By: Liz, Slow Mist
Background
Recently, there has been a scammer (CYBER RESCUE) pushing a safety reminder from Slow Mist founder Cos The article is phishing victims under the guise of "helping to recover/restore stolen funds". In response to this situation, the SlowMist security team reverse-phished the scammer and disclosed his deception process. We hope that users will be more vigilant and avoid being fooled.
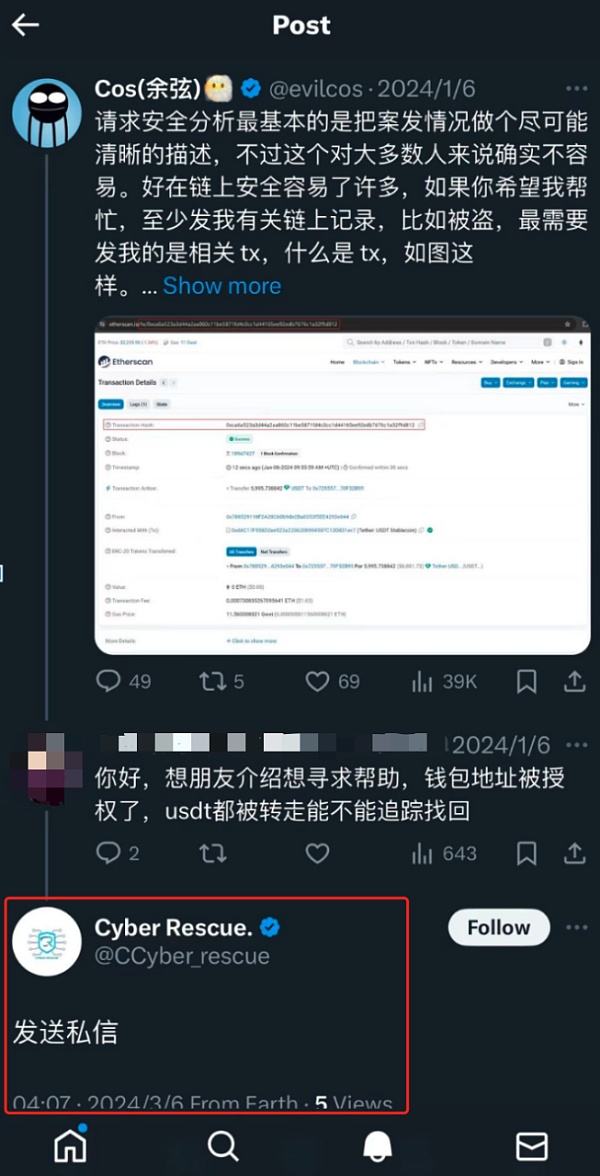
Fraud process
As a victim, we contacted CYBER RESCUE, which claims to be able to recover 100% of stolen funds. The following is the scammer’s deception process:
< img src="https://img.jinse.cn/7190656_image3.png">
1. CYBER RESCUE first asked the victim when it was stolen, the wallet used and the reason for the theft, and then said it could be 100 % Recover stolen funds by processing transactions through USDT and redirecting stolen funds to the victim's wallet under the BNB smart chain network. Victims are required to download MathWallet, which the scammer explains is to guide the victim through user settings for transfers and redirect funds to the victim's wallet.
