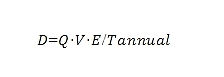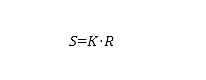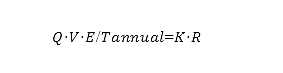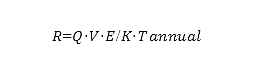Author: ArweaveOasis, Source: PermaDAO
In the past month, @aoTheComputer ecosystem has ushered in tremendous development, continuously releasing the latest progress including Permaweb 1.0, AO white paper/Tokenomics, and AI on AO. And Tokenomics is undoubtedly the most concerned content of the entire ecosystem. Since the development of AO Mint, more than $400 million of $stETH assets have been stored in the AO network. This short-term rise in TVL undoubtedly shows the industry's interest and confidence in this new narrative distributed supercomputer.
At present, there are a lot of text contents about AO in the community, all of which are well written, so I will not repeat them. Today I want to talk about the overall economic model after staking AO Token becomes a role in various networks after the AO mainnet is launched. How to reflect the time value of staking? How can these mechanisms be used to regulate the dynamic balance between roles in the network?
Security Foundations of Mainstream Blockchains
First, let's compare the current mainstream blockchains.
The economic model used by blockchain networks such as Bitcoin, Ethereum, and Solana is a relatively common and typical one that revolves around the concept of purchasing scarce block space. Users pay transaction fees to incentivize miners or validators to package their transactions into blocks and broadcast them to the entire network to complete the operation of on-chain. However, this model essentially relies on the scarcity of block space to drive fee income, thereby providing funds to incentivize network security maintainers (that is, miners or validators).
Bitcoin's security architecture mainly relies on block rewards and transaction fees. Let's assume a scenario where the scarcity of block space will no longer exist if block rewards are canceled and transaction throughput is assumed to be infinitely scalable, which will cause transaction fees to plummet. Therefore, the economic incentives for network participants to maintain security will also drop significantly, which will undoubtedly bring unprecedented challenges to the security of the entire network.
Solana's primary consensus mechanism is a combination of PoH (Proof of History) and PoS. As the network scales, fee income decreases accordingly. In the absence of large transaction fees, the main source of security funding comes from block rewards, which on Solana are initially 8% inflation, decreasing by 15% each year until they stabilize at the long-term inflation target of 1.5%. These long-term inflations are essentially a tax on token holders, which appear as operational expenses for holders who choose to stake their tokens, and as a gradual dilution of their proportional ownership in the network for those who do not stake.
AO's Security Resource Market Model
Like other blockchains, whether a network can operate more securely and stably depends on providing a reasonable enough economic model for the overall security of the network to incentivize participants to maintain the network in the long term. But in contrast to the above example, AO does not use a "one size fits all" model, but introduces a new way of security resource market model, allowing each user to purchase the specific security level required for each message. This model facilitates the customization and efficient allocation of security resources by allowing users to purchase “insurance” for their messages to achieve the level of security deemed necessary by their counterparties. This direct relationship between the supply of message security and user fee expenditures avoids the need to subsidize security through block rewards or collective fee negotiation mechanisms.
In addition, AO’s economic model creates a competitive market for network stakes, which become the cornerstone of network security. Since security is purchased per message, a dynamic staking market emerges so that security prices are determined by supply and demand rather than rigid network rules. This market-driven approach facilitates efficient pricing and allocation of security resources, providing strong security tailored to the actual needs of users.
Stake Exclusivity Period
An important feature of the AO security framework is the implementation of a “Stake Exclusivity Period”. This security mechanism enables message recipients to specify a specific time window. During this exclusivity period, the staked assets are locked and cannot be used for other purposes, ensuring that if the message is later found to be problematic, the stake can be slashed rather than "double-spent".
This feature significantly enhances the credibility of the transmission process by allowing recipients to set a "stake exclusivity period" that meets their specific transaction security needs. Stakers can also customize security measures based on the risk and value of the message. For critical or high-value messages, such as large transactions in finance, longer exclusivity periods can be set to provide parties with enough time to conduct the necessary challenges and verifications, while for low-value messages, shorter exclusivity periods are sufficient. This arrangement not only enhances security, but also strengthens the integrity and resilience of the message verification process.
Time Value of Stake
In the AO model, each message delivered requires the user to compensate the staker for the "time value of the stake", which is the opportunity cost of locking up capital for a specific period of time to ensure the security of the message. This mechanism plays a key role in determining the pricing dynamics within the AO system.
Let's assume that a user wants to provide a 15-minute staking exclusivity period for a message worth $1 million. The cost of "insurance" for this message - paying the time value of the stake - can be modeled as a function of the staker's expected annual return. For example, if the staker expects a 10% annual return on their participating capital, the cost of providing security for this message can be derived as a fraction of this expected return during the exclusivity period.
The formula for calculating the price P of providing security for an exclusivity period of length E in a given unit (such as minutes or seconds, etc.) is as follows:
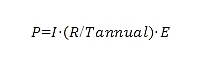 Where:
Where:
I is the value of all collateral provided for this insurance,
R is the expected annual rate of return of the pledger,
E is the pledge exclusivity period,
T_annual is the total number of time units considered for the pledge exclusivity period in one year (for example, minutes is 525,600).
For a message with a stake of $1 million, a 15 minute exclusivity period, and an expected return of 8%:
P=$1,000,000⋅(0.08/525,600)⋅15=$2.28
In this example, the time value price for a staker to stake $1 million is $2.28. Message recipients can choose their preferred over-collateralization ratio and stake exclusivity period, effectively balancing risk with the cost of accessing the service. Service providers also have the flexibility to customize their time value strategy for each message of varying value.
This flexibility reflects the underlying economic principle of the network: providing a customizable environment that enables users and services to adjust parameters such as stake amounts and timing to meet the needs of their specific operations.
Supply and Demand in the Staking Market
The equilibrium in the AO staking message market is influenced by the interaction between security demand (driven by the value of the message and the staking exclusivity period) and the supply of staking capital (affected by the expectations of stakers’ returns).
Security staking demand: can be expressed as a function of the number of transactions Q and their average value overline{V}, adjusted by the average staking exclusivity period overline{E}:
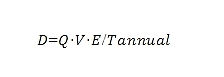
This formula reflects the total staking capital demand required for the average economic value active in message security at any given time.
Stake capital supply: Its economic utility S is modeled as the product of the total available stake K and the expected rate of return R:
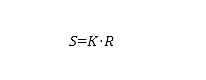
This equation reflects the total economic value that staked capital hopes to generate in a year. Among them, K represents the number of AO tokens actively invested in ensuring network security (because staking requires AO tokens to be completed), and R is the annualized expected rate of return on these staked tokens.
When the pledge market is balanced, D=S, that is, supply and demand reach a balanced matching state, the above formula can also be converted to:
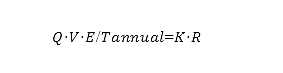
Solving the required rate of return R, we can balance the supply and demand relationship of the pledge utility and get:
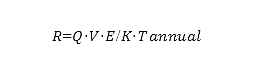
This formula calculates the equilibrium rate of return R. If the calculated R is higher than the current market rate of return, it indicates that the pledged capital is insufficient relative to the security demand. Therefore, more capital will flow into the pledge, and the K value will increase until a new equilibrium is reached. Conversely, if R is lower than the market rate of return, it indicates that the pledged capital is in excess, and some pledgers will withdraw funds, thereby reducing the K value until the equilibrium is restored.
Based on the above analysis, we can understand the relevant economic model of the AO network in token staking in the future in a relatively detailed manner. It can be said that this new customizable security resource allocation model makes the overall network more flexible and scalable.
And this decentralized peer-to-peer market structure of the AO network essentially allows nodes to independently set the fees for their pledge messaging services without forcing global pricing. This flexibility enables them to dynamically adjust to market demand and supply changes, promote competition and increase responsiveness. Nodes that offer competitive rates and terms will naturally attract more users, optimize their returns and lead to efficient market equilibrium.
This mechanism promotes market efficiency while laying the foundation for clear token valuation indicators. By analyzing the volume and value of secured messages and competitive rates of return, a comprehensive real-time token valuation framework is established, which depends on the security, utility and demand of the network.
 Sanya
Sanya


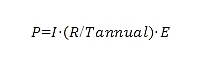 Where:
Where: