Author:Yao & Thinking & Pds Editor: 77
Background
As the competition in live trading using large AI models intensifies, more and more crypto communities and developers are beginning to experiment with AI-driven automated trading, and many open-source solutions are being rapidly deployed. However, these projects are not without security vulnerabilities.
Open source address: https://github.com/NoFxAiOS/nofxVulnerability Cause Analysis
Through in-depth analysis by the SlowMist security team, two main authentication issues were found in different commit versions of NOFX AI.
After in-depth analysis by the SlowMist security team, two main authentication issues were found in NOFX AI.
The "Zero Authentication" vulnerability version was introduced in commit 517d0caf6fb091235e56c27889170b53a16e4e6b on October 31, 2025 (included in branches such as origin/main and origin/dev). In this commit version, admin mode is enabled by default and middleware allows access directly.
config.json.example:1-24 and the database migration script both set admin_mode to true, and main.go:42-63 directly calls auth.SetAdminMode(true) after reading.
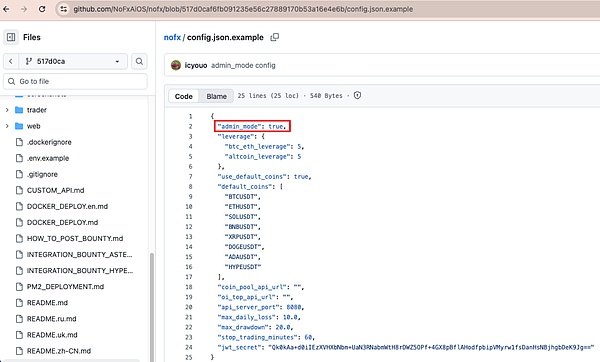
(Refer:https://github.com/NoFxAiOS/nofx/blob/517d0caf6fb091235e56c27889170b53a16e4e6b/config.json.example)
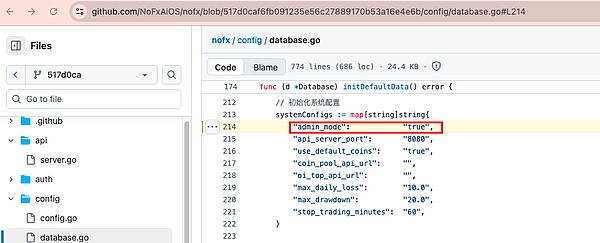
(Refer:https://github.com/NoFxAiOS/nofx/blob/517d0caf6fb091235e56c27889170b53a16e4e6b/config/database.go#L214)
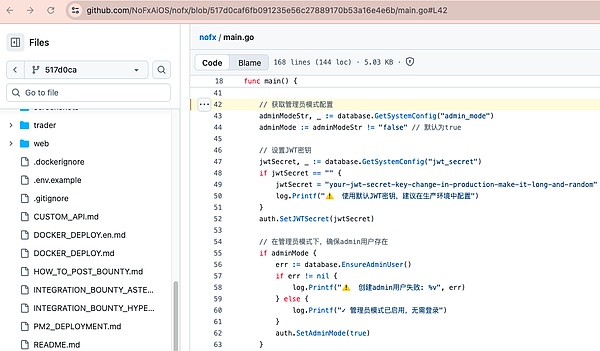
(.
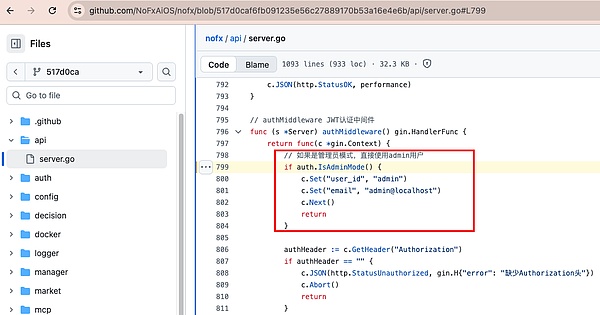
(Refer:https://github.com/NoFxAiOS/nofx/blob/517d0caf6fb091235e56c27889170b53a16e4e6b/api/server.go#L799)
So in this commit Before submission, as long as the deployment maintains the default administrator mode, anyone can directly access `/api/exchanges` and obtain all exchange APIs/private keys. In this mode, all authentication-protected APIs, including `/api/exchanges`, will execute as "admin," so anyone can simply send a GET request to the public API to obtain the complete contents of the `ExchangeConfig` field in the database. The `ExchangeConfig` field includes `api_key`, `secret_key`, `hyperliquid_wallet_addr`, and `aster_private_key`, all of which are exchange login keys or private keys. In other words, as long as the default administrator mode is maintained, anyone can directly access `/api/exchanges` and obtain all exchange APIs/private keys. This commit essentially exposes all exchange keys to a single GET request that requires no login.
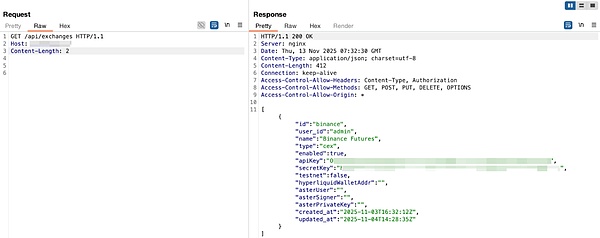
Requirements Version of Authorization
Commit on November 5, 2025 be768d91a3969b39741623c9507f3119e583eb16(PR #540 “Enable admin password in admin mode”) In the previous code, the developers removed the logic that would allow access without verifying Authorization simply by detecting admin_mode. It's important to note that this commit is currently only available in the dev branch (including local dev and origin/dev, etc.). origin/main does not contain this commit. authMiddleware has been rewritten to the form api/server.go:1471-1511, and must include Authorization: Bearer to access protected routes. Incorrect formatting or JWT verification failure will result in a 401 error.
