Background
On January 16, 2024, a blogger in Chinese Social media broke the news that the Myanmar Allied Forces were suspected of forcibly charging high amounts of cryptocurrency from e-fraud industry practitioners stranded in Myanmar, and displayed the cryptocurrency addresses they claimed were used to collect payments. This revelation has now formed a relatively widespread network. Spread.
This article is jointly conducted by Bitrace & MistTrack to analyze the crypto funds of disclosed addresses, including: address fund collection and payment rules, address fund source risks, associated address activities, etc. , aiming to disclose relevant analysis content.
Address behavior analysis

(https://mp. weixin.qq.com/s/WDWM22vw68-NsVr0_1jHfA)
The picture above shows the information in the breaking article. Based on this, the researchers have disclosed The payment address TKFsCN conducted a USDT exchange rate analysis and tried to deduce the settlement unit behind it through the USDT payment of certain specific amounts.
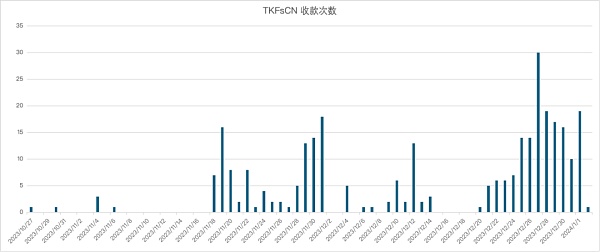
Historical transaction records of the payment address show that the USDT single transaction received by this address contains a large number of non-intact tens and hundreds, such as 71417, 42857 and other numbers. This is common when transactions use non-USD as the settlement unit. situation. After trying to calculate the exchange rate of major legal currencies against USDT, the researchers found that these transactions were suspected to be settled at an exchange rate of 1 USD: 7-7.2 RMB, and the amount of a single fund transfer ranged from RMB 500,000 to 600,000. There is clustering phenomenon in several intervals of 1 million and 1.5 million.
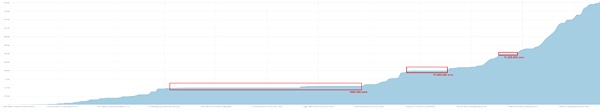
After filtering out transactions with an amount of 100 USDT and below, according to statistics, among the total 307 USDT transfer amounts in TKFsCN, 193 were transfers of amounts based on the RMB-USD exchange rate, accounting for 62.86% of the total. The transaction amount accounted for 45.29% of the total.
This shows that more than half of the transactions collected by this address are settled in RMB, and transfers with a conversion amount of 500,000 dominate. The party paying USDT should be Chinese.
Funding source analysis
As mentioned in the original article, " After occupying the old street, they also arrested Chinese people everywhere (author's note: practitioners in the electronic fraud industry). If they are willing to pay to protect themselves, those who pay can be sent away, and those who do not pay will be sent to China." If true, TKFsCN's transaction There should be a large number of new counterparties in the transaction, and part of the funds come from gray and black assets, money laundering, fraud and other related addresses.

Data shows that between October 22, 2023 and January 2, 2024, TKFsCN received a total of USDT transfers from 182 direct counterparties, of which 117 addresses had consecutive small amounts + large amounts. Two transfer characteristics. This is a typical transfer test behavior. The payer does not choose to complete the transfer in one go in order to confirm that the address is correct. This shows that at least 62.29% of the counterparties may be making transfers for the first time and are not regular trading partners of TKFsCN.
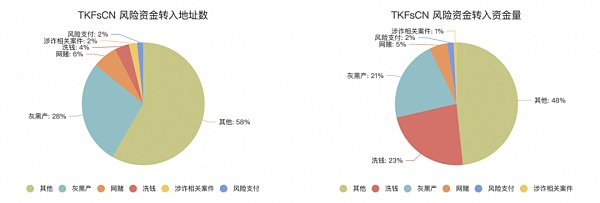
A more in-depth audit of the address risk funds of TKFsCN showed that the counterparty transferring funds to this address is closely related to black and gray industry, online gambling, fraud, money laundering, risk payment and other activities. Among the 182 direct transfer parties, up to 42% were addresses associated with risk activities, transferring USDT worth $33,523,148 to TKFsCN.