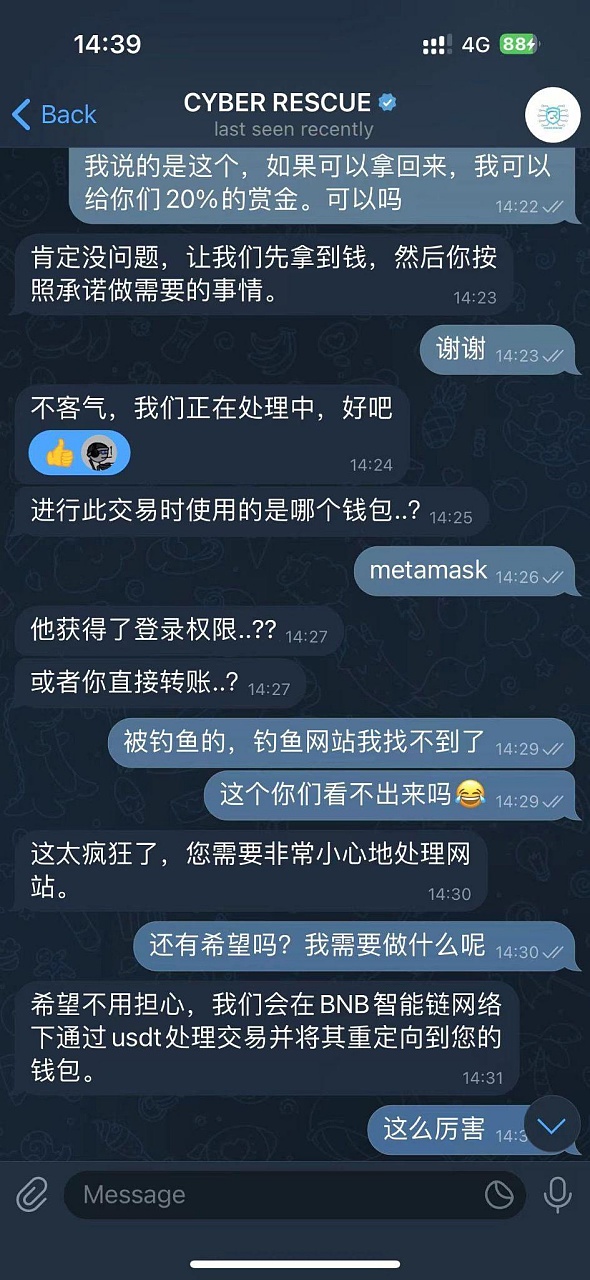
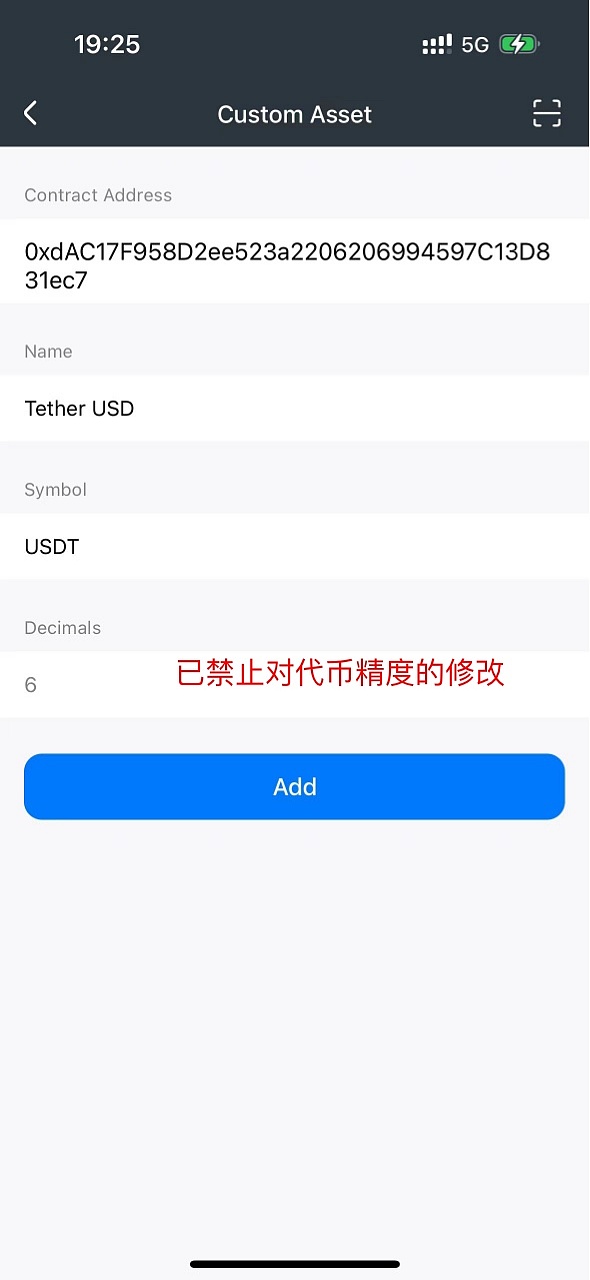
2. The scammer then asks the victim to click "Add Custom Assets" on the homepage , guide the user to enter USDT contract 0x55d398326f99059ff775485246999027b3197955 (the contract address is correct). At this time, MathWallet will automatically recognize that the token precision is 18.
