Last week, we released the " 2023 Blockchain Security and Anti-Money Laundering Annual Report". Next, we will divide the report into four articles to interpret and analyze the report The key contents in it help readers gain a more comprehensive and in-depth understanding of the key security challenges and opportunities in the current blockchain ecosystem.
This article mainly focuses on the ecological security situation of the blockchain.
Blockchain security situation
With the impact of macro and geopolitical tensions on the global economy and the residual traces of various thunderstorm events in 2022, the blockchain industry is also suffering from incredible turmoil. In the past year, many cryptocurrency-friendly banks have collapsed one after another, coupled with a series of security attacks caused by North Korean hackers Lazarus Group and multiple phishing gangs Wallet Draines, further highlighting the lack of user security awareness and inadequate regulatory policies. Perfect question.
According to statistics from SlowMist Hacked, there were a total of 464 security incidents in 2023, with losses as high as US$2.486 billion. Compared with 2022, there were a total of 303 security incidents and losses of approximately US$3.777 billion. In 2023, losses decreased by 34.2% year-on-year, and the number of security incidents increased by approximately 53.13% year-on-year. Although losses have declined, the number of security incidents is on the rise.
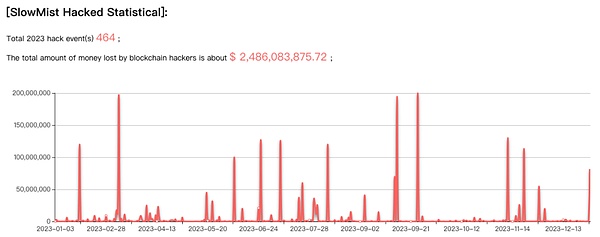
Next, we will interpret the blockchain security situation in 2023 from three aspects: project track, ecology, and incident causes.
Project Track
From the perspective of the project track , DeFi is the field where the most security incidents occur and the greatest losses occur. The development of DeFi not only brings new innovations and opportunities, but also leads to more potential risks and attack surfaces. Because DeFi projects have a certain capital scale and user base, they can easily become potential attack targets for hackers.
There will be a total of 282 DeFi security incidents in 2023, accounting for 60.77% of the total number of incidents, with losses as high as US$773 million. Compared with 2022 (a total of 183 incidents, losses of approximately US$20.75 billion), although the losses from DeFi security incidents decreased by 62.73% in 2023, the number of incidents increased by 54.64%, highlighting that the DeFi field still faces severe challenges in preventing and handling security issues.
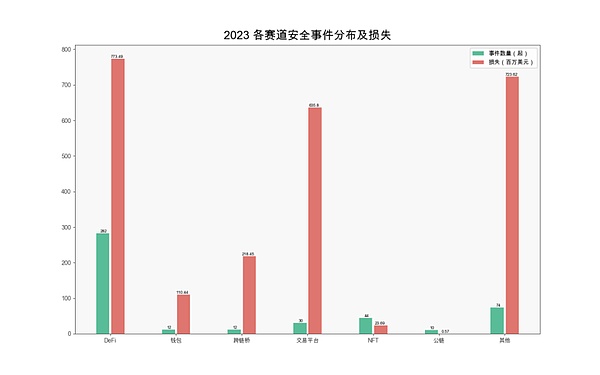
(Distribution and losses of safety incidents at each track in 2023)
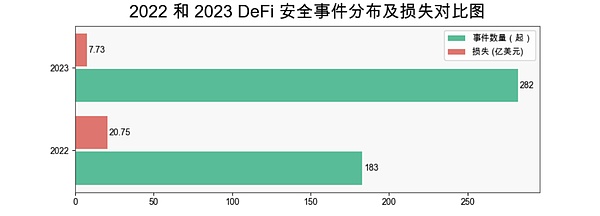
(2022 and 2023 DeFi security incident distribution and loss comparison chart)
< strong>Ecology
From an ecological perspective, since Ethereum is the preferred platform for many smart contracts and decentralized applications, it has become a target for hacker attacks. The main target suffered the largest losses, amounting to $487 million. Followed by Polygon, as a Layer 2 solution extended on Ethereum, it also faces considerable security threats. The losses caused by 6 security incidents in this ecosystem amounted to US$123 million, among which the non-custodial lending platform BonqDAO and the crypto base The facility platform AllianceBlock was hacked due to a smart contract vulnerability in BonqDAO, resulting in a loss of approximately US$120 million.
