Before this, Beosin has conducted a complete link analysis of the Bybit incident. Now, the hacker is "cleaning" the stolen funds. At the same time, Bybit has obtained about 446,869 ETH (worth about $1.23 billion) through various channels such as loans, large deposits and ETH purchases. At present, Bybit is close to making up for the funding gap caused by the hacker incident. The Beosin team is also analyzing the progress in sync with the Bybit team.

Bybit Hacker Attack Overview
Bybit is a world-leading cryptocurrency derivatives exchange, founded in 2018, headquartered in Singapore, with an operations center in Dubai, UAE. In addition, it has obtained corresponding VASP licenses in Cyprus, Kazakhstan, Georgia and other countries. The exchange focuses on providing perpetual contracts, option contracts, spot trading and other services for cryptocurrencies, and is committed to creating a safe, efficient and transparent digital asset trading platform for users.
At 22:56 on February 21, Beijing time, the cryptocurrency trading platform Bybit was hacked. The scale of the attack was huge, and more than 400,000 ETH and stETH with a total asset value of approximately US$1.44 billion (approximately RMB 10.4 billion) were transferred to an unknown address.
According to the analysis of the Beosin security team, the stolen assets mainly include:
401,347 ETH (worth about 1.12 billion U.S. dollars)
8,000 mETH (worth about 23 million U.S. dollars)
90,375.5479 stETH (worth about 250 million U.S. dollars)
15,000 cmETH (worth about 44 million U.S. dollars)
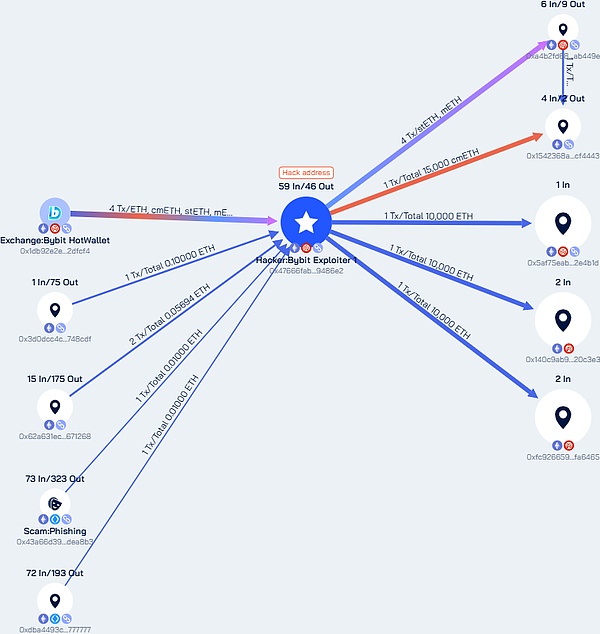
Complete review of the incident
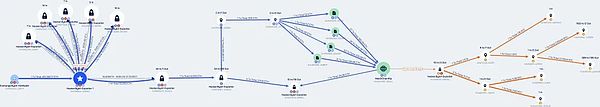
Technical details and timeline of the attack process
1. Attack timeline restoration
Before February 21, 2025:
The hacker organization Lazarus Group may have lurked in the devices of Bybit team members through Trojans and other means to prepare for subsequent attacks
February 21, 2025:
The hacker tampered with the front-end interface of the Safe multi-signature wallet accessed by the Bybit team, induced the signer to sign a malicious transaction, and changed the smart contract logic of the ETH cold wallet to a malicious contract controlled by the hacker, thereby completely controlling the wallet.
UTC time 2025-02-21 14:16:11, Bybit exchange hot wallet has more than 1.46 billion US dollars worth of ETH and stETH flowing to the hacker address
0x47666fab8bd0ac7003bce3f5c3585383f09486e2, becoming the largest theft in the history of cryptocurrency.
UTC time 2025-02-21 14:44:00, Bybit's co-founder Ben Zhou confirmed the incident at the first time, saying that Bybit's official cold wallet was hacked and began to deal with related security issues urgently.
