With the rapid development of blockchain, security incidents such as theft, phishing, and fraud against users are increasing, and the attack methods are diverse. SlowMist receives a large number of victims' help messages every day, hoping that we can provide assistance in fund tracking and rescue, including victims who have lost tens of millions of US dollars. Based on this, this series counts and analyzes the stolen forms received each quarter, aiming to analyze common or rare malicious methods with real cases after desensitization, and help users learn how to better protect their assets.
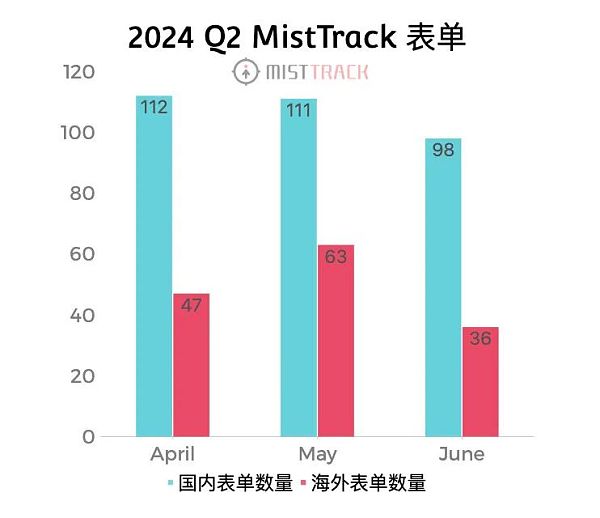
According to statistics, MistTrack Team received a total of 467 stolen forms in Q2 2024, including 146 overseas forms and 321 domestic forms. We provided free evaluation community services for these forms (Ps. The content of this article only applies to cases submitted from forms, and does not include cases contacted through email or other channels)
Among them, MistTrack Team assisted 18 stolen customers in freezing approximately US$20.6641 million in funds on 13 platforms.
Top 3 reasons for theft
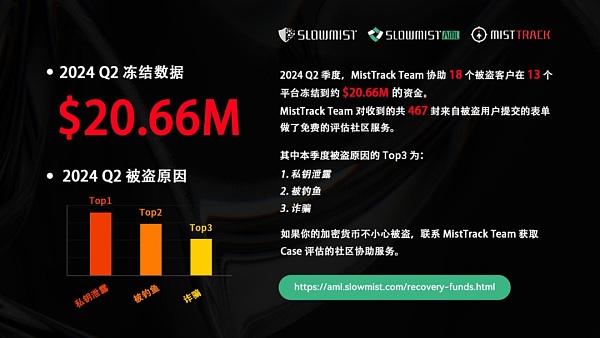
The most common malicious methods of Q2 Form in 2024 are as follows:
Private key leakage
According to statistics from Q2 Form, many users store private keys/mnemonics in cloud disks such as Google Docs, Tencent Docs, Baidu Cloud Disk, and Graphite Docs. Some users send private keys/mnemonics to trusted friends through tools such as WeChat. Some even use WeChat's picture recognition function to copy mnemonics to WPS Spreadsheets, then encrypt the spreadsheet and enable cloud services, while storing them on the computer's local hard drive. These seemingly improved information security behaviors actually greatly increase the risk of information theft. Hackers often use the method of "database collision" to collect publicly leaked account and password databases on the Internet and try to log in to these cloud storage service websites. Although this is a probability behavior, as long as the login is successful, hackers can easily find and steal information related to cryptocurrency, which can be regarded as passive information leakage. There are also some cases of active leakage, such as victims being induced by scammers pretending to be customer service to fill in mnemonics, or being deceived by phishing links on chat platforms such as Discord, and then entering private key information. Here, the MistTrack Team strongly reminds everyone that private keys/mnemonics should not be disclosed to anyone under any circumstances.
In addition, fake wallets are also a disaster area that leads to private key leakage. This part is already a cliché, but there are still a large number of users who accidentally click on advertising links when using search engines, thereby downloading fake wallet applications. Due to network reasons, many users will choose to obtain related applications from third-party download sites. Although these sites claim that their applications are all downloaded from Google Play mirrors, their true security is questionable. Previously, the SlowMist security team analyzed the wallet application on the third-party application market apkcombo, and found that the imToken 24.9.11 version provided by apkcombo is a non-existent version, and it is the version with the most fake imToken wallets on the market.

We also tracked down some backend management systems related to the fake wallet team, which include complex digital currency control functions such as user management, currency management, and recharge management. The advanced features and professionalism of this type of phishing behavior have exceeded many people's imagination.

