Background
On June 10, 2024, according to the monitoring of SlowMist MistEye security monitoring system, UwU Lend, a platform providing digital asset lending services on the EVM chain, was attacked and lost approximately US$19.3 million. The SlowMist security team analyzed the incident and shared the results as follows:
(https://x.com/SlowMist_Team/status/1800181916857155761)
Related information
Attacker address:
0x841ddf093f5188989fa1524e7b893de64b421f47
Vulnerable contract address:
0xb3f067618ce54bc26a960b660cfc28f9ea0315e2e9a1a855ede1508eb4017376
0x9bc6333081266e55d88942e277fc809b485698b9
Attack transaction:
0xca1bbf3b320662c89232006f1ec6624b56242850f07e0f1dadbe4f69ba0d6ac3 0x242a0fb4fde9de0dc2fd42e8db743cbc197ffa2bf6a036ba0bba303df296408b
Attack Core
The core of this attack is that the attacker can directly manipulate the price oracle by making large-scale exchanges in the CurveFinance pool, affecting the price of sUSDE tokens, and using the manipulated price to withdraw other assets in the pool.
Attack Process
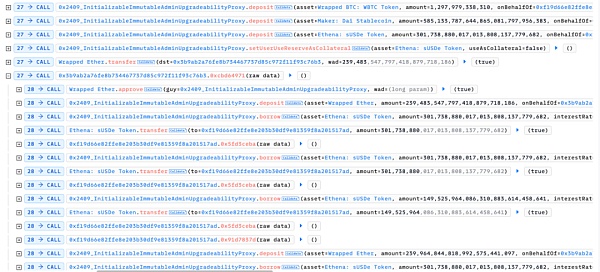
1. Borrow assets through flash loans and drive down the price of USDE:The attacker first borrows a large amount of assets through flash loans, and exchanges some of the borrowed USDE tokens for other tokens in the Curve pool that can affect the price of sUSDE.

2. Create a large number of lending positions:With the current sharp drop in sUSDE prices, a large number of sUSDE tokens are borrowed by depositing other underlying tokens.
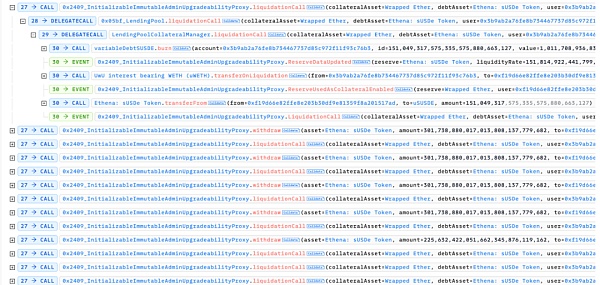
3. Manipulate the oracle again to raise the price of sUSDE:By performing a reverse exchange operation in the previous Curve pool, the price of sUSDE is quickly raised.

4. Liquidate a large number of liability positions:Due to the rapid increase in the price of sUSDE, the attacker can liquidate a large number of previously borrowed positions to obtain uWETH.
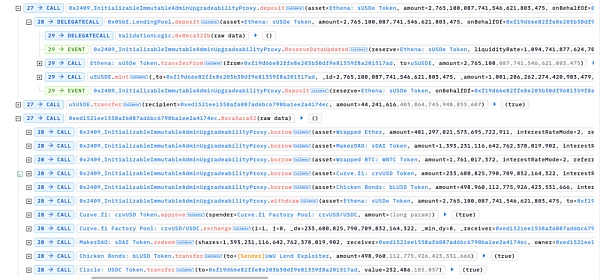
5. Deposit the remaining sUSDE and borrow other underlying tokens in the contract:The attacker deposited the currently high-priced sUSDE again to borrow more underlying asset tokens for profit.
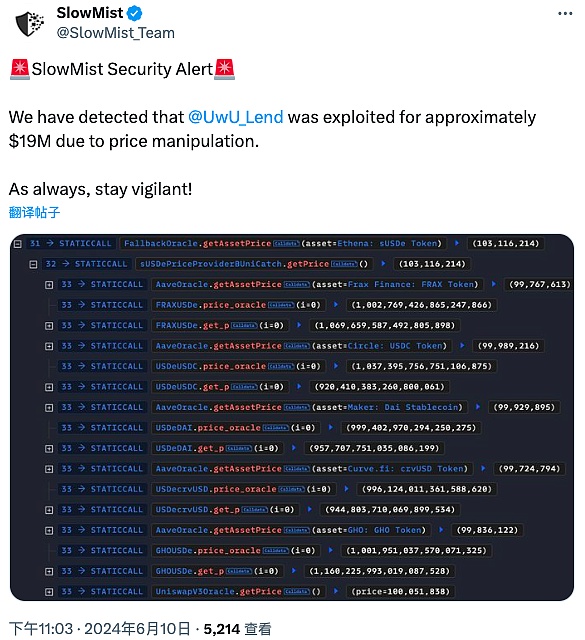
It is not difficult to see that the attacker mainly manipulated the price of sUSDE repeatedly, borrowed a large amount of money at low prices, and made profits by liquidating and re-mortgaging at high prices. We followed up with the oracle contract sUSDePriceProviderBUniCatch that calculates the price of sUSDE:
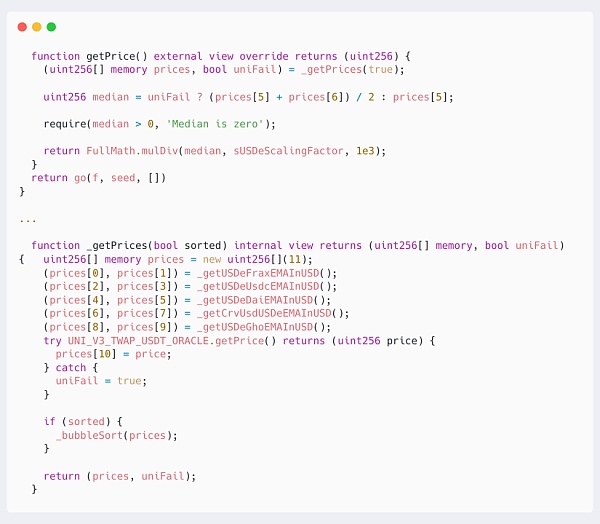
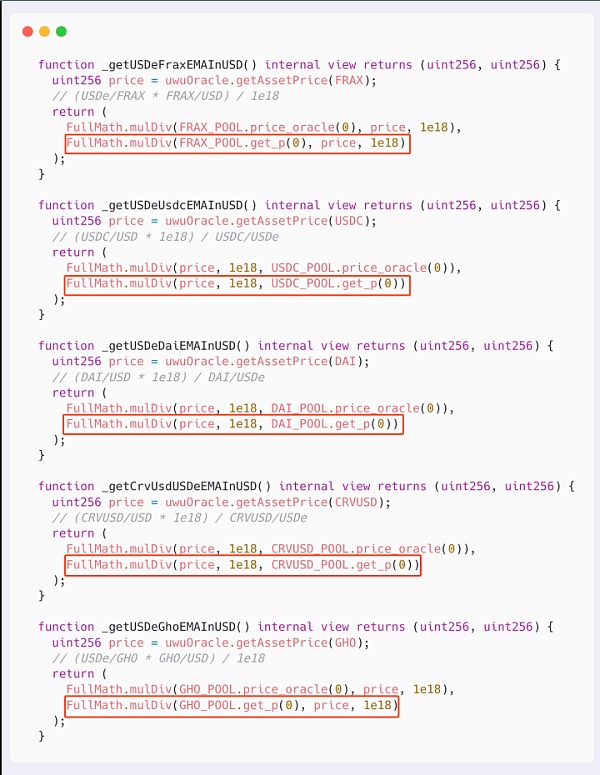
It can be seen that the price of sUSDE is determined by first obtaining different prices of 11 USDE tokens from the USDE pool and UNI V3 pool on CurveFinance, and then sorting and calculating the median based on these prices.
In the calculation logic here, the prices of 5 USDEs are directly obtained by using the get_p function to obtain the real-time spot price of the Curve pool. This allows the attacker to directly affect the calculation result of the median price by exchanging a large amount in one transaction.
MistTrack Analysis
According to the on-chain tracking tool MistTrack, the attacker 0x841ddf093f5188989fa1524e7b893de64b421f47 made a profit of approximately US$19.3 million in this attack, including the currencies ETH, crvUSD, bLUSD, and USDC. Subsequently, all ERC-20 tokens were exchanged for ETH. By tracing the fee of the attacker's address, it was found that the initial funds on the address came from 0.98 ETH transferred from Tornado Cash, and then the address received 5 funds from Tornado Cash.
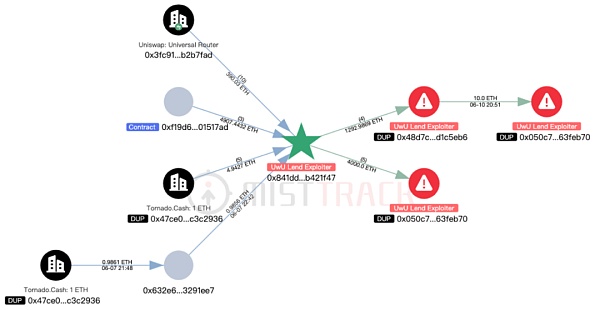
Expanding the transaction graph, it was found that the attacker transferred 1,292.98 ETH to the address 0x48d7c1dd4214b41eda3301bca434348f8d1c5eb6, and the current balance of this address is 1,282.98 ETH; the attacker transferred the remaining 4,000 ETH to the address 0x050c7e9c62bf991841827f37745ddadb563feb70, and the current balance of this address is 4,010 ETH.
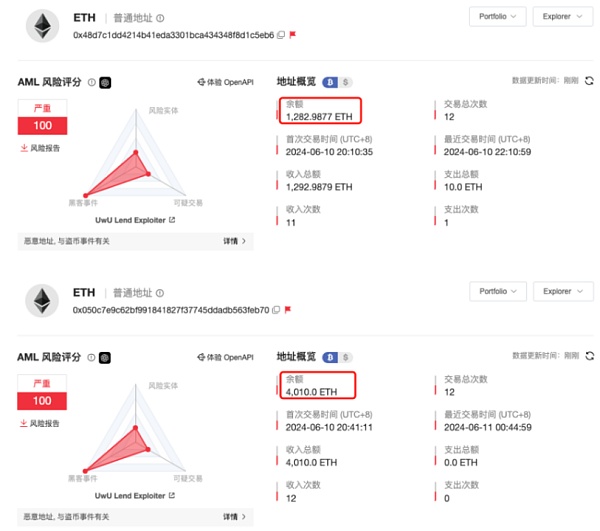
MistTrack has blacklisted the relevant addresses and will continue to pay attention to the transfer dynamics of the stolen funds.
Summary
The core of this attack is that the attacker took advantage of the compatibility defects of the price oracle to directly obtain the spot instant price and the median calculation price to manipulate the price of sUSDE, thereby borrowing and liquidating under the influence of severe price differences to obtain unexpected profits. The SlowMist Security Team recommends that the project party enhance the anti-manipulation ability of the price oracle and design a safer oracle price feeding mechanism to avoid similar incidents from happening again.
 ZeZheng
ZeZheng