We have carried out in-depth tracking and analysis of the stolen funds in the Bybit exchange hacker attack. The study found that one of the stolen funds was deposited at 0x36ed3c0213565530c35115d93a80f9c04d94e4cb. At 06:28:23 UTC on February 22, 2025, 5,000 ETH was transferred to the split address 0x4571bd67d14280e40bf3910bd39fbf60834f900a. Subsequently, the funds were split into amounts ranging from tens to hundreds of ETH at a frequency of once every few minutes, and further transferred to multiple addresses. It is worth noting that after multiple transfers, some funds attempted to cross-chain to the BTC chain address through Chainflip
bc1qlu4a33zjspefa3tnq566xszcr0fvwz05ewhqfq, which shows that the hacker tried to further conceal the flow of funds through cross-chain operations.
In addition, we found the same address in the Bybit hacker attack and disposal path as the Bingx and Phemex hacker attack and disposal path, suspecting that these attacks were carried out by the same gang or used the same disposal path, and the overlapping address is:
0x33d057af74779925c4b2e720a820387cb89f8f65
0xd555789b146256253cd4540da28dcff6e44f6e50.
This key discovery further confirms our previous inference based on the similarity between the attack mode and the WazirX incident, that is, the Bybit exchange hacker attack is very likely related to the Lazarus Group.
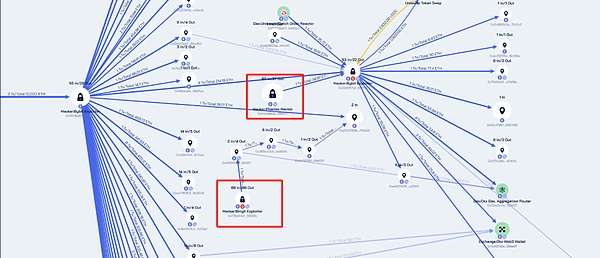
February 23, 2025:
Bybit hackers' stolen goods sales model has stabilized, mainly using Thorchain to transfer assets to the BTC public chain, and using OKX DEX to convert them into DAI for circulation.
2. Analysis of attack technical means
a. Vulnerability exploitation methods (such as phishing attacks and social engineering methods, front-end UI tampering, malicious contract deployment).
Phishing Attacks and Social Engineering
The attackers hacked into the computers of Bybit internal employees through phishing attacks (such as forged emails or malicious links) and obtained operating permissions. Using social engineering methods, attackers may disguise themselves as internal personnel or partners to induce employees to click malicious links or download malware, thereby implanting backdoors.
Front-end UI Tampering
The attackers tampered with the front-end interface of the Safe multi-signature wallet, forged a seemingly normal transaction prompt page, and induced the signers to sign malicious transactions. When the signers confirmed the URL "Safe", the actual signed transaction content had been tampered with, resulting in the implantation of malicious contract logic.
Malicious contract deployment
The attacker deployed a malicious contract (address: 0xbDd077f651EBe7f7b3cE16fe5F2b025BE2969516) before the attack, and wrote the malicious logic into the STORAGE[0x0] of the Safe contract through DELEGATECALL. The malicious contract contains backdoor functions (such as sweepETH and sweepERC20) to transfer assets in the cold wallet
b. How the attacker bypasses the risk control system (such as forging IP or pages, simulating normal user signing behavior, etc.).
Forged pages and transaction prompts
The attacker tampered with the front-end interface of the Safe multi-signature wallet and forged a seemingly legitimate transaction prompt page, making the signer mistakenly believe that the transaction content was normal. The transaction content seen by the signer on the hardware wallet was inconsistent with the actual transaction content, resulting in the "blind signature" phenomenon.
Simulation of normal user behavior
After invading the employee's device, the attacker simulated normal user operation behavior (such as logging in, signing, etc.) to avoid triggering abnormal behavior detection by the risk control system. By forging IP addresses or using proxy servers, the attacker concealed the true source and further evaded the IP blacklist detection of the risk control system.
Exploiting the limitations of hardware wallets
Hardware wallets have insufficient parsing capabilities when processing complex transactions and cannot fully display the detailed transaction data of the Safe multi-signature wallet, resulting in the signer being unable to verify the authenticity of the transaction content. The attacker took advantage of this flaw and induced the signer to "blindly sign" by forging the transaction content.
Bypassing the trust loophole of the multi-signature mechanism
Although Bybit uses a multi-signature mechanism, multiple signatories rely on the same infrastructure and verification process. Once one of the links is breached, the entire security system is breached. An attacker only needs to break into the device of one signer to forge transactions and obtain sufficient signing permissions.
