On March 27, 2022, according to monitoring by the Beosin KYT anti-money laundering analysis platform, theBlast ecological Web3 game platform Munchables suffered a hacker attack. The hacker gained approximately 17,413.96 ETH and lost money. Over 6200W.
It is understood that Munchables is a Blast Big Bang award-winning project, and it has recently announced the completion of a Pre-Seed round of financing jointly led by Manifold and Mechanism Capital. .
After Munchables announced the attack, its TVL dropped significantly from $96 million to more than $34 million. Regarding this incident, the Beosin security team conducted an analysis immediately.

● Attack Transaction
https://blastexplorer.io/tx/0x3d08f2fcfe51cf5758f4e9ba057c51543b0ff386ba53e0b4f267850871b88170
https://blastexplorer.io/tx/0x9a7e4d16ed15b0367b8ad677eaf1db6a2a54663610696d69e1b4aa1a08f55c95
● Attacker address
0x6e8836F050A31561208A5CD7E228701563D09C5
● & nbsp; t; "> 0x29958E8E4D8A9899CF1A0ABA5883DBC7699A5E1F
Vulnerability Analysis
Previously, on-chain detective ZachXBT analyzed the attack An investigation into the cause revealed that Munchables may have been stolen due to the hiring of North Korean hackers posing as developers.
ZachXBT said: "Four different developers employed by the Munchables team are related to the exploiter and are likely the same person. They recommended each other for work, Regularly transfer funds to the same two exchange deposit addresses and recharge each other's wallets."
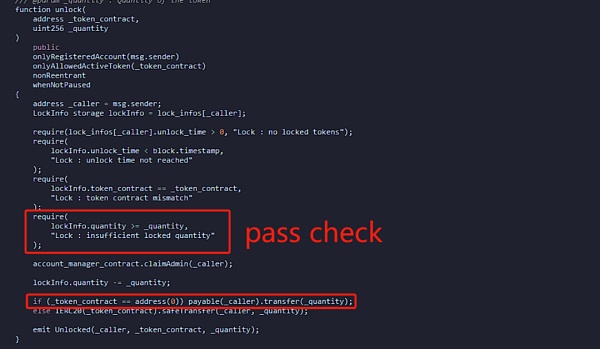
After analysis by the Beosin security team, we found that this attackmainly It was the North Korean hacker developer who used the contract upgrade function to set up his own mortgage ledger in advance. Then, after the contract accumulated funds, he withdrew the ETH in the contract by calling the unlock function.
Attack process
Attack preparation phase:
Hacker developers pre-create the implementation contract 0x910fFc04A3006007A453E5dD325BABe1e1fc4511 containing the backdoor and pre-set the hacker's own mortgage ledger to a maximum value.
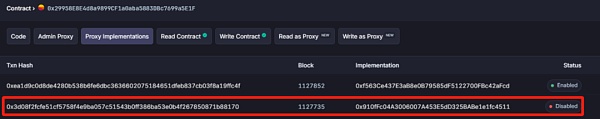
Attack stage:
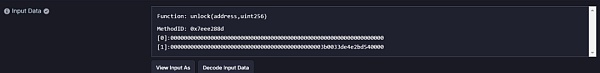
The attacker calls the unlock function to withdraw ETH. Since the hacker has already set up the mortgage ledger during the attack preparation stage, The check is easily bypassed.
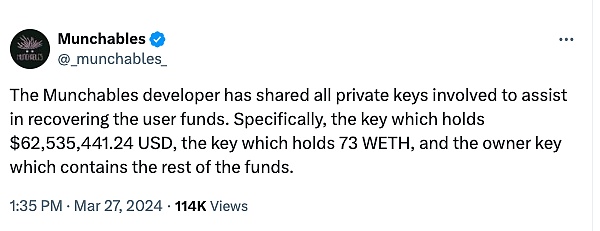
After being stolen, Munchables took to social media to The previously released announcement of shared private keys further explained that the purpose of sharing private keys is to assist security personnel in recovering user funds. Specifically, it contains the private key that holds $62,535,441.24 in crypto assets, the private key that holds 73 WETH, and the owner’s private key that holds the remaining funds.
While the project team and users were anxious, at 14:00 Beijing time, the Munchables attacker returned all 17,000 ETH to a multi-signature wallet.
As of the time of publication, the stolen funds have been returned and sent to the multi-signed contract.
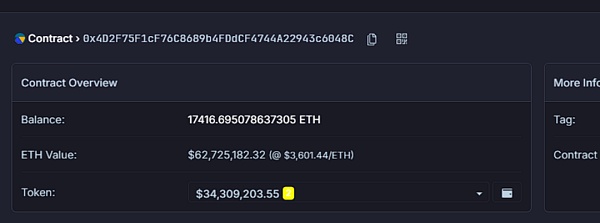
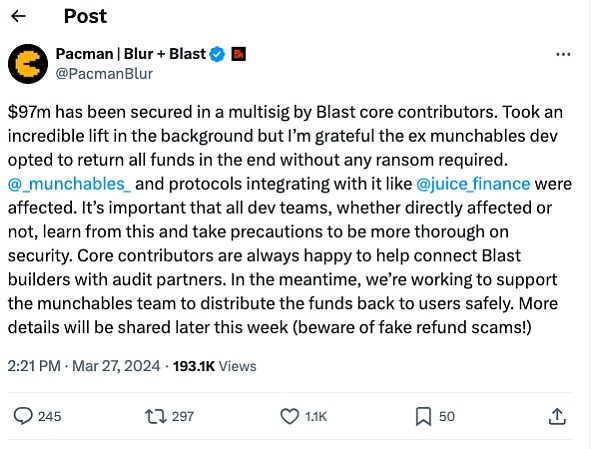
Half an hour later, Blast founder Pacman announced on the ; wETH, currently worth $96 million). Kudos to the former Munchables developer for choosing to finally return all funds without any ransom. Munchables also forwarded this announcement saying: "All user funds are safe, no locks will be enforced, and all Blast-related rewards will be distributed. Updates will be made in the coming days."
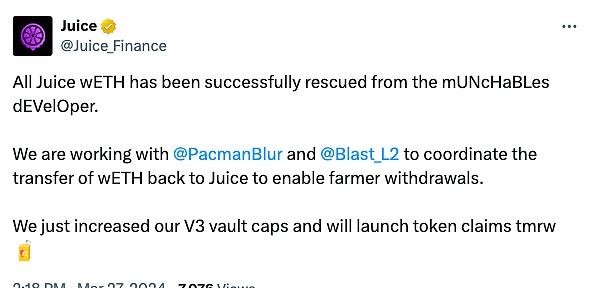
At the same time, the previous synchronization was attacked by Munchables Juice, which was affected by the incident, also announced the safety of funds. All its wETH has been withdrawn from the Munchables developers. Juice is coordinating with Pacman and Blast to transfer wETH back to Juice so that users can withdraw funds.
The twists and turns of the whole incident are surprising. Although we still don’t know the reason why the hacker returned the funds, this experience once again sounded the alarm for security. It also made us deeply aware of the importance of security. importance.
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance Cheng Yuan
Cheng Yuan Aaron
Aaron Aaron
Aaron Catherine
Catherine Catherine
Catherine Coinlive
Coinlive  Coinlive
Coinlive  Cointelegraph
Cointelegraph Bitcoinist
Bitcoinist