Source: The Economist; Compiled by: AIMan@Golden Finance
Ben Zhou, the boss of Dubai cryptocurrency exchange Bybit, recalled that February 21 was originally an ordinary day. Before going to bed, he approved the transfer of funds between company accounts, which was a "typical operation" performed when providing services to more than 60 million users worldwide. Half an hour later, he received a call. "Ben, something went wrong," his chief financial officer said in a trembling voice. "We may have been hacked... All Ethereum is gone."
Independent investigators and the US FBI quickly pointed the finger at a familiar culprit: North Korea. Hackers from the hermit kingdom have become one of the biggest threats to the encryption industry and an important source of income for the North Korean regime, helping it to resist international sanctions, control elites, and fund its missile and nuclear weapons programs.
In 2023, North Korean hackers stole $661 million; in 2024, they doubled their thefts, stealing $1.34 billion in 47 thefts, equivalent to more than 60% of the total amount of cryptocurrency stolen worldwide, according to the cryptocurrency investigation company Chainalysis.
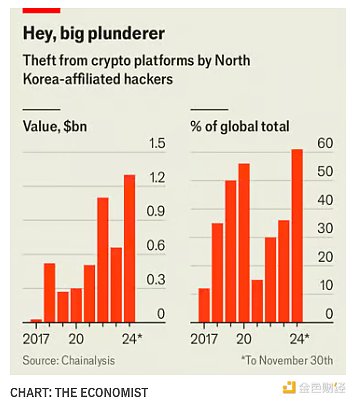
The ByBit theft shows that hackers are becoming more skilled and ambitious: In one hack, North Korea stole the equivalent of $1.5 billion from the exchange, the largest theft in cryptocurrency history.
North Korea's Cyber Force Origins
North Korea's attacks are the culmination of decades of effort. The country's first computer science school dates to at least the 1980s. The Gulf War helped the regime recognize the importance of cyber technology to modern warfare. Gifted math students were sent to special schools and exempted from annual compulsory labor in the countryside, said Thae Yong Ho, a senior North Korean diplomat who defected in 2016. North Korea's cyber forces were originally conceived as tools of espionage and sabotage, but began focusing on cybercrime in the mid-2010s. Kim Jong-un is said to have called cyber warfare a "universal sword."
Crypto Attacks and Money Laundering
Stealing cryptocurrency involves two main stages. The first stage is to hack into the target system - the equivalent of finding an underground passage to a bank vault. Phishing emails can insert malicious code. North Korean agents pose as recruiters to trick software developers into opening infected files during fake job interviews. Another approach is to use a fake identity to get a remote IT job at a foreign company, which can be the first step to access an account. “They’re very good at finding vulnerabilities through social engineering,” says Andrew Fierman of Chainalysis. In the ByBit case, the hackers compromised the computers of developers working for a digital wallet software provider.
Once stolen, the cryptocurrency must be laundered. The dirty money is spread across multiple digital wallets, mixed with clean funds and moved between different cryptocurrencies, a process known in the industry as “coin shuffling” and “chain hopping.” “They are the most sophisticated cryptocurrency launderers we’ve ever encountered,” says Tom Robinson of Elliptic, a blockchain analytics firm. Finally, the stolen funds need to be cashed out.
A growing number of underground services, many with ties to organized crime, can help make that happen. Law enforcement intercepts and roadblocks reduce overall revenue, but Nick Carlsen, a former FBI analyst now at blockchain intelligence firm TRM Labs, said North Korea can expect to get “definitely 80, maybe 90 percent” of the money it steals.
Why North Korea is so good at stealing cryptocurrency
North Korea has several advantages. One is talent. It may seem counterintuitive: The country is extremely poor, and ordinary people don’t have access to the internet or even computers. But “North Korea can pick the best talent and tell them what to do,” said Kim Seung-joo of Korea University in Seoul. “They don’t have to worry that they’re going to work for Samsung.”At the 2019 International Collegiate Programming Contest, a team from a North Korean university took eighth place, beating teams from Cambridge, Harvard, Oxford and Stanford.
Those talents have been put to use, too. North Korean hackers work around the clock. They are unusually bold when they launch their attacks. Most state actors try to avoid diplomatic backlash and “act like they’re in Ocean’s Eleven: wear white gloves, go in quietly, steal the crown jewels, and leave quietly,” said Jenny Jun of Georgia Tech. North Korea doesn’t “value secrecy — they’re not afraid to make a lot of noise.”
What North Korea’s Stolen Crypto Is Used For
For the North Korean regime, stolen cryptocurrency has become a lifeline, especially as international sanctions and the coronavirus pandemic have curbed their already limited trade. Crypto theft is a more efficient way to earn hard currency than traditional sources of hard currency, such as overseas labor or illegal drugs. The United Nations Panel of Experts (UNPE), a monitoring body, reported in 2023 that cyber theft accounts for half of North Korea's foreign exchange earnings. The value of digital theft in North Korea last year was more than three times the value of its exports to China. "What a workforce of millions acquires can be replicated by just a few dozen people," Mr. Carlson said.
The funds help prop up the North Korean regime. Hard currency is used to buy luxury goods to keep the elite in check. It is also used to build weapons. Much of North Korea's stolen cryptocurrency is believed to have flowed into its missile and nuclear weapons programs.
Will there be more North Korean hacks in the future?
Crypto investigators are getting better at tracking stolen funds on the blockchain. Mainstream cryptocurrency exchanges and stablecoin issuers often work with law enforcement to freeze stolen funds. In 2023, the United States, Japan and South Korea announced a joint operation aimed at combating North Korean cybercrime. The United States has sanctioned several "coin mixing" service providers used by North Korea.
However, the authorities are still a step behind. After the United States sanctioned North Korea’s favored mixers, hackers turned to other companies offering similar services. Solving the problem requires a multilateral effort by governments and the private sector, but that cooperation has been breaking down. Last year, Russia used its veto at the United Nations to abolish the United Nations Commission on Cybersecurity Capabilities. President Donald Trump’s moves to cut U.S. development aid have dealt a blow to programs aimed at building cybersecurity capabilities in vulnerable countries.
In contrast, North Korea is pouring more and more resources into cybercrime. South Korean intelligence estimates that North Korea’s cybercrime force grew from 6,800 in 2022 to 8,400 last year. North Korea has an increasingly “rich target environment” as the cryptocurrency industry expands in countries with weaker regulation, said Abhishek Sharma of the Observer Research Foundation, an Indian think tank. Mr. Sharma noted that last year, North Korea attacked exchanges based in India and Indonesia.
North Korea is already known to use AI in its operations. AI tools can help make phishing emails more convincing and easier to craft at scale in multiple languages. They can also make it easier for remote IT workers to infiltrate companies. Bad days like Bybit's Mr. Zhou's may become more common.
 Alex
Alex
 Alex
Alex Miyuki
Miyuki Weiliang
Weiliang Kikyo
Kikyo Joy
Joy Alex
Alex Catherine
Catherine Weatherly
Weatherly Miyuki
Miyuki Weiliang
Weiliang