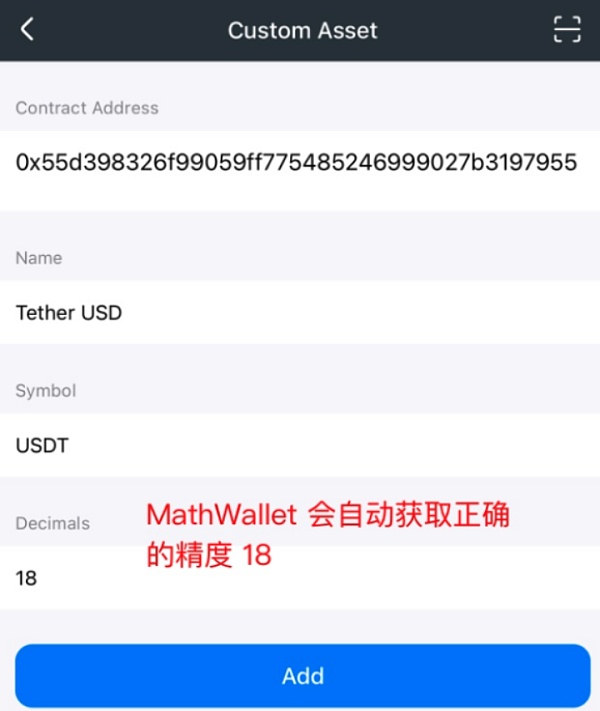
At this step, the scammer emphasized: When pasting the contract address, Decimals must be Changed from 18 to 0. The victim thus added a USDT token with the correct contract but wrong precision. Here is an explanation of what Decimals (decimal digits) are. In tokens, Decimals represents the number of the smallest divisible units of the token, which determines the accuracy of the token in transactions and calculations. The higher the value of Decimals, the more accurate the token.
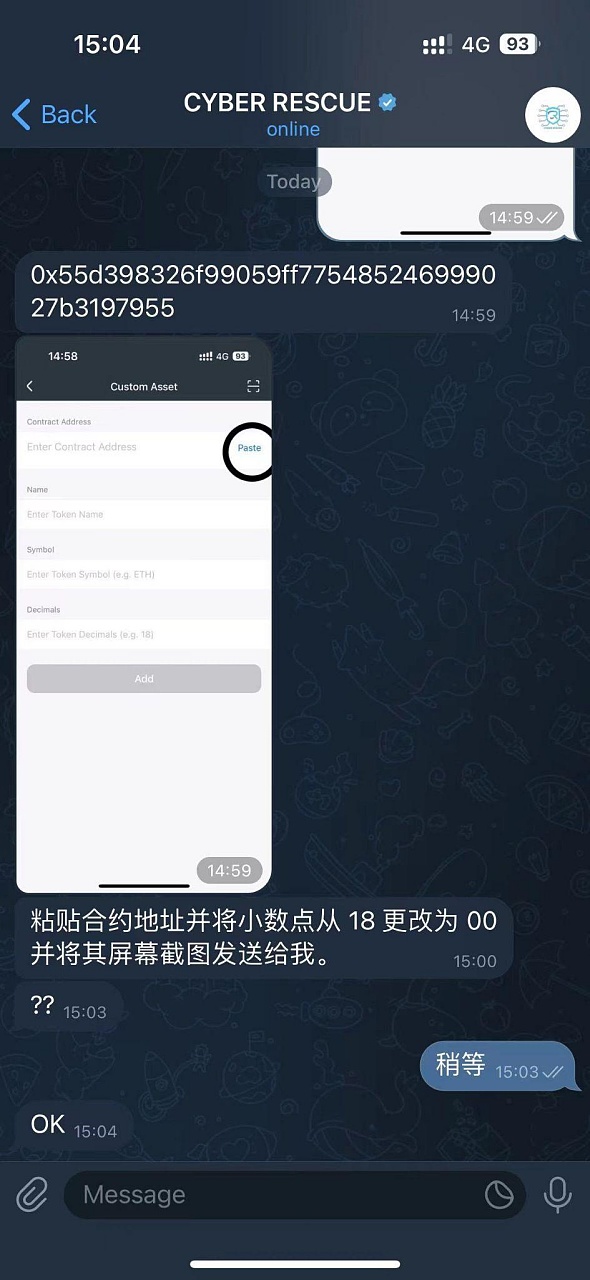

After the victim complied, the scammer said that was enough. He wanted to freeze the stolen funds and return