Author: Paul, CoinmanLabs Researcher
In today's digital age, as our personal data is everywhere, how to protect privacy has become a global focus. The rise of blockchain technology has not only changed our understanding of finance and data management, but also provided new possibilities for privacy protection. Today, we will explore how to build a safe and efficient digital society with the help of blockchain technology combined with three cutting-edge technologies: zero-knowledge proof, multi-party computing and fully homomorphic encryption.
With the popularity of cryptocurrency and the maturity of blockchain technology, we can achieve secure transactions in an untrusted environment.
1. Zero-knowledge proof technology (ZK) allows us to verify the validity of a transaction without disclosing personal information. This means that you can prove that you own a digital asset without exposing your account balance or transaction history
2. Multi-party computing (MPC) further strengthens our ability to protect privacy in the case of multiple parties. Imagine that multiple individuals can work together to complete complex computing tasks without sharing their private data. This technology is not only suitable for data analysis in the financial industry, but can also be applied to healthcare, market research and other fields.
3. Fully homomorphic encryption (FHE) provides us with a higher level of data protection method, especially in cloud computing and outsourced data processing. With fully homomorphic encryption, we can encrypt data and safely entrust it to cloud service providers for computing without worrying about the risk of data leakage or tampering.
Above we gave an overview of the three, maybe everyone is confused, then let's take an example to help everyone better understand.
Suppose Alice, Bob and Charlie have a complex project to complete, involving identity verification, computing sensitive data and outsourcing processing:
Verify identity (ZK): Alice needs to prove that she has permission for the project, but does not want to disclose her password. She uses zero-knowledge proof to show Bob that she does have the permission, and Bob trusts her without knowing the specific password.
Computing sensitive data (MPC): Alice, Bob, and Charlie need to calculate the total budget for the project. Each of them has their own part of the budget, but they don't want to reveal it to each other. They use multi-party computation to get the total budget without telling each other their specific budget amounts.
Outsourced processing (FHE): Finally, they need to perform complex analysis on the project data, and they decide to outsource this part of the work to a cloud server. They fully homomorphically encrypt the data and then send the encrypted data to the cloud server. The server completes the analysis without decrypting the data and returns the encrypted result. Alice decrypts it to get the final analysis result.
Then let's summarize:
ZK (zero-knowledge proof): prove without leaking, prove that a fact is true without leaking any additional information related to the fact.
MPC (Multi-Party Computation): Calculation without disclosure, allowing multiple participants to jointly perform calculations without disclosing their input data.
FHE (Fully Homomorphic Encryption): Data is encrypted and then outsourced for calculation. The data is encrypted and then outsourced for calculation. Finally, the correct result can be obtained without decrypting the data.
These three technologies each solve the privacy protection problem in different scenarios:
ZK is used for verification without leaking information.
MPC is used for multi-party collaborative computing to ensure the privacy of all parties' data.
FHE is used to protect data privacy when outsourcing computing.
After this summary, you can understand their respective functions and application scenarios more clearly.
Mind Network

Project official website: https://mindnetwork.xyz/
Project Twitter: https://x.com/mindnetwork_xyz
Project Introduction: Mind Network is FHE re-staking for POS and AI networks. Its framework runs as an FHE verification network, bringing secure computing and consensus to AI, DePIN, EigenLayer AVS, Bittensor Subnet and many key POS networks.
Investment institutions:

Project Analysis
Q· What are the problems with current POS?
Since ETH switched to POS, more and more projects have also switched to POS. Now let us briefly explain how to generate blocks under the POS mechanism. In POS, the coin holders pledge their tokens to get the opportunity to generate blocks. Then, in the POS consensus, the election algorithm will be used to select miners according to the proportion of the coin holdings. The miners complete the packaging transaction at the specified height, generate a new block, and broadcast the block. The broadcasted block is verified by the validator. After verification, the block is confirmed. In this way, a round of POS consensus process is completed.
At first glance, this is no problem and it is relatively fast. It also saves energy. Let's look back at the three important elements of blockchain: decentralization, security, and scalability.
Personally, I think decentralization is the most important point. This is also the reason why BTC block upgrades failed and ETH tried to reduce the cost of operating nodes (POW period). Now there will be a problem after switching to POS, because the nodes are selected according to the amount of coins held, so is it possible to be centralized?
For most POS networks, they usually use native tokens to pledge and entrust to validators, and reach a consensus-based voting mechanism. Of course, these are not a big problem for ETH, because ETH's nodes are scattered and decentralized enough, but in some networks with fewer nodes, we will see a lot of cheating and manipulation in the voting process, that is, by imitating and influencing the results of other validators
People are lazy. For example, when you search for products, most of them will look at the front. Of course, this is also true in the blockchain. What about your vote? Will you also follow the options with more people or the first few options? Then this will definitely cause centralization and reduce consensus.
Let's talk about another problem. In many scenarios, miners and validators need to process high-value data such as personal data, sensor data, transaction data, and generate output predictions or analyses with a certain degree of sensitivity. These input and output data must be protected, especially in decentralized networks to process high-value data in production. This is a well-known problem in practical applications.
How does Mind Network solve it?
As we said above, Mind Network uses FHE technology to solve it. Here I will give you an example.
