xKingdom claims to be a SocialFi and GameFi platform based on Arbitrum. On this platform, users can build a "kingdom" on the X social platform and receive rewards by interacting with tweets, participating in treasure hunts and other tasks. The project has 3 ERC-20 contracts and 1 NFT contract.
On January 6, 2024, the xKingdom project team stole community funds and deleted their website and all social media disappear. The xKingdom exit scam resulted in a total loss of $1.2 million and is one of the worst exit scams to occur in the past few months.
Event Overview
To join xKingdom, users must first mortgage ETH to lend XKING. According to the interaction records on the chain, participants can exchange XKING for XCOIN and receive XCROWN. The document explaining the relationship between these ERC-20 contracts has been deleted, but after research, we believe that both XCOIN and XCROWN can be replaced by XKING.
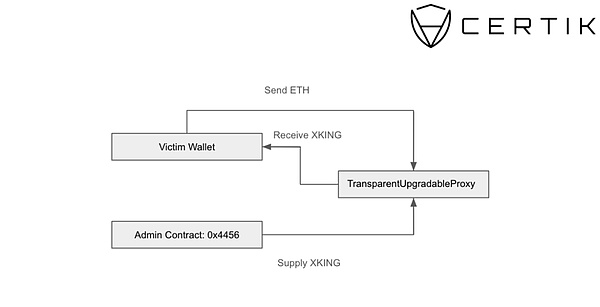
To obtain XKING, users need to call the borrow() function on TransparentUpgradableProxy contract 0xdcd...7275e.
This function will transfer the user's ETH to the above contract, and then obtain XKING from the administrator contract 0x445...24a13. Although the 0x4456 contract has not been verified, we can evaluate its role through the setConfig() and grantRole() functions.
The above process operates normally in the initial stage until the amount of ETH deposited in the TransparentUpgradableProxy contract exceeds 500.
"Escape" Timeline
- < p style="text-align: left;">December 29, 2023: Authorization
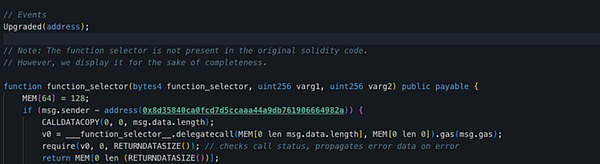
When analyzing the 0x445...24a13 contract (most likely the administrator contract), we found that the project team called grantRole() multiple times on December 29, 2023, add MINTER_ROLE (0x9f2...956a6) to each contract.
When decompiling the administrator contract, we found that MINTER_ROLE is a prerequisite for executing multiple functions, including claimETH.
The following pictures are some cases:

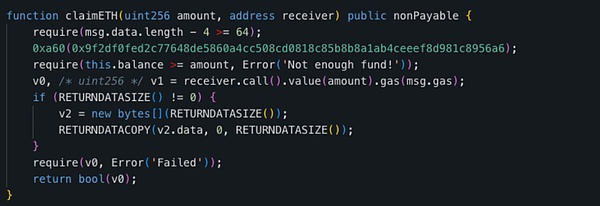
< p style="text-align: left;">In the picture below, we can see that the TransparentUpgradableProxy contract 0xdcd...7275e mentioned at the beginning to store user ETH also owns MINTER_ROLE.
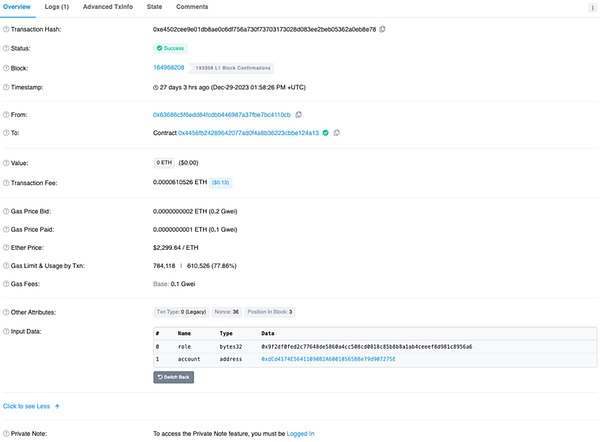
Decompilation analysis of the TransparentUpgradableProxy contract shows that the contract also has a proxy administrator contract 0x8d3...4982a.
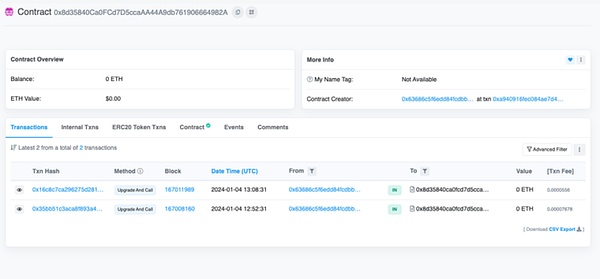
January 4, 2024: Upgrade
At 12:52 pm and 13:08 pm UTC time, xKingdom called upgradeAndCall() twice to upgrade the TransparentUpgradableProxy contract mentioned above.
We found no new changes in these two upgrades that directly led to exit scams. The centralization risk surrounding the claimETH and retrieveETH functions has always existed before the contract upgrade.
However, the timing of this upgrade is very interesting: It was carried out amid a series of failed interactions between contract deployers and the xKingdom contract.
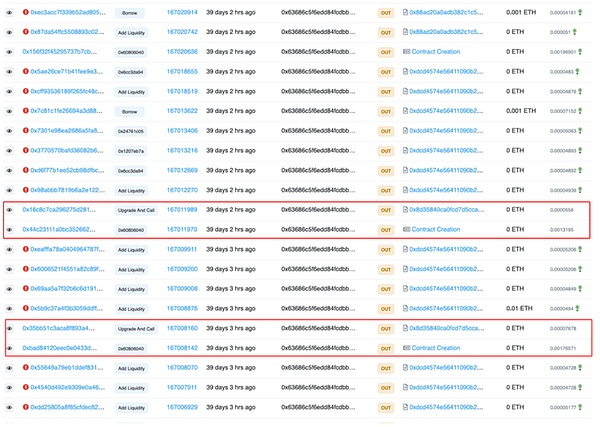
One possible explanation is that the project team tried to prove to the community that they were fixing some problems that occurred in the project by upgrading twice. The content of these two upgrades includes modifications to the addLiquidity() function and revert(), but the upgraded contract call still fails.
In the final "escape" action, the project team called claimETH() and transferred 558.3 ETH was transferred from the TransparentUpgradableProxy contract to the address 0xeF7...6A13D.
After converting part of the stolen ETH into stable coins, the project team transferred 1.02 million USDT and 99 ETH across Linked to the Ethereum network. The funds were then transferred to 0xCA1...474c6, who exchanged the stolen funds back for ETH and deposited them into Tornado Cash.
Event summary
xKingdom incident is 2024 so far The second largest exit scam that occurs.
Six such scams have occurred in 2024, with losses exceeding $4 million. Often as the market picks up, more scammers hiding in the dark will take advantage of users' positive emotions to commit fraud.
In order to better prevent such incidents and enhance community confidence, CertiK provides the project team with a strict and comprehensive KYC process. After completing the certification, the project can obtain a KYC badge on the Skynet page, which represents CertiK's independent certification of the project team.
 Brian
Brian