them to the victim's account. Now he needs the victim to provide a MetaMask wallet. ). Because the translation software translated the MetaMask wallet into a metamask wallet, the victim was completely confused and the scammer was also shocked. You don't have a MetaMask wallet?
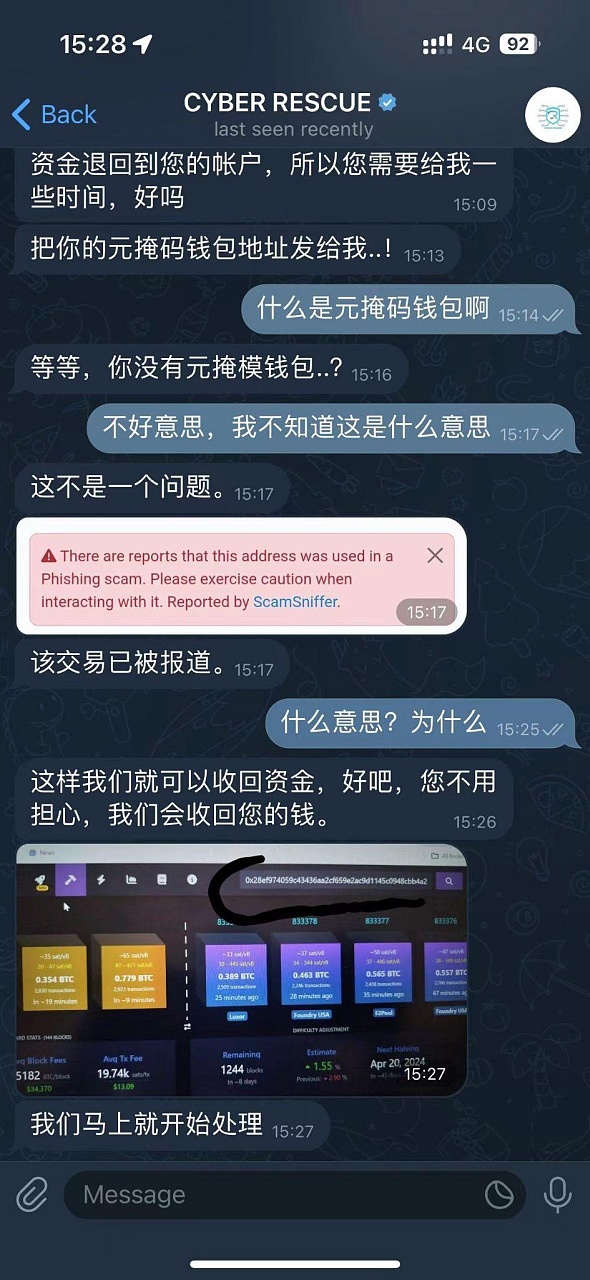
3. At this point, the scammer began his magic to "recover" the stolen funds. Operation:
After checking the stolen transaction we provided him, the scammer stated that he could only recover $89,589 of the stolen funds. The reason he gave was that the remaining funds had already entered the foreign exchange market and been converted into local currency.