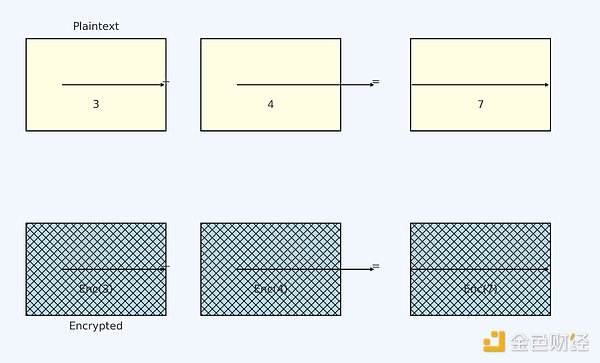
Let's do a simple addition first. 3+4=7, which we all know. Now what if we encrypt 3 and 4 separately? Then Enc(3) and Enc(4) are generated respectively. Now we don't know the encryption algorithm and can't know the specific encrypted result. This is likely to be a string. If you know a little code, you may know that the string cannot be calculated. But in FHE, when you encrypt the plaintext, you can calculate it. It's very simple to calculate Enc(3)+Enc(4)=Enc(7), and get the correct calculation result without letting anyone get the plaintext.
Does this perfectly solve the above problems? Honest nodes calculate the correct results and prevent other nodes from blindly following, thereby improving the consensus of the overall network.
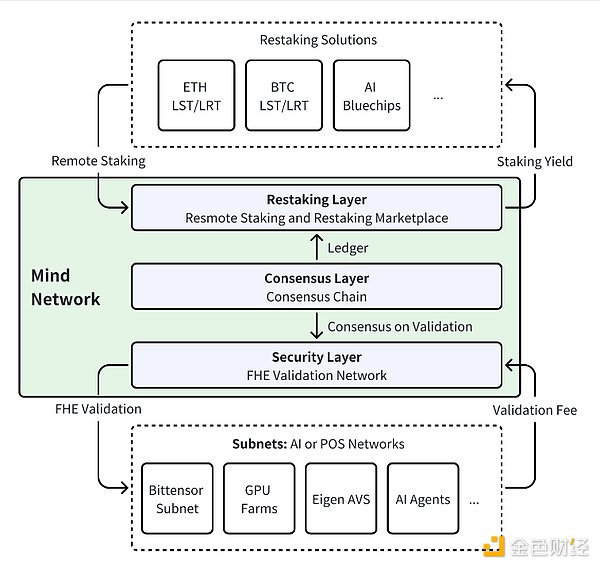
Mind Network has a layered structure: heavy pledge layer, consensus layer, and security layer.
Security Layer
The core security service of the Mind Network FHE verification network consists of multiple independent FHE validators.
Consensus Layer
This is the backbone of Mind Network. It is a Rollup chain developed with AltLayer and EigenDA to ensure consensus of the FHE verification process and to protect the remote pledge ledger that interacts with users.
Restaking Layer
Accepts pledges from Ethereum, BTC, and AI ecosystems from various chains and networks through remote pledges. It also acts as a re-pledge market, providing different re-pledge tokens for Subnet to protect its network.
One of the final nodes is the Mind Network subnet: a subnet is an AI or POS network that uses Mind Network's FHE verification service and becomes part of the ecosystem. They can be networks built from scratch on Mind Network or existing networks that use Mind Network's verification services, which is equivalent to outsourcing.
Participant Benefits
Mind Network introduces a fully homomorphic encryption (FHE) re-staking layer to protect consensus, data, and crypto-economic security through FHE verification. It brings benefits to all participants:
1. For AI and POS networks:
Consensus security: FHE verification protection ensures the fairness and security of consensus calculations.
Crypto-economic security: Further protection by providing a re-staking market, allowing AI or POS networks to use re-staking tokens from ETH, BTC, or AI ecosystems to diversify risks.
Data security: End-to-end encryption of high-value data through decentralized computing ensures data security.
2. For heavy stakers:
Remote staking: Stake liquidity staking tokens on mainstream chains without transferring to other chains to minimize costs and avoid bridging risks.
Income from AI Network: Get additional income on top of the income from re-staking native tokens of AI and POS networks.
3. For validators:
FHE validation: Participate in the FHE validation network and earn rewards by registering and providing GPU-accelerated FHE validation.
Heavy Staking Guide
Mind Network's re-staking service is an innovative layer designed to enhance the security and functionality of AI and Proof of Stake (POS) networks. It uses fully homomorphic encryption (FHE) to accept re-staking tokens from major cryptocurrencies such as ETH, BTC, and AI bluechip tokens, forming a secure and efficient FHE verification network.
Advantages of Mind Network's re-staking service:
1. Asset security: Through FHE, Remote Staking is realized without cross-chain asset transfer, reducing security assumptions, reducing costs, and ensuring Staking security.
2. Flexibility and convenience: Mind Network supports a variety of LST/LRT assets, providing flexibility and ease of use for re-staking.
3. Diverse rewards: By participating in Restaking, you can not only obtain the original network Staking rewards and protocol rewards, but also obtain additional rewards from Mind and AI/POS networks within the ecosystem, improving asset liquidity and utilization.
4. Contribute to network security: The pledged assets will serve the FHE verification of the subnet, contributing to and benefiting from the overall security and reliability of the decentralized ecosystem.
5. Obtain Mind XP: In the upcoming phase, participants who re-stake can obtain Mind XP rewards.
Currently supported networks and tokens: Ethereum, Scroll, tokens are: eEth, ezEth, stEth, STONE, pSTONE, pufETH, swETH, weETH.
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance JinseFinance
JinseFinance Edmund
Edmund Cryptoknowmics
Cryptoknowmics Beincrypto
Beincrypto Coinlive
Coinlive  Darren
Darren Beincrypto
Beincrypto Bitcoinist
Bitcoinist Cointelegraph
Cointelegraph