The laundering path of stolen funds and key breakthroughs
1. Analysis of money laundering methods
a. Cross-chain bridge conversion: transfer assets through Chainflip, ChangeNow, Thorchain, LiFi, DLN, etc.
Lazarus Group is good at using various cross-chain bridges to evade on-chain tracking. In addition to Chainflip, the organization has also widely used cross-chain tools such as Avalanche Bridge, BitTorrent Bridge, Thorchain, Threshold and Swft to transfer funds in previous attacks. For example, Avalanche Bridge was found in the Atomic Wallet theft, Alphapo theft, Stake.com theft, DMM Bitcoin theft, Harmony cross-chain bridge attack, and Coinspaid theft.
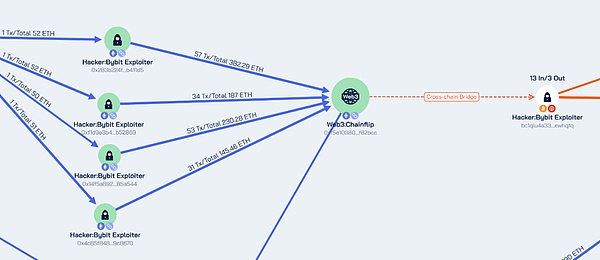
b. Mixing platform used: eXch Mixing Exchange
Lazarus Group used Tornado Cash, Sinbad, and Railgun to mix and clean funds.
Tornado Cash was sanctioned by the U.S. Treasury Department's Office of Foreign Assets Control (OFAC) in 2022 for assisting the Lazarus Group in money laundering. The organization subsequently stopped using the mixer. However, since March 2024, the Lazarus Group has once again used Tornado Cash for large-scale fund laundering. It is worth mentioning that we are fully prepared for the Bybit incident. Once the relevant funds enter the Tornado.cash mixer, Beosin will immediately initiate fund penetration analysis. The special working group has been equipped with the latest version of the Tornado Cash penetration algorithm, and several professional analysts who have successfully completed fund penetration in similar cases have joined to ensure that the flow of funds can be tracked efficiently and provide strong support for subsequent actions.
Sinbad was designated by OFAC as the main money laundering tool of the Lazarus Group, especially in the CoinEX theft incident, the organization transferred a large amount of stolen assets to Sinbad for mixing operations.
Railgun is also an important channel for Lazarus Group to launder funds. In early 2023, the Federal Bureau of Investigation (FBI) reported that Lazarus Group had laundered more than $60 million in illegal funds through Railgun.
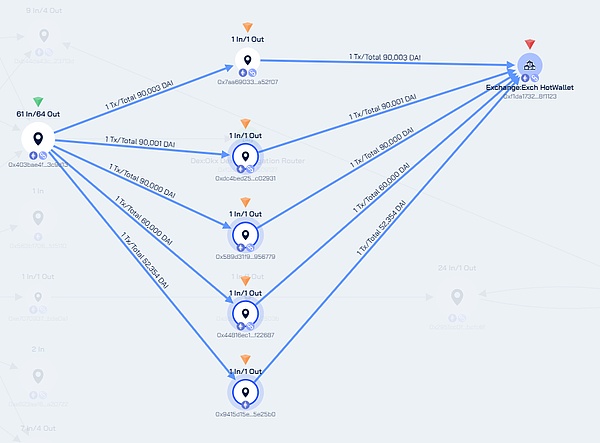
c. OTC money laundering
After stealing crypto assets, Lazarus Group usually adopts a chain money laundering process of cross-chain transfer + mixer cleaning + OTC realization. The organization will first repeatedly transfer the stolen funds between multiple cross-chain bridges, and use the mixer to cover the source of funds, and then extract them to a specific address cluster, and then use OTC transactions to convert crypto assets into legal currency.
Statistics show that exchanges such as Paxful, Noones, MEXC, KuCoin, ChangeNOW, FixedFloat and LetsExchange have all received funds associated with the Lazarus Group. In addition to on-chain money laundering, the organization also frequently uses over-the-counter transactions to evade regulation. Previous reports show that since 2022, OTC trader Yicong Wang has long provided funds laundering services to the Lazarus Group, helping the organization convert tens of millions of dollars worth of stolen crypto assets into cash through bank transfers. The Lazarus Group has demonstrated a highly systematic operating model in the process of fund laundering. This multi-level, decentralized money laundering method further increases the difficulty of tracking funds.
