Author: DingPay
In the world of blockchain and cryptocurrency, digital signatures are one of the core technologies to ensure transaction security and data integrity. Modern blockchains rely on digital signatures to secure billions of dollars of assets. Digital signatures use so-called key pairs, which are a set of cryptographic keys consisting of a private key and a public key, where the private key is kept secret and the public key is made public. Through digital signatures, users holding private keys can sign transactions, thereby proving their ownership and control over the transaction. Therefore, it is crucial to protect the security of private keys. Tech-savvy blockchain users often choose to manage their own private keys, although this comes with the risk of the keys being stolen or lost. Other users choose to trust online wallets or exchanges and entrust the management of keys to third parties. However, this trust is not without risk because it relies on the security capabilities and reliability of the third party.
In the above scenarios, users' trust is concentrated on one entity, which may bring the risk of a single point of failure. To solve this problem, threshold digital signatures came into being. Threshold signatures are a cryptographic technique that relies on multiple cooperating participants to generate signatures. It disperses risks by introducing multiple trusted participants to avoid complete control by a single entity.
Basic Principles of Threshold Signatures
Before understanding threshold signatures, it is necessary to first understand threshold cryptography. Threshold cryptography is an encryption technique whose core idea is to split the key into multiple parts and distribute them to multiple participants. Only when a certain number of participants (i.e., the threshold is reached) can the key be reconstructed or encryption operations be performed. This is usually described as a t-out-of-n scheme, where n is the total number of participants and t is the minimum number that must participate.
A well-known example is Shamir's secret sharing scheme, which uses Lagrange interpolation to split a secret value into n parts, and only t or more parts can reconstruct the original secret. In cryptography, this technique ensures that even if the key shares of some participants are leaked, the attacker still cannot recover the complete key.
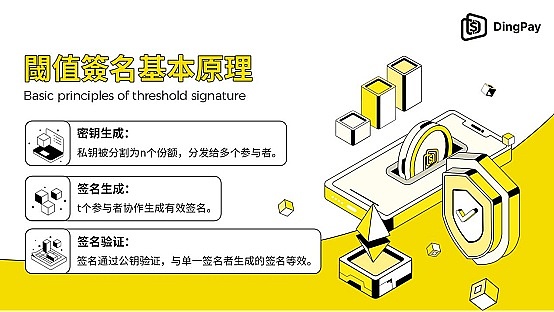
Implementation of Threshold Signature
Threshold signature schemes are usually based on existing digital signature algorithms, such as the Elliptic Curve Digital Signature Algorithm (ECDSA) or the Schnorr signature algorithm. Specifically, the implementation process of threshold signature includes the following steps:
Key generation: First, a pair of public and private keys are generated, and then the private key is split into multiple shares (secret shares) and distributed to n participants. This can be done through the Trusted Dealer mode or the Distributed Key Generation (DKG) protocol. In the DKG protocol, the key generation process is completed by multiple participants in collaboration, without any single entity holding the complete private key.
Signature generation: During the signing phase, t participants use their respective private key shares to collaborate to generate a valid digital signature. This signature is equivalent to the signature generated by a single signer in terms of verification, meaning that they can be used interchangeably.
Signature verification: Ultimately, any third party can verify the validity of the threshold signature using the same signature verification algorithm as a single signer.
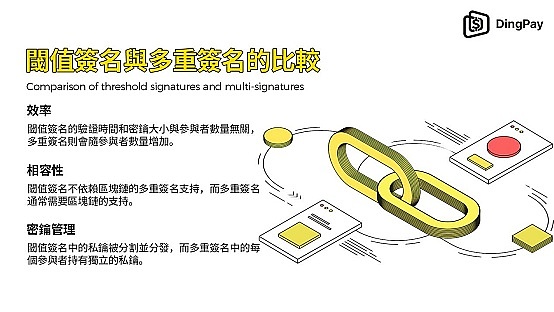
Comparison of threshold signatures and multi-signatures
In the field of cryptocurrency, threshold signatures are often compared with multi-signatures (Multisig). Multi-signature schemes also allow multiple participants to jointly sign a transaction, but each participant holds an independent public-private key pair instead of a split private key share. The following are the main differences between threshold signatures and multi-signatures:
Efficiency: In the threshold signature scheme, the verification time and key size of the signature are independent of the number of participants, and only one public key is needed to represent the entire group of participants. In the multi-signature scheme, the verification time and key size increase linearly with the number of participants because each signer has an independent public key.
Compatibility: Multi-signature usually requires the support of the blockchain itself, usually implemented in the form of smart contracts, which limits its universal application on different blockchains. MPC-based threshold signatures can be implemented independently of the blockchain as long as the blockchain supports the selected signature algorithm.
Application in DingPay
As a digital asset payment wallet dedicated to building a complete payment ecosystem, DingPay actively adopts threshold signature technology to enhance transaction security and user autonomy. Through the threshold signature scheme, DingPay can reduce the risk caused by the loss or leakage of private keys while ensuring the security of users' private keys. This distributed security mechanism eliminates the need for users to fully trust a single entity, ensuring the reliability and security of transactions.
Threshold signature technology represents an important innovation in the field of cryptocurrency. It not only improves the security of transactions, but also provides users with more control. Compared with traditional multi-signature schemes, threshold signatures have significant advantages in efficiency and compatibility. By adopting threshold signature technology, DingPay provides users with a safe, reliable and forward-looking payment solution. In the future, with the further development of threshold cryptography, DingPay will continue to explore and apply more advanced cryptographic technologies to maintain its leading position in the field of digital payments.
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance JinseFinance
JinseFinance Miyuki
Miyuki CryptoSlate
CryptoSlate New York Magazine
New York Magazine decrypt
decrypt cryptopotato
cryptopotato cryptopotato
cryptopotato Ledgerinsights
Ledgerinsights 链向资讯
链向资讯