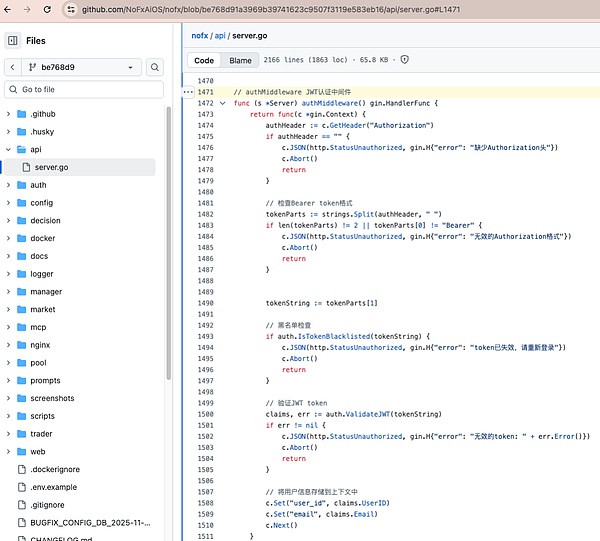
(Refer:https://github.com/NoFxAiOS/nofx/blob/be768d91a3969b39741623c9507f3119e583eb16/api/server.go#L1471)
The same submission also added The `/api/admin-login` API requires the deployer to set the environment variable `NOFX_ADMIN_PASSWORD`, meaning administrator mode is no longer "automatically activated without login". If `admin_mode` is still true, `main.go:203-226` will check the `NOFX_ADMIN_PASSWORD` environment variable and call `log.Fatalf` to terminate the process directly, unless this variable has been set beforehand. After setting the password, the administrator must submit this password through the new `/api/admin-login` API to obtain the JWT; starting the API without setting a password will result in a forced exit during the initialization phase. However, this change only upgrades "completely no authentication" to "requires JWT," still not solving two core problems. First, `config.json.example:1-27` still hardcodes `jwt_secret`, and `main.go:203-214` continues to revert to that public string when environment variables are missing. If developers directly use the example configuration file, the default key will be enabled, posing a security risk. The default deployment script in the project, start.sh, will directly copy the example configuration file when it detects a missing configuration. Secondly, /api/exchanges still returns sensitive fields such as api_key, secret_key, and Aster private key in JSON format as is. Therefore, although this version requires Authorization to access /api/exchanges, attackers can still create JWTs using the default key or obtain tokens by calling the default login interface, thereby reading all keys.
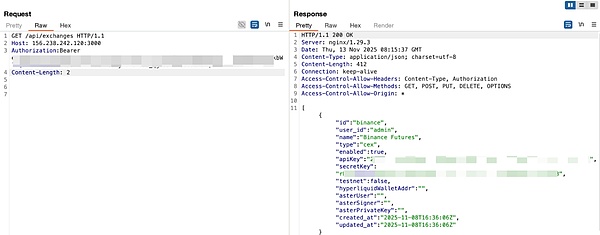
The fixed JWT issue still exists in the current version
As of now (around November 13, 2025), the HEAD of the dev branch is b2e4be91523dc606be8708ec6602fecbbb0c20ea (PR#546) "Feature/faq"). After the SlowMist security team re-checked out this submission, they found that: `authMiddleware` is still the implementation of `api/server.go:1471-1511`, which requires a Bearer token; `/api/exchanges` still directly returns `ExchangeConfig` (`api/server.go:1009-1021`); and `config.json.example:1-27` and... In main.go:198-226, admin_mode=true and the default jwt_secret are still hardcoded. Therefore, unless the operations and maintenance personnel actively change jwt_secret and disable administrator mode, attackers can still use the public key to create a fixed JWT, thereby accessing /api/exchanges and obtaining all exchange APIs/private keys. In other words, the fix on 2025-11-05 only changed the vulnerability from "zero authentication" to "authentication with the default key," and the root cause of the problem remains.
Impact
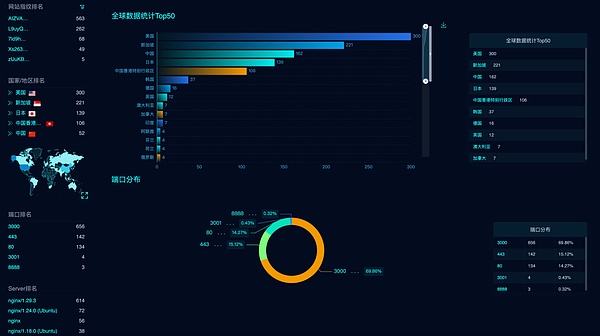
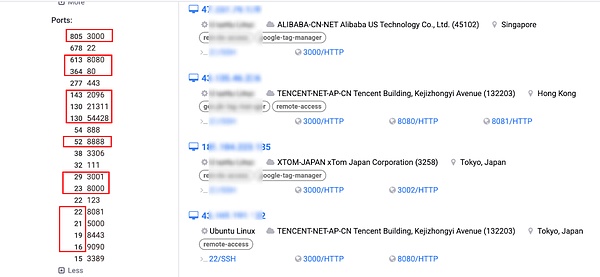
Based on program characteristics, a full network search revealed over 1000 publicly accessible systems that have been privately deployed:
 Brian
Brian
 Brian
Brian Alex
Alex Brian
Brian Alex
Alex Hui Xin
Hui Xin Kikyo
Kikyo Brian
Brian Joy
Joy Hui Xin
Hui Xin Joy
Joy