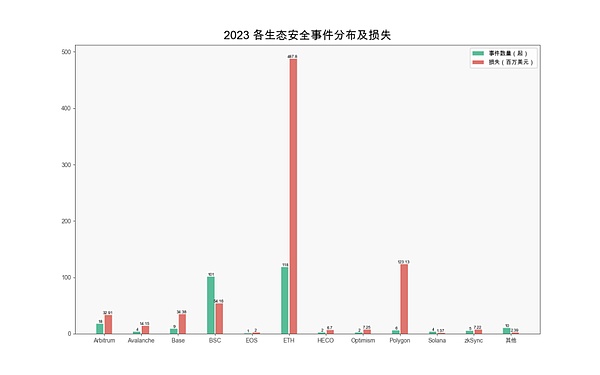
(Distribution and losses of various ecological security incidents in 2023)
Cause of the incident
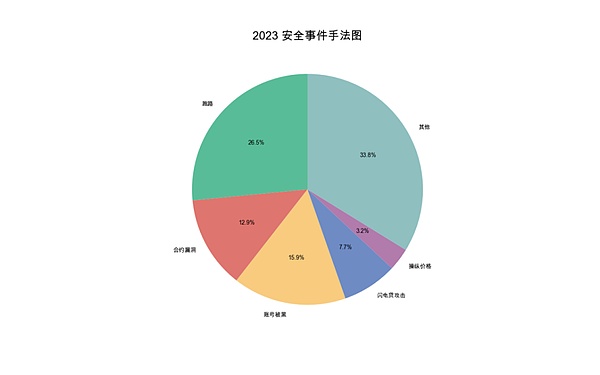
(2023 Security Incident Methods Map)< /p>
In 2023, there will be a total of 117 safety incidents caused by project parties running away, resulting in losses of approximately 8,300 Ten thousand U.S. dollars. Among them, Base Ecosystem suffered the highest loss, reaching US$32.5 million. Followed by BSC Ecology, reaching US$23.05 million.
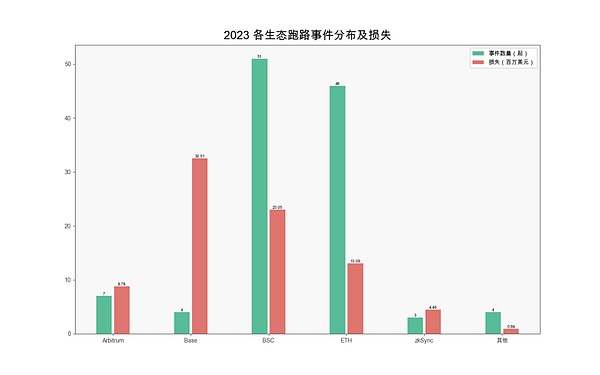
(Distribution and losses of various ecological escape events in 2023)
It is usually difficult for investors to recover losses after the project party runs away. Running away is a way for the project party to take the initiative to do evil. For example, the project party initiates initial liquidity, pushes up the price and then withdraws the liquidity; for example, the project party leaves money in the project. Downloaded the backdoor code and so on.
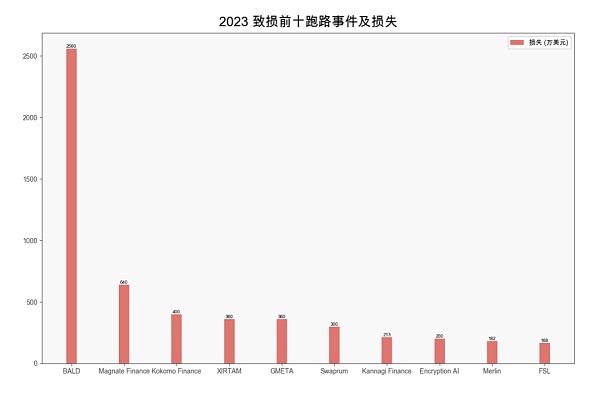
(2023 top ten runaway events and losses)
In 2023, there were 57 attacks due to contract vulnerabilities, resulting in losses of approximately US$75.82 million. However, the use of contract vulnerabilities is often accompanied by flash loan attacks, price manipulation and other techniques. In 2023, there were 34 flash loan attacks launched by hackers, causing losses of approximately US$225 million; there were 14 price manipulation attacks, causing losses of approximately US$140 million.