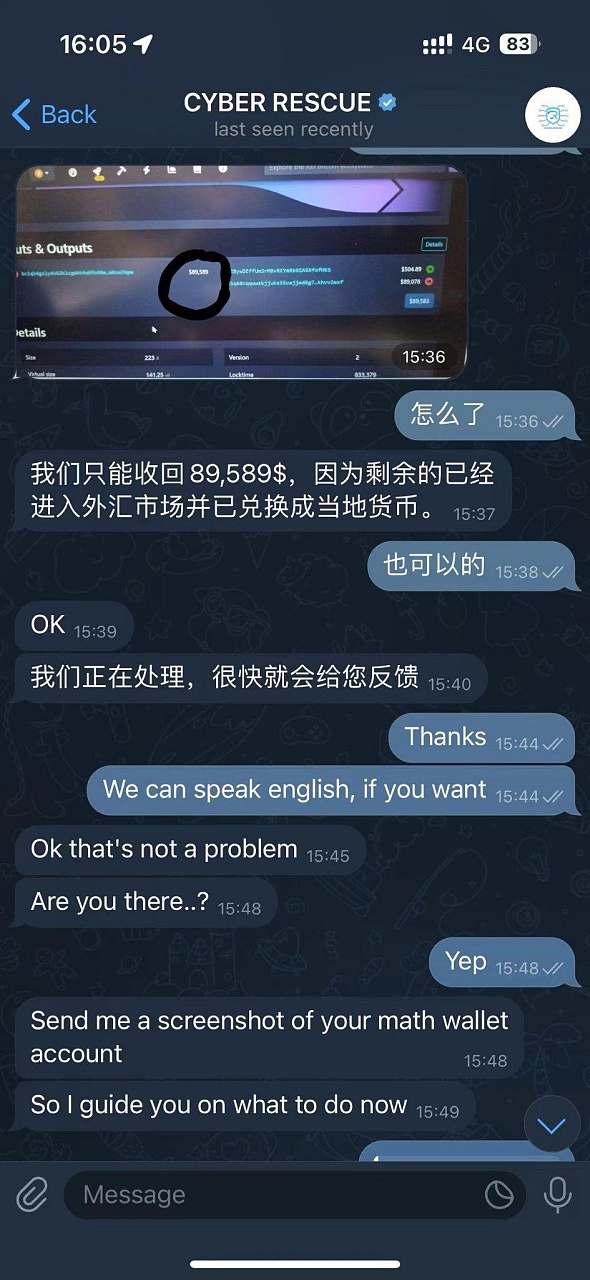
The scammer then asks the victim to send a screenshot of the MathWallet Account and reminds the victim: Please stay online, success or failure depends on this. This sentence is a bit confusing. The victim has already lost his money. The scammer’s urging at this time will make the victim think about seizing this opportunity to get the money back. Who will he realize that he is about to fall into another trap? .
The scammer asks the victim to click on the Export Private Key in the Manage Wallet to guide the victim Copy the private key to him. The scammer's explanation for needing the private key is to connect the app to redirect transactions to the victim's wallet. If the scammer’s previous operations didn’t make you suspicious, but now he wants your private key, run!
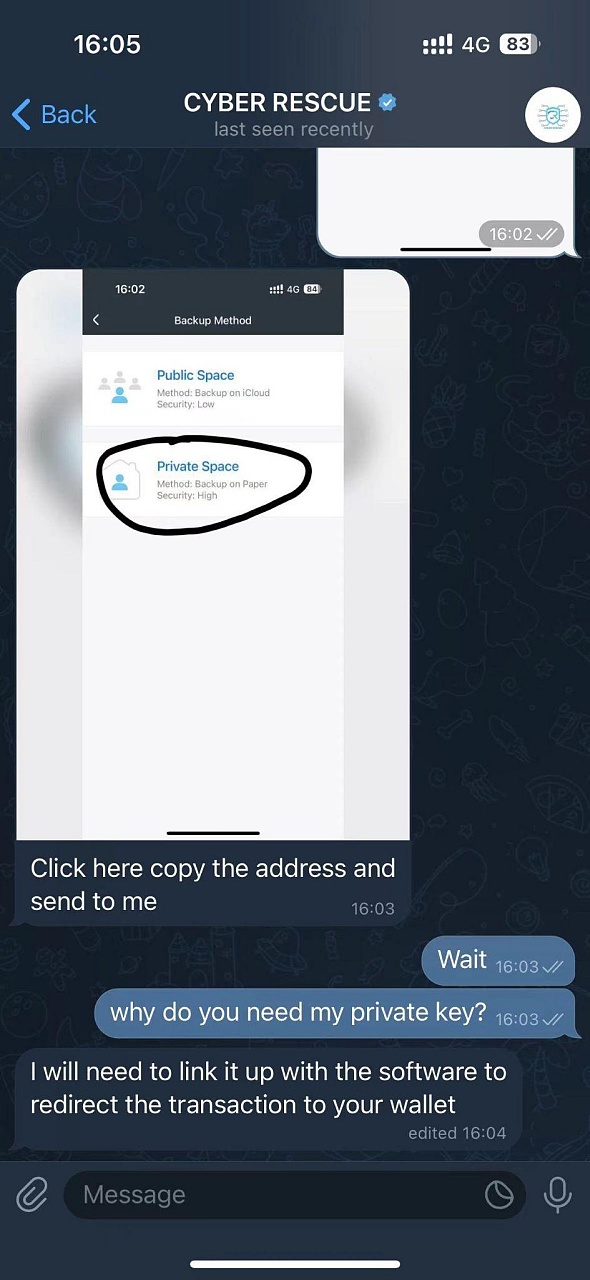
The victim sent the private key to the scammer. Soon, the scammer said that the operation was completed and he could check his wallet. The victim checked the wallet and found that the amount of USDT had indeed changed to 89589, which the scammer had just guaranteed to recover. What was going on?
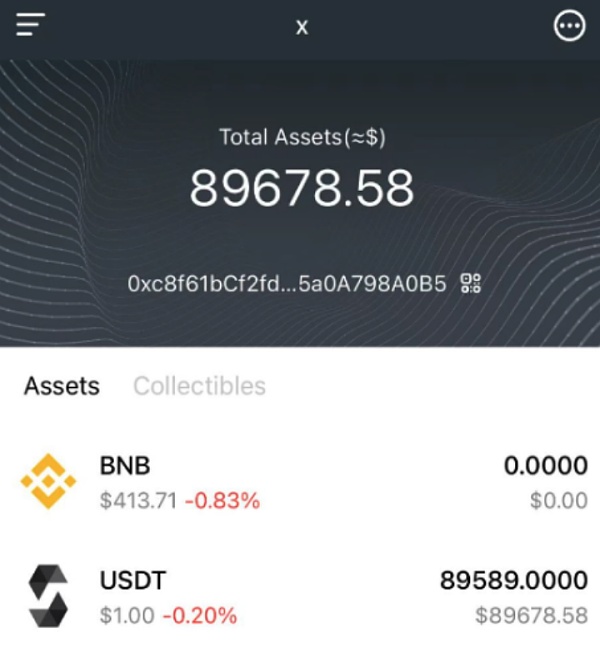
Check on the block explorer and found that the scammer actually transferred money to the victim The amount is 0.000000000000089589 USDT. This is because the victim was previously induced by the scammer to manually change the Decimals of the custom token in the wallet from 18 to 0. Therefore, although the scammer transferred the amount to the victim of 0.000000000000089589 USDT, the victim's wallet will show that 89589 USDT was received. .
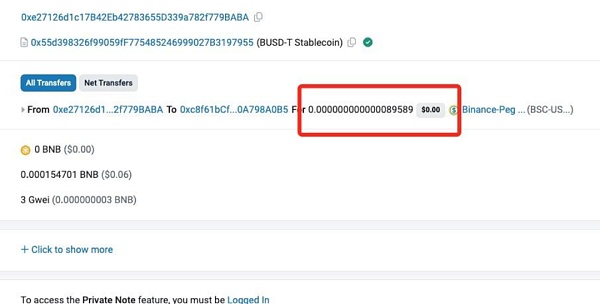
(https://bscscan.com/0x009073dc1EC68987406FDB11 BF7B112A6C380EC3839D6A8E5)
The scammer has defrauded the private key, how will he profit next? He told victims that they needed to have sufficient BNB available balance to execute transactions to other accounts, and that this available balance should be 10% of the initial balance in the BNB smart chain network. If the victim believes it and transfers BNB worth about $8968 to the wallet as required, it will be stolen by the scammer.

We used a block explorer to check the scammer’s address (0xe27126d1c17B42Eb42783655D339a782f779BABA) and found that The address frequently transfers small amounts to other addresses, indicating that the scammer continues to use this deception to commit crimes.
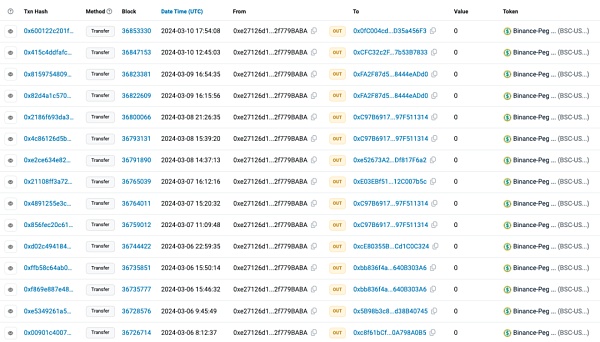
(https://bscscan.com/txs?a=0xe27126d1c17B42Eb42783655D339a782f779BABA&p =1)
Use MistTrack (https://misttrack.io/) to query the address. You can see that the source of the handling fee for this address is Binance. MistTrack has blocked the relevant addresses and will continue to monitor fund changes.

MathWallet Update
After receiving feedback on the case, MathWallet immediately fixed and released a new version, prohibiting users from manually modifying the accuracy. Users who have already installed MathWallet please upgrade in the App Store or Google Play.
Summary
area There are endless scams in the dark forest of blockchain. The scammer in this article even pretended to be an on-chain tracking expert to fish for the stolen victim. During the deception process, it can be said that he taught the victim step by step how to give away the private key. The SlowMist security team hereby reminds users to stay vigilant. No matter what identity the other party approaches you, be sure not to give out your private key to prevent it from being stolen. If your cryptocurrency is unfortunately stolen, we will provide free community assistance services for case evaluation. You only need to submit a form according to the classification guidelines (funds stolen/fraud/extortion). At the same time, the hacker address you submitted will also be synchronized to the InMist threat intelligence cooperation network for risk control. (Note: Submit the Chinese form to https://aml.slowmist.com/cn/recovery-funds.html, and submit the English form to https://aml.slowmist.com/recovery-funds.html)
< p>
 Huang Bo
Huang Bo






















