On January 1, 2024, Beijing time, according to monitoring by Beosin's EagleEye security risk monitoring, early warning and blocking platform, the Orbit_Chain project suffered an attack loss of at least approximately US$80 million. According to Beosin Trace analysis, the hacker address (0x27e2cc59a64d705a6c3d3d306186c2a55dcd5710) launched a small-scale attack as early as one day ago, and used the stolen ETH as the source of transfer fees for the remaining five addresses in this attack.
Orbit Chain is a cross-chain bridge platform that allows users to use various encrypted assets from different blockchains on one chain. Currently, the project team has suspended the cross-chain bridge contract and is communicating with the hackers. Regarding this security incident, the Beosin security team immediately conducted the following analysis.
Event Analysis
This incident was mainly caused by attackers Directly call the withdraw function of the Orbit Chain: Bridge contract to transfer the assets.
By further analyzing the code of the withdraw function, we can find that this function uses a method of verifying signatures to ensure the security and legality of lending.
In blockchain transactions, verifying signatures is a common security mechanism to confirm whether the initiator of the transaction has sufficient authority and control. In the withdraw function, by verifying the signature, it can be ensured that only authorized users or contracts can successfully call the function and transfer assets.
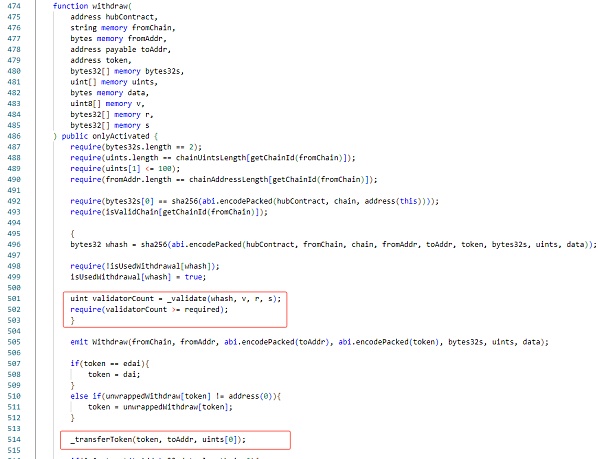
After entering the signature verification function (_validate), we can observe that the function returns the number of owner signatures. This information is crucial to verify the legality and security of the transaction.
By returning the number of owner signatures, the compliance and authenticity of the transaction can be verified to a certain extent. Depending on the implementation, the number of owner signatures may be compared to a preset threshold to determine whether the conditions for executing the transaction are met.
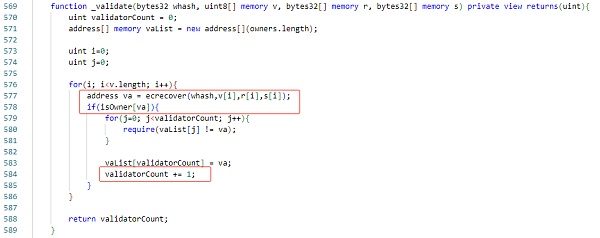
Then it is determined whether the quantity is greater than or equal to required, and if the conditions are met, the loan will be made.
It can be known from the data on the chain that the owner who manages the contract has a total of 10 addresses. The required value is 7, which means that in order to withdraw assets, 70% of administrators need to sign the withdrawal transaction.
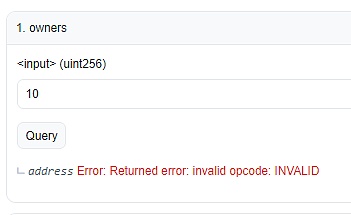
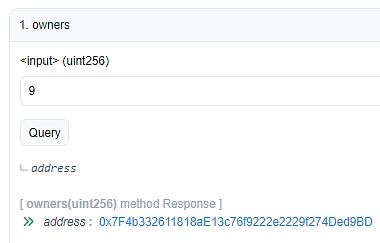

In summary, the cause of the incident tends to be that the server that saves the administrator's private key was deceived and attacked.
Attack process
According to on-chain data,hackers have successively launched attacks on the Orbit_Chain project as early as 2023-12-30 03:39:35 PM +UTC Attack, the amount of ETH stolen by the hacker is relatively small, and the stolen ETH is sent to several other hacker addresses as transaction fees.
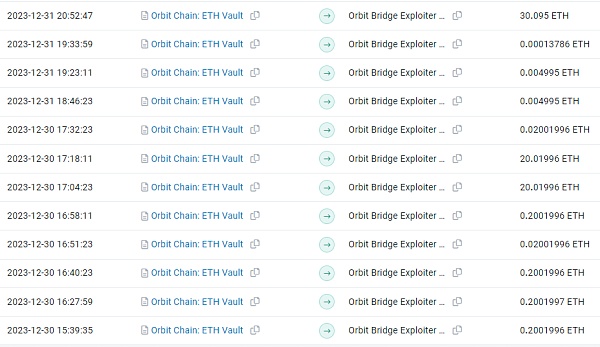
Several other hacker addresses successively attacked DAI, WBTC, ETH, USDC, and USDT of the Orbit_Chain project at 2023-12-31 9:00 PM +UTC.
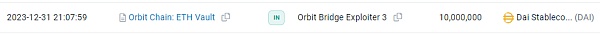


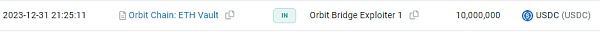
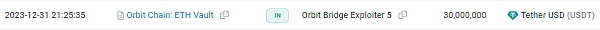
Fund Tracking
As of press time, stolen The fund transfer situation is shown in the figure below. After the hacker officially launched the attack, the stolen funds were transferred to the above five addresses. In five separate transactions, each sent to a new wallet, Orbit Bridge sent $50 million in stablecoins (30 million Tether, 10 million DAI, and 10 million USDC), 231 wBTC (approximately 10 million US dollars) and 9500 ETH (approximately 21.5 million US dollars).
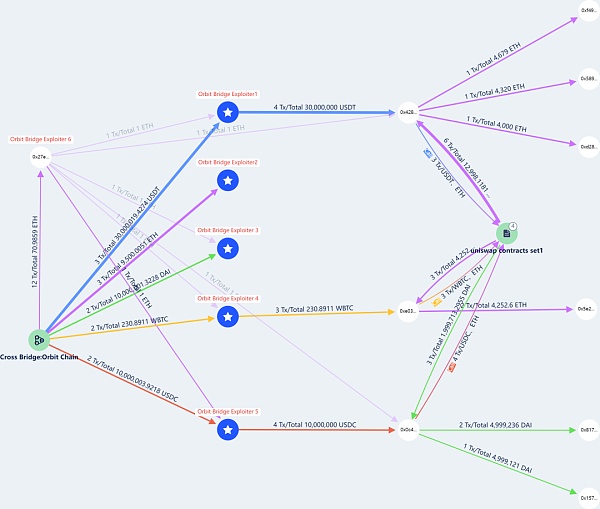
Beosin Trace tracking fund flow chart
This cross-chain bridge security incident It once again gives us security inspiration and reminds us that security should always be the primary consideration when designing and implementing blockchain systems.
First of all, we need to pay attention to the security of the code. Contract code is a core component of a blockchain system,so when writing and reviewing contract code, best practices and security standards should be followed to avoid common security vulnerabilities and attack vectors.
Secondly, authentication and identity verification are crucial. In a blockchain system, ensuring that only authorized users or contracts can perform critical operations is key to preventing unauthorized access and asset loss. Adopting measures such as strong authentication mechanisms, multi-signatures, and rights management can effectively limit access rights and ensure that only authorized entities can perform sensitive operations.
 JinseFinance
JinseFinance
