How do crypto asset platforms conduct pre-emptive defense, in-process response, and post-event tracking?
1. Pre-emptive defense
a. Strengthen the security construction of the internal multi-signature process, use proprietary networks and equipment for signature review and operation, and prevent the equipment from being controlled by hackers and becoming a breakthrough for hackers to enter the intranet;
b. When reviewing the signature content, the signatory should clearly compare the consistency between the signature displayed in the process and the content displayed in the wallet. If any abnormality is found, the signing process should be stopped immediately and an emergency response should be carried out;
c. The risk control system can also monitor the fund dynamics of cold and hot wallets in real time, and issue timely warnings for abnormal behavior;
d. When the signature data of a multi-signature wallet is submitted to the chain, only a few fixed addresses can be specified to submit the signature data, and the transaction submission and signature permissions are controlled within the enterprise.
2. Emergency response during the event
a. Threat intelligence sharing: Rapid warning through the Beosin security intelligence network.
b. Emergency response mechanism: After discovering abnormal transactions, quickly initiate emergency response, evaluate whether it is necessary to suspend customer wallet deposits and withdrawals, synchronize the situation with the community, and use the power of the entire security community to hinder the flow of stolen funds;
c. Attack source tracing analysis: Combine on-chain data with off-chain logs to track the source of the attack and the destination of funds.
d. Fund freezing assistance: Link financial and law enforcement agencies to freeze stolen funds.
3. Post-event tracking and review
a. Fund flow map: Use the Beosin Trace tool to visualize the money laundering path.
b. Anti-money laundering (AML) labeling: Beosin quickly marked all hacker-related wallet addresses as hackers and issued alerts for all fund transfers, blocking the hackers from laundering money through Beosin's customer platform.
c. Judicial evidence support: Provide an on-chain evidence chain that meets legal standards.
Warnings and industry improvement directions brought by this incident:
The Bybit incident exposed the loopholes in the cryptocurrency industry's fund security management and sounded the alarm for the entire industry. The following are some important lessons learned from this incident:
Improve the security of the multi-signature process
Multi-signature management of funds is a common practice in the industry, but its security still needs to be strengthened. In this incident, hackers hacked into the internal Safe signature system workflow, implemented signature fraud and tampered with the signature data. Therefore, the security of the signature system is of paramount importance, and similar attacks must be prevented through technical upgrades and strict permission management.
Strengthen the review and monitoring of the signature link
During the signing process, the operator needs to carefully review the signature content. For example, when signing with a cold wallet, the signature content should be compared with the signature content displayed on the front end to detect potential anomalies. In addition, it is recommended to simulate the execution of the signed data and broadcast the transaction after confirming that the execution result is consistent with the expectation. Although the hacker directly obtained the signature content and broadcast the transaction in this incident, this step can still effectively prevent other types of attacks.
Establish an industry alliance to jointly respond to security threats
Establish a VASP (Virtual Asset Service Provider) industry alliance to share the latest major event information and security threat intelligence among alliance members, and gather industry forces to jointly respond to hacker attacks and money laundering. This collaborative mechanism can enhance the defense capabilities of the entire industry.
Strengthen compliance construction and prevent money laundering risks
Decentralized protocols and VASP platforms need to further strengthen compliance construction to avoid being used by hackers for money laundering activities. Once a platform is marked as a high-risk entity by the compliance department, it will seriously affect the deposit and withdrawal operations of normal users. Therefore, exchanges and decentralized platforms should improve anti-money laundering (AML) and know your customer (KYC) mechanisms to ensure compliance operations.
Continuously optimize security and compliance mechanisms
Security and compliance is a dynamic process that needs to be continuously optimized based on the latest threats and technological developments. Industry practitioners should remain vigilant, regularly review and upgrade security measures, and actively participate in the formulation and improvement of industry standards.
The Bybit incident is not only an exposure of a security vulnerability, but also a test of the security and compliance system of the entire industry. Only through technology upgrades, process optimization, industry collaboration and compliance construction can we effectively respond to increasingly complex network security threats, protect user asset security, and promote the healthy development of the industry.
 Kikyo
Kikyo










