with ZKP.
 Weatherly
Weatherly