For example, there was a rare case in Q2: a user searched for "Twitter" in a search engine and accidentally downloaded a fake Twitter app. When the user opened the app, a prompt popped up, claiming that a VPN was required due to regional restrictions, and guided the user to download the fake VPN that came with the app, resulting in the user's private key/mnemonic being stolen. Such cases once again remind us that any online applications and services should be carefully reviewed and verified to ensure their legitimacy and security.
Phishing
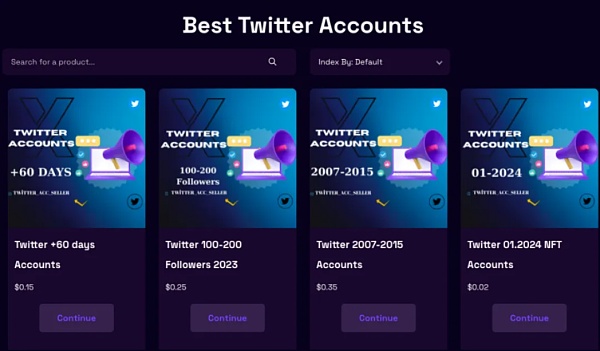
According to analysis, the reasons for phishing in many cases of stolen help in Q2 were: users clicked on phishing link comments posted on the Twitter of well-known projects. Previously, the SlowMist Security Team conducted targeted analysis and statistics: about 80% of well-known project parties will have the first message in the comment area occupied by fraudulent phishing accounts after posting on Twitter. We also found that there are a large number of groups selling Twitter accounts on Telegram. These accounts have different numbers of followers and posts, and different registration times, which allows potential buyers to choose to buy according to their needs. Historical records show that most of the accounts sold are related to the cryptocurrency industry or Internet celebrities.
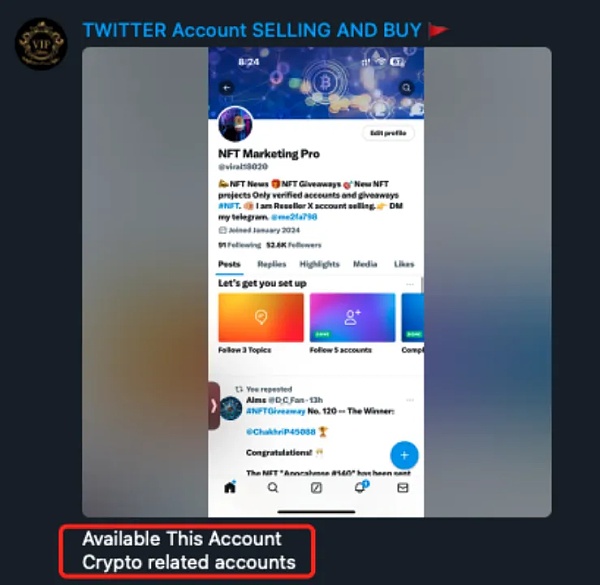
In addition, there are some websites that specialize in selling Twitter accounts. These websites sell Twitter accounts of various years and even support the purchase of highly similar accounts. For example, the fake account Optimlzm and the real account Optimism are extremely similar in appearance. After purchasing such highly similar accounts, the phishing gangs will use promotional tools to increase the account's interaction and number of fans, thereby improving the account's credibility. These promotional tools not only accept cryptocurrency payments, but also sell a variety of social platform services including likes, reposts, and fan increase. Using these tools, the phishing gang can get a Twitter account with a large number of fans and posts, and imitate the project party's information release dynamics. Due to the high similarity with the real project party's account, many users find it difficult to distinguish between the real and the fake, which further increases the success rate of the phishing gang. Subsequently, the phishing gang carried out phishing operations, such as using automated robots to follow the dynamics of well-known projects. When the project party posts a tweet, the robot will automatically reply to grab the first comment, thereby attracting more views. Given that the accounts disguised by the phishing gangs are extremely similar to the project party accounts, once the user is negligent and clicks on the phishing link on the fake account, and then authorizes and signs, it may lead to asset losses.
In general, looking at the phishing attacks in the blockchain industry, for individual users, the risks are mainly in the two core points of "domain name and signature". In order to achieve comprehensive security protection, we have always advocated the adoption of a dual protection strategy, namely personnel security awareness defense + technical means defense. Technical means defense refers to the use of various hardware and software tools, such as the phishing risk blocking plug-in Scam Sniffer to ensure asset and information security. When the user opens a suspicious phishing page, the tool will pop up a risk prompt in time, thereby blocking it at the first step of risk formation. In terms of personnel security awareness defense, we strongly recommend that you read in depth and gradually master the "Blockchain Dark Forest Self-help Handbook" (https://github.com/slowmist/Blockchain-dark-forest-selfguard-handbook/blob/main/README_CN.md). Only through the mutual cooperation of these two protection strategies can we effectively fight against the ever-changing and upgraded phishing attack methods and protect the security of assets.