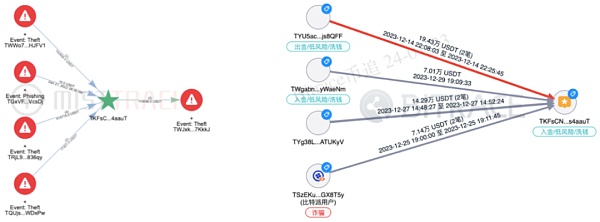
(Pictures from MistTrack and BitracePro)
It is worth noting that in Among the addresses associated with this batch of risky activities, investigators also found 7 addresses that were clearly related to known criminal cases, including two money laundering cases, one fraud case, one online gambling case, and one phone fraud case, and the suspect’s geographical location The locations are all in northern Myanmar or Cambodia.
This shows that the counterparty address that initiated payments to TKFsCN is not only involved in a large number of risky encryption activities, but is also closely related to criminals in Southeast Asia.
Another strange thing is that investigators also found a money laundering address related to the telecom fraud case in the transfer address, indicating that some of the funds in the transfer address There are also certain doubts in the upward traceability analysis. This doubtful point will be non-sensitively expanded in the "Related Address Analysis" section below.
Related address analysis
Aggregation based on the above TKFsCN address Class analysis found that this address is suspected of having a subject clustering relationship with nearly a hundred addresses. Some of the addresses not only have similar fund collection and payment activities to TKFsCN, but also reveal more information about the payee, with the payee TKKj8G For example:
TKKj8G directly received 6 transactions from TKFsCN totaling more than 4.6 million USDT The funds are one of the collection addresses in the payee’s subsequent fund link;
TKKj8G is one of the core collection addresses. Among the 60 collections with an amount exceeding 100 USDT, up to 50 collections have small-amount testing behaviors similar to TKFsCN;
TKKj8G became active on August 18, 2023, much earlier than other addresses, and there were transactions with Huiwang Guarantee during this period - from The Huiwang guarantee address received 160,000 USDT, and the behavioral analysis showed that the merchant guaranteed by Huiwang got back the deposit from Huiwang guarantee.
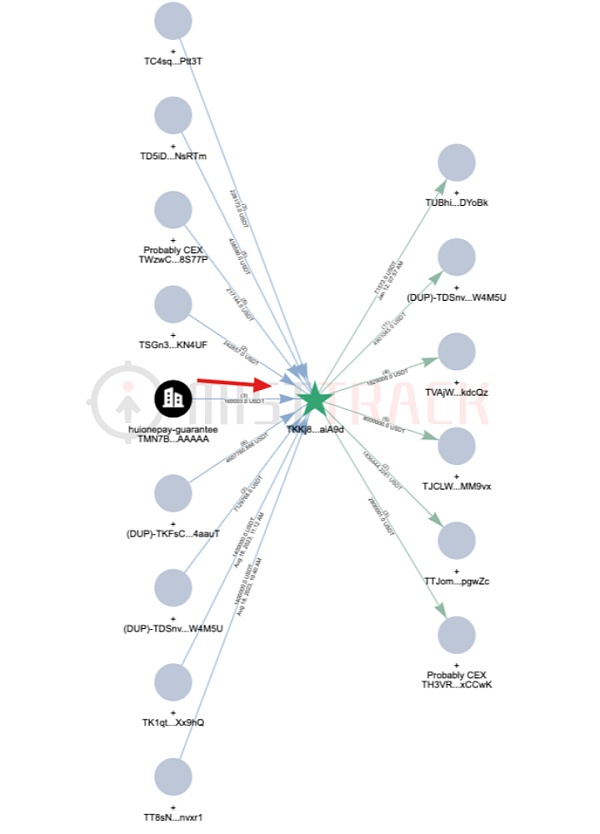
This indicates that the "Ministry of Finance address" mentioned in the original article may not exist. The address set including TKFsCN and TKKj8G should belong to a certain address in Myanmar. Digital currency acceptors in North Korea or Cambodia collect these payments on their behalf for some reason.
Abnormal transactions
To sum up, it is not difficult for investigators to outline a typical payer portrait - in People engaged in illegal work in Southeast Asia had to pay USDT worth 500,000 yuan to a certain collection address for some reason. Since this was the first transaction, a small test was conducted before transferring a large amount to prevent address errors. The cryptocurrency used for payment either comes from its original illegal gains or is purchased from other illegal entities.
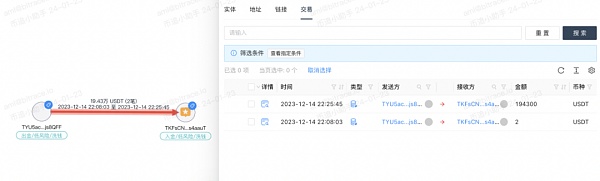
But not all payers are like this. Investigators also found some addresses that do not meet or do not fully meet such characteristics. Take TYU5acSGRwsYJfBhdpQc3broSpfsjs8QFF as an example. The address is one of the 7 addresses directly involved in the case mentioned above. The other 6 addresses transferred encryption worth RMB 500,000, RMB 500,000, RMB 1 million, RMB 1 million, RMB 2.7 million (1.50 + 1.2 million), and RMB 550,000 to TKFsCN respectively. currency, but the transfer amount of TYU5ac is converted to 1.36 million yuan at the same exchange rate. Although it is an integer, this special amount is still very different from other addresses.
Investigators have no way of knowing the reason. Considering that there is small-amount testing behavior at this address, a reasonable guess is that the transaction behind this address represents 3 A combined transfer worth RMB 500,000 and received a 10% discount.
Summary
This article analyzes the rules of fund collection and payment from public addresses, address fund source risks, and associated address activities. In-depth analysis and disclosure of relevant analysis content. The main conclusions are as follows:
1. More than half of the transactions charged by the target address of this analysis are settled in RMB, and the conversion amount is 50, 100 , the transfer of 1.5 million occupies a major position;
2. The counterparty address of the transfer to the analysis target address is related to black and gray industries, online gambling, and fraud , money laundering, risk payment and other activities are closely related;
3. The target address and its associated addresses have already had risky business activities before intensive collection of such funds. After performing cluster analysis on the analyzed address, it was found that the cluster was suspected to be a merchant guaranteed by Huiwang;
4. Initiate an attack to the analyzed target address The counterparty address of the payment is closely related to criminals in northern Myanmar or Cambodia.
To sum up, part of the content revealed in the article "Allied Forces Virtual Currency Account Exposed, Extorting Hundreds of Hundreds of Millions of Virtual Currency from the North Country" is inconsistent with the content on the chain Consistent with the facts, there are indeed a large number of Chinese electronic fraud industry practitioners located in northern Myanmar or Cambodia who collectively transfer USDT assets with an integer amount of RMB to a certain address set. However, this group of addresses may not be the so-called "Ministry of Finance Address", but a local The address of the digital currency acceptor is different from that stated in the original article.
About us
This survey was conducted by MistTrack Completed with Bitrace investigators.
MistTrack (https://misttrack.io/) is an anti-money laundering tracking system developed by the blockchain security company SlowMist, focusing on Used to combat cryptocurrency money laundering and open to everyone. The MistTrack anti-money laundering tracking system has accumulated more than 200 million address tags and can identify various wallet addresses on the world's mainstream trading platforms, including more than 1,000 address entities, more than 400,000 threat intelligence data and more than 90 million risk addresses.
Bitrace (https://www.bitrace.io/) is a blockchain data analysis company that provides services to Web3 enterprises, financial institutions, and regulatory and law enforcement agencies. Provide leading compliance and regulatory tool products and service support such as cryptocurrency data analysis, risk management, and law enforcement collaboration.
Disclaimer
The content of this article is based on the anti-money laundering tracking system MistTrack and the data support of the cryptocurrency tracking and analysis platform BitracePro are designed to analyze public addresses on the network and disclose the analysis results. However, due to the characteristics of the blockchain, we cannot guarantee the absolute accuracy of all data here. nor shall we be held responsible for any errors, omissions, or losses caused by the use of the contents of this article. At the same time, this article does not constitute the basis for any position or other analysis.
 JinseFinance
JinseFinance