The occurrence of contract vulnerabilities is usually related to insufficient review of contract code, and contracts should be continuously audited. Moreover, the development team should adopt the best security development practices. The SlowMist security team has opened a smart contract security audit skill tree on Github (https://github.com/slowmist/SlowMist-Learning-Roadmap-for-Becoming-a -Smart-Contract-Auditor); Web3 Project Security Practice Requirements (https://github.com/slowmist/Web3-Project-Security-Practice-Requirements) and Solana Smart Contract Security Best Practices (https://github .com/slowmist/solana-smart-contract-security-best-practices), interested friends are welcome to read it on Github.
2023 There have been 70 security incidents in which various subject accounts have been hacked. With the rapid development of Web3, attacks against users and project parties have emerged in an endless stream, especially attacks against media platforms such as Discord and Twitter.
Hackers usually pretend to be administrators and publish phishing links after obtaining administrator or account rights, and then induce users to Authorization to transfer assets. It is recommended that project parties adopt security operations such as two-factor authentication and setting strong passwords to protect accounts, and be wary of various traditional network attacks and social engineering attacks.
According to slow fog According to statistics from the Blockchain Hacked Event Archive (SlowMist Hacked), 11 scams occurred in the blockchain industry in 2023. Among them, the Hong Kong cryptocurrency scam JPEX incident in 2023 attracted investment with "low risk and high return". As of December 18, 2023, the Hong Kong police had arrested a total of 66 people and received reports from 2,623 victims, involving approximately HK$1.6 billion. According to relevant reports, the JPEX thunderstorm may become the largest financial fraud case in Hong Kong history.
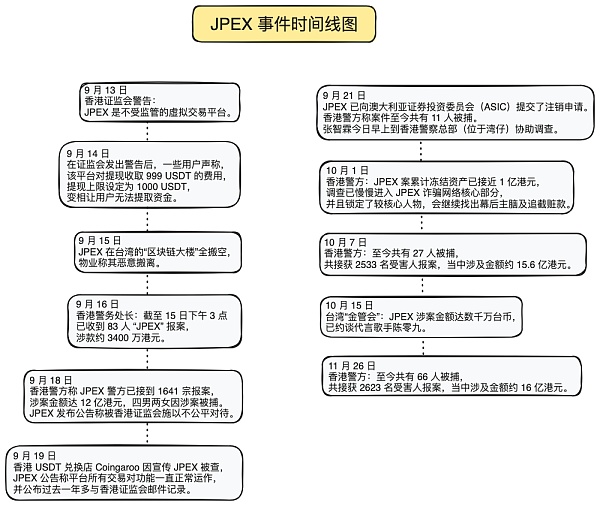
Suggestions
For project parties:
Should continue to monitor smart contracts Conduct audits to ensure the security and stability of the code and prevent contract vulnerabilities;
In Multi-level defense measures are introduced into the contract, including permission control, security checks and insurance mechanisms, to minimize the risk of other attacks;
Establish an emergency response mechanism to respond promptly when an attack occurs and control the scope of losses;
Adopt two-factor authentication, set strong passwords and other security operations to reduce the risk of account hacking.
For individual users,obey the following safety rules and Principle, most risks can be avoided:
Two safety rules:
< p> Zero trust. Simply put, be skeptical, and always be skeptical.
Continuous verification. If you want to believe, you must have the ability to verify your doubts and develop this ability into a habit.
Safety principle:
For knowledge on the Internet, refer to at least two sources of information for everything , support each other, and always remain skeptical;
Do a good job of isolation, that is, do not put the eggs together In the basket;
For wallets that contain important assets, do not update them easily, as long as they are enough OK;
What you see is what you sign. That is to say, the content you see is what you expected to sign. When your signature is sent, the result should be what you expected, and it will never be a slap in the face afterwards;
Pay attention to system security updates and act immediately when security updates are available;
Don't mess with the program.
It is recommended to read and master the "Blockchain Dark Forest Self-Rescue Manual" (https://github.com/slowmist/Blockchain- dark-forest-selfguard-handbook/blob/main/README_CN.md).
Full report download:
https://www.slowmist.com/report/2023-Blockchain-Security-and-AML-Annual-Report(CN).pdf
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance Brian
Brian Brian
Brian Bitcoinist
Bitcoinist TheBlock
TheBlock Beincrypto
Beincrypto Others
Others Cointelegraph
Cointelegraph Ftftx
Ftftx 链向资讯
链向资讯