Fraud
There are many fraud methods, and the most common fraud method in Q2 is the Pixiu plate. In legend, the Pixiu is regarded as a magical creature. It is said that it can swallow everything without excreting. Once swallowed, the treasures such as gold and jewelry mentioned in the fable cannot be taken out of its body. Therefore, the Pixiu plate is used to metaphorically describe digital currencies that cannot be sold once purchased.
A victim described his experience: "I asked a question in the Telegram group at that time. Someone enthusiastically answered many of my questions and taught me a lot. After we chatted privately for two days, I felt that he was a good person. So he proposed to take me to the primary market to buy new tokens and provided me with a contract address of a currency on PancakeSwap. After I bought it, the coin has been soaring. He told me that this is a golden opportunity that only comes once every six months and suggested that I increase my investment immediately. I felt that things were not that simple and did not accept his advice. He kept urging me. As soon as he urged me, I realized that I might have been deceived. I asked other people in the group to help check. It turned out that this was indeed a Pixiu coin. I also tried to buy but not sell. When the scammer found that I was no longer adding positions, he also blocked me."
The experience of this victim actually reflects the typical pattern of Pixiu scams:
1. The scammers deploy a smart contract that sets a trap and throws out bait that promises high profits;
2. The scammers try their best to attract the target to purchase the token. After the victim purchases, they often see the token appreciate rapidly. Therefore, the victim usually decides to wait until the token has increased enough before trying to exchange it, but finds that they cannot sell the purchased token;
3. Finally, the scammers withdraw the funds invested by the victim.
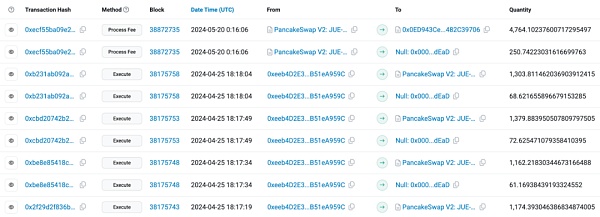
It is worth mentioning that the Pixiu coins mentioned in the Q2 form all occurred on BSC. In the figure below, you can see that there are many transactions of Pixiu coins. The scammers also sent the tokens they held to wallets and exchanges, creating the illusion that many people are involved.
Because the nature of Pixiu disk is somewhat hidden, even experienced investors may find it difficult to see the truth. Nowadays, meme style is prevalent, and various types of "Tugou coins" have a certain impact on the market. Because the price of Pixiu disk will rise rapidly, people often impulsively follow the trend and buy it. Many market participants who are unaware of the truth are struggling to chase this wave of "Tugou fever", but inadvertently step into the trap of Pixiu disk and can no longer sell it after purchasing it.
Therefore, MistTrack Team recommends that users take the following measures before trading to avoid financial losses due to participating in Pixiu trading:
Use MistTrack to view the risk of related addresses, or use GoPlus's Token Security Detection Tool to identify Pixiu coins and make trading decisions;
Check whether the code has been audited and verified on Etherscan and BscScan, or read relevant comments, because some victims will issue warnings on the fraud token comment tab;
Understand relevant virtual currency information and consider the background of the project party to improve self-prevention awareness. Be wary of virtual currencies that offer super high returns, as super high returns usually mean greater risks.
Written at the end
If your cryptocurrency is unfortunately stolen, we will provide free community assistance services for case assessment. You only need to submit the form according to the classification guidelines (funds stolen/fraud/extortion). At the same time, the hacker address you submitted will also be synchronized to the SlowMist InMist Lab threat intelligence cooperation network for risk control. (Note: Chinese forms are submitted to https://aml.slowmist.com/cn/recovery-funds.html, and English forms are submitted to https://aml.slowmist.com/recovery-funds.html)
SlowMist has been deeply involved in the field of cryptocurrency anti-money laundering for many years and has formed a complete and efficient solution covering compliance, investigation and auditing. It actively helps build a healthy cryptocurrency ecosystem and provides professional services to the Web3 industry, financial institutions, regulatory agencies and compliance departments. Among them, MistTrack is a compliance investigation platform that provides wallet address analysis, fund monitoring, and tracking and tracing. It has accumulated more than 300 million address tags, more than 1,000 address entities, 500,000+ threat intelligence data, and 90 million+ risk addresses, all of which provide strong protection for ensuring the security of digital assets and combating money laundering crimes.
 Weiliang
